Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.
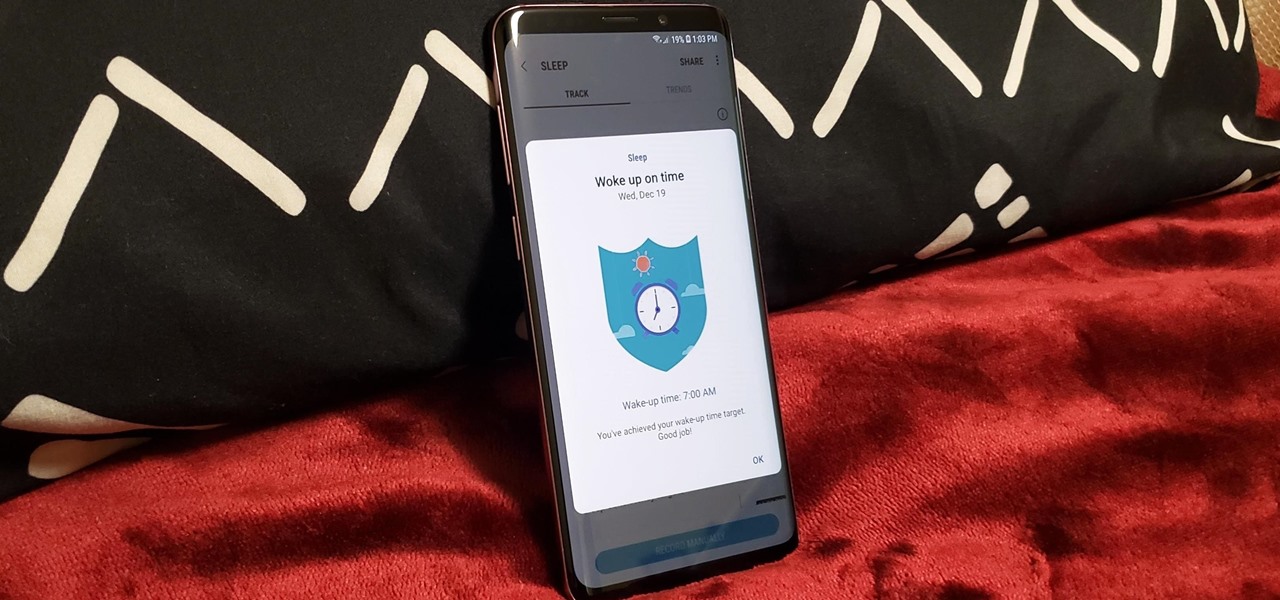
The quality and length of your sleep will almost always dictate how the rest of your day unfolds. Sleeping fewer hours increases your chances of spending the day in a tired and cranky state, while having a restful night's sleep contributes greatly to being alert and productive. Luckily, if you want to track your sleep patterns to figure out how you can improve your circadian rhythm, Samsung Health has you covered.
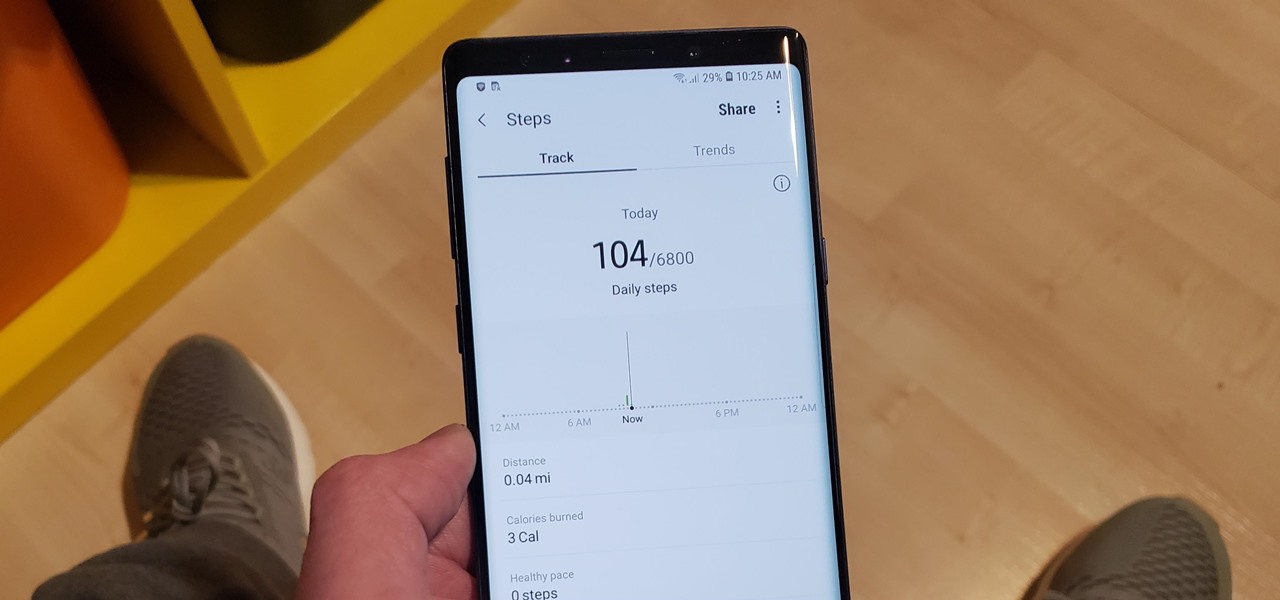
Once known as S Health, Samsung Health has become one of the most comprehensive health apps available for Android. In fact, we all can benefit from the features the app brings to the table — whether you're a marathon runner or a couch potato. If you're in the latter category, the app has a simple feature that can nudge you towards becoming more active.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

At its F8 developers conference on Tuesday, Facebook announced new tools and features coming in a new version of AR Studio, including the integration of 3D content aggregator Sketchfab's Download API.

Epic Games just released update v3.4 for Fortnite Battle Royale on all four platforms. This new version brings a number of UI changes, performance improvements, and bug fixes, but the addition that will get the most players excited is a new weapon: the Guided Missile.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

If you've ever wanted to hone your paintball skills, without spending a ton of money and making a huge mess, Show Me Virtual and Apple's ARKit have an app for you.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

A new dating app has arrived, and it'll finally land you a date with your celebrity crush ... kind of. The app — Dating AI — uses face search technology to help you search for potential love interests that resemble a celebrity you're attracted to.

We're all looking to meet someone, and in this day and age the easiest way to do that is through one of the various dating apps out there. But we can all admit it can get disheartening swiping through all of those people for the frustration of someone not answering your messages after matching. The fact is, we could be missing out on great people just because they don't have time in their busy lives to answer their dating apps every day. Not to mention the fact that we as a society are becomi...

T-Mobile just unveiled two new services—Scam ID and Scam Block—which specifically target those pestering robo-calls that reach out to 2.4 million Americans every month.

Android 6.0 introduced a new feature called Direct Share that allows apps to pin a more specific set of targets to Android's share menu. You've probably seen it already—messaging apps will allow you to share a file directly to a specific contact instead of just to the main app, and there are several other implementations like this.

Anyone who paid attention to the Lavabit shutdown had a feeling it was connected to Edward Snowden, the high-profile NSA whistleblower. Ever since the government's case against Lavabit went public in late-2013, people have put two and two together.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Five Phases of Hacking:- The five phases of Hacking are as follow:

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

The bread at your local supermarket will most likely always be fresh, but how do you know which loaf is the freshest out of the bunch? You can squeeze and inspect them like an annoying TSA agent, but there's actually a much simpler way to do it.

We share links on an almost daily basis, usually not even thinking twice about it. Whether you're sending a funny cat video to your sister, or letting your coworker know where to go to download relevant files, there are plenty of reasons you might be giving someone a URL.

Link shorteners like TinyURL and Bitly are great for Twitter (or anytime you're limited on space), but they're also great for hackers. It's easy to hide a malicious link in an innocent-looking shortened URL, which increases the chances that people will click on it.

The video presents "How to start your own Clothing Line Business". The steps include getting the financing, designing the prototype outfit/s, producing the line of clothing, promotion and sales. A good way of financing for a small business such as this is to sell your idea to family, friends and even colleagues. Research and prepare the business plan for your clothing line and be passionate about it in your presentation to convince them to fund your business. The next step is to get the produ...

In this how-to video, you will teach your dog how to target objects with its front paws. You will need a clicker, treats, and a target such as a yogurt lid or ball on a stick. Take a treat and hide it under the object. Click when the dog does any paw movements towards the object. After ten successful tries, pretend to put a treat. Once the dog paws the object, show that there is no treat but still give the dog a treat. Once this is done, wait until the dog paws the object, and give a treat. I...

A lot goes into making a hunt successful, and most of it happens before you take to the field--like making sure your rifle is properly sighted in. It's not hard to do if you follow a few simple steps: first, and this is the first step when you do anything with a firearm, make sure it's unloaded. Make sure your scope is properly mounted and the mounting screws are tight. Remove the bolt from the rifle and sight through the barrel to make sure you're lined up with a sight-in target placed at 25...

You've got Apple's latest and greatest, the iPhone 4. Make sure you keep it up to date with the most recent versions of your apps available. Watch this video to learn how to update apps from the App Store on your iPhone.

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 720th installment in their series of digital spreadsheet magic tricks, you'll learn how to use filtering, the AND, TODAY and EDATE functions, and conditional formatting to show values between two dates.

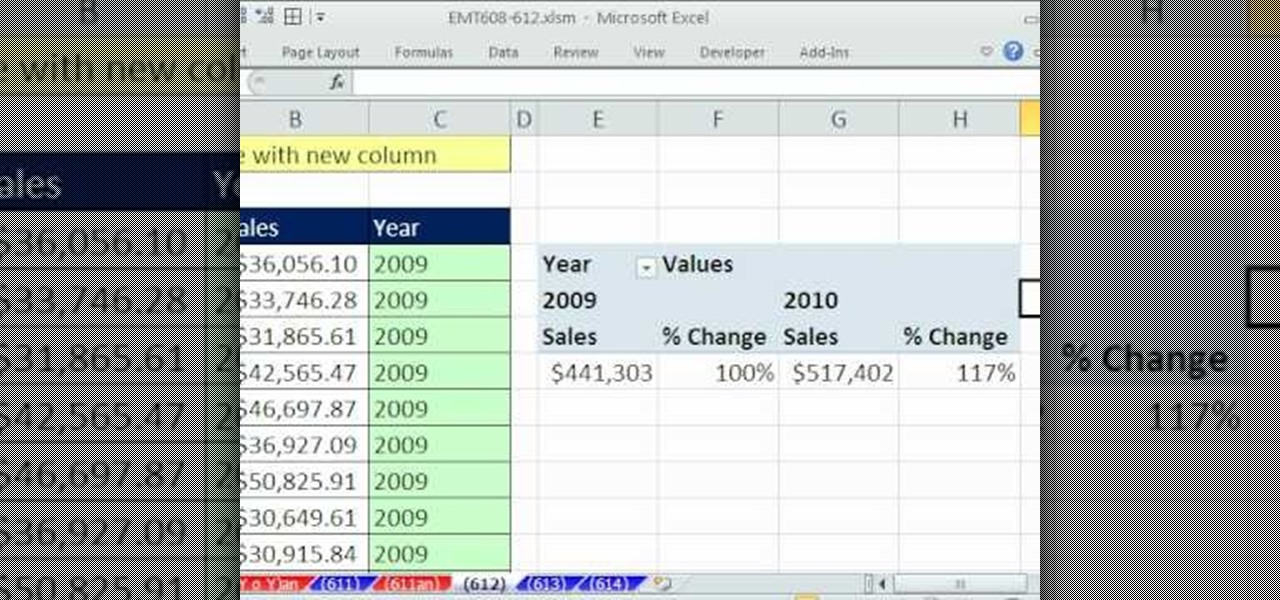
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 612th installment in their series of digital spreadsheet magic tricks, you'll learn how to create a Year Category for a PivotTable from dates entered as text using the RIGHT function and the ampersand (&) join symbol.

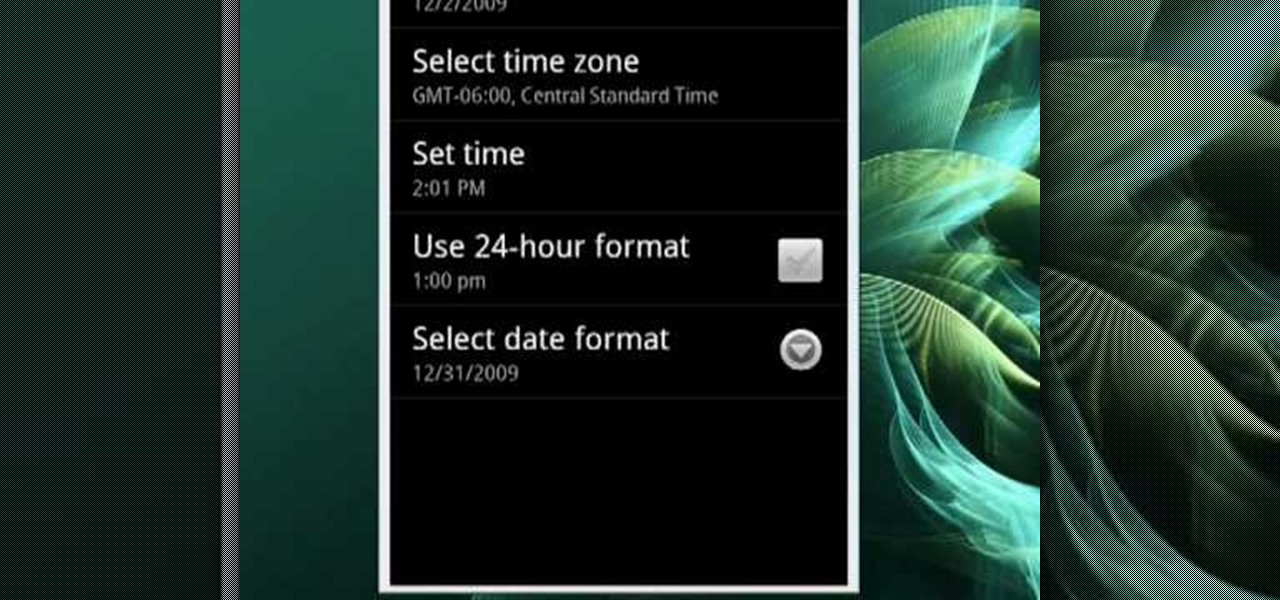
You can change how the date appears on your Android phone. One of the salient advantages of a Google Android smartphone over, say, an Apple iPhone, is the inherent extendibility of the open-source Android mobile OS. There are a seemingly infinite number of settings to tweak and advanced features to discover and use. This free video tutorial will show you how to adjust calendar display settings on your Android device.

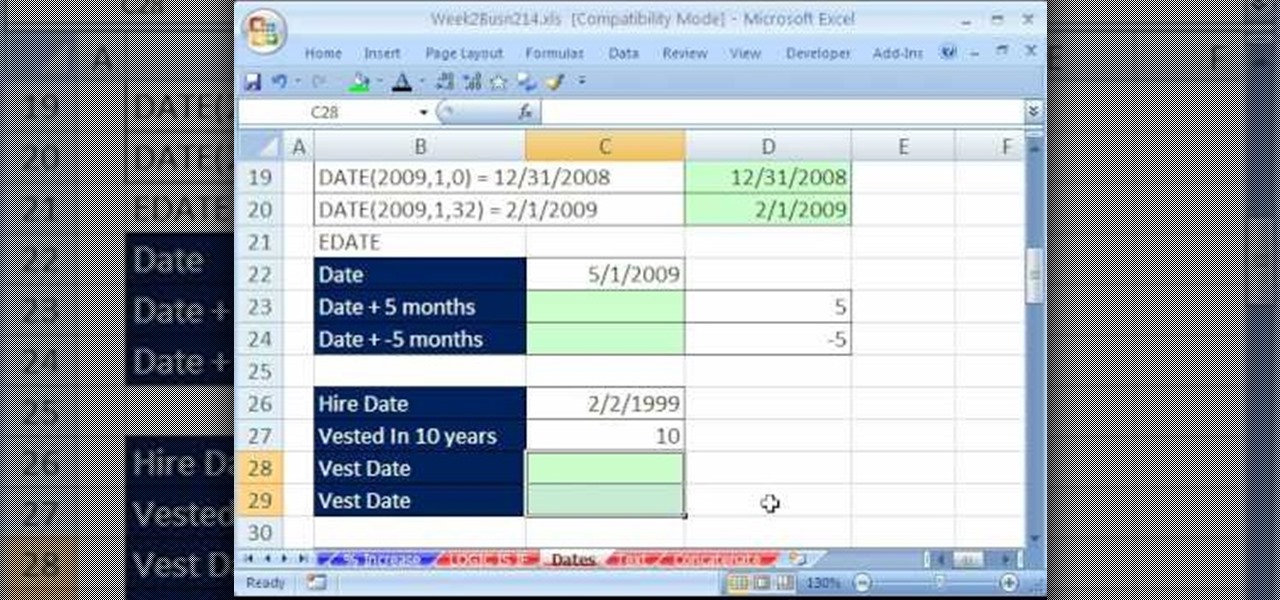
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you've come to the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 12th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to use the TODAY, NOW, DATE, YEAR, MONTH, DAY and EDATE functions.

As you might guess, one of the domains in which Microsoft Excel really excels is business math. Brush up on the stuff for your next or current job with this how-to. In this tutorial from everyone's favorite digital spreadsheet guru, YouTube's ExcelIsFun, the 48th installment in his "Excel Business Math" series of free video lessons, you'll learn how to calculate cash discounts via dating.

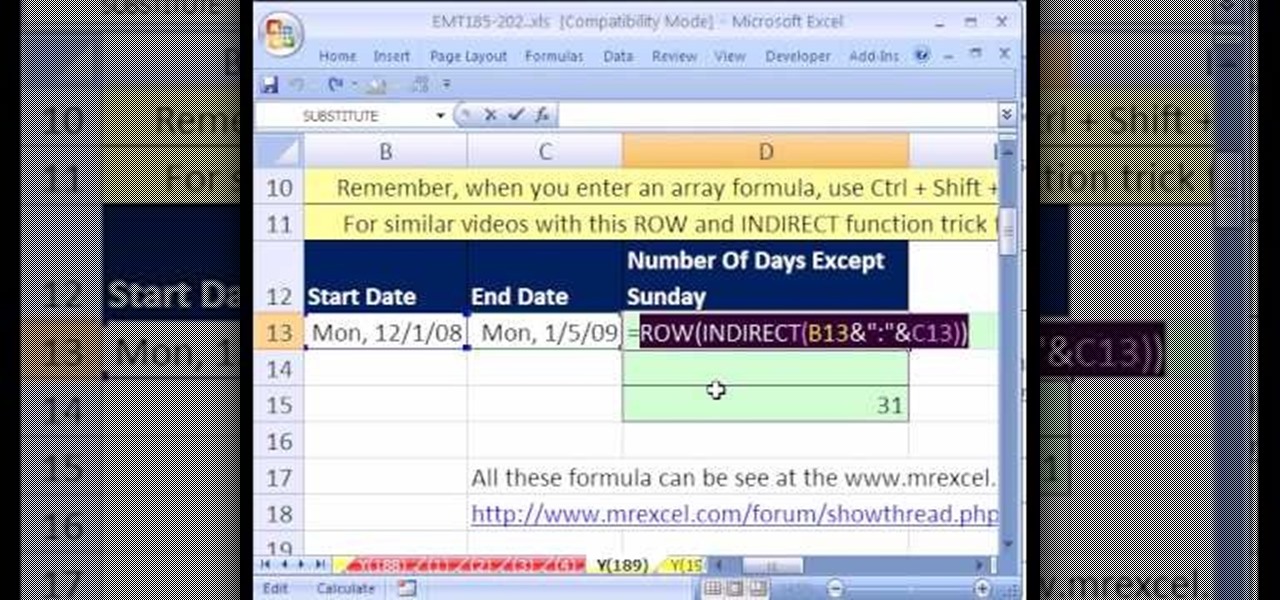
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 189th installment in their series of digital spreadsheet magic tricks, you'll learn how to count all the days except for Sunday using an array formula for a given date range with a specified start and end date.

In this video tutorial, viewers learn how to use a jump rope drill to help prevent golf pull shots. When beginning a swing, some people tend to rock the right shoulder upwards which doesn't get it far enough from the target line and causes the down swing to go out and over the target line. When swinging, make the right shoulder go straight backwards away from you and put the weight on your left heel. To perfect this, loop a jump rope over a fixed object. Then alternated and pull one end of th...

When shooting a shotgun, you don't really have to aim--just point and shoot. Whether you hit what you're shooting at depends on how well you did your homework. "Patterning" your shotgun allows you to choose exactly the right brand of shells, size and type of shot and type of choke required for the game you're pursuing. Set yourself up 40 yards from a 30-inch circle target, and bring along several brands of shells in various shot sizes. Use some form of rest like sandbags on a table or a rolle...

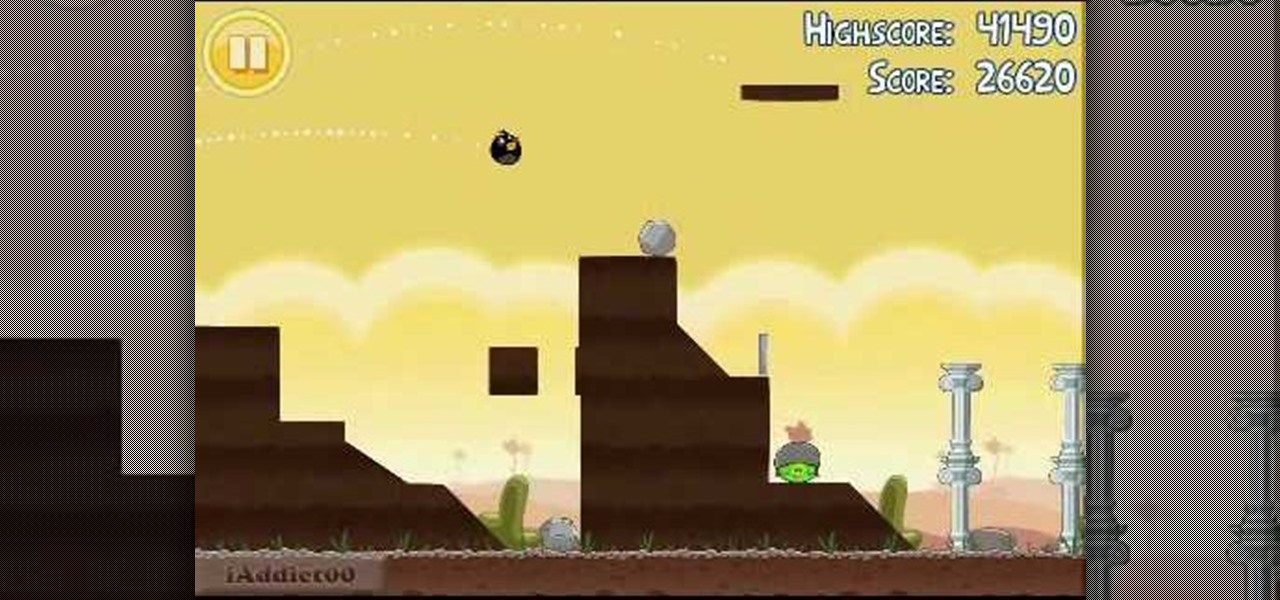
Your target in level 3-13 of Angry Birds is not so much a pig fortress but a series of pig-defended hilltops. Still no problem for a properly trained bird army. Watch the video for a guide to beating level 3-13 with three stars.