Granola bars taste better when you make them right in your own kitchen. And this is the perfect recipe for you to try out. They're jam-packed full of seeds, nuts and carrots, and they're made with all natural ingredients, and are very healthy and easy to make!

It is important to know how to keep your cooking and baking ingredients fresh. Many have either an expiration date or a "use by" date on the containers which should be followed. Shortening can turn rancid if it is kept in a warm environment. To keep it from going bad it can either be stored in your refrigerator or in a sealed container in a cool, dark, dry place. Sugar doesn't generally go bad, but it can develop moisture which causes lumps to form. If this happens then you can usually either...
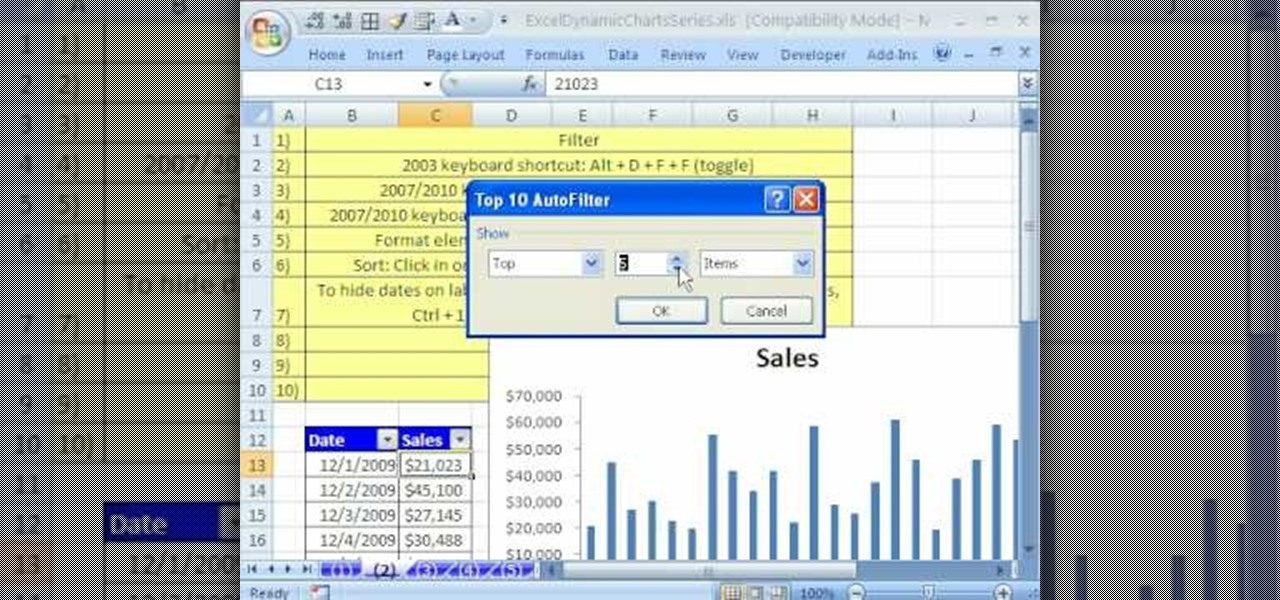
In this Software video tutorial you will learn how to use the filter & sort feature in Excel. First create a column chart on an excel sheet. In this example, it is a date and sales chart. Click alt+F1 and the chart is displayed. Then click and delete the legend and the horizontal lines. Now go back to the data set, click on a cell and click ctrl+shift+L and that will add the auto filter. ctrl+shift+L is for Excel 07. For earlier versions, see the commands listed in the video. This is a toggle...
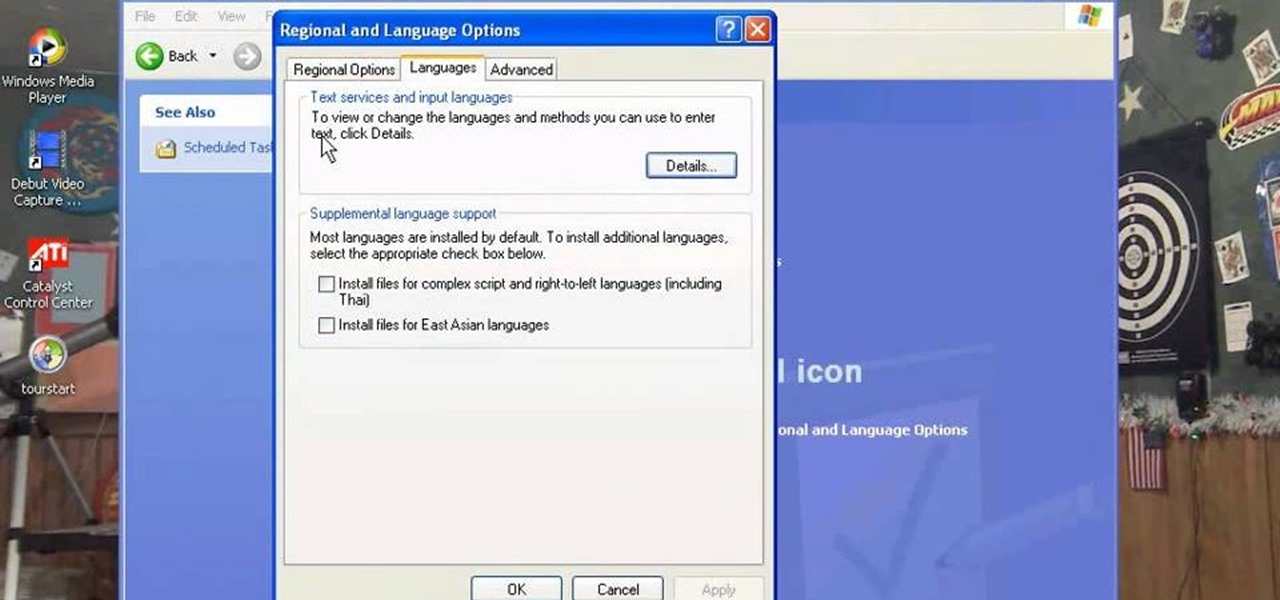
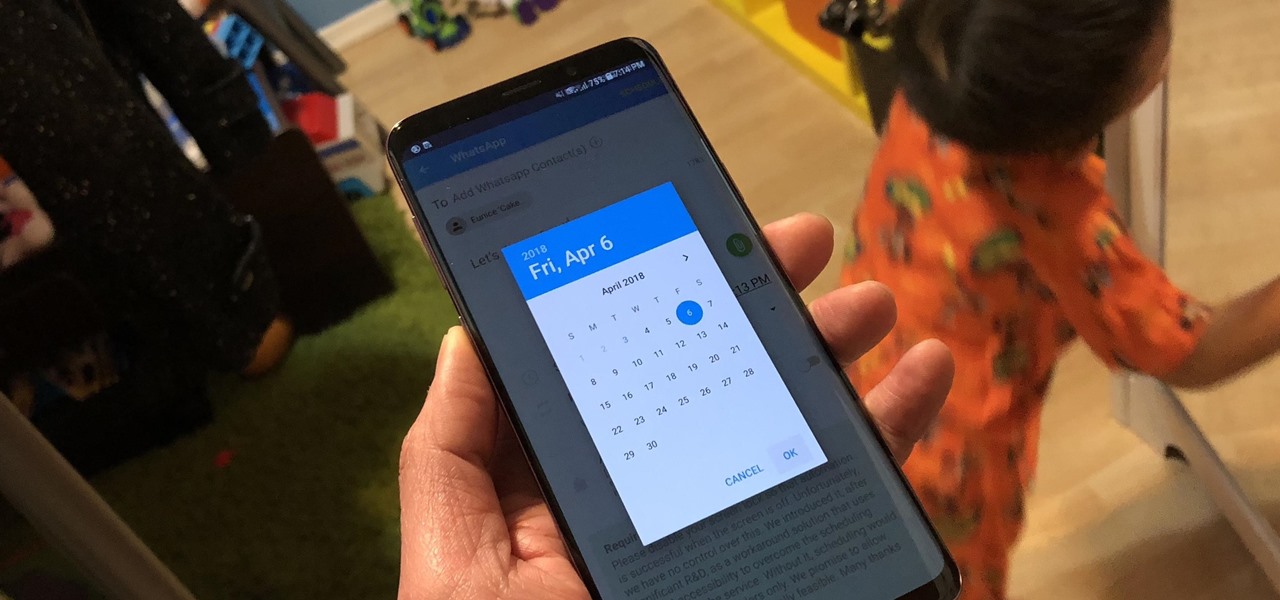
There are a number of items that you will have to use your mouse and click onto in the process of changing your clock, language and religion in Windows XP. Click START-CONTROL PANEL-DATE/TIME/REGIONAL OPTIONS. This will get you to the window that allows you to change any of these settings. To change the date or the time click on Date/Time icon. Here is displayed the current time. If you change the time here, you will have to click the Apply button to enable the new setting. Set to the correct...
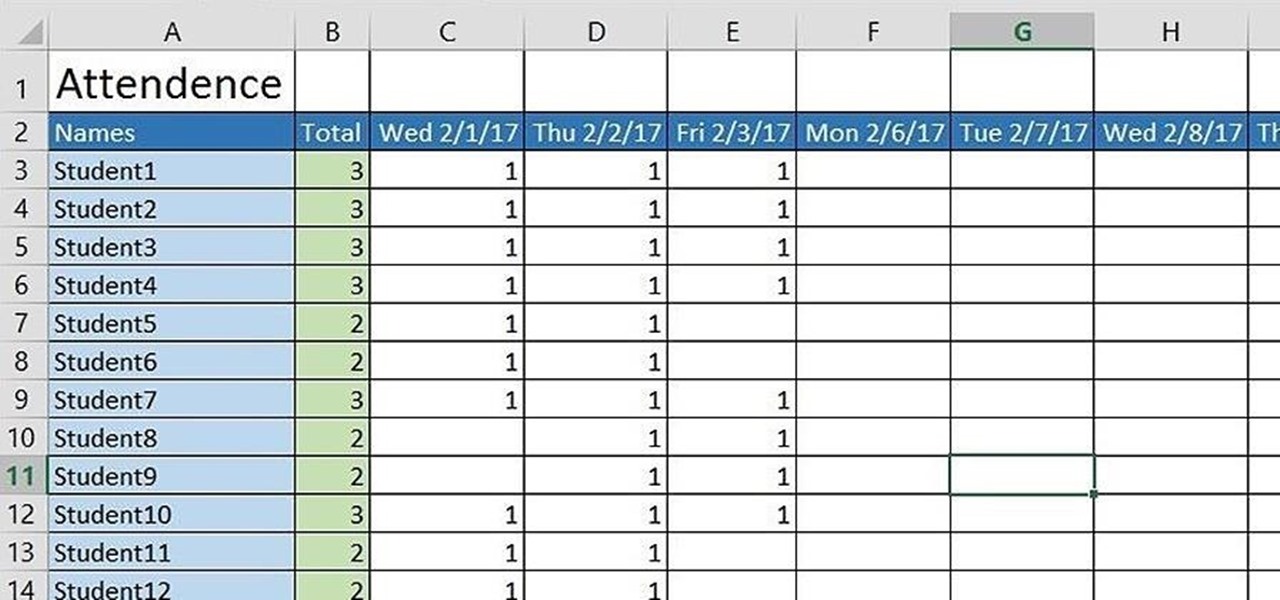
If you're a teacher in any type of school, whether it's high school, college, or middle school, it's imperative that you keep an attendance sheet. The paper and pen route can get pretty messy, and very disorganized, and that's where Microsoft Excel comes in. With this software, you can create a simple yet functional attendance sheet to keep track of your students.

It might seem easy to a few, but some of us out there grew up with email and consider "the letter" an artifact. However, writing a letter is the ultimate in class and shows someone you took the extra time to get in touch with them. Whether you are writing a business letter or a friendly letter, these tips will guide you in properly writing that letter to a special someone, friend, or client.

What would be cooler than showing up at your prom with a famous celebrity? It's a long shot, but here's your best chance to make it a reality.

The difference between a good fashion shoot and a great one isn’t the model — it’s the lighting. Learn how to expertly light a fashion shot with this how to video.

Twitter is a science. The smarter you post and engage with others, the better chance you have at building a bigger audience. Scheduling your tweets is one way to get there. Most engagement occurs at specific hours, but you may not be around then to post your tweet manually. While the official Twitter app on iOS and Android doesn't allow you to schedule, there is another way.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

While Snapchat is no stranger to location-based AR scavenger hunts, the app's new world-facing game adds some environmental understanding to the mix.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

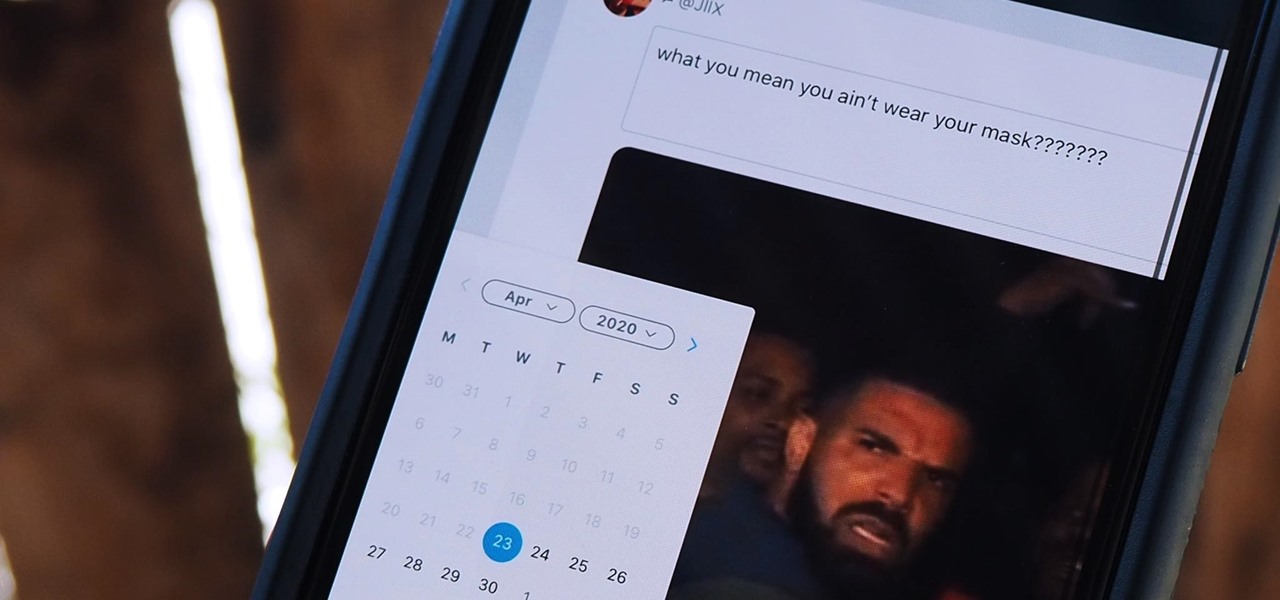
Great ideas often strike at random times, but messaging friends and loved ones at an inopportune hour not only risks their wrath, but also increases the chances of your message not being paid proper attention to. Thankfully, there's an app that lets you create and post WhatsApp messages at the time you wish for maximum effect.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

Android's share intents system is great in theory, but the execution can sometimes be frustrating. When you tap the "Share" button next to a link, app, or file, you see a list of apps you can share that item with. But it seems like every time you use this function, the list of apps is in a different order — especially when it comes to the Direct Share targets at the top.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

With a new installment of the Saw horror series opening in theaters nationwide this weekend, Lionsgate is betting its ad dollars on immersive advertising to sell tickets.

Shapr is a new networking app that aims to help professionals connect more efficiently, and draws much of its format from dating-focused social networking apps. Shapr could be especially useful for those who have recently moved into their industry or location, and for those seeking employers or employees. For example, the app already has 65,000 users just in New York City alone.

Finally, the much anticipated OnePlus 5 has got a release date. A few days ago, a leaked image from OnePlus suggested that June 20 might possibly be the launch date for the Chinese smartphone and today those leaks were confirmed.

In a series of news about the OnePlus 5, the company posted its first teaser of the upcoming device on its Weibo account. According to GSM Arena, the teaser doesn't show us any sneak peaks of what the phone might look like — co-founder Carl Pei took care of that — though, we are greeted with the caption "Hey Summer! Give me five!"

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

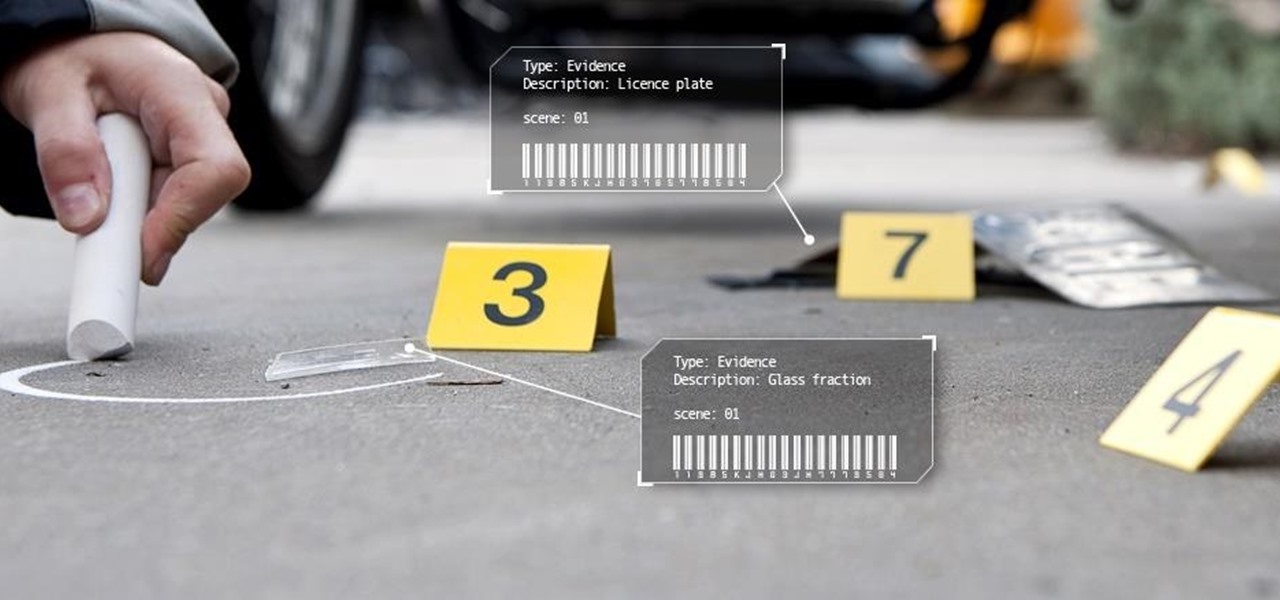
In this tutorial I am going to show you how to change some file metadata, this could be very useful if you want to edit or access a file and remove any evidence of your changes.

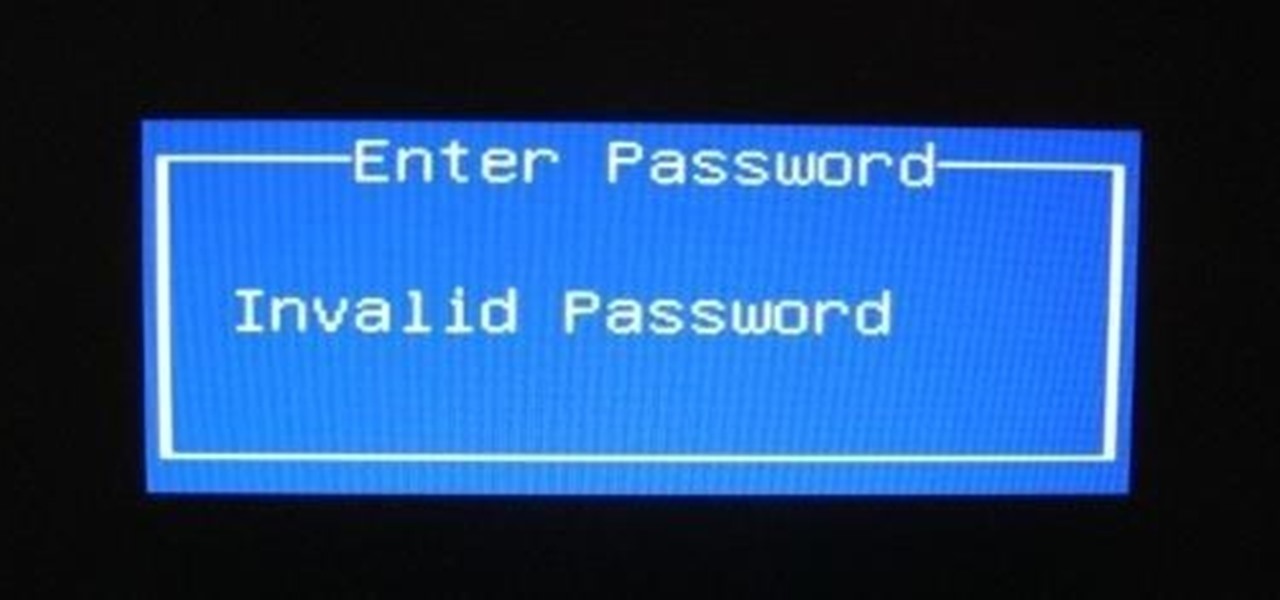
So i ran into a problem few days ago and it seemed to be very annoying one. I got hands on ASUS X55A with broken HDD. So i changed HDD and woo enter bios password. I hit enter and got into bios where uder security tab was shining ADMINISTRATOR PASSWORD INSTALLED. There was no user password but administrator password was set and it led to that i wasnt able to boot anything. At all.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

If you're the de facto tech support person in your family or circle of friends, you know how frustrating it can be to have to hold someone's hand and walk them through every troubleshooting step. Luckily, several options now exist for you to remotely access a Mac or Windows PC, which effectively skips the middle man and lets you get straight to fixing the issue yourself.

One of the most rewarding things about jailbreaking is theming. Unlike Android, iOS doesn't allow you to make small changes to certain aspects like the icons or the lock screen, so jailbreaking facilitates the ability to make some of these desired changes happen.

Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done...

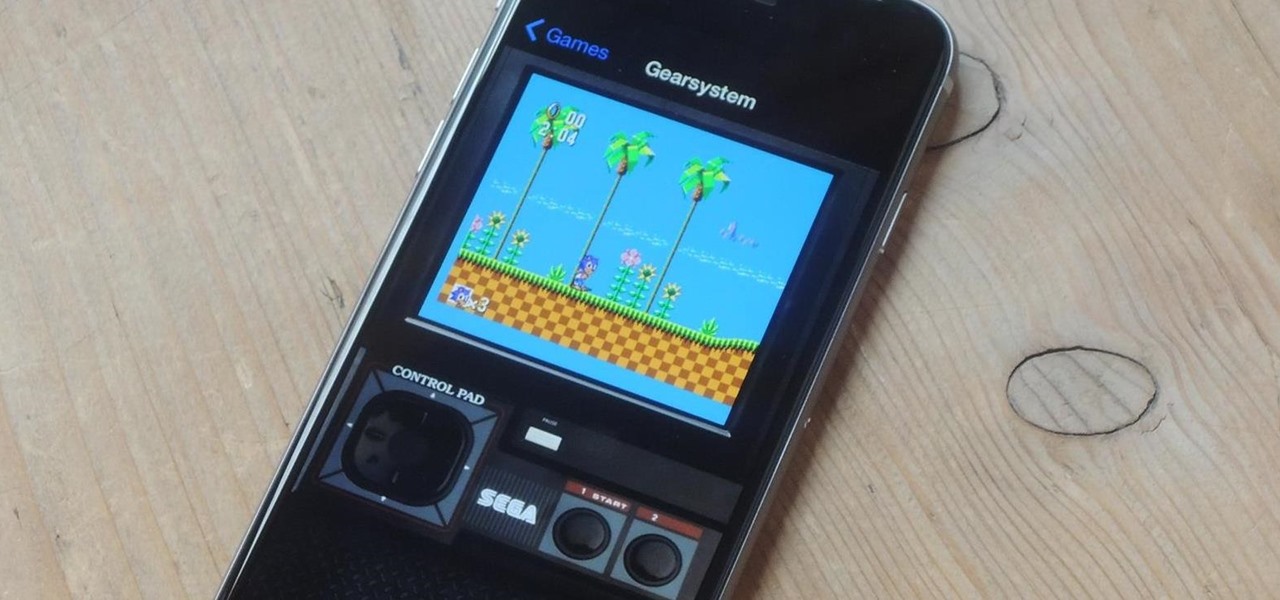
The Master System, more popularly referred to as the Sega Master System, or SMS for short, is a video game console that was released in the mid-1980's as a direct competitor to the original Nintendo (NES).

A lot of people rely on the date on the packaging to tell them when food has gone bad, even with eggs, but the sell-by dates are often somewhat arbitrary and are not expiration dates. If you've been tossing your eggs based on the dates on your carton—you could be wasting perfectly good food.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

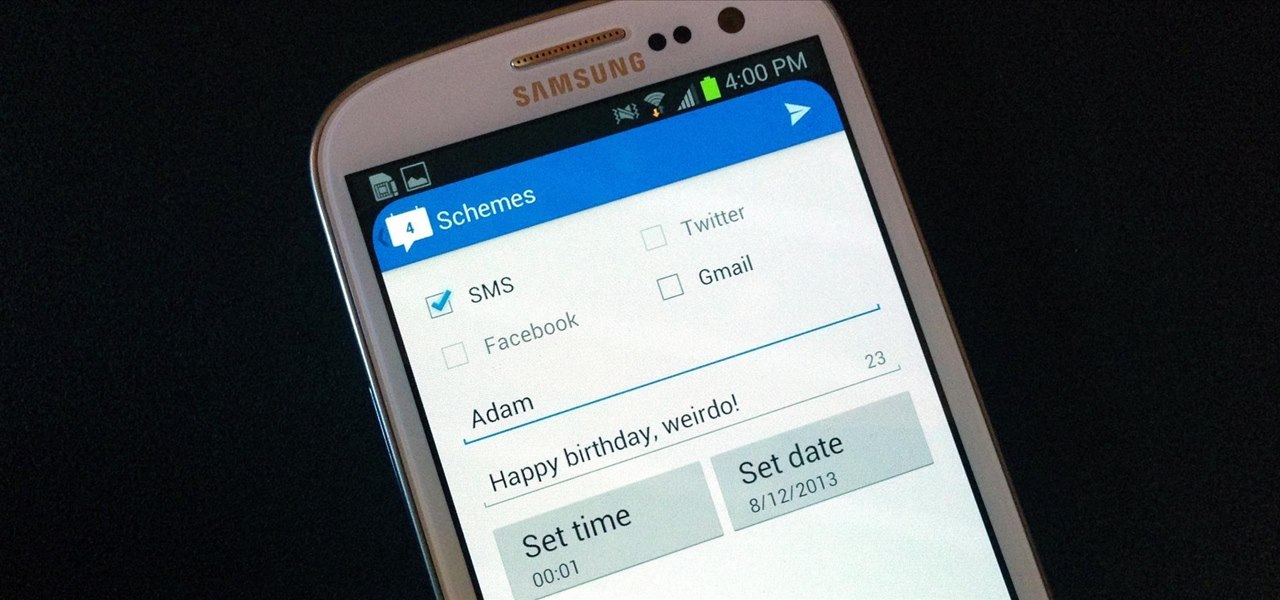
I'm sorry your mom hates you now, but it's pretty hard to forgive someone who forgets to say "Happy Mother's Day." Your poor ole ma could've spent anywhere from 10 to 20 hours popping you out, so the least you could do is set aside two minutes every year to say thanks. If you live to be 90 years old, that's only 3 hours over your entire lifetime!

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

Skype is a great way to stay in contact with friends and family over the internet, and people tend to share a lot in their chats, so why not try and find a way to hack it! Once a Skype account is hacked, you can view all conversations within the last three months, see how long each video call was, and even access files that were shared through chat.

Want to hand out lollipops to your kid's class for Valentine's Day? Then don't just phone it in by scouring the shelves at Target the night before for some Dora the Explorer paper valentines that you'll tape to the lollipops.

After you purchase your first car in Gran Turismo 5 on the PlayStation 3, you'll unlock the National B License Tests. The first one (B-1) is a stopping challenge, and if you want to learn how to get the gold trophy, this video gives a perfect example of how to get it.

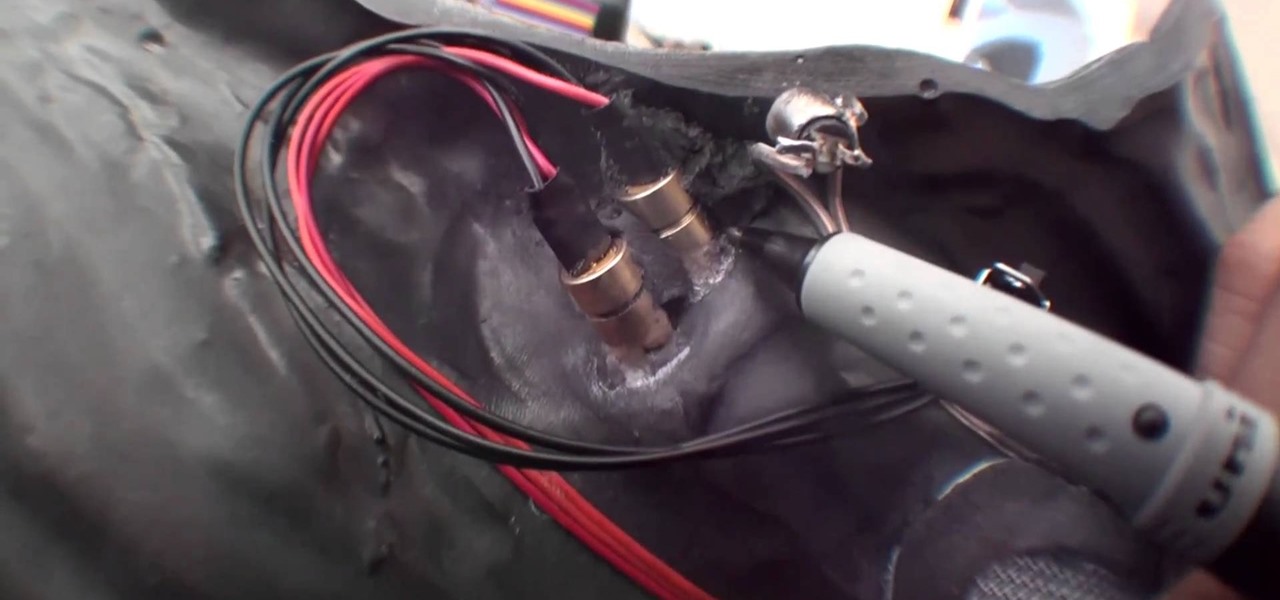
Going for a Predator outfit for Halloween or as a cameo in your film, you want to try to get as close to the real thing as possible. In this video you will learn how to perfectly align LED lights to create the targeting lights that the predator uses for its canon with a quick tutorial!