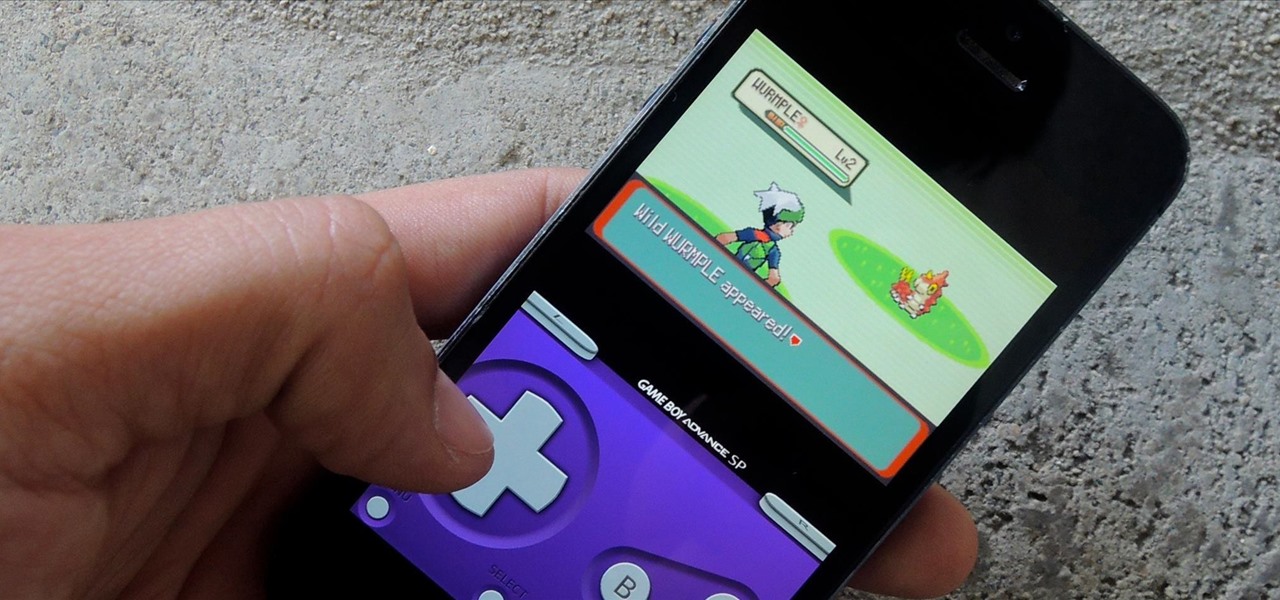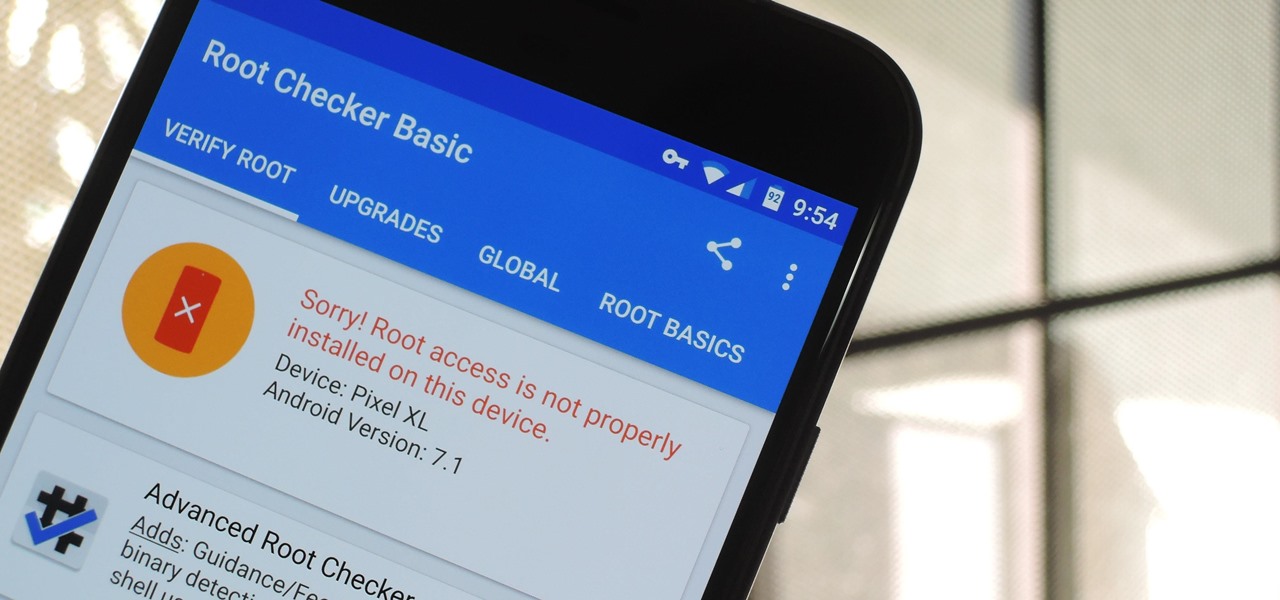
In the past, some of Google's Nexus devices have had root methods even before the phones hit shelves. The Google Pixel and Pixel XL are basically Nexus devices from a software standpoint, so why have we gone more than a week since release without a working root method or custom recovery?

It just got a whole lot easier to decide whether or not saving $50 on Amazon's new ad- and bloatware-subsidized smartphones is worth the headache of having to see an advertisement on the lock screen every time you wake the device.

When casting a flyrod, in most cases, tight loops will allow the fly to travel farther, more accurately, and with less effort. To cast these tight loops, the tip of the rod must travel in a straight line path, slack must be eliminated, and there must be a constant acceleration to a sudden stop. The most common mistake is using the wrist to move the rod which causes the tip to travel in a half circle or windshield wiper type motion.
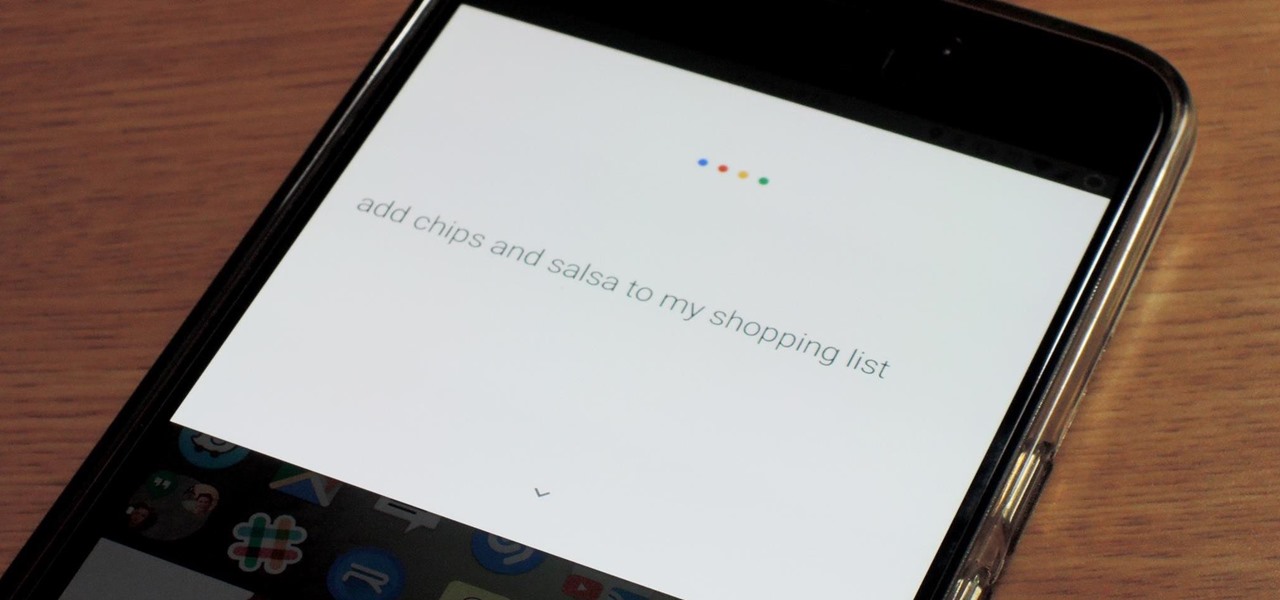
If you use Google Keep, you'll be happy to know that you can add items to lists and even start new ones with "OK Google" voice commands on Android, and it works fairly well. (Hat tip to Reddit user rambantu for finding this trick.)
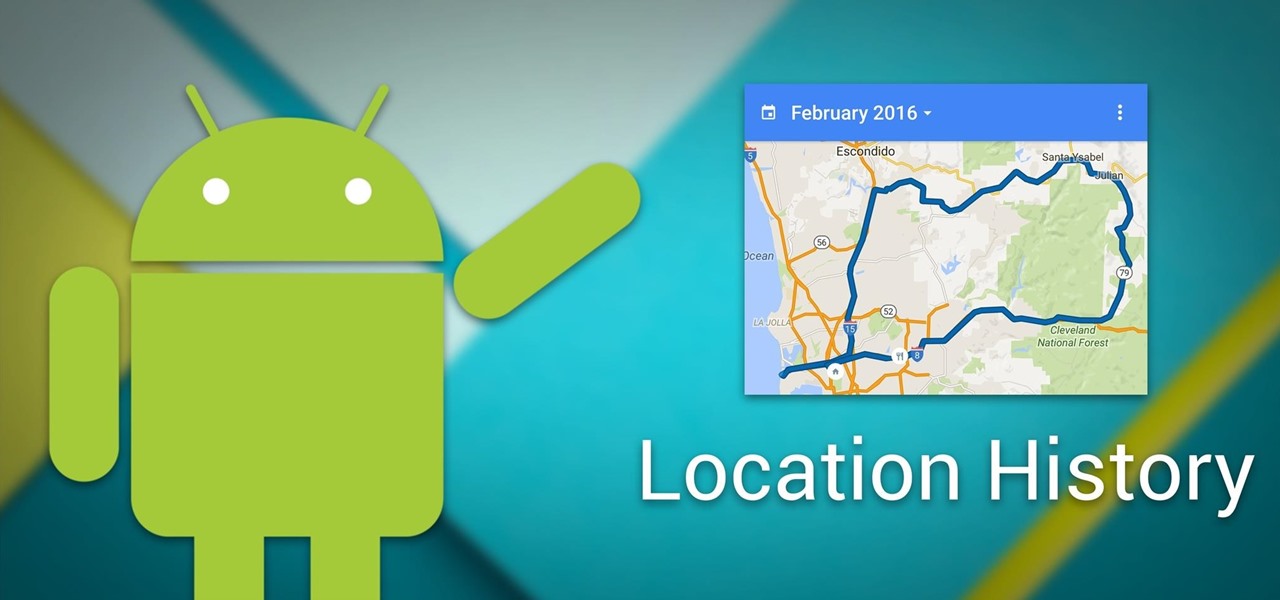
Your smartphone has a GPS chip inside of it that can pinpoint your location down to the nearest 4 meters, and this little device stays in your pocket or purse all day. Combine those two facts and you start to realize that your phone knows exactly where you've been during every moment that has passed since you've owned it.

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

There are a lot of great tutorials on Null Byte using Python to create backdoors, reverse shells etc, so I thought it might be worthwhile making a tutorial on how to convert these python scripts to exe files for Windows victim machines.

Google's Chromecast has been out for almost two years, and I can safely say it has changed the way I use my TV. At first it was a hassle to even get local media to play on it, but now casting has branched out to torrent streaming, which was a real game changer. Unfortunately, most apps only let you stream one video or song at a time, or you can't add magnet links or torrents to a playlist of local content.

And we meet again Crackers! Welcome to my 7th post (Part-2), this tutorial will explain about some more basics of Batch Scripting, with C00L Scripts, which in turn will help you learn and understand better

Customization helps your device stand out from the rest, and that sentiment is no different when it comes to the Apple Watch. Unlike every other Apple device before it, the Watch allows you to customize the information that appears on the UI—without the need for any jailbreaking.

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Show your significant other just how much you love them by surprising him or her with one of life's most precious, romantic gifts—bacon! Best thing is, this passionate treat works for any day of the year (Valentine's Day, a first date, anniversary, etc.), since love and bacon go hand in hand.

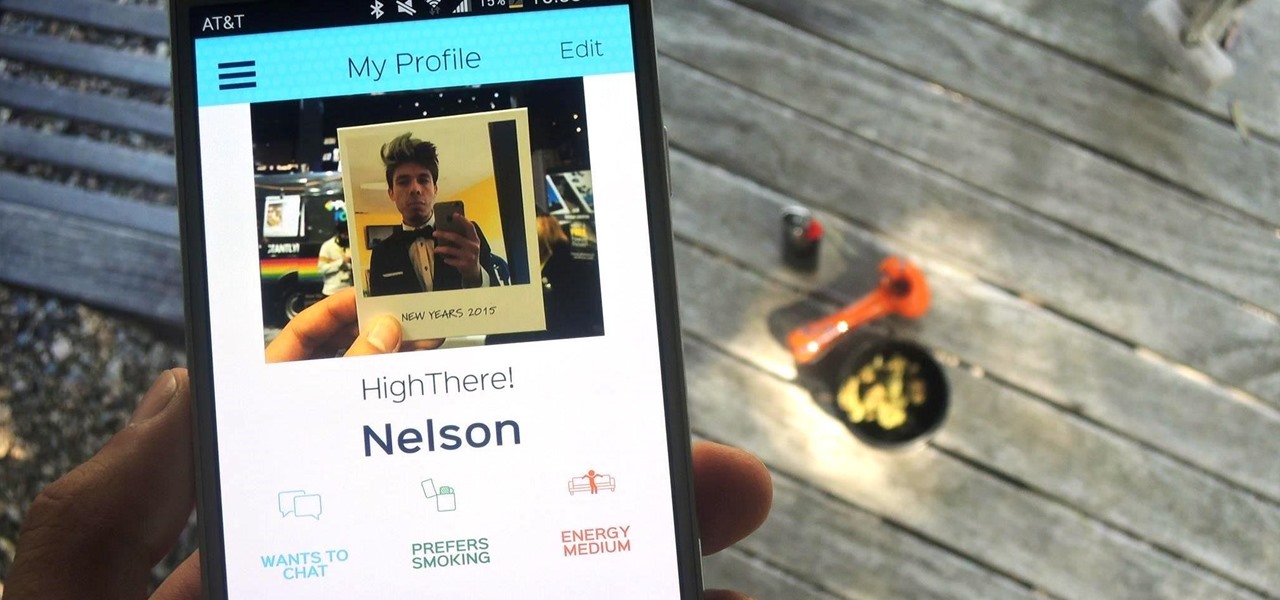
Dating can sometimes be a cruel and embarrassing game. You could be having a great time with someone, only for the situation to turn awkward and uncomfortable when a little bit of information is released, especially when that information is your use of medicinal or recreational marijuana.

Microsoft dropped a couple of huge bombs at their Windows 10 event Wednesday afternoon. Free operating systems and holographic glasses? This must be a Sci-Fi novel or a Hollywood blockbuster, because it reeks of fiction.

Well Welcome Back My Fellow Hackers. What is Slowhttptest? You may be asking. Slowhttptest is a Application Layer Denial of Service attack aka an attack on HTTP. You can read more about it here and also download it if you don't have Kali Linux. slowhttptest - Application Layer DoS attack simulator - Google Project Hosting.

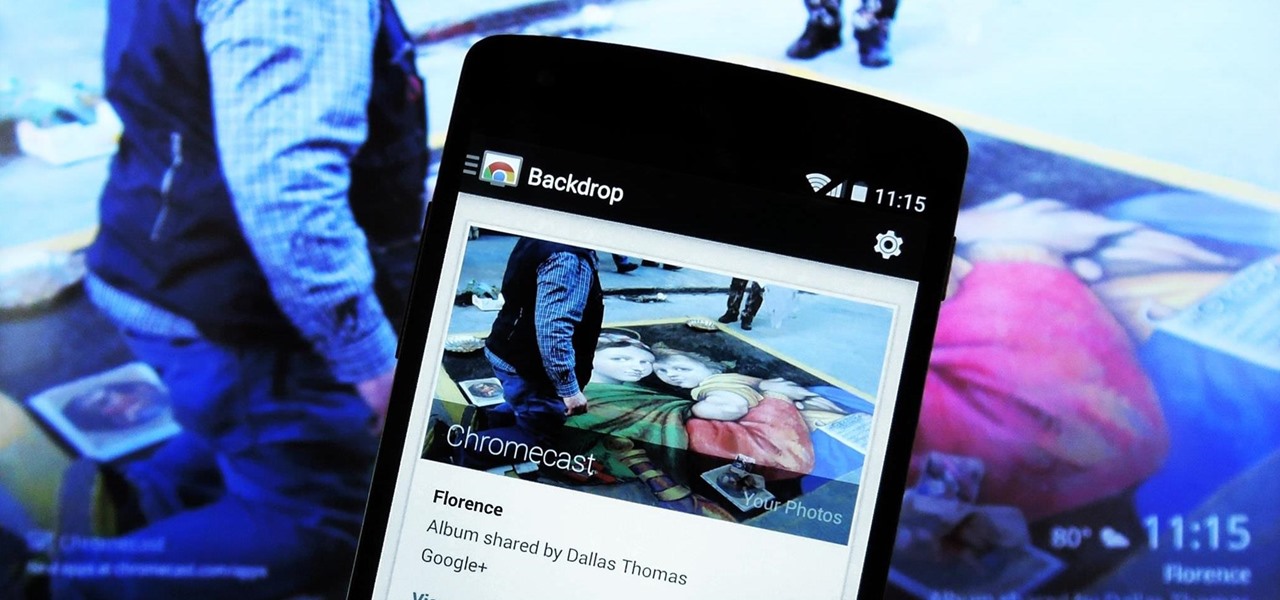
It's been a long-awaited feature since being announced at Google I/O in June, but Backdrop for Chromecast has finally started rolling out. With an update to the Chromecast app for Android and iOS, users will be able to personalize the background images that appear when Chromecast is idle.

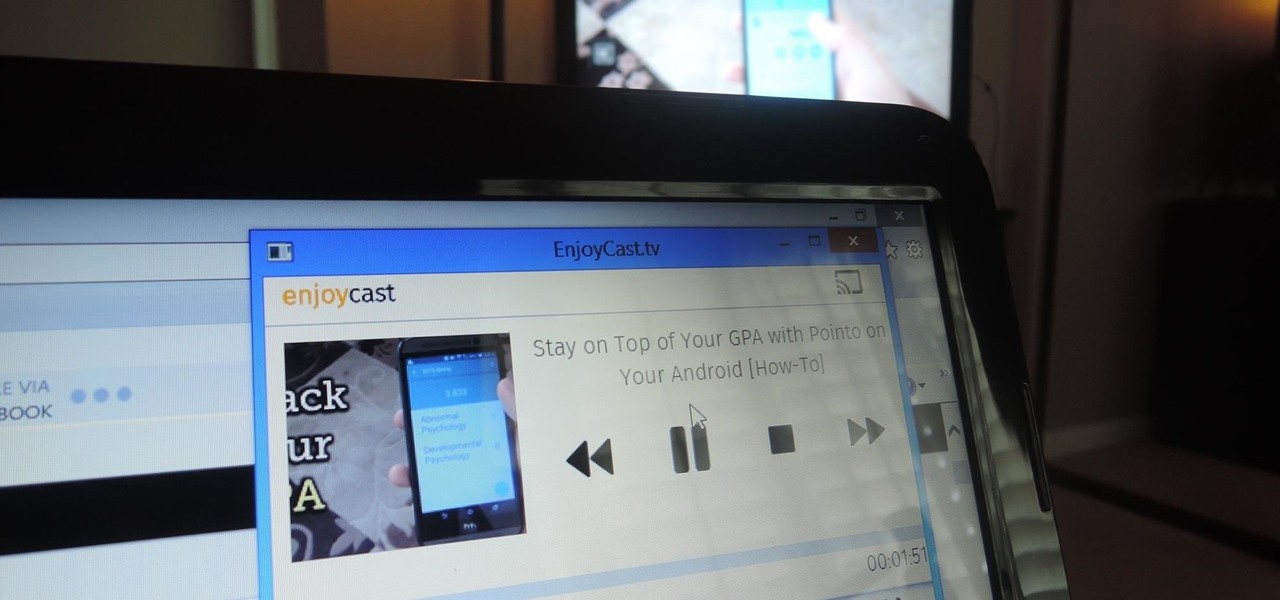
I may not be a well-traveled man, but one thing I've learned from my few excursions across the world is that currency exchange rates are a serious pain to keep up with. With global markets seemingly in a continuous flux, I started looking for anything to make staying on top of them easier, and thats when I found Price Helper.

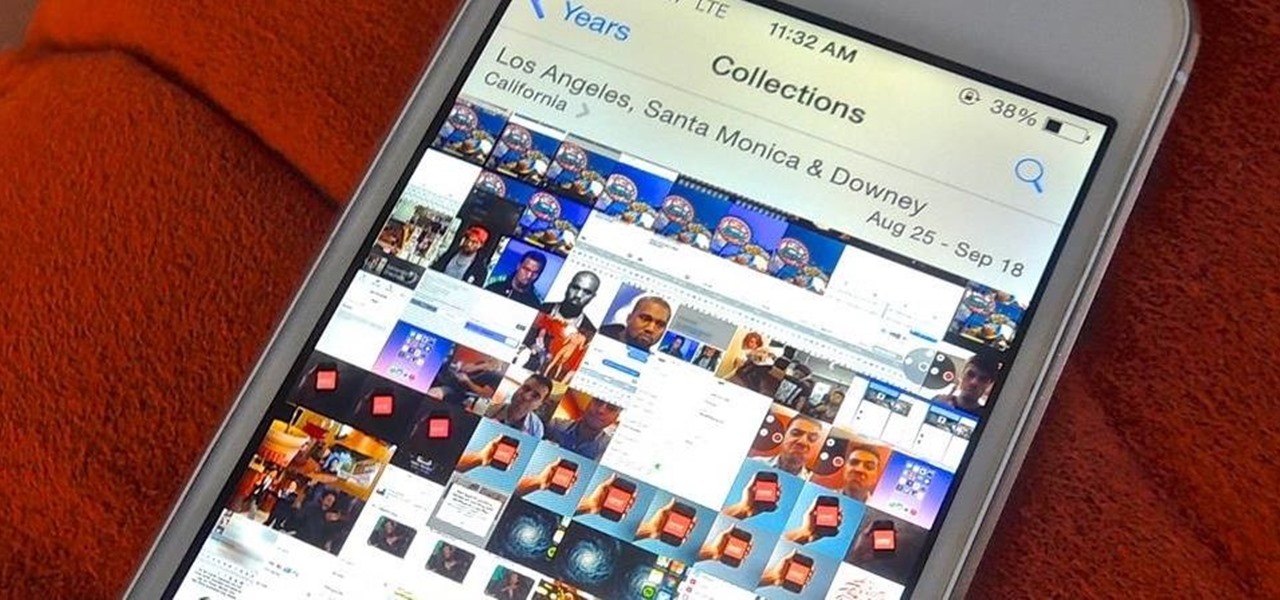
After updating to iOS 8, some of you have probably noticed that a lot of your pictures and videos are missing from the Photos app. Even if you were to restore your iPad or iPhone to your last backup, they would still be missing. But don't worry, that's just because albums work differently in iOS 8—all of your old photos are still there, just not as in your face as before.

Say goodbye to your boring stock Apple keyboard, because when iOS 8 is finally released, you'll be able to use Fleksy, SwiftKey, Swype, TouchPal, and other third-party keyboards on your iPad, iPhone, and/or iPod touch.

As much as it pains me to say it, without my phone, I would pretty much be useless. I can barely remember what I had for lunch yesterday, let alone all of the hundreds of numbers in my contact list. That's why whenever I forget my phone at home, I am pretty much stuck having to choose whether I want to be late to wherever I'm going, or feeling completely lost and disconnected for the rest of the day.

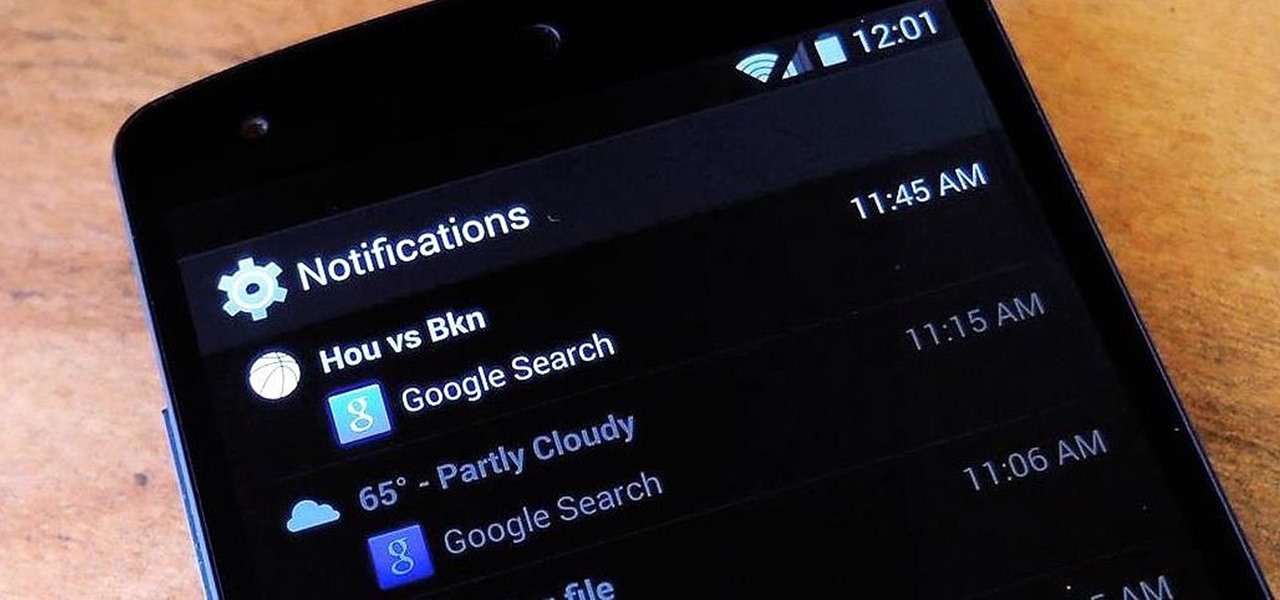
Have you ever been a little overzealous in dismissing notifications on your Nexus 5? Perhaps you missed your target and swiped away the notification you meant to read later. Or maybe you simply hit the "Clear All" button when you really meant to tap the button that switches to the Quick Settings tiles.

A good prank requires decent effort, creativity, and impeccable timing. If you're in the office, there are plenty of hilarious pranks to play on coworkers, and for your family and friends, there's everything from toothpaste-filled Oreos, to solid milk, to impossible-to-solve Rubik's Cubes and smartphone-friendly pranks.

While it may not serve much of a purpose here in sunny Los Angeles, it's still a good idea to keep constant tabs on the weather forecast, because you don't want anything to rain on your parade.

Normally, you'd have to jailbreak your iPad or iPhone to play any games that aren't available in the iOS App Store, like the now-extinct Flappy Bird game. But this isn't the case if you want to play some of your favorite old school Nintendo classics.

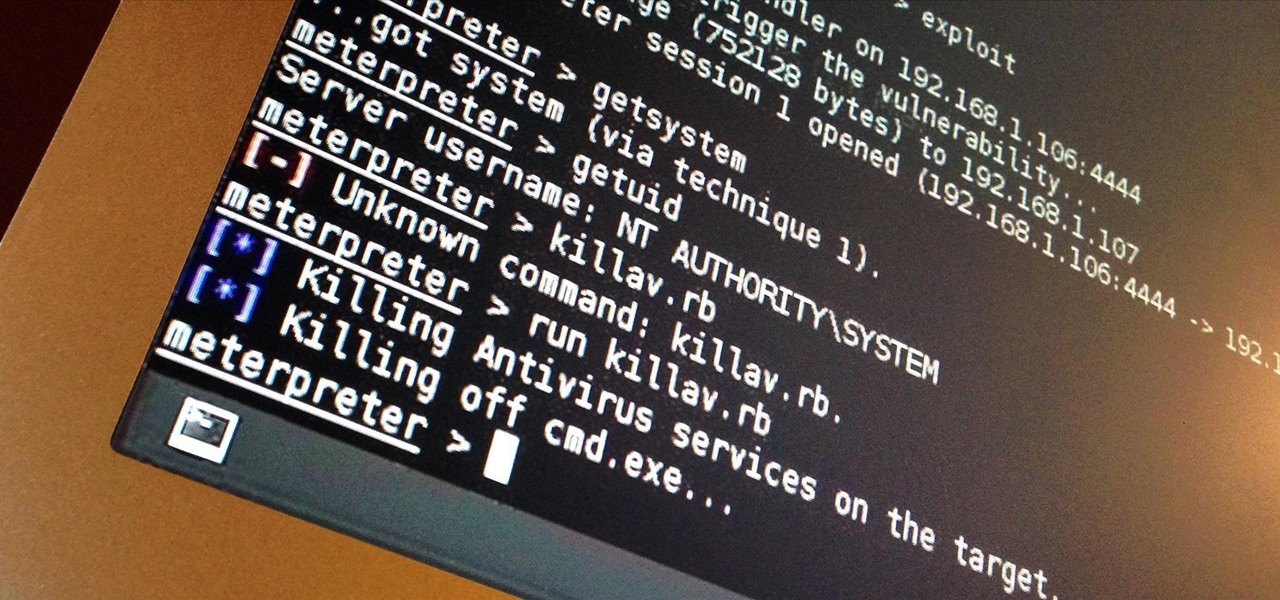
I've done numerous tutorials in Null Byte demonstrating the power of Metasploit's meterpreter. With the meterpreter on the target system, you have nearly total command of the victim.

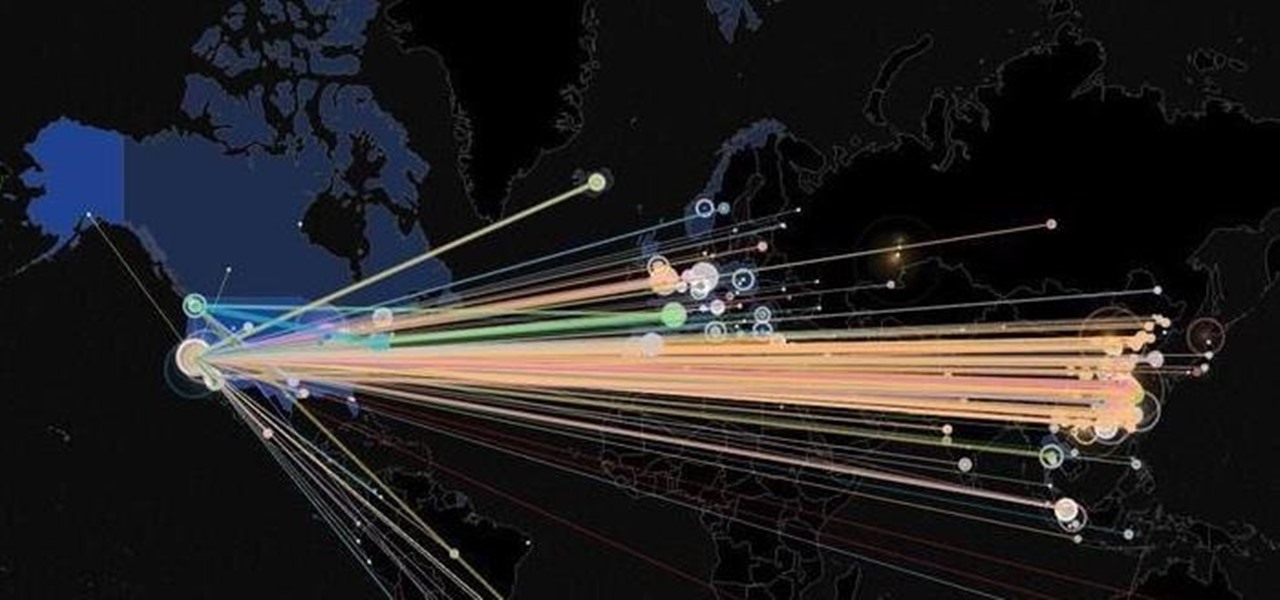
We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

We've all had that awful, sinking feeling when something you've been typing away at is suddenly gone. Maybe you accidentally hit the Back button, lost your internet connection, or your computer crashed, but whatever the reason, losing your work totally sucks. A lot of word processing programs have a built-in auto-save feature to prevent you from losing everything, but most websites and blogs haven't gotten there yet. An extension for Chrome and Firefox called Lazarus: Form Recovery can help y...

While graffiti may never be fully accepted by the masses, it has already become a very large medium for creative artists across the globe, who make mundane and austere cityscapes a little more interesting for the rest of us. Walking past this Banksy stencil on my way to class (at UCLA) made my day. Art like this can cause people to stop and appreciate the otherwise boring and blank walls that surround the city. It can stir up artistic feelings, pensive thoughts, and other emotions stored insi...

It's tough out there on the battlefield, especially when your stuck in the trenches and your comrades are dropping like flies. There's no hope. At least, until the next airsoft battle.

Keeping your operating system up to date is essential to keeping it bug-free and running properly. Windows regularly pushes out patches and security fixes through Windows Update, so making sure to turn on Automatic Updates or checking at least once a week is strongly advised.

You can do a lot with water guns. Have trouble waking up? Make a water gun alarm clock that (almost) no one could sleep through. Prefer real ammo? Turn your water gun into an airsoft BB gun. And if you don't have one, you can even make your own.

Yesterday, Bryan Clark pointed out a new option on Verizon's privacy settings that gives new customers 30 days to opt out of a data sharing program that gives advertisers information on basically everything you're doing on your new iPhone (or any other smartphone).

In an effort to appease iPhone fans eager for an NFC-equipped device, an option that is available on many other smartphones, Apple created Passbook, their version of a digital wallet.

Apple announced earlier this week that the official release date for iOS 6 will be September 19, but why wait when you can get it now? The Gold Master developer version was made available on Wednesday, and it's the same file as the final version that's going to be released to users on the 19th. Anyone can download it, so if you want to avoid being part of the frenzy on Wednesday when everyone else is trying to get it too, it may not be a bad idea to get a head start. A quick note: If you inst...

The streets of Tokyo are about to get a lot scarier (or more awesome), after Suidobashi Heavy Industries unveiled their latest project: a 13-foot tall, customizable, piloted robot. It's armed to the teeth with a water bottle rocket launcher and a BB Gatling gun capable of firing 6,000 rounds a minute; all for the very reasonable price tag of around 1.35 million dollars.

Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill