Everyone wants to have a pretty young thing on their arm, but not everyone can get it. To secure perfect trophy wife of your dreams, you need to meet a few criteria. Check out this tutorial and learn the do's and don'ts of dating younger ladies.

It can be hard finding fellow singles in the suburbs but it can be done! Keep your eyes peeled and make sure you are out and about meeting new people in public settings. Don’t forget about your online or in print options.

Body language is one way to tell if a guy likes you. He will lean towards you or look at you a lot. If he likes you, both feet will be pointed towards you. If he doesn't like you, one foot will be pointed at the door. Eye contact is another way to tell if he likes you. If he is shy, he will turn his head quickly when you catch him looking at you. He may try to catch your gaze and hold it, which could be uncomfortable to you if you don't like him as much. Guys will try to make themselves seem ...

Starcraft 2, like it's predecessor before it, has a very robust level editor that allows you, the DIY modder, to create nearly any scenario within the bounds of the Starcraft 2 engine that you could imagine. We have compiled videos on how to do all sorts of fun things with it, from making RPG's and Tower Defense games to just making you dream Starcraft 2 level. This video will teach you how to make a Starship Troopers (film, not book) style map where a group of Terrans have to defend a remote...

Commemorate the worst president in history by drawing his face to a lifelike representation and then having a dart throwing contest with your homeboys at the bar! This drawing tutorial, which teaches you how to sketch the face of George W. Bush, or W, is an excellent way to hone your targeting and aiming skills.
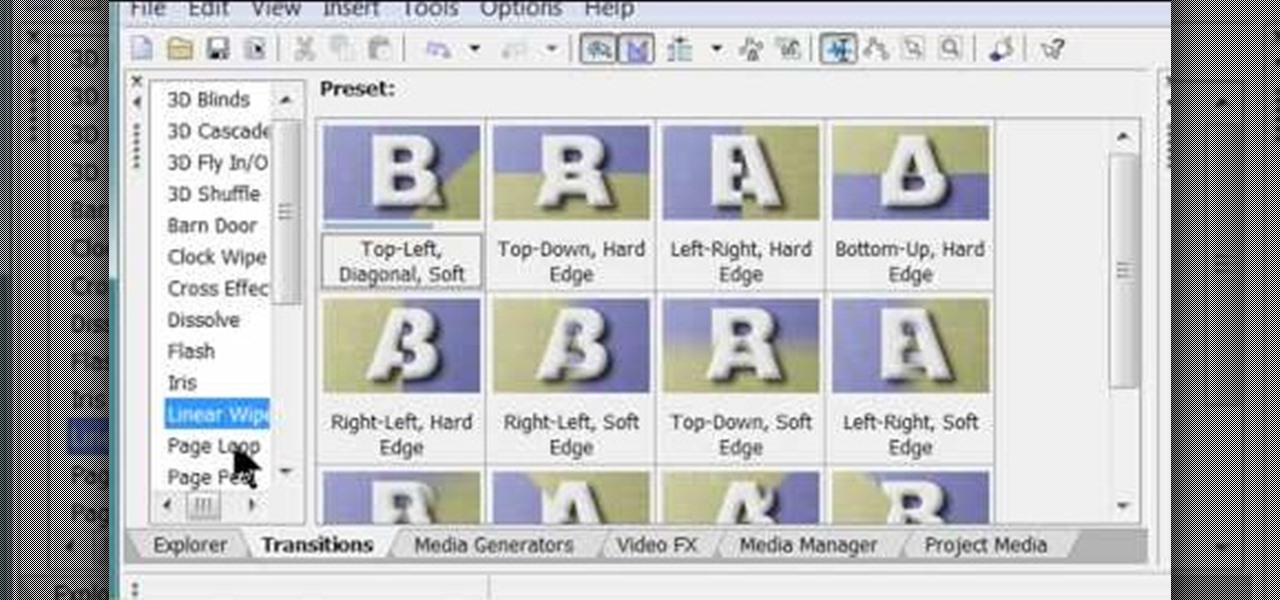
Software manufacterers always advise you to read the instruction manual first before attempting to do anything on a new program. But who has the time to obsess over ever little boring detail in a 300-page tome when just playing around the controls on your own gets you attuned to the program immediately?

Monitoring your blood glucose level is absolutely essential to your health if you suffer from diabetes. You need to keep track of your blood sugar or you could be in danger. This video tutorial will show you the proper way to use a blood glucose meter and give you helpful tips on getting the most out of them.

This week: a rigged game of skill & a simple sucker bet! Check out this video if you want to learn how to beat anyone in a simple game that can be played anywhere with coins and a napkin. Some might call it magic, others call it skill.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to shop the App Store on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

If you have ever wondered about the functionality of slating during a film shoot, what a shooting script or line script is and how to keep a shot log, then this may be the perfect video tutorial for you, in two parts.

If you think you might be a likely target of a black-hat hacker, there's a new iOS security feature that offers extreme protection for your iPhone against spyware, phishing attempts, and other highly sophisticated cyberattacks.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

There's a growing sentiment around the web that when it comes to Android, stock is best. Many people prefer the clean look of Google's vision for Android, but manufacturers like LG will add features and themes on top of this base to differentiate themselves from the pack. But these OEM skins, as they're called, aren't always as overbearing as you might think.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

This is the end of the Xbox 360 game Darksiders. It's the last level, the last quest, your last mission… the Destroyer. You'll need to summon Ruin to stand a chance against the Destroyer. Hold the Focus button to target lock onto the creature so you can keep in in view as you move around. The idea is for you to ride in close enough to the dragon and slash it with your Armageddon Blade. Watch out when you see the Destroyer's front claws glow red as this means he's coming to slash at you. Eithe...

Rumors, gossip, exclusion. Mean girls have a lot of weapons in their repertoire – here's how to combat all that nastiness.

Learn how to do single leg cable curls. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do knee tuck floor crunches. Presented by Real Jock Gay Fitness Health & Life. Benefits

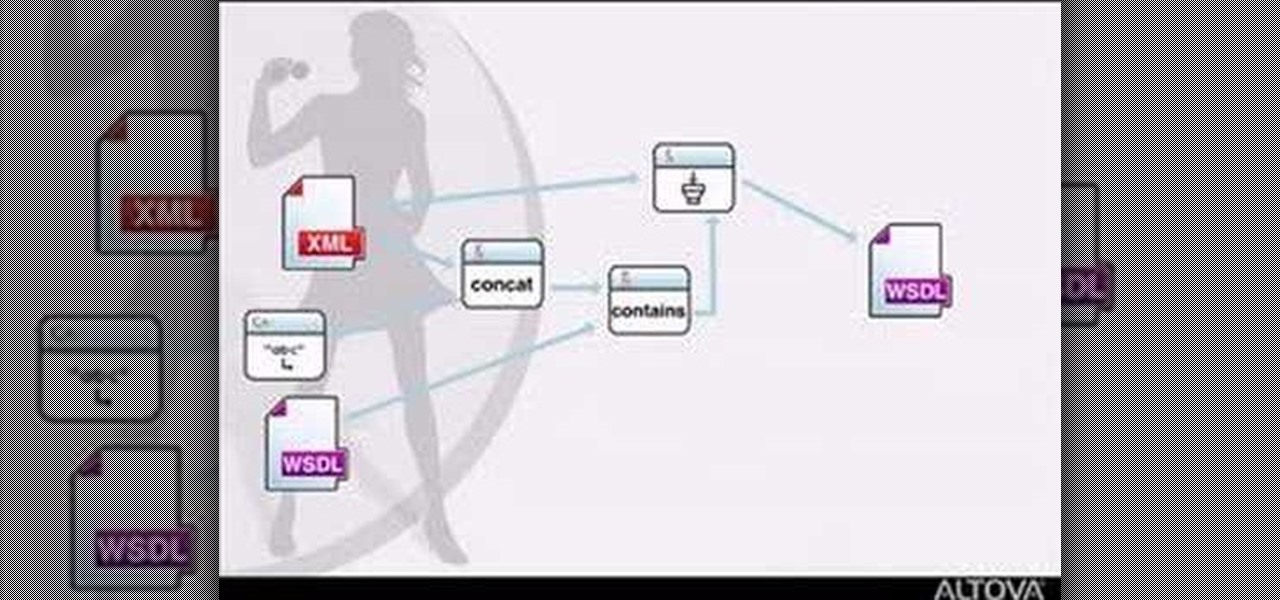
MapForce supports XML, databases, flat files, EDI and web services as the source and target of any mapping. In this tutorial, you'll take a look at how to use the different data sources available in MapForce.

Feel beautiful from the inside out with targeted exercises, like these exercises for your feet. This how-to video has a few simple exercises that will strengthen your toes and relieve some foot discomfort. Keep your feet in good shape so you can wear those high heeled shoes all night.

Brad Keller demonstrates how to throw a flying disc. The key is that whoever has the most fun wins. You need to throw the disc flat other wise you will miss your target.

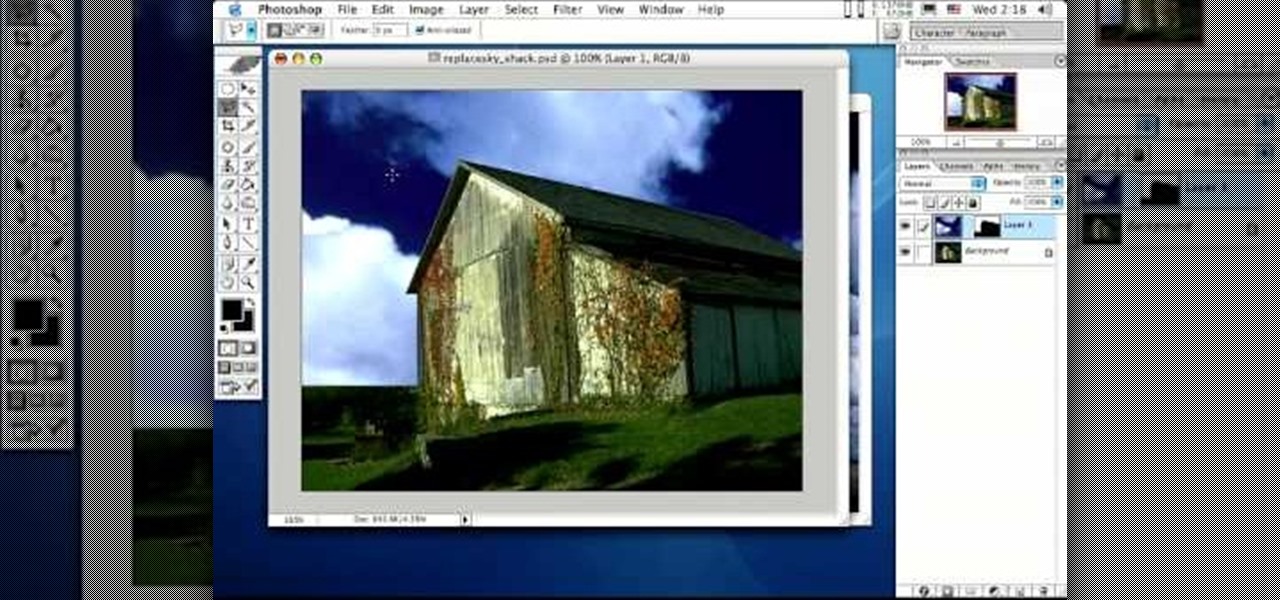
Photoshop is the perfect program to use when you want to make adjustments to photos you have taken. You can really make a sky pop in any of your pictures by using Photoshop to manipulate the color by following this tutorial.

Feeling unprepared for the next earthquake? In this tutorial, learn what to do and what not to do to survive "the big one". You'll be surprised to learn that hiding in a doorway is a myth!

Learn how to do alternate power stability ball pikes and knee tucks. Presented by Real Jock Gay Fitness Health & Life.

Steve G. Jones tells you how to get dates using the secret powers of hypnosis techniques.

Ask someone out on a date in multiple languages including French, Spanish, Portuguese, Russian, Hindi and English.

Ah, springtime. When the flowers bloom, the birds chirp, and a young coed's thoughts turn to steamy hook ups. Watch this video to learn how to hook up on spring break.

Increase your odds of meeting Mr. Right with these tips. Learn how to meet men if you are single. You Will Need

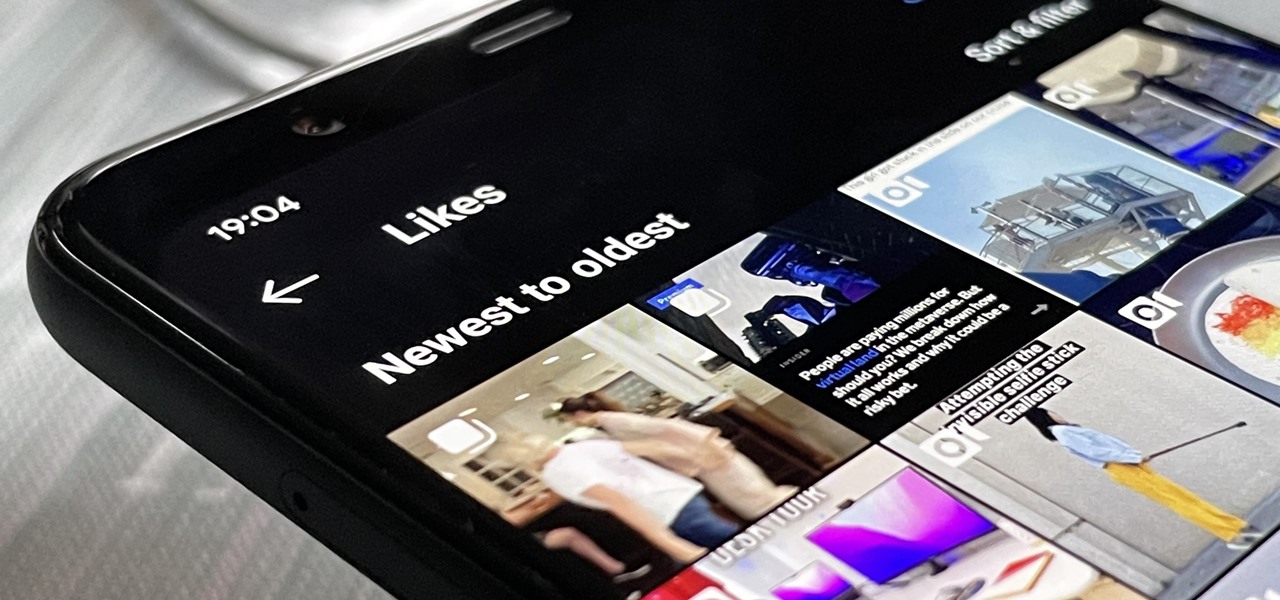
Unlike TikTok, there isn't a convenient "Likes" tab directly on your Instagram profile page to see all the posts you've ever loved. That's too easy. Instead, you have to dig a bit deeper if you want to take a trip down IG memory lane.

Apple's Reminders app has come a long way. In the past, if you really wanted to keep track of your important daily, weekly, and monthly tasks, you needed to install a specialty third-party app to make it work. While those apps still offer valuable features, Reminders can get the job done for many iPhone users now. With iOS 14.5, Apple only sweetens the deal.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

Black Friday is upon us. Whether you prefer to duke it out in stores or calmly shop online, there's no doubt you'll find great deals on the items you're looking for this holiday season. It's the perfect time of year to buy something expensive, like a good pair of AirPods, Beats, or Bose, at a much more opportune price.