Pisces can be hard to figure out, but here are some clues. To figure out a Pisces you will need an interest in the entertainment field, a strong personality, and a reassuring nature. Learn how to use astrology advice in dating, by watching this how-to dating video. Pick up tips on making a relationship with a Pisces work.

In this free video exercise lesson, you'll learn a popular variant on the push-up, one designed to target your triceps. With pushups, as with any body-sculpting exercise, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. For more information, and to get started using this exercise yourself, watch this handy home-fitness how-to.
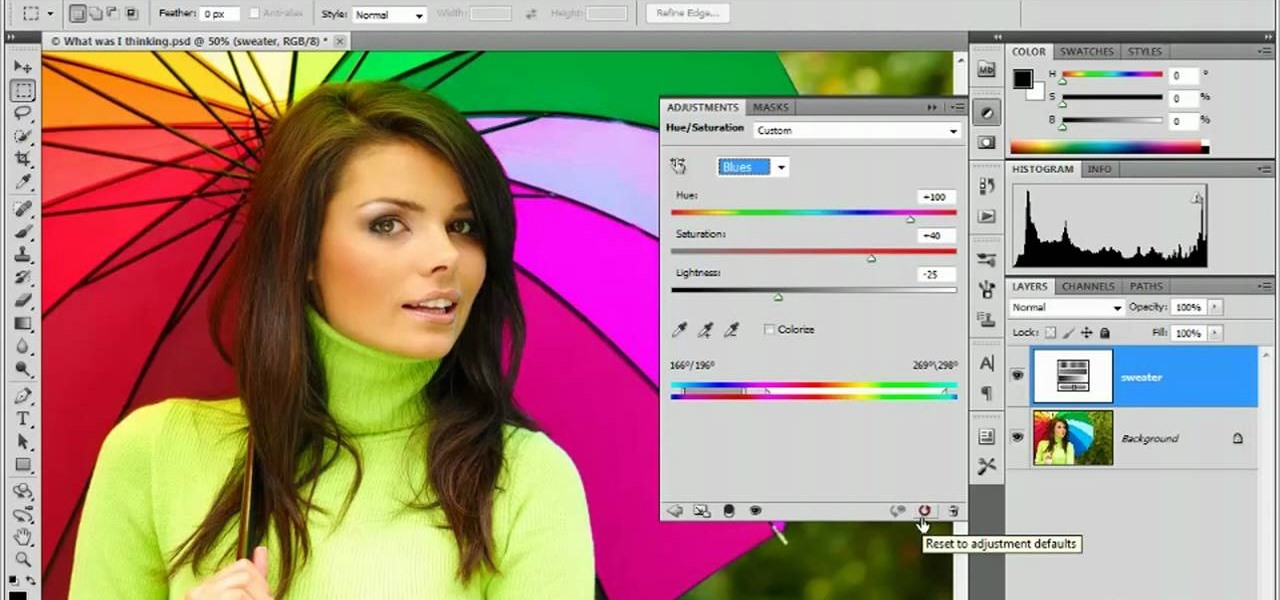
Learn how to use the Target Adjustment feature in Adobe Photoshop CS5. Whether you're new to Adobe's popular image editing software or a seasoned graphic design professional just looking to better acquaint yourself with the unique features of Photoshop CS5, you're sure to find something of value in this free video tutorial.

This video explains how to throw a football like a quarterback. With your elbows bent at a 90-degree angle, hold the ball in front of your chest with the fingers of your throwing hand across the laces of the football.

If you've been dating for a while and have finally met someone you want to have a serious relationship with, congratulations. The only problem is now you have to break it off with the other people that you've been dating. Fortunately, this video will teach you how to do just that.

The beach can often be the perfect setting to get a date with a pretty girl. Follow these dating tips to ask out a girl you like! Learn the right flirting techniques to become a beach pickup pro.

Are you afraid that your dating life is over now that you're older? Whatever your reason for being single at the age of 65 and up, know that you're not alone! In this video, you'll get some fabulous tips and advice from relationship expert Donna Barnes on the process of dating at a mature age.

More and more people are finding love in people they met on the internet, but meeting someone you know online for the first time in person can be stressful and even dangerous. Watch this video for tips on planning a fun, safe first date with someone you've met online.

This instructional dating video demonstrates five of the worst possible ways to kiss someone. There are many ways to kiss a person that can be every enjoyable; like a romantic French kiss, a smooch, or a peck on the cheek. Pay attention to these kissing tips to avoid a dating disaster.

Asking a girl out on a date can be daunting. But with a positive attitude and a little preparation, you’ll soon be wooing the girl—or girls—of your dreams. Watch and learn how easy it is to ask girls out.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Department store chain Target is the latest retailer to offer an augmented reality cosmetics app for customers to virtually try on lipstick.

This video will show how to target your facebook post for a specific audience. With this tutorial video you could target a set of audience who has interest about the post.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

It's a real challenge to create exploding targets that can be set off by low velocity projectiles, yet remain safe to handle without risk of ignition during construction.

In this tutorial, we learn how to unlock the Tank Dropper achievement in Halo 3. This is an easy achievement that you will do when you first start out in the level. This is where you have to drop a tank onto someone and kill them. To do this, you need to stand up on a higher area and find your target. Once you do this, you will be able to grab the tank and then drop it onto the target you have found. After this, you will get the achievement and you will be able to continue on. If you miss, ju...

In this video we are shown a workout that targets your stomach and helps you to lose belly fat and tighten your lower abs.

Take a look at this instructional video and learn how to fit a projected image onto a target surface with Johnny Chung from Carnegie Mellon University. Typically, you'd need to use a screen to be directly in front of the projector and at a very specific orientation to get an undistorted image. What this tutorial is trying to accomplish is to place a screen at any location that is convenient and then calibrate the projector onto the target surface. This technique is used to automatically disco...

The object is to pass to ball between the cones in as few shots as possible, watch and learn how to do this target passing soccer drill.

All-American Skeet Champion Todd Bender explains the safety "does and don'ts" of shooting clay targets. He shows how everyone in the family can enjoy the game and still use proper gun handling techniques.

Whenever deciding to use fields in FileMaker Pro 10, some fields require special handling like the date field. Date field is able to store any date between 1/1/0001 to 12/31/4000. It stores dates in the form of whole numbers. Now, to create a date field, it shows at the bottom of your data and date can be stored. The format of the date can also be changed. One can add dates as well as get the number of days elapsed. This is quite flexible in terms of format as well as keeping records.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Are you sitting alone on a Friday night wondering why you haven't met Mr. Right yet? Well that may be your problem right there - you're just sitting and not actually putting yourself out there! If you're usually super busy at work and other commitments, then you're probably dreading the thought.

If the only way you know how to show a girl you dig her at the movie is the old "yawn and lean your arm over her shoulder" move, then you're clearly not getting any. When you're taking a girl out for a date at the movies, there's a fine line to be drawn between scary and creepy (fondling her a wee bit too soon) and just boring (sweaty palms, not approaching her at all). So how do you walk that fine line from first date to second date?

In this video, Dan and Jennifer will teach you how to be safe while trying to meet girls or date online. Learn tips and tricks to avoid common scams such as identity theft and fraud, as well as things to look out for and early warning signs that your potential lover may not be all she says she is. Dan and Jennifer will also show you how to watch out for one of the most common scams online: "cam girls". Don't fall for that fake girl that acts like she's totally into you but really just wants y...

Life and dating coach Donna Barnes discusses dating if you're over 65. There are a lot of people out there looking for companionship, and just because you are over a certain age does not mean there isn't someone for you! Try to find places that arrange activities for seniors, look online and find fun things to do with new people. You don't have to spend your life alone, a lot of people are out there looking to meet someone like you.

We all want to know how to make a girl fall in love with us. If you can't do that then at least how to keep her interested. Vanae gives some dating advice to guys. It's also great for guys who are already dating or in a relationship.

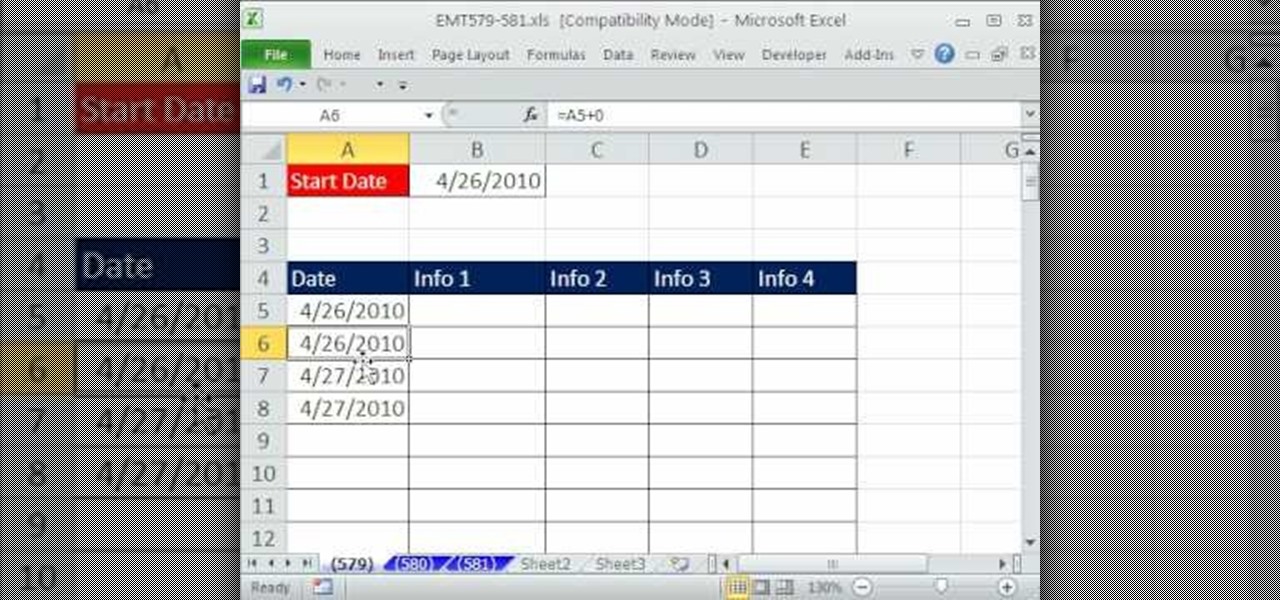
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 579th installment in their series of digital spreadsheet magic tricks, you'll learn how to use the MOD function and date math to create a column of dates where each successive date is repeated twice.

In Morocco, dates are a very ritualistic food during Ramadan, the month during which Muslims fast from sunrise to sundown. During Ramadan, Muslims ask for forgiveness from past sins and ask for guidance in the future. But once sundown hits, it's time to eat up and rejoice.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

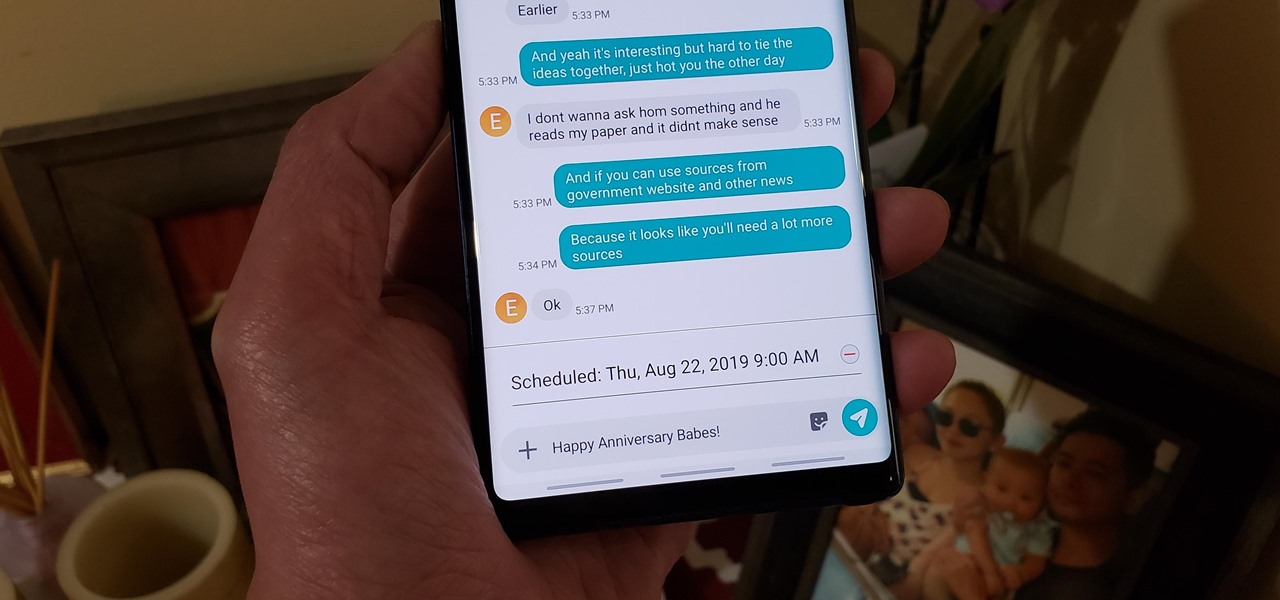
Ideas can hit you out nowhere, but texting loved ones in the wee hours of the morning or during work hours isn't always ideal, especially if they've muted their notifications. So you'll want to send a message at a better time to ensure it gets the attention it deserves. Samsung Messages lets you do just that by scheduling messages to send at a later date.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.