A vaccine against HIV might prevent the disease that we can't seem to cure. Some HIV patients make antibodies that can take down the virus, much the way a vaccine might. But, scientists haven't been able to provoke that type of response in other people. However, in a process that might work in humans, a group of researchers has successfully generated antibodies in cows that neutralize multiple strains of HIV.

Significant strides have been in the race to find antibiotics to treat superbug infections — those caused by bacteria resistant to the antibiotics used to treat them. Now, an international team of scientists has discovered a new antibiotic produced by a microbe found in Italian soil.
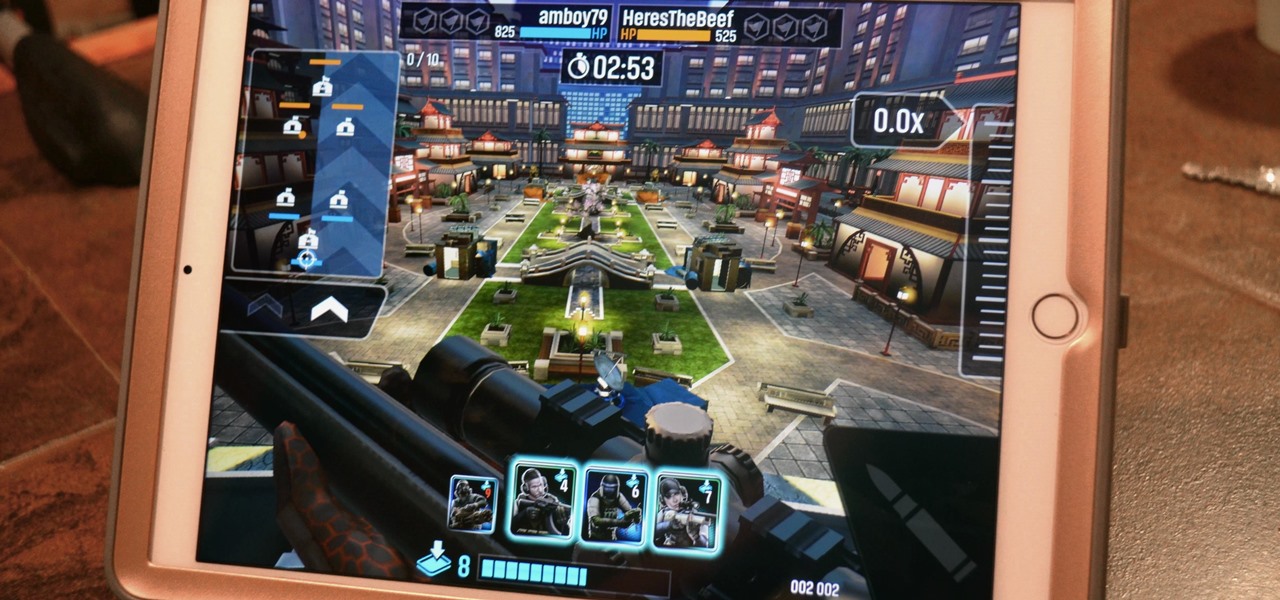
Tom Clancy games, like Rainbow Six and Ghost Recon: Wildlands, are famous for their realistic and immersive gameplay that focuses on covert, low-intensity warfare. Ubisoft now appears to be testing the overcrowded waters of mobile gaming with the release of ShadowBreak, and has soft released the game for both iOS and Android in Canada for further development, which means that with a little tinkering, you can play ShadowBreak in any country.
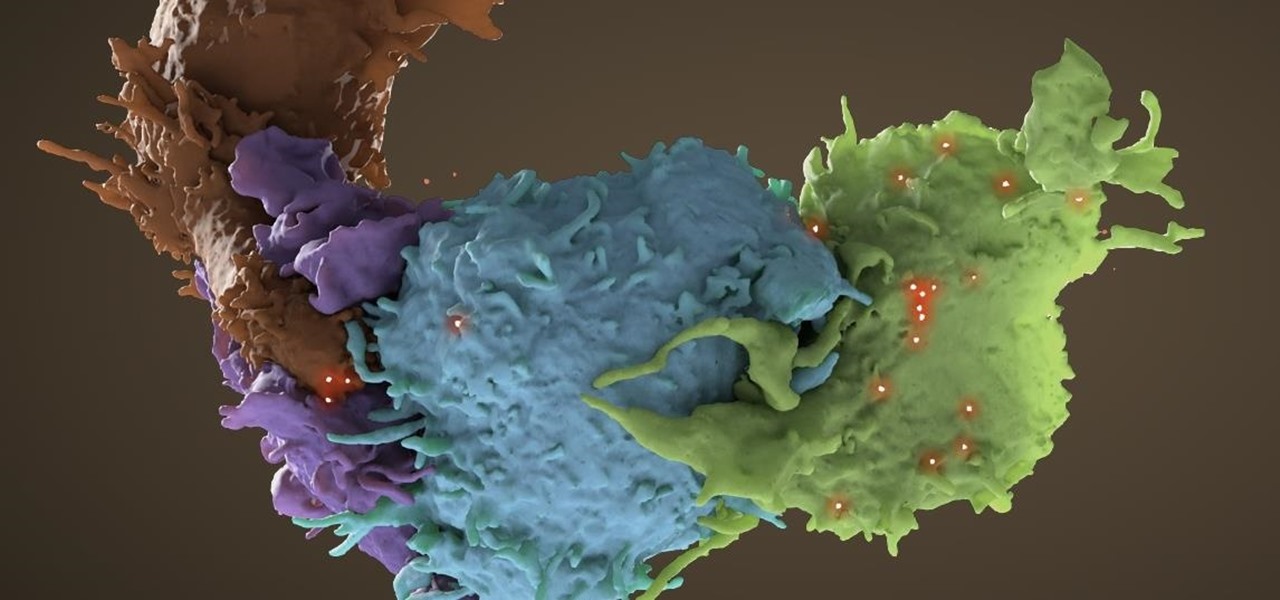
Tremendous strides have been made in the treatment and outlook for patients infected with HIV, the human immunodeficiency virus. Treatment with a combination of antiretroviral drugs can keep patients with HIV alive for decades, without symptoms of the infection. The trouble is, if HIV-infected people stop taking their medications, the virus takes over in full force again—because the virus hides out quietly in cells of the immune system, kept in check, but not killed by the treatment.

A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.

Welcome back to this series on making physical objects come to life on HoloLens with Vuforia. Now that we've set up Vuforia and readied our ImageTarget and camera system, we can see our work come to life. Because in the end, is that not one of the main driving forces when developing—that Frankenstein-like sensation of bringing something to life that was not there before?

The story of Helicobacter pylori is a real testament to the tenacity of medical researchers to prove their hypothesis. It took decades before the scientific world would accept that the bacteria H. pylori caused ulcers.

Findings from a mouse study suggest that the Zika virus infection may have serious reproductive consequences for men.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

Starting April 10th, you'll will be able to book 15-minute appointments online to try on an Apple Watch in person at Apple Stores across the world. With the April 24th release date just around the corner, making an appointment is a great idea for those who are unsure about which color and size to purchase—or if they'll even want one.

Beginning with KitKat, I've been used to customizing every aspect of my Android phone, but with the release of Lollipop, there is quite a bit of catching up that developers need to do. Most customization features, like quick settings rearrangement and theme support have already been ported over, but any type of lock screen customization has been noticeably absent.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

While rooting your Galaxy Note 2 certainly has its advantages—everything from increasing security to relieving the Power button of its duties—it's definitely not for everyone.

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Halloween is only a few short weeks away, and most people are scrambling to get their costumes together before the big night. The secret to a great getup is all in the details, and including your pet in the fun can be exactly what you need to take your costume to the next level.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

This video has a man by the name of Dr. Neder and he has a book by the name, ‘how to be a man in a woman’s world.’ He answers a series of questions. The first question asked is how to get a girl with a boyfriend. The answer this video provides is simply that all girls are looking to date up. Meaning your value and assets, if there is a greater attraction then the girl will end up with you and dump the guy that she is with. Does size matter? The average size of most man is five inches to five ...

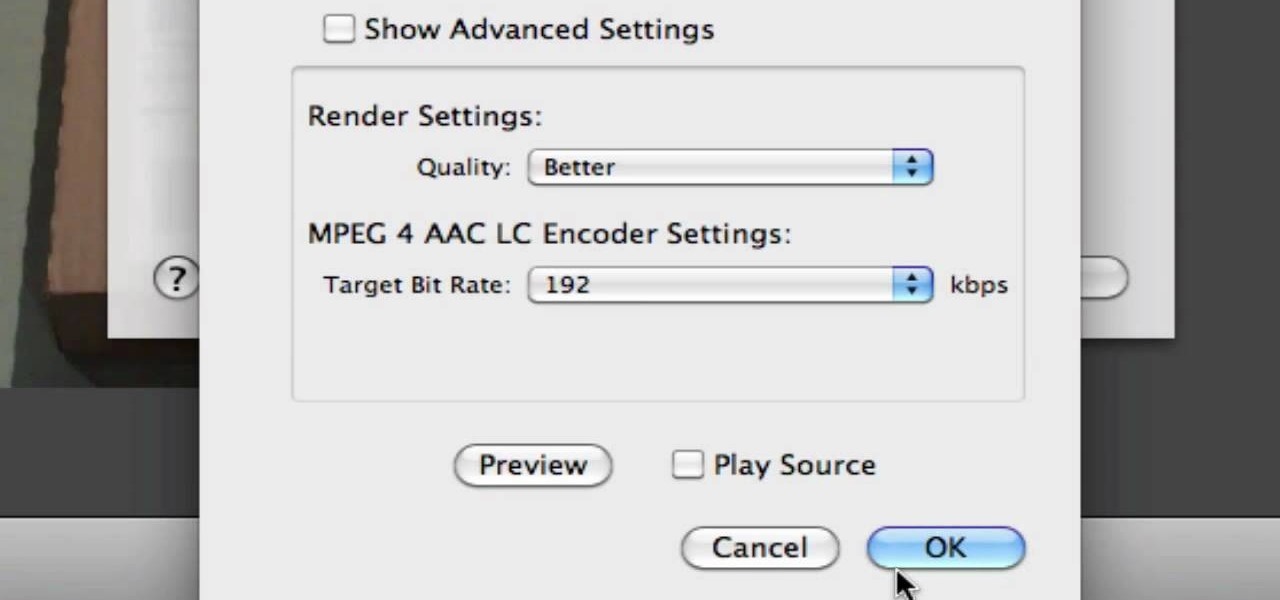
In this video from AppleGenius0921 we learn how to export videos using Screenflow in HD. Launch Screenflow, make sure you're editing is complete and go to File, then Export. A window will come up asking the name you want to save it as and where you want to save it. Make a good title that is relevant to your video. Now click customize. Then click settings. Now go to compression type and double click H.264. Set the quality on Best. Click OK and use no filter. Now go to size and click 1280x720 H...

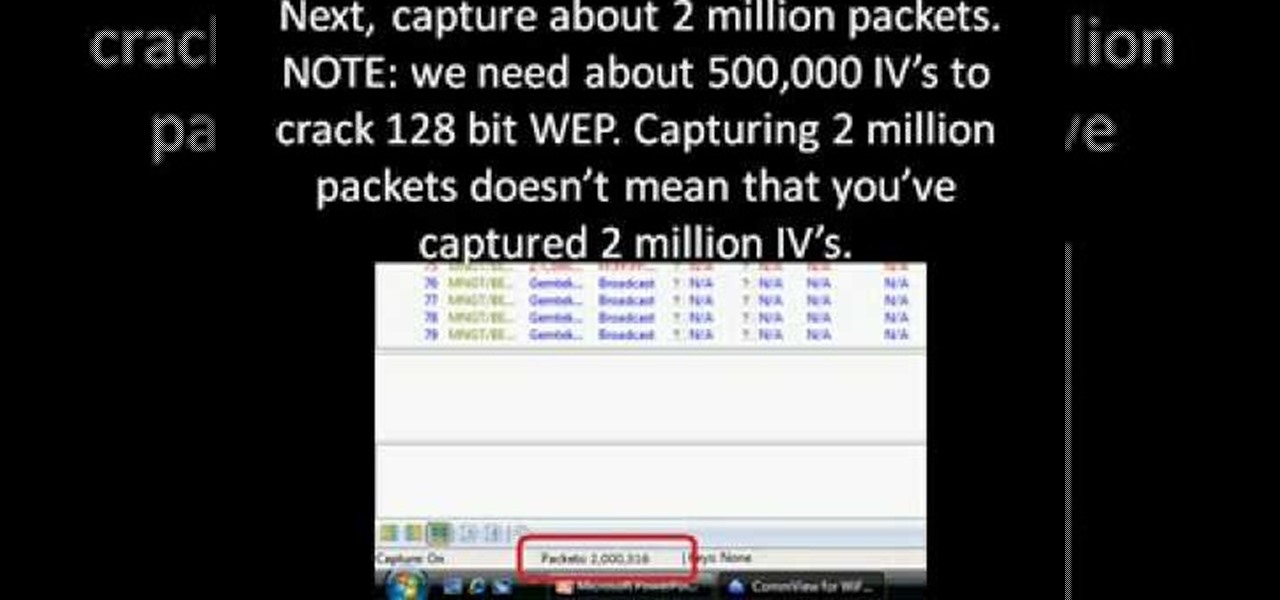
First you need to download Aircrack-ng and Second thing you need to download is CommView for Wi-Fi. Now you have to install CommView for Wi-Fi and then install the right driver.

In this Business & Money video tutorial you will learn how to make a successful curriculum vitae or resume. This is the first step in getting your dream job. A well written CV captures the interest of the person who is reading it. Think yourself as a product and the CV is a piece of paper that is going to sell you. Don't be afraid to sell your skills and abilities. If you don't do it, nobody else is going to do it for you. First thing on top is to put your name; centered and bold. Then leave ...

Almost 125 million people worldwide suffer from what is known as psoriasis, the skin disease that's marked by red, itchy, and scaly patches that are hurtful, if not visually god-awful. There can be a little hope though for psoriasis sufferers. Though you can treat and control psoriasis, characterized by dry scaly patches of skin, the progress is often erratic and cyclical, so be patient and consistent in executing these steps.

Speeding tickets are one of the worst things a driver fears on the highway, aside from wrecking, of course. But you can get home safe without getting a ticket. You just need to keep your vehicle off the radar by following these stealthy driving techniques.

In this edition of ClubHouseGas, with host Casey Bass, basketball coach Chuck Melito shows us how to shoot free throws. He shows us how to work on both the mental and the physical approach to free throw shooting. A right-handed shooter should place his right foot at the center of the basket. A left-handed shooter should place his left foor at the center of the basket. Then it's important to get balanced, so you're not leaning to one side or another, or more weight on one foot than the other. ...

John Roy demonstrates the tutorial to view or retrieve layouts that ens with .swf. SWF files can be viewed by pasting the url in the address box.

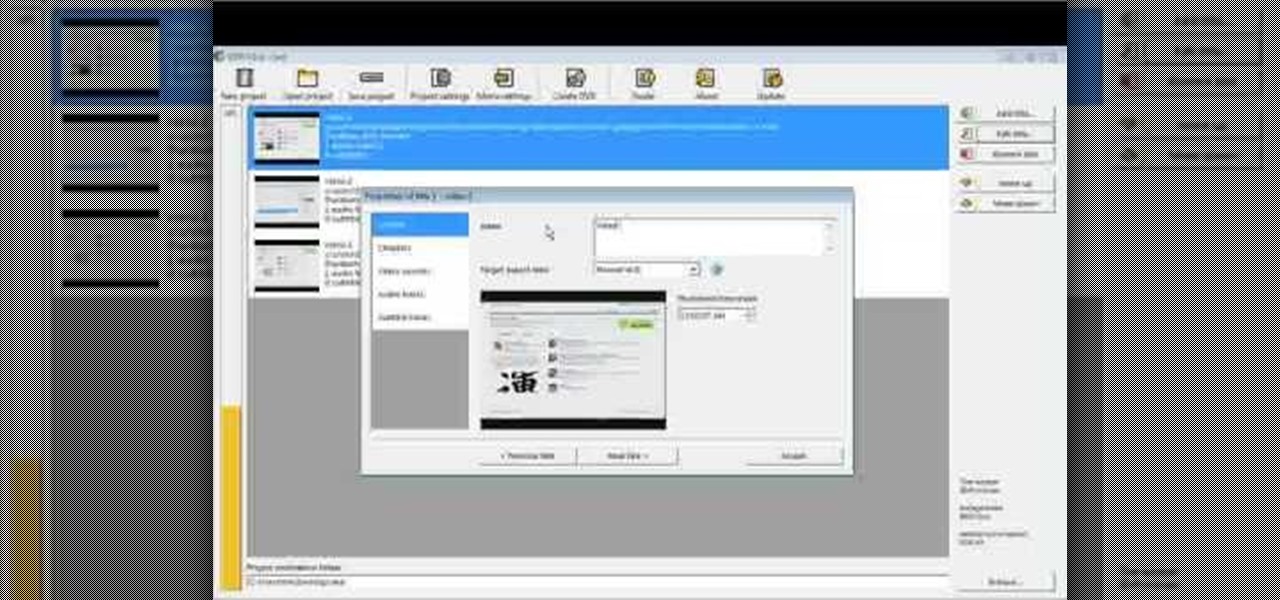
This video tutorial from Foreclosureresearch presents how to burn video files to a playable DVD using DVD Flick application.First you need to download and install free software called DVD Flick.You can find it at DVD Flick.Once it's installed, run the program. First thing to do is to set your Project Settings. Click Project Settings from top menu. From Project Settings window you can name the project, select Target size (size of your DVD), Encoder, Thread count, DVD format, bitrate, playback ...

Golf Link demonstrates how to identify whether your golf swing plane is correct. The swing plane is the path described by the golf head that controls the direction that the club head is traveling through when it impacts the ball. An on plane swing will have the club head directly traveling towards the target at the point of impact. That and a square face will make a straight shot. If the swing comes inside or below the plane, it will produce a hook shot or a push shot. A swing that comes outs...

You can manipulate the AF fine-tune on your Nikon DSLR in order to optimize the sharpness and resolution of your lenses. This is a great tool for achieving the highest picture quality possible.

You can organize your closet with simple drawers and shelves or racks that you purchase at a discount store such as Target. Outside of your closet you can have drawer space (use transparent drawers) by labeling your own drawers with large labels that you have written the contents of the drawer on and placed this at the front where it will be visible. The drawers can be divided into short sleeved sweater tops, long sleeved sweater tops, tanks, vests, short sleeved tees, long sleeved regular to...

This video shows you how to use an exercise band to do bicep curls, triceps extensions and shoulder raises along with some fun extensions of these basic exercises. When doing the bicep curl with the band it is very important to ensure that the band is firmly secured under your shoe, so that it does not slip forwards and snap. Once the band is secure you must curl the arms up towards the shoulders, keeping your elbows bent and close to your sides. The arms are still working in a negative resis...