Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

On Wednesday, Microsoft launched a chatbot on social media that learns from conversation, and trolls quickly taught it how to be a shameless, Nazi-loving bigot. Oh Internet, an opportunity for a Hitler joke never slips past you, does it? This Is Why We Can't Have Nice Things

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

Hello All, So to recap in part 1 I went through setting up the dchp server. Part 2 detailed the bash script. Now in part 3 I will post the entire bash script. I am doing this in its own post because Part 2 is just way to much info on one post IMO.

If you're entirely new to smartphones, Android's share menu can seem like a foreign concept at first glance. In reality, it's one of Android's most central and unique features, and with a little experience, it can make your smartphone a lot easier to use.

Tired of being rejected? Not getting as many dates as you hoped for? Having a hard time getting the ladies to notice you? We've all been there before. This is a step by step guide to make sure you get the girl 100% of the time

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Video: . Learn how to make an origami mini book tutorial.

Do you have a friend that likes to show off, a friend that is always wearing nice clothes and getting all the ladies? How about you try this prank on him...

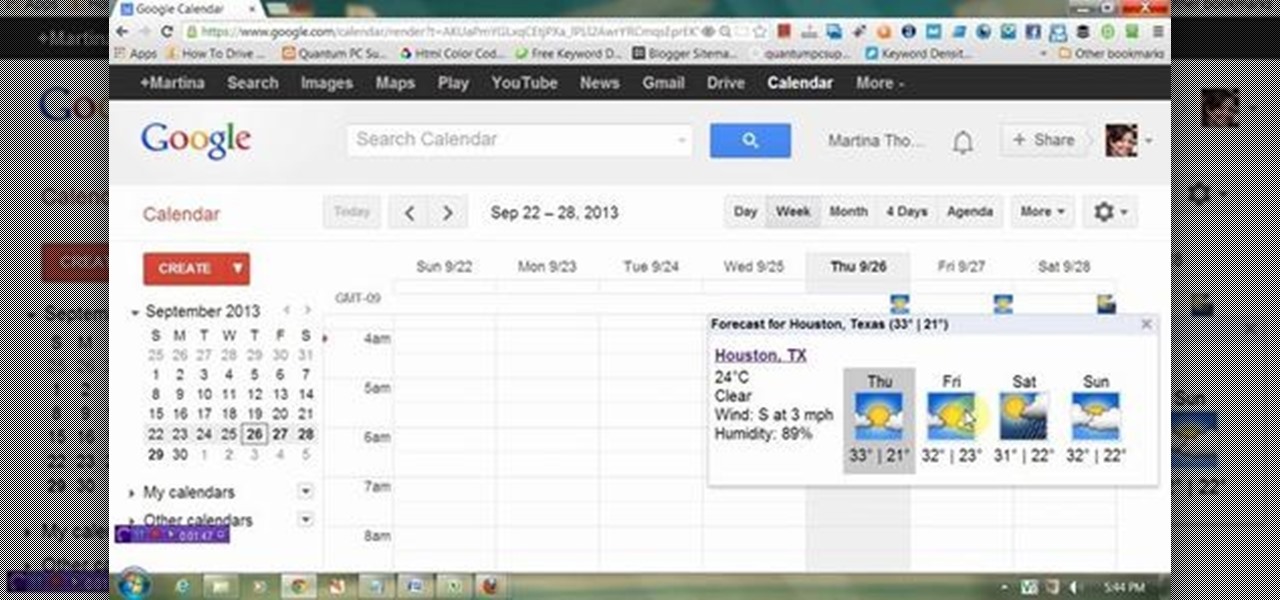
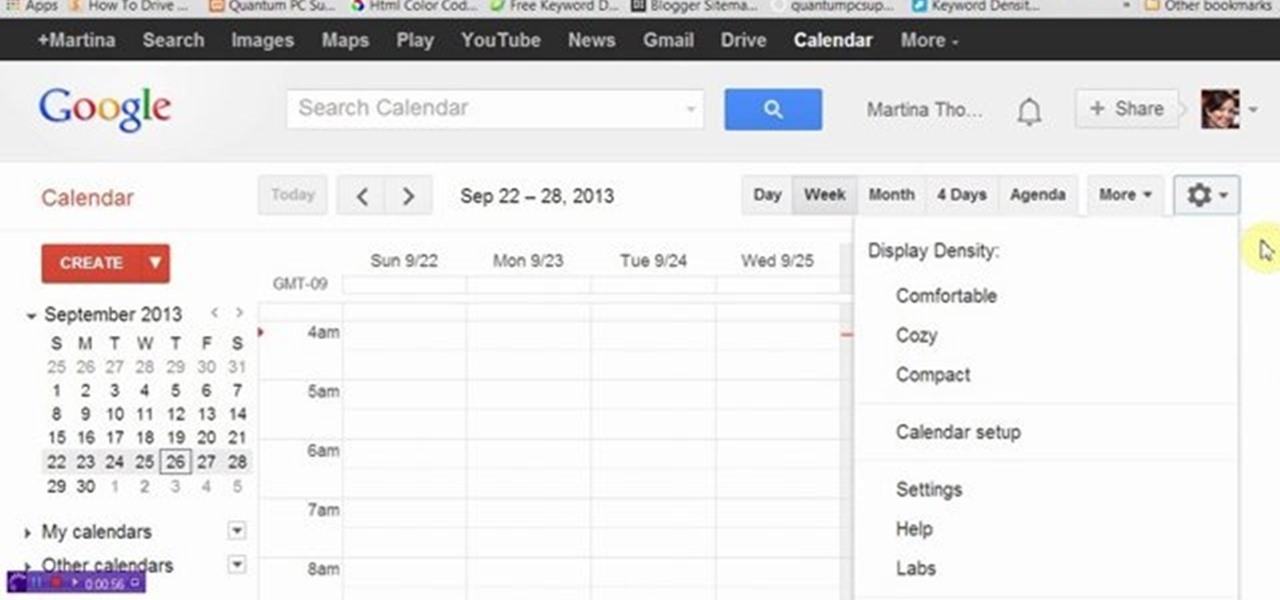
This video will show you how to display weather information about a particular place in Google calendar. You could see the present date weather and coming 3 day forecasting. So enjoy your Google calendar.

This video will provide an idea how to display weather information of a particular place in Google calendar. You could see the present date weather and coming 3 days forecasting. Watch the video carefully and employ the technique.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

A comedic look at making an impressive italian style dinner. Nominated for Best Comedy at UCF Campus Movie Fest.

Welcome to this short and easy tutorial on hacking and DDosing (is that even a word I don't know) anyways lets get started

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.

i can guess exact date and month of your birth day.bet and win with anyone using this trick .it never fails.you can attract your colleagues and classmates with this trick.

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

Featuring intensely competitive multiplayer action, Offensive Combat enables players to harness their skills and use their creativity and ingenuity to win the ultimate mash-up of first-person shooters. The browser version and the mobile/tablet versions of the game are interconnected, and work together unlike any game before.

As if you needed another reason to lock down your Facebook profile, the company's sketchy new partnership with data mining firm Datalogix is geared towards giving advertisers more information on what you're doing—even when you're not online. It's just not enough that they can target ads based on your preferences, now they want to know how those ads are influencing your buying habits in the real world.

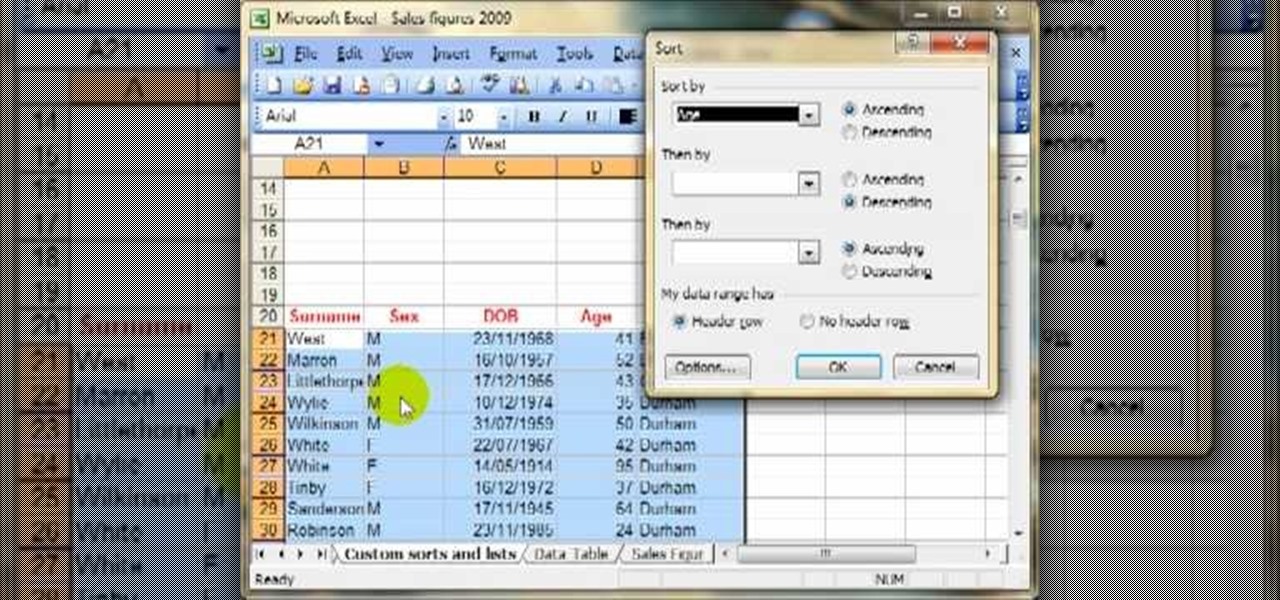
Today we are going to learn how to sort data in a Microsoft Excel 2003 spread sheet. We will go over single column and multiple column sorting. In a single column sort you may high light the data or just click on any cell in the column. Once the data is selected look for the sort icons just under the menu bars. There is a sort ascending and sort descending icon. Click on the icon and Excel will sort the list. When sorting multiple columns the data must be in columns next to each other. If the...

To start with you have to write the author's name, with the last name entered first followed by first name and then the period. Title of the article should be in quotation marks. Do not use italic format. Title of the actual journal must be written. After this there is a series of numbers the volume number, issue, year, pages number separated by a colon. Don’t write 'p' for pages as the number itself is a standard for it. Write the period and also the dates.

Not sure how to plan a funeral? A well-planned memorial service honors the deceased and comforts those who are grieving. Learn what steps to take when planning a funeral in this how-to video.

Weird gifts from friends and family aren't the only things you can score on your birthday. With a little advance planning, you can get lots of freebies.

When you need an eye-catching boutonniere for a special occasion, you don't have to spend a fortune at the florist. Make your own!

No need to make a bad situation worse when running into an ex boyfriend or girlfriend. There is no need to be petty or spiteful when keeping to a nice yet vague conversation will ultimately leave you looking like a real class act.

Before iOS 14, the date and time picker on the iPhone had been a scroll wheel for a very long time. Whether you loved or hated it, it was like second nature to use it. Now, you need to use a calendar and your keyboard to input dates and times. If you got so used to the old way and find the new method jarring, there's a trick to getting the scrolling date and time selector back.

It's finally here. After years of rumors and speculation, Apple unveiled the new iPhone SE on April 15. While it doesn't have a 4-inch display like the original SE, it's the smallest new iPhone you can buy today, with the chipset of the iPhone 11, 11 Pro, and 11 Pro Max. So, when can you get your hands on it?

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

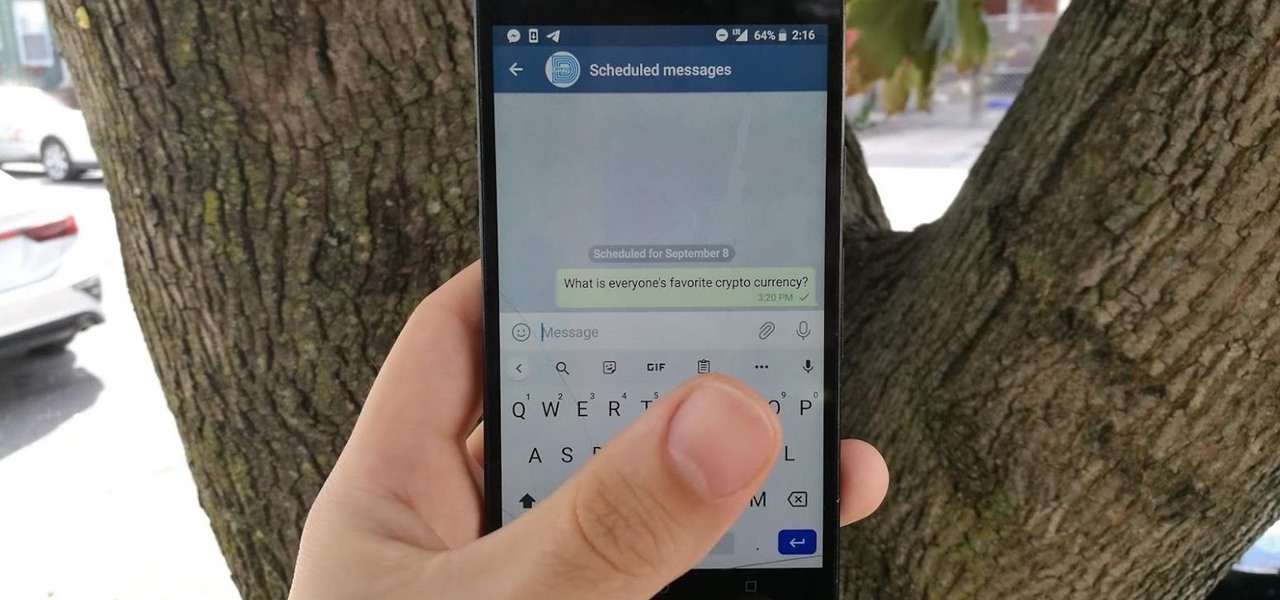
Sometimes you may need to send a message out at a specific time. Say a thought strikes you late at night, but you don't want to wake anyone up. You could do this by waiting to sending it at your desired time — or, you could schedule your message at a precise time.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

As the stigma of online dating fades and swiping potential suitors on your phone becomes the new norm, one very real issue that you may have to deal with is catfishing: the act of being deceived by a fictional online persona. Although dating apps do their best to weed out fake accounts, a few of them slip through the cracks and take advantage of innocent people just looking for a connection.

Spotify integration in Bumble has been around for a few years now, allowing prospective matches to view the artists you listen to the most on the popular music streaming service. It definitely helps people connect, but sadly, it doesn't work as well as it should because it rarely updates to show what you're listening to now.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

As we predicted earlier this week, the focus has already begun to move from Magic Leap back onto Apple's rumored augmented reality smartglasses. The latest credible whispers come from none other than longtime Apple-focused analyst Ming-Chi Kuo.