Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Razer just made a big step into the mobile industry by releasing an absolute beast of a smartphone. The gaming-centric Razer Phone tries to provide the best experience for its target audience: Gamers. With that in mind, they created a top-tier device with some of the best specs available on Android. But how does it compare to the current spec champion, the Samsung Galaxy Note 8?

It seems that mobile app developers are constantly coming up with new ideas to apply augmented reality, with Apple's ARKit promising to increase adoption in apps exponentially.

People love sex. They don't love talking about the possible repercussions of sex. And with dating apps such as Tinder, Grindr, and Bumble paving new ways for strangers to talk and have casual hookups, people need to be able to more comfortably have a conversation about sexual health and protection. Luckily, now there's an app for that.

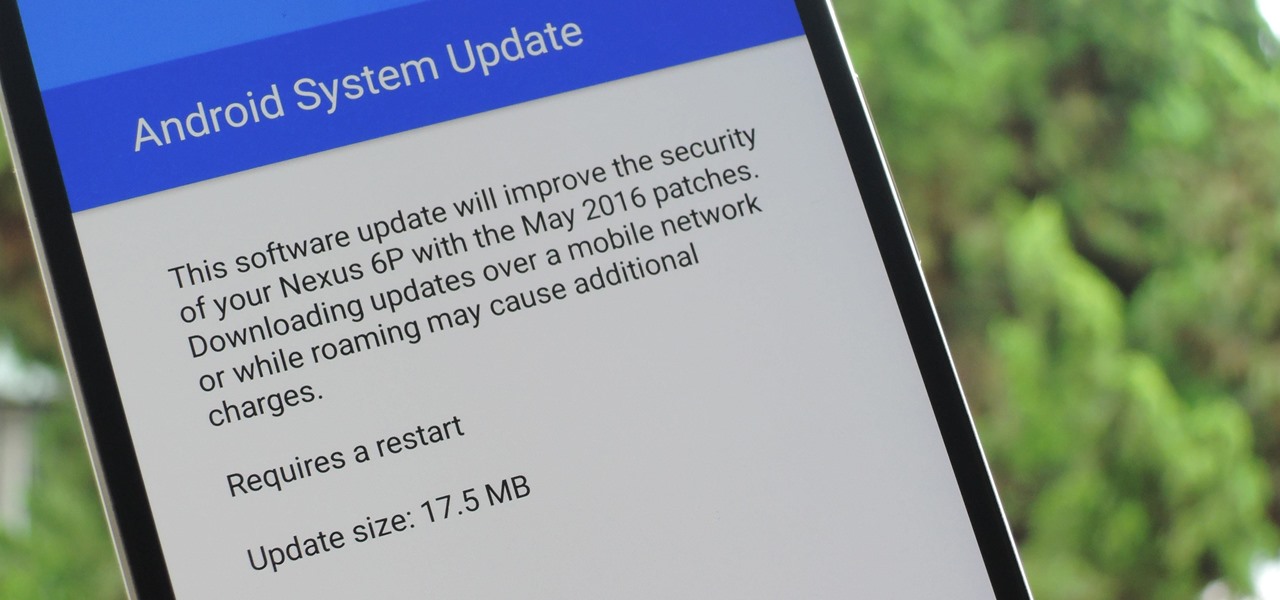
The beauty of Nexus devices is they receive firmware updates faster than any other Android phone, and keep getting updates for years longer than most of the competition. This means that you can always use the great new features that come along with an Android update, and even more importantly, your phone gets monthly security patches to keep hackers and malware at bay.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Apple has once again improved functionality of Siri, their personal voice assistant for iPad and iPhone, in iOS 9—and this update is a big one. You can now use Siri to find photos based on location and date, set up contextual reminders, find your friends and family, and more.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too.

It's been over three months since iOS 7.1 came out, but your wait for jailbreak is now over. If you're still running iOS 7.0 iterations to maintain your jailbreak, you can now finally update to the latest and greatest thanks to a Chinese team of developers, who recently released their untethered jailbreak for Apple devices running iOS 7.1, 7.1.1, and even 7.1.2.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Welcome back, my novice hackers! The worst thing that can happen to any hacker is being detected by a security admin, the security technologies (IDS, firewall, etc.), or a forensic investigator.

A boring work meeting. A conversation with someone you don't like. A date that's going horribly. A run-in with an aggressive and intimidating stranger. These are all situations where you want to flee—and fast.

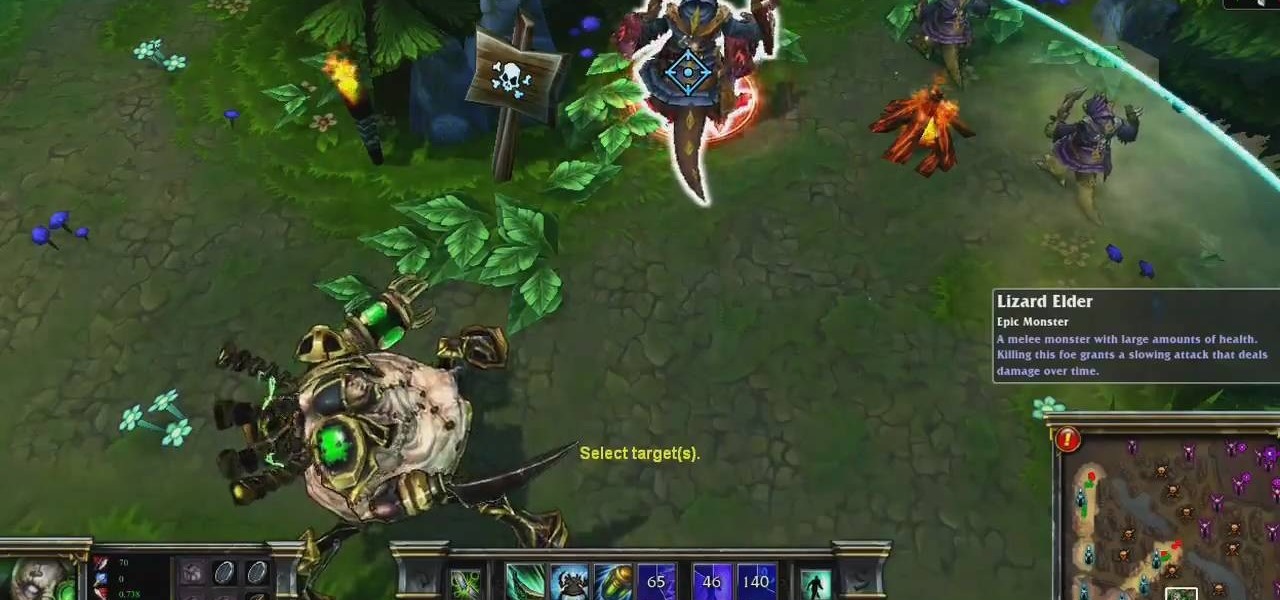
Urgot is a unique champion who can deal out high amounts of damage early in his game, and eventually evolves into a tank/assassin hybrid who can be sent after important enemy targets. Here's a guide for building and leveling Urgot to take advantage of his capabilities to help your whole team.

Lady Gaga is definitely in shape. No one can deny that. But how does she do it? How does pop music's most popular artist stay in perfect shape? How does she get those great looking abs?!?

Shane goes into detail on a specific type of boof in which the paddler comes across the drop with angle and boofs into an eddy.

They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.

Suspect that your bovine (bull, cow) is pregnant. Well, there's only one way to be sure. Put on a plastic glove and insert your hand into the rectum, with your fingers together. See how to find out if your cattle is pregnant with help of this video tutorial.

Well, you've shot one too many compromising photo and it's time to wipe your iPhone photo library. But, for some reason, this isn't the easiest thing to do. Well, with this how-to video, you'll learn how to get rid of those 212 photos of your niece in her sailor suit you thought looked adorable. Those cat climbing photos. Gone. That girl/boy you were recently dating. Bye bye. Delete at will and clear your iPhone photo library.

We love ponytails - for yoga class. They're ridiculously easy to throw together, which is why they're great for on-the-go hair management. But just because the ponytail is a practical, functional look doesn't mean you can't dress it up and wear it to formal occasions like cocktail parties and work.

Valentine's Day is traditionally thought of to be a lover's holiday. You know, the whole Casanova-esque wooing with red roses and chocolates exchanged, romantic dinner dates by candlelight in hopes of Cupid working his magic later on. But Valentine's Day can be just as fun for kids.

Is your wedding date coming up soon? Not to scare you or anything, but a typical wedding costs upwards of 20,000 to hold. This of course includes booking a location, getting all the props, flowers, dress, party favors, etc.

Celebrites make party hopping look so easy. Flitting around from red carpet event to after party to after after party, they always seem to look so flawless in their pictures. But here's a little secret: They have some help from Hollywood's top hairstylists.

When the weather turns cooler and you begin to see the first signs of snow outside, you know it's time to whip out the comfort foods. And there's really nothing better to help you warm up inside than a nice, hearty stew.

Halitosis, or bad breath, unfortunately affects all of us at some point in our lives. And boy, does having bad breath suck. It can make the difference between acing your job interview and making your potential boss step sharply away from you in digust, and can ruin those special first date kisses.

Every girl needs a "go-to" recipe, as it were, for looking good. For every girl this "go-to" is different: One gal may fall back to a red lip and neutral eyes when she wants to look hot with minimal effort, while another may work some magic with her smudge brush to create the perfect smoky eye.

It doesn't have to be summer and 100 degrees outside for you to enjoy a big scoop of ice cream! In fact, you can have ice cream anytime you want with these ice cream-inspired nails.

Beyonce looks like a veritable MGM screen siren in her music video for "Why Don't You Love Me?", pulling of very retro curled hair, WWII bandanas, and and plush red lips. She pulls off a kind of dated that we envy rather than feel distanced from.

In this tutorial, we learn how to express "to be" in Spanish using ser, estar and haber. When expressing forms such as: am, are, was and were you will say "ser" and "estar" in Spanish. The verb "ser" should be conjugated for each of the different tenses that you are using. Often, "ser" is used to ask questions such as: where you are from, what nationality are you, and what things belong to someone. "Ser" is also used to indicate occupation, religion, political party, event locations, date, an...

Taylor Swift looks an awful lot like the princesses she sings about in her rhapsodies about teen angst and finding your white knight. Which means, of course, that she's a makeup artist's dream.

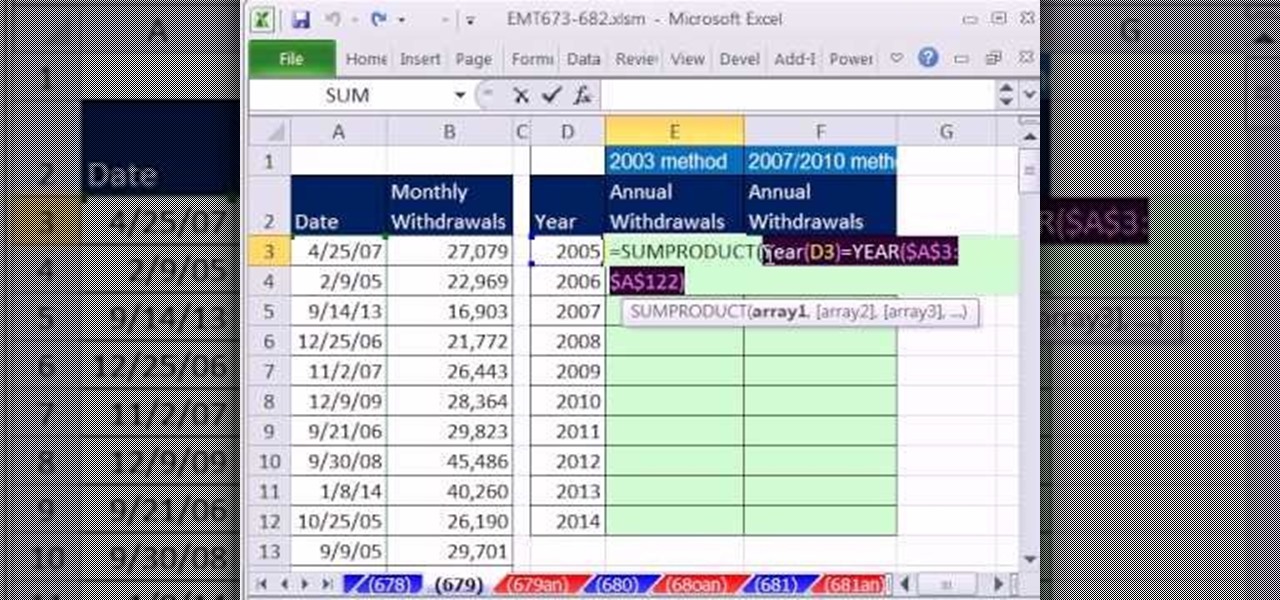
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 679th installment in their series of digital spreadsheet magic tricks, you'll learn how to summarize yearly totals from monthly totals when there Year Criteria is entered as a serial date. See the SUMPRODUCT and SUMIFS functions. Learn about criteria and how to enter it into the SUMIFS functions.

Dessert has pretty bad connotations. After all, starving models and women trying to lose weight are often stereotyped as saying "no" to dessert in an effort to cut calories and not look like a piggy in front of friends (or a handsome date). It's pretty crappy, this world that we live in, with so much good food that's so bad for you tempting our every mealtime.

Urban Decay's new makeup palette, Naked, sold out within minutes of debuting on Sephora and on Urban Decay's website. Why? Well, with eight universally flattering neutrals and four gunmetal gray shades, you can either do a very neutral, daytime look for work or amp up the glam factor with the smokey gray colors for night.