Southwest Yard and Garden featuring John White, Dona Ana County Extension Agent, hosts a 6 minute clip with co-host Master Gardener Valois Pearce both of Dona Ana County, New Mexico host a short web show featuring plants that can easily survive on smaller amounts of water over typical plants. They begin by discussing the full sun Ice Plant, which comes in many species and colors as well as their hardiness, but unfortunately are easy targets for wildlife. They then move onto the Gopher Plant, ...

There comes a time in many tattooed individuals when they want to remove their tattoos. There are a lot of different ways to remove tattoo but they all cause scar. Dr. Neal Schultz explains only laser tattoo removal will not leave a scar and give a cosmetically-superior result. Laser energy is specifically targets the colored pigment of the tattoo so it only damages the colored pigment. It does not damage any of the surrounding skin. When people are treated for tattoos, it can take 8-12 treat...

Dating a man who wants to keep his freedom? - Why does he say he loves you, then? Dating coach Francisco Bujan tells you how to interpret mix messages from men.

In this how-to video, you will learn how to make Cobra-style paper airplane. All you need is a regular piece of paper. This style is useful for hitting targets or flying straight. Fold the paper in half vertically and unfold. Take the top corner of the paper and fold it to the edge of the middle crease. Repeat with the other corner. Take the tip of the center and fold it to the horizontal line created by the folded corners. Make sure you make tight folds. Open it up and make a fold horizontal...
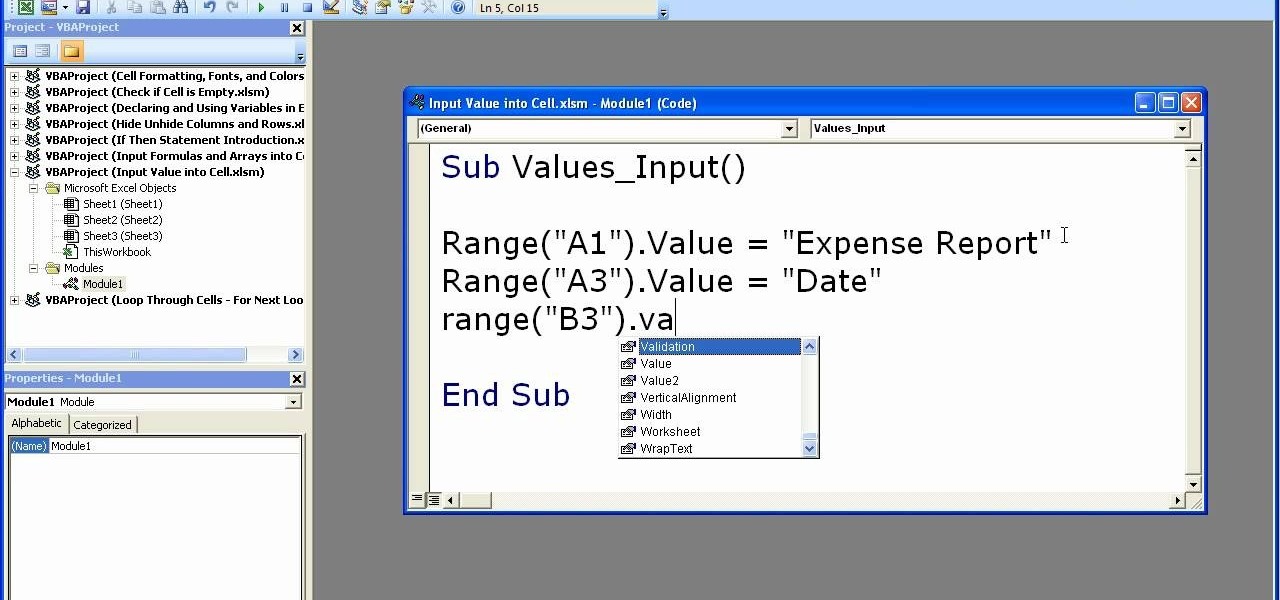
This video shows how to enter values into cells using Excel macros and Visual Basic. This includes a sample Expense Report that is used in this demonstration. In this demonstration, we will create the macro that inputs a title as "Expense Report", Three columns i.e. "Date", "Item" & "Amount", and the summery field as "Total Expenses", as well as the formulas located at the respective cells. Now, we're going to use two keyboard shortcuts i.e. "Alt + F11" to open-up the VBA window and "Alt + F8...

See the angled edge of the blade? This is the bevel angle. Match this to the face of the whetstone. For a clever-like tool like a machete, this should be at a high angle--15 to 25 degrees.

Ladies, it seems to be the trend to wear boyfriend cuts in clothes so here’s a video that will show you how to create a creative super cute and girly top using a guys shirt and tighty-whities. You can wear guy clothing and still look very feminine.

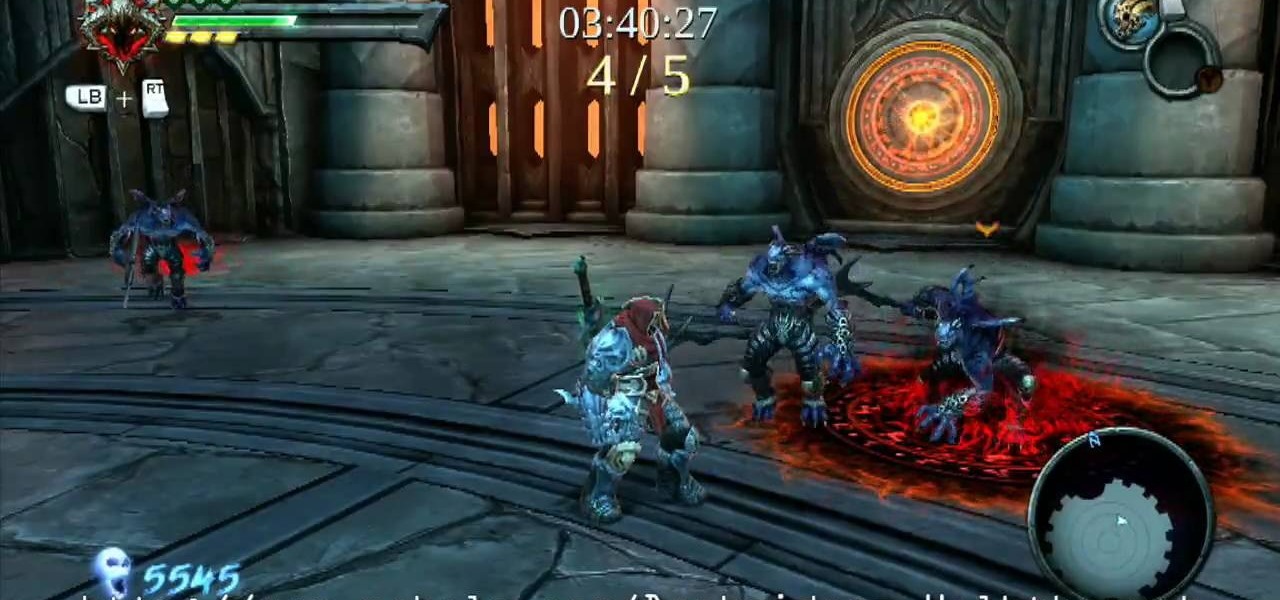
Get ready for one heck of a battle in the Shadow Arena Challenge in the Drowned Pass on the Xbox 360 game Darksiders. You need to enter the Shadow Realm and defeat four portals to free Vulgrim.

You may have to eventually abandon your stealthy approach in this mission on The Saboteur for the Xbox 360. The second mission in Act 2: Better Dying Through Chemistry is when you reach the entrance, there's a gunner behind sandbags by himself. If you take him out quickly and disguise yourself you can actually play this level pretty quietly. There are two basic kinds of targets, the smaller, thinner tanks, and the bigger, darker tanks. The big tanks you can blow with dynamite and as long as y...

Get all of the info on the 15th puzzle, entitled "Guardians", in Assassin's Creed 2. Puzzle wheel: Seemingly every other ring is linked here, so we’ll cut straight to the chase: Turn the third (and fourth) rings right twice, the fifth (and first) right four times, the fourth (and first) right five times, the fifth (and first) left five times and the second left five times. Finally, move the fifth (and second) rings right five times. Image: Another gimme – just move the Assassin logo over the ...

All Things Come to He Who Waits: After parting ways with Leonardo, break into the walled-off area to the northeast and trigger this mission via a waypoint on the parapet walk. After the cut scene, you need to trail a courier that zigs a zagging path through the city. Stay far enough behind him that he doesn't get curious, but also be sure to keep him in your sights. If he gets separated from you by a wall, a countdown timer hurries you to catch back up.

Wolves in Sheep's Clothing: So, yes, that means there are more than one wolf in sheep's clothing. Hit the map marker and this mission will immediately kick off. You need to check the nearby street in front of a large, regal building to find a certain somebody. The area is marked green on your map, so don't waste time anywhere else. Just turn on eagle vision and, once you've spotted the target, a cut scene will take over.

Arivederci: Or is that Arrivederci? This mission won't take long. As long as your notoriety is at zero (and it has to be), this mission is a piece of cake. You have to escort Ezio's mother and sister across town to the city's exit. The city is temporarily packed with guards, but they'll pay you no mind, even if you run. Just avoid bumping into guards and you'll be a-okay.

Family Heirloom: Find the precious family peice passed down generation to generation. Go back to Giovanni's room and use eagle vision to locate the hidden door. Okay, it's not really very hidden. Open the door and step into the secret room. Open up the chest inside to get a snazzy new outfit, plus a useful sword.

Create lasting memories by organizing a well-planned family reunion. This video will show you how to organize a family reunion.

People like Ralphige and The Jerky Boys have elevated prank phone calls to an art. Here’s how you can get in on the fun.

Work out the butt and thighs with press exercises. Learn about butt and thigh presses in this dumbbell fitness video. Take action: place feet higher or lower depending on target area, bring thighs to chest without rolling hips, but do not lock knees. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting an...

Learn how to do incline barbell presses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do wide push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

How to unlock everything - all of the hidden characters and stages - Super Smash Bros Brawl (SSBB) for the Nintendo wii.

You use your iPhone's Reminders app to keep track of everything from grocery lists to the day's most important tasks. Over recent iOS updates, Apple has added tools to Reminders to make it even more powerful, like assigning tasks to other people and setting location-based reminders. Now there's another great update, and it gives you the ability to sort your lists.

While conducting an OSINT investigation, it's important to be able to pull in information based on any clue you uncover. In particular, license plate information can turn up everywhere, from photos to live data to on your own street. You could use that data to find the VIN, see if a Tinder date has hit anyone, find out who's blocking your driveway, and so on. Skiptracer can help get the ball rolling.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

As the demand for realistic volumetric video for AR experiences begins to grow (along with the available facilities and services for capturing it), researchers at Google have figured out how to improve upon the format.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

The updated Reminders app in iOS 13 makes productivity a little bit more seamless on the iPhone. The overhauled user interface makes it easier to find your reminders, the new Messages integration makes it simpler to remember to-dos regarding your contacts, and the new toolbar provides shortcuts to tasks that were once clunky and confusing.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

All of the the tech industry giants, including Apple, Facebook, and Google, are working on new smartglasses and/or AR headsets, but this week, Google took a major step forward with gesture recognition technology that could make its way into AR wearables, posing a threat to Leap Motion and its hand-tracking controllers.

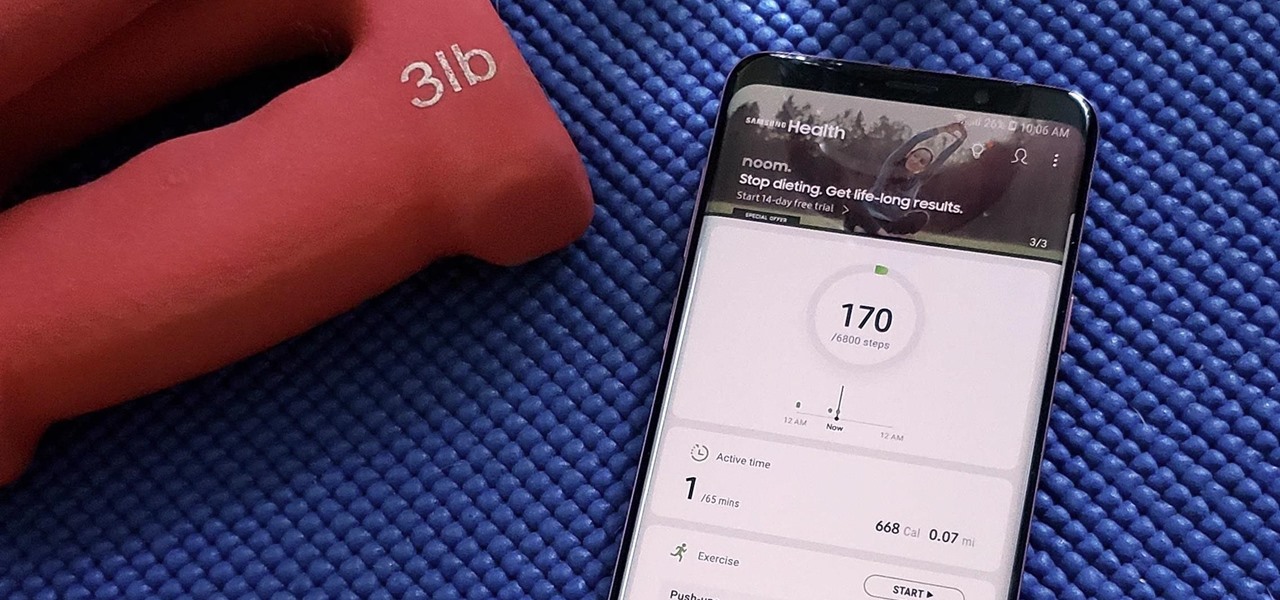
Samsung Health has become one of the most comprehensive wellness apps thanks to features that cover everything from step counting to nutrition logging and symptom diagnosis. But because the app has so much to offer, it can be easy to overlook some smaller, but useful features.

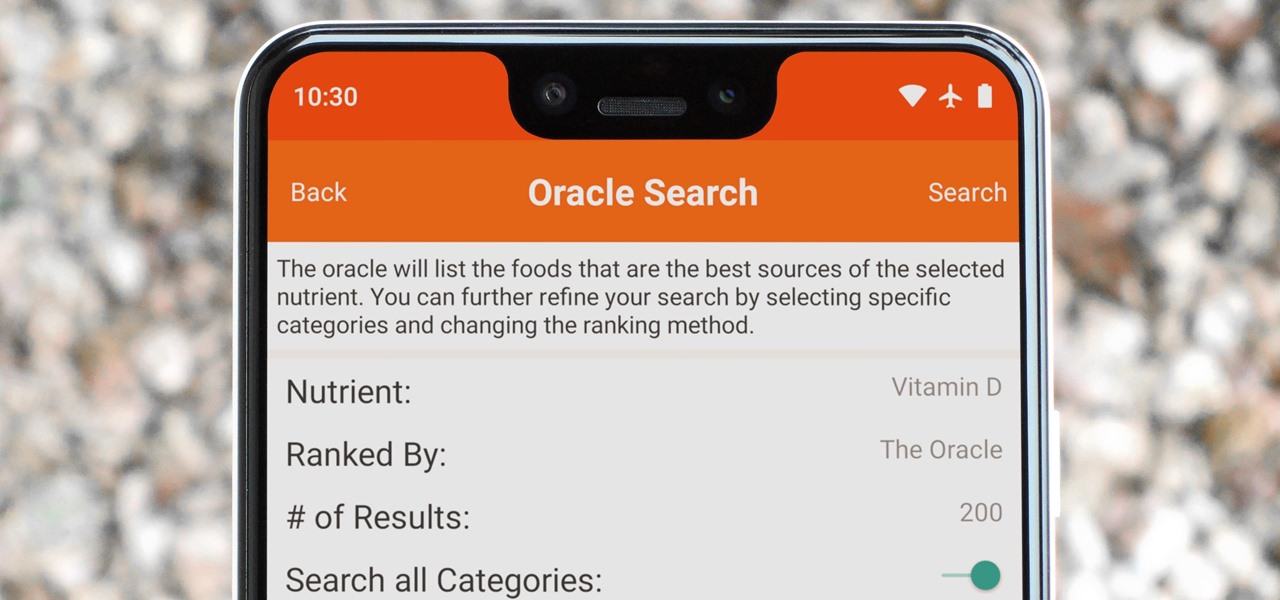
Micronutrients are essential to our health. Unfortunately, many of us aren't getting enough of each nutrient from our diets. It isn't that the food we're eating is bad, but rather we are not eating enough of the right food to get our recommended daily allowance. But with the help of a micronutrient tracker, we can change this.

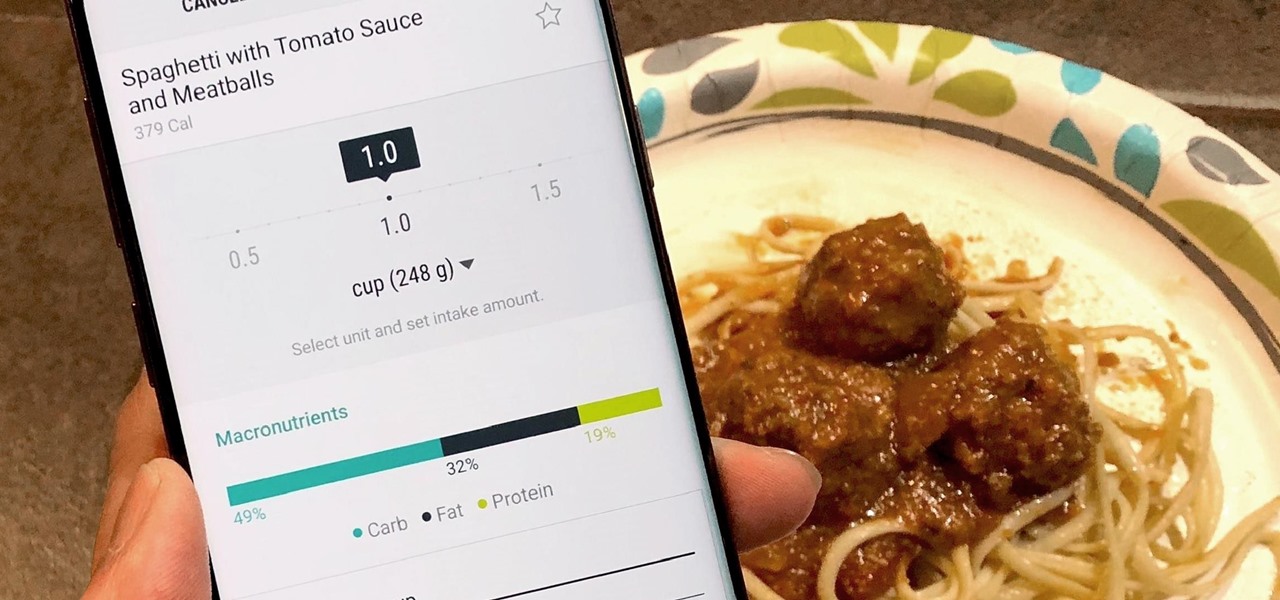
The most essential part of a healthy lifestyle is managing your diet — after all, what would be the point of a daily workout regimen if you were eating junk food? Thankfully, Samsung Health makes it easy to record your calorie and nutrient intake to get a clear picture of your dietary habits and how you can make them better.

Signaling a new direction forward for the company, Magic Leap shook up its executive suite by re-assigning to top leaders to new advisory roles. Meanwhile, a new startup backed by Hollywood executives, tech venture firms, and notable angel investors plans to bring new life to AR for marketing entertainment properties.

If you or someone you're shopping for has a newer iPhone model or an Android smartphone like the Galaxy Note 9 or Pixel 3, they come with wireless charging capabilities. Problem is, they don't come with wireless chargers. But there's no better time to snag one than on Black Friday, and we've found the best deals out there for 2018's holiday season.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

PUBG is currently taking the mobile world by storm, and it's easy to see why. The game has breathed much-needed life to the multiplayer shooting genre, primarily by adding an element of sheer terror as you scavenge for weapons in a hostile environment. With new players continually joining in on the fun, many players are looking for ways to gain an edge.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

According to Digi-Capital, investors poured $1.8 billion into augmented and virtual reality companies over the last 12 months, including $300 million in the third quarter. These investments are not made without a means to monetize products and services.

Apple officially unveiled the long-awaited iPhone X, its tenth-anniversary edition iPhone, on September 12. With preorder and release dates just around the corner, you'll want to brush up on all things iPhone X to make sure you get your hands on one as soon as possible. After all, preorders start Friday, October 27.