If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Compared to the original AirPods, Apple's second-generation AirPods have better battery life, Hey Siri support, a more stable connection, faster switching between devices and call connections, less latency for gaming, and an optional Wireless Charging Case. If you plan on preordering the new model, you might want to skip the Apple Store and opt for Amazon instead to get it at your door quicker.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

While it has been slower to arrive than a walker limping through thick Georgia mud, location-based augmented reality game Walking Dead: Our World finally has a confirmed launch date: July 12.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

Thanks to its advanced cameras, the Galaxy S9 can capture videos at an astonishing 960 frames per second (fps). To put it in perspective, you now have you the ability to record the world around you in ways that previously required expensive professional camera equipment. And that's just the tip of the iceberg.

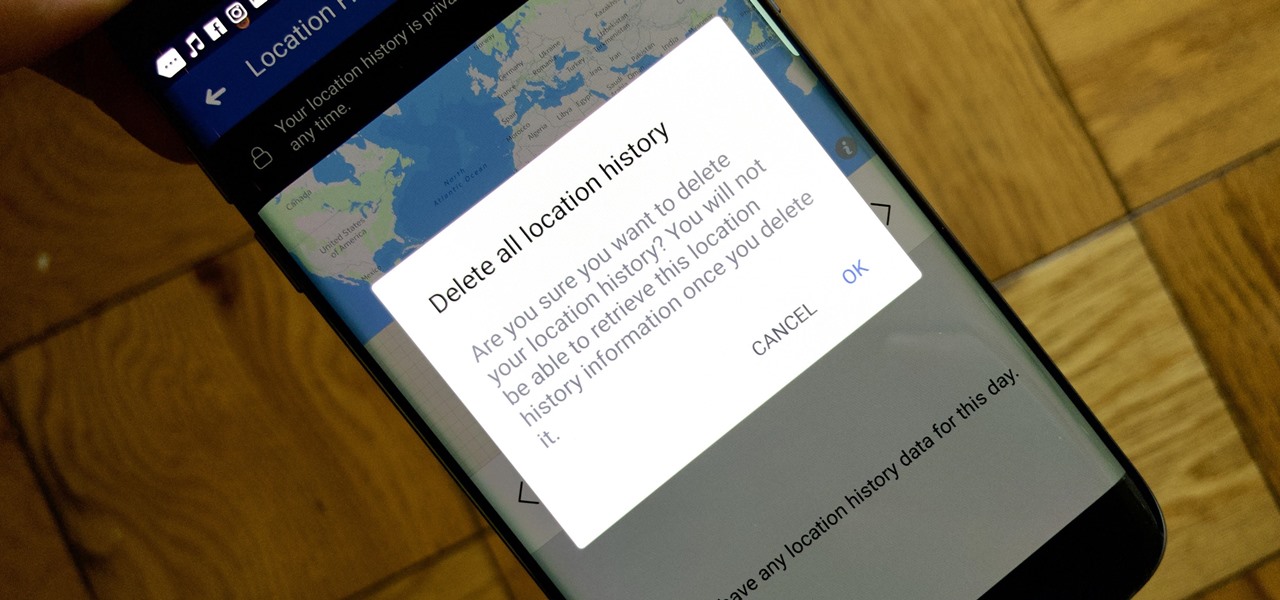
Facebook's shadiness when it comes to user privacy has never been much of a secret. The Cambridge Analytica scandal, however, has thrown the company and its practices into the limelight, with users taking their data more seriously than ever. If you're one of those users, you might want to check your "Location History" to see if and how Facebook's kept tabs on your whereabouts.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

Stop me if you've heard this one before: scan an image with your iPhone's camera and augmented reality content shows up.

The Sony Xperia XZ Premium brought 4K HDR to a Sony flagship along with some competitive internals, while the Xz1 brought some powerful specs in a more midrange, traditional form factor. While it only makes sense to be excited about what's coming next, Sony has yet to show us the XZ2. For now, we need to stick to the rumor mill. Thankfully, the rumor mill is a fun place to be.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

Black Friday is fast approaching, and just like every other day-after-Thanksgiving, there will be too many tech deals you won't want to pass up. If you've been saving up all year just for this sometimes-chaotic shopping holiday, we'll help you figure out the best tech sales to take advantage of and when, whether it's Black Thursday, Black Friday, or Black Friday weekend.

The first wave of iPhone X preorders, the ones with a delivery date of Nov. 3, sold out in ten minutes. You can still preorder one and skip the lines next week at Apple Stores across the country, but if you want that bezel-less beauty in your hands ASAP, brick and mortar might be the way to go.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Antibiotics are one of our main weapons against infections. The problem is that many bacteria are becoming resistant to most of the antibiotics we use to treat them, and those 'superbugs' have created an urgent threat to our global health. A research group found a new way to hit a well known bacterial target and have developed a drug to hit it.

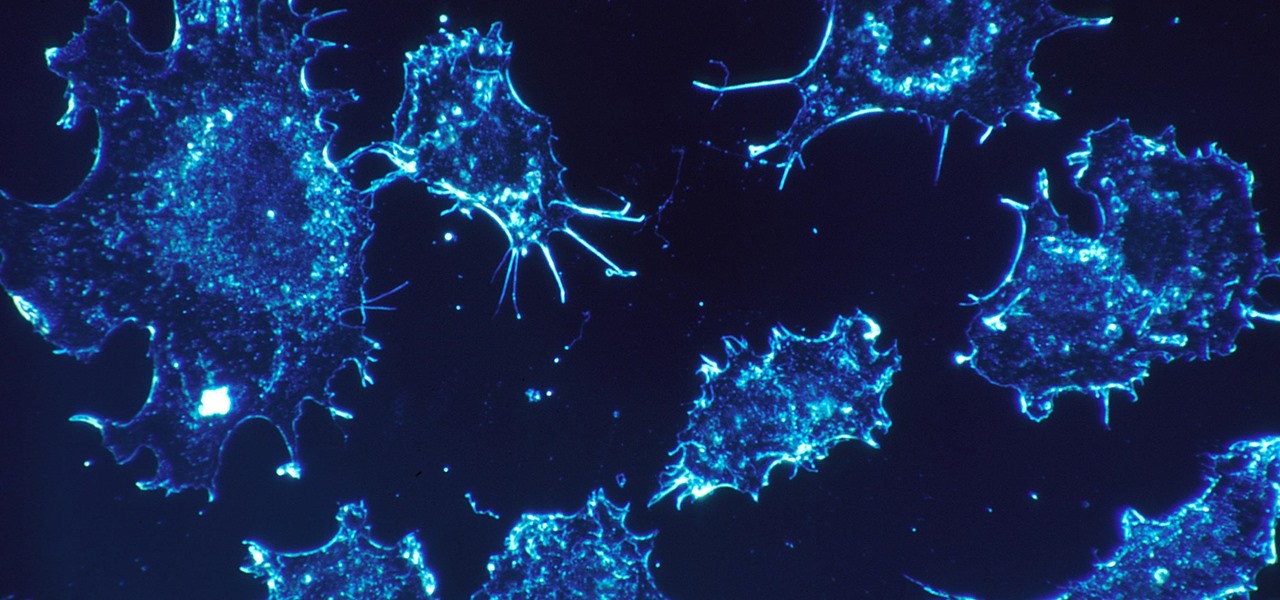
As our cells age, they eventually mature and die. As they die, they alert nearby cells to grow and multiply to replace them. Using a special imaging process that combines video and microscopy, scientists have observed the cellular communication between dying and neighboring cells for the first time, and think they may be able to use their new-found information against cancer cells, whose damaged genomes let them escape the normal dying process.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Super Mario Run was released for iOS on December 15, 2016. Even though it debuted as a "free" app, almost all of the playable content was hidden behind a ridiculous $10 unlocking package. Despite coming with such a hefty price tag and receiving a two-star rating on the day of its release for iOS, Android users are still very much interested in giving this game a whirl.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Video: . This Video will Show you how to Season and Clean

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

Here is a video that shows 90 seconds that could save your life. How to actually MAKE A FIRE with a lens, rather than just burning a hole in a leaf. (Or frying ants, which seems to be the other thing that kids like to do with magnifying glasses.)

90 seconds that could save your life. How to actually MAKE A FIRE with a lens, rather than just burning a hole in a leaf. (Or frying ants, which seems to be the other thing that kids like to do with magnifying glasses.) By forming your target material into an efficient ball, you will be able to start a fire even with very small lenses. Like less than an inch across small. The finer the individual fibres, and the more densely they are packed, the more effective is your ball of smigtin (smoulde...

Sony is ready to get into the micro-console gaming fight, with its PlayStation TV set to debut this fall.

Last year, Todd Blatt ran a Kickstarter campaign to make 3D-printed accessories for Google Glass, and has turned it into a company: GlassKap.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

Try making your own granola bars instead of buying them at the grocery store. You could just surprises yourself. They may taste better. Start out by trying this recipe for peanut butter and banana nut granola bars. They're made of all natural and healthy ingredients, plus they're a cinch to whip up!

In this video, couples issues-expert Dr. Karen Stewart discusses how to remain friends with someone after having dated them. For more information, and to learn more about staying friends with ex partners, watch this helpful video guide from the folks at Mahalo.

Got a special occasion coming up that requires a necktie? If your knot-tying skills are out-of-date, check out this video for a refresher on tying a Double Windsor, also known as the Full Windsor knot. This kind of knot gives you a much fuller knot than the four-in-hand or the Half-Windsor. It's the way to go, but takes a little more effort.

Oh dang it! You got sprayed by a skunk? What will you do now? The smell won't get out of your clothes, and your skin for that matter, and you've got a hot date. This video has the answer, coca-cola. Yea you heard me, watch it and find out!

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...