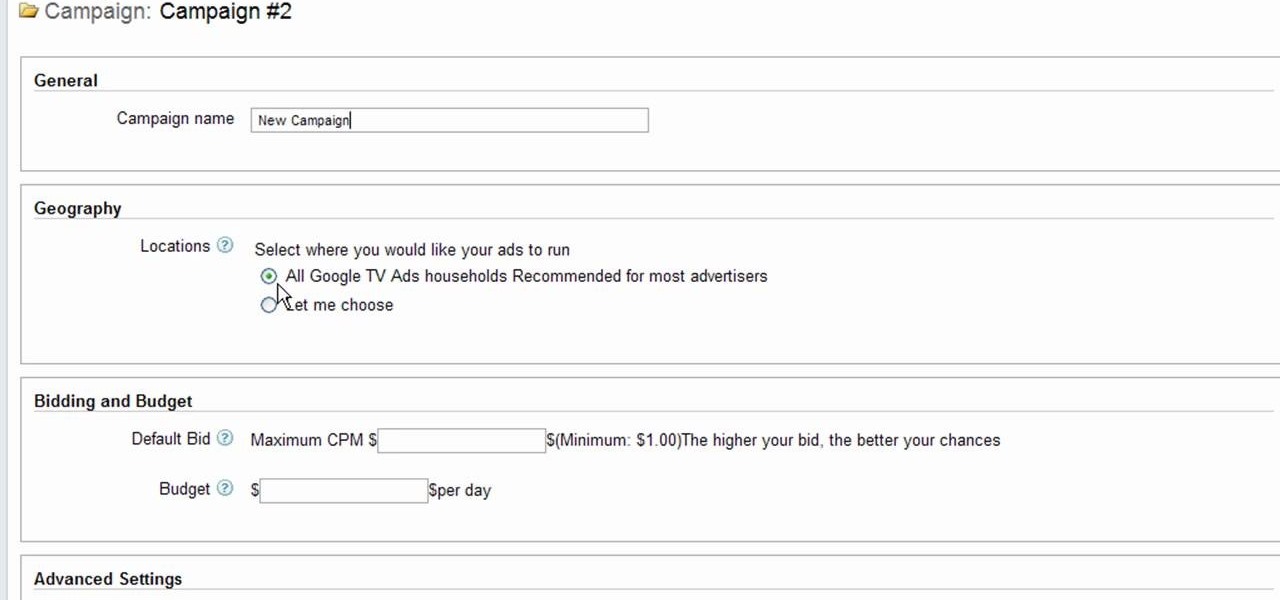
Interested to know how to start a new cable television ad campaign with Google AdWords TV Ads? This official video from Google will teach you how to use the new interface to determine just that. For all of the relevant details, and to get started creating your own televised advertising campaigns, watch this clip.

It's been a few years since Finding Nemo became the highest-grossing animated film of all time, but it's cultural appeal lingers on. If you want to capture some of that Nemo cuteness for your Halloween costume, watch this video to learn how to make a really cute Nemo costume with no sewing required.

The ground and pound is one of the most controversial aspects of MMA fighting, and is a great chance for you to do a lot of damage to your opponent. In this video UFC fighter Joe Lauzon will show you how to use an elbow technique from guard to defend yourself and get a solid elbow shot in at the same time, using Joanne from MMA Girls as his target.
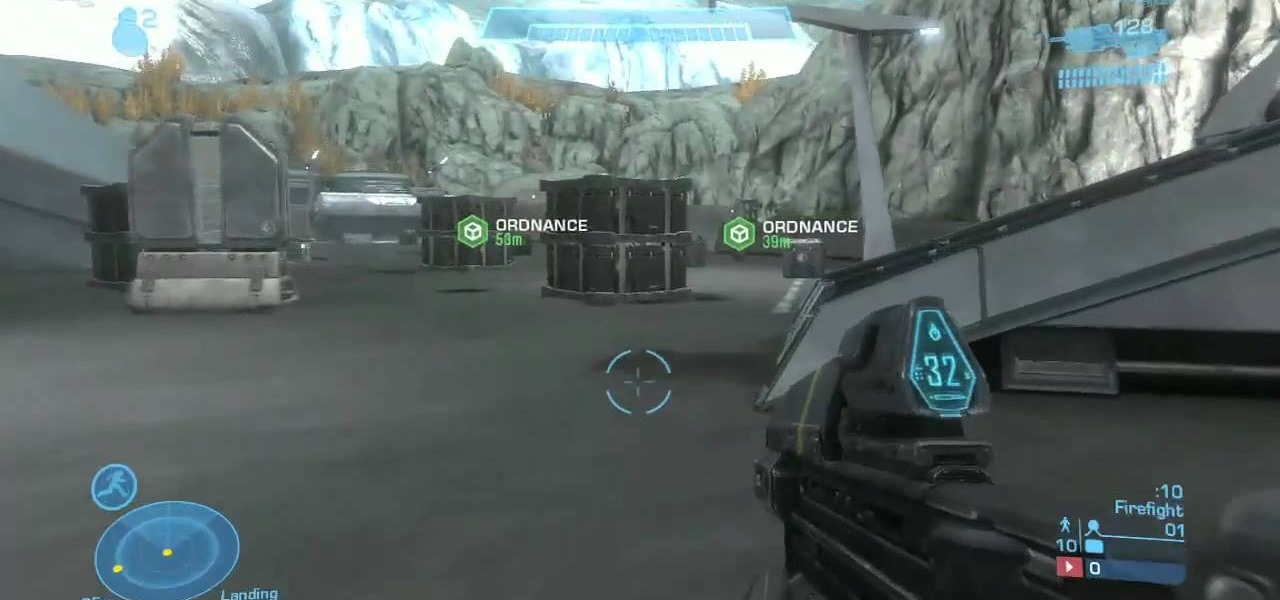
Halo: Reach has so many tough to get achievements, but the easiest one that you can get pretty fast is the "Crowd Control" achievement, and you can get it on Courtyard using the target locator. In this video you will learn how to effectively kill off multiple Covenant drop ships to get the achievement in about five seconds!
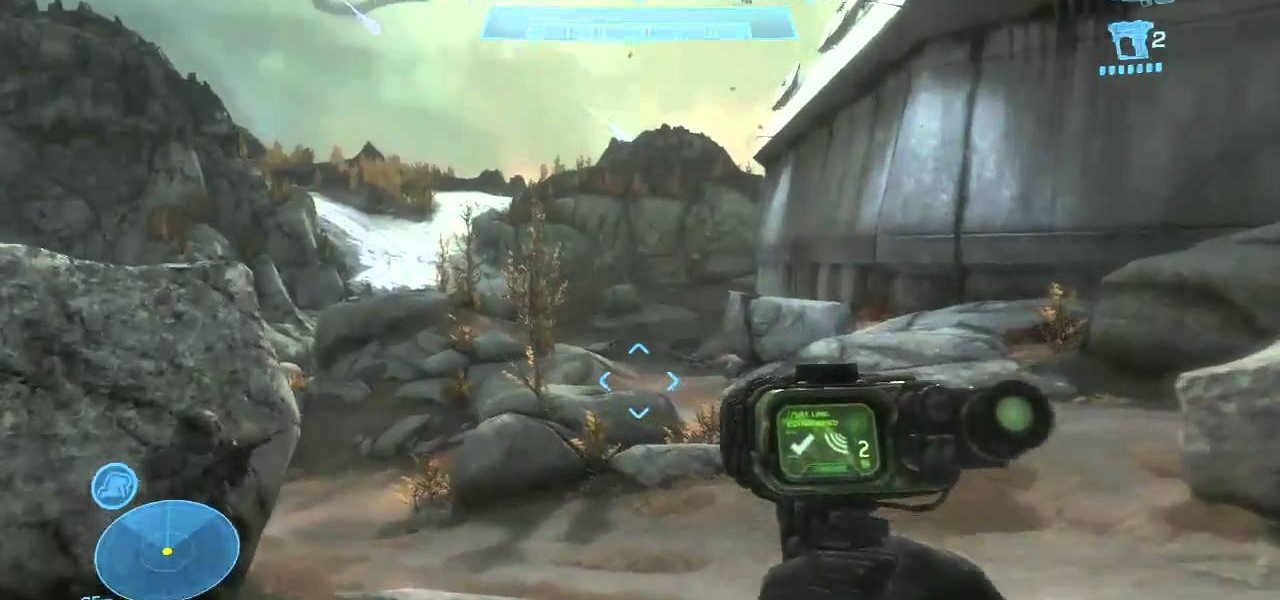
Two Corpses in One Grave is a difficult achievement in Halo: Reach if you don't know where to look on mission 3. You will have your chance right after you acquire the Target Locator when two Wraiths show up for the killing! Just be sure to aim straight and true and you will be alright!

Thanks to modern technology, we don't have to visit our nearest Target or Rite Aid to get our pictures professionally retouched and printed. With many printers offering photo-quality ink and paper companies that offer photo-quality paper, you can use your home printer to create professional-grade photos.

If you're planning to become a veteran yogini, you'd better start practicing and loving the up dog pose now, because you'll be spending the greater part of your yoga flow doing up dogs and down dogs.

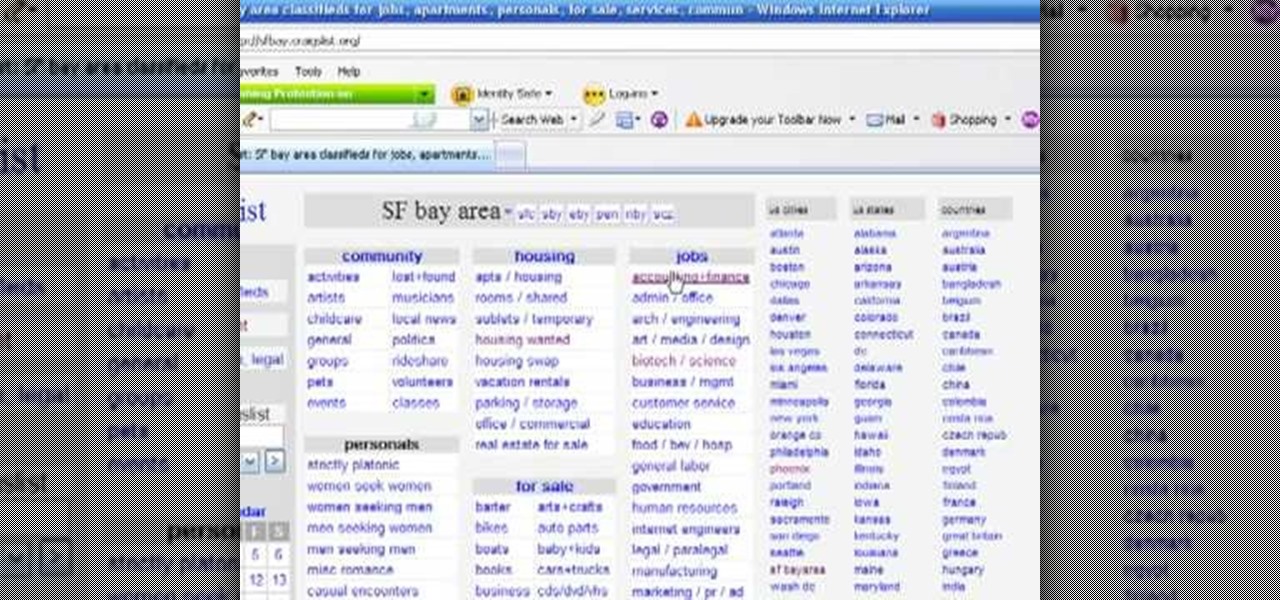
Sometimes searching Craigslist can be a real hassle if you're looking for something specific. You really have to sort your way through all the clutter in order to find whta you're looking for. If you are looking for email addresses of people who might fit your target market, you can scrape Criaglist for emails. This video will show you how.

In this episode of Hak5, Darren shows us a USB key, dubbed the USB Hacksaw, that instantly and silently installs on target Windows 2000 or higher computers with guest or higher privileges which will monitor USB ports for flash drives and automatically download their contents for silent archival and email. For detailed instructions on replicating this hack yourself, watch this video hacking tutorial.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Trying to score all of the achievements in Duke Nukem Forever? Here's a DNF walkthrough that will show you how to earn the I Need a Date achievement. This achievement is in the Shrunk Machine chapter of Duke Nukem Forever for Xbox 360.

Ever wished there were an easy way to delete files according to when they were last opened? Well, there is. And it's called Delete Files by Date. This home-computing how-to from the team at Tekzilla has got the scoop. For more information, including detailed, step-by-step instructions, take a look!

In this webmaster's guide, you'll learn how prevent Google from displaying the date when presenting a snippet from your website. Whether you're new to the world of search engine optimization (SEO) or are merely looking to pick up a few new tips and tricks, you're unlikely to find a better source than this official video guide from Google. Take a look.

Applying makeup for a date is always tricky. You can't go too heavy or else you'll look like you're trying too hard, but if you put on too little you'll just look tired and like you didn't make an effort.

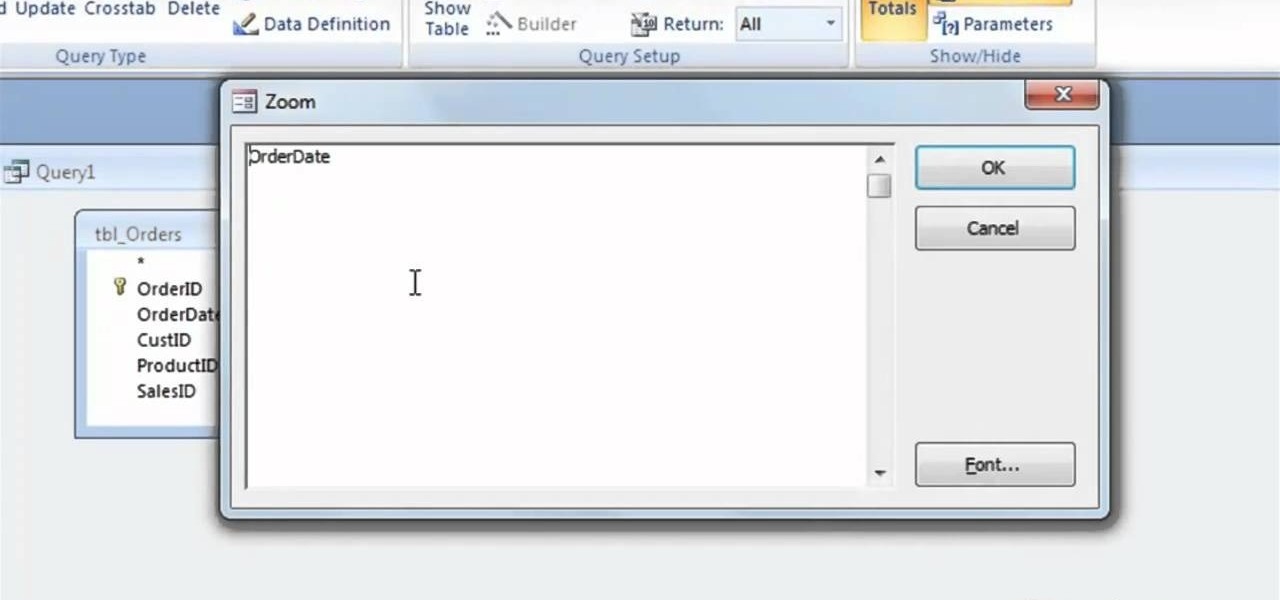
Looking for a quick guide on how to utilize date & time functions in your Access queries? You're in luck. Whether you're new to Microsoft's popular data management application or a seasoned MS Office professional just looking to better acquaint yourself with the Access 2007 workflow, you're sure to be well served by this video tutorial. For more information, including step-by-step instructions, watch this free video guide.

Have an important date you're looking to get sexy for? In this video presented by Jennisse Makeup, learn how to get dark, black dramatic smoky eyes - perfect to lure him in with! Steal this smoldering smoky eye for your next date to make his heart beat a littl faster!

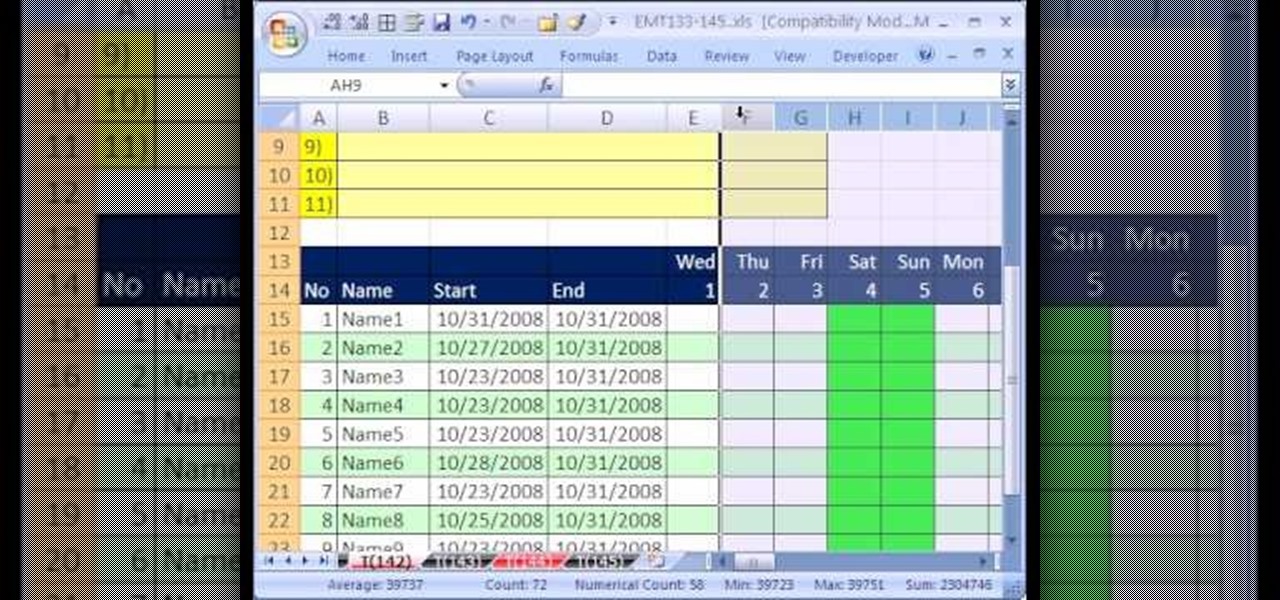
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 142nd installment in their series of digital spreadsheet magic tricks, you'll learn how to create a complex array formula that counts weekends between two dates with the SUM, IF WEEKDAY, ROW and INDIRECT functions.

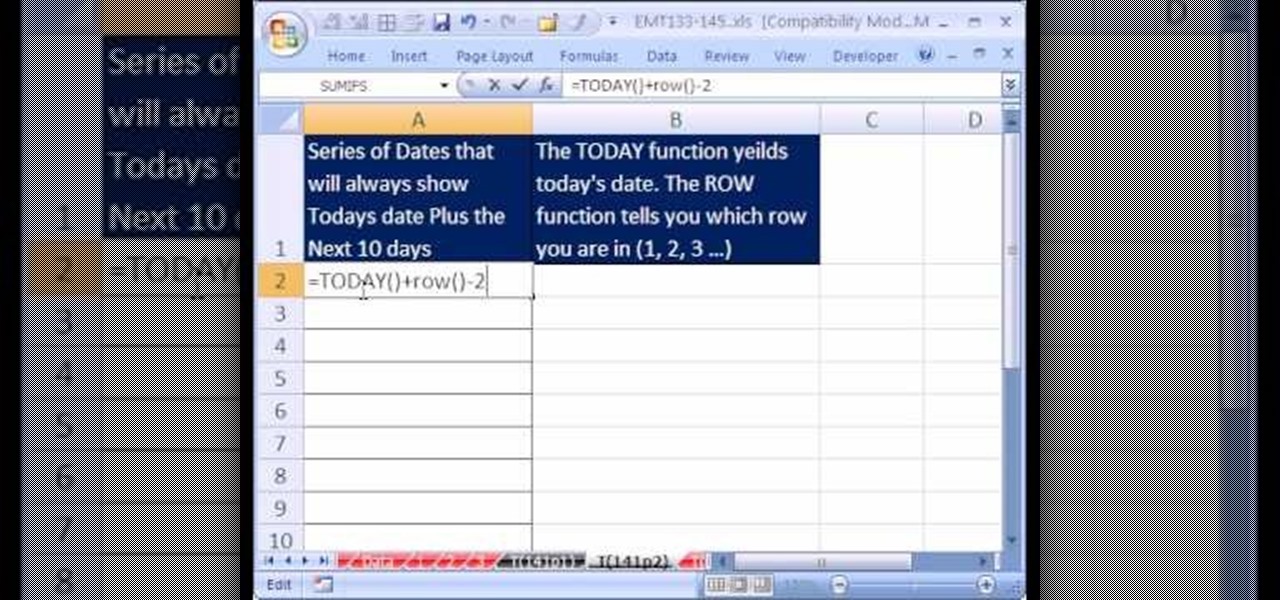
Love Microsoft Excel? This clip contains a tip that just might induce you to. With this free video tutorial from ExcelIsFun, the 141st installment of his "YouTubers Love Excel" or YTLE series of free video MS Excel lessons, you'll learn how to generate a series of dates with the TODAY and ROW function that will always show today plus the next 10 days.

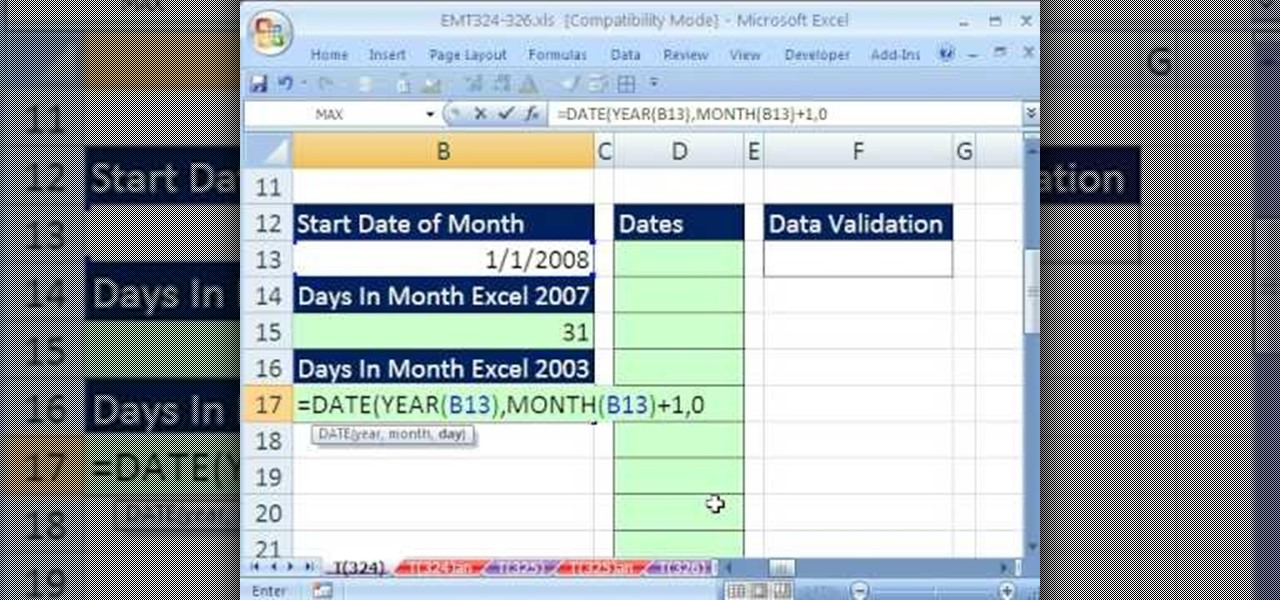
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 324th installment in their series of digital spreadsheet magic tricks, you'll learn how to create a dynamic list of dates for a data validation drop-down list.

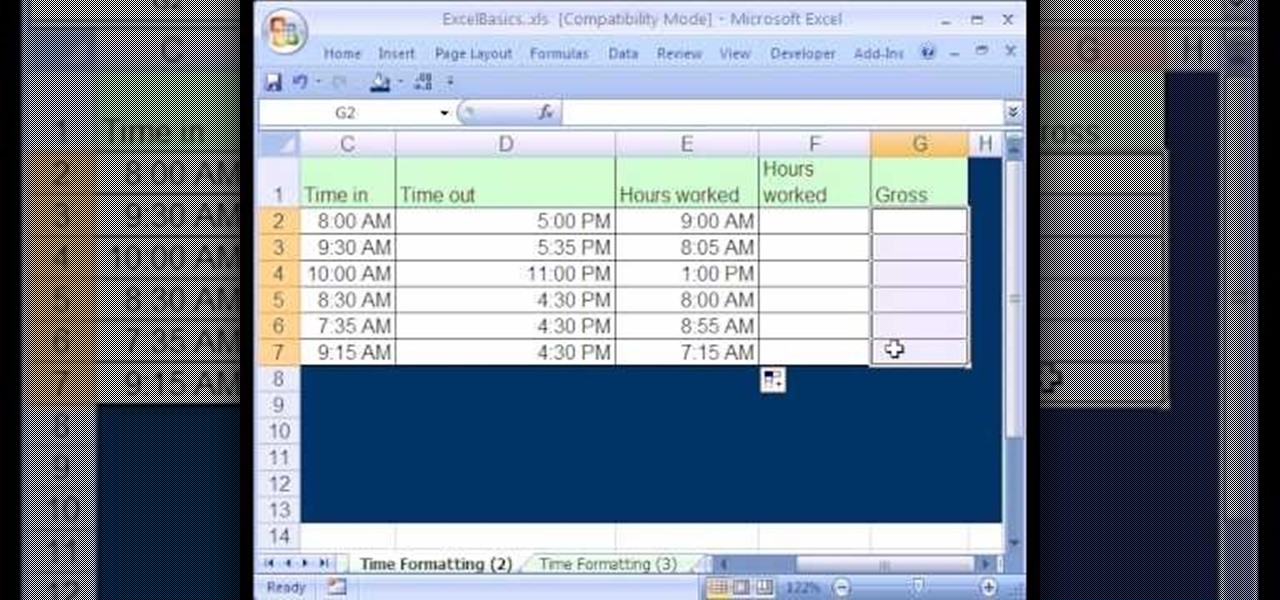
Once you learn some of the basics, Excel is an easy program to use. With the use of some simple formulas, you can streamline your whole data entry process. Just by typing in =SUM you can set a row or column to show the sum of other entries. It really is that easy. This video will show how to use these formulas and take advantage of Excel date math and time formatting.

See how to quickly add watermarks, date stamps, and time stamps to digital photos using Mark IT Now! software with Bill Myers.

This is a video lesson on the days of the week, months, and dates in Portuguese. Listen, repeat, and rewind as needed.

SEO specialist Aaron Wall shares tips on using date based search filters to help you improve your search engine optimization knowledge.

Talking on the phone with a girl you like for the first time can be nerve wracking. Luckily, The Wing Girls are here to help with their honest and earnest dating & relationship advice. Learn how to get past that first phone call and get comfortable on the phone with your crush with tips & tricks given here!

It’s easy to make a Libra fall in love with you – but it’s just as easy to lose their love. To trap a Libra you will need elegance, generosity and patience. Learn how to use astrology advice in dating, by watching this how-to video. Pick up tips on making a relationship with a Libra work.

You will always remember your first kiss, so try making it a good one. This how-to dating advice video will show how to prepare for that first kiss you have been waiting for. To practice kissing you will need a partner, a suave technique and a mirror. Choose some one who will is willing to kiss you and be courages when going in for your first kiss.

If you want a tight, lean stomach and obliques so sculpted you'd make Jillian Michaels jealous, then the only way to get what you want is to complete alternating days of cardio with strength training.

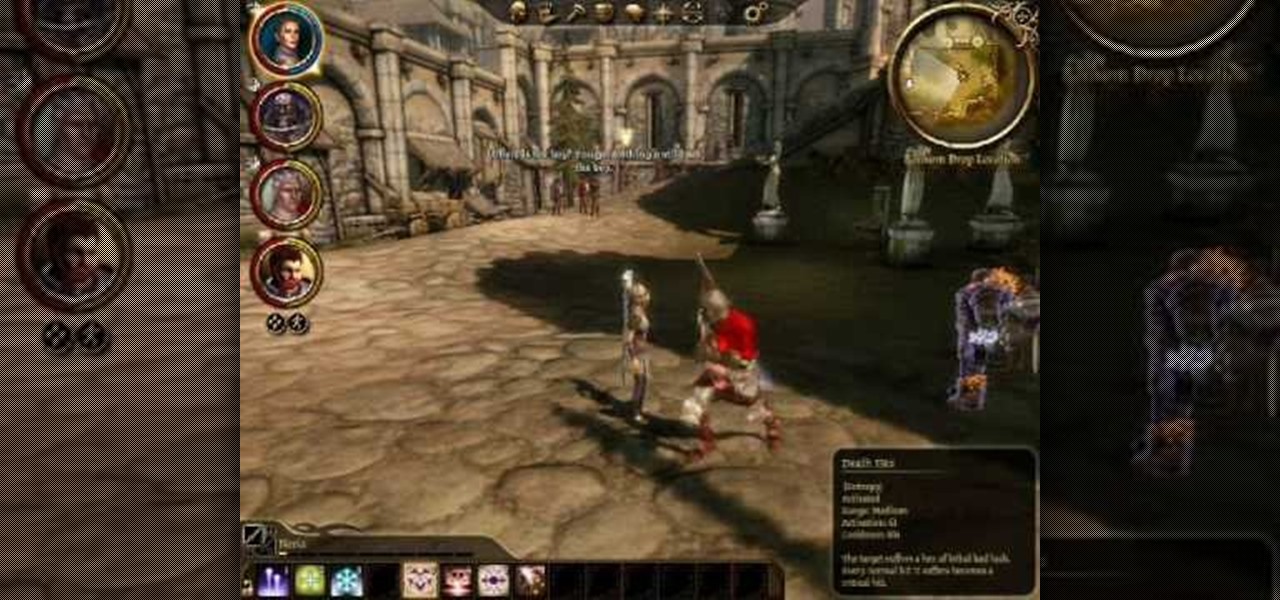
By combining different spells on the same target, or combining spells with other effects, you can do some devastating damage in Dragon Age: Origins. Turn your mage into an archmage by mastering effects like Paralysis Explosion, Grease Fire and more (including the deadliest, Storm of the Century)!