If shield kicking is legal in your game, here's how you can safely and effectively kick your opponents shield (and perhaps even knock them down). Know what's a good target, and a good way to deliver the kick without exposing your leg to be hit in turn.
In this tutorial, we learn how to create and edit tasks in MS Project 2007. Before you begin, you need to set the start date by going into project information and changing the start date and end date. After this, type in your first task name, then enter in the information that goes with it. After you have entered this, press the check mark to set it up. After this, enter in the other task names that you need to specify in your project. When you are finished, you will need to save this onto yo...

This next video, is a great blend of woodworking and technology. In the tutorial, you'll be finding out how to create a wooden frame for the small digital picture keychains that can be bought from stores like Target and Best Buy. It's a great gift idea for parents, relatives, or just for you. So check it out, take notes, and good luck!

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 353rd installment in their series of digital spreadsheet magic tricks, you'll learn how to make date calculations with Excel's VLOOKUP formula (e.g., finding approximate matches and returning a season for a date within a given range).
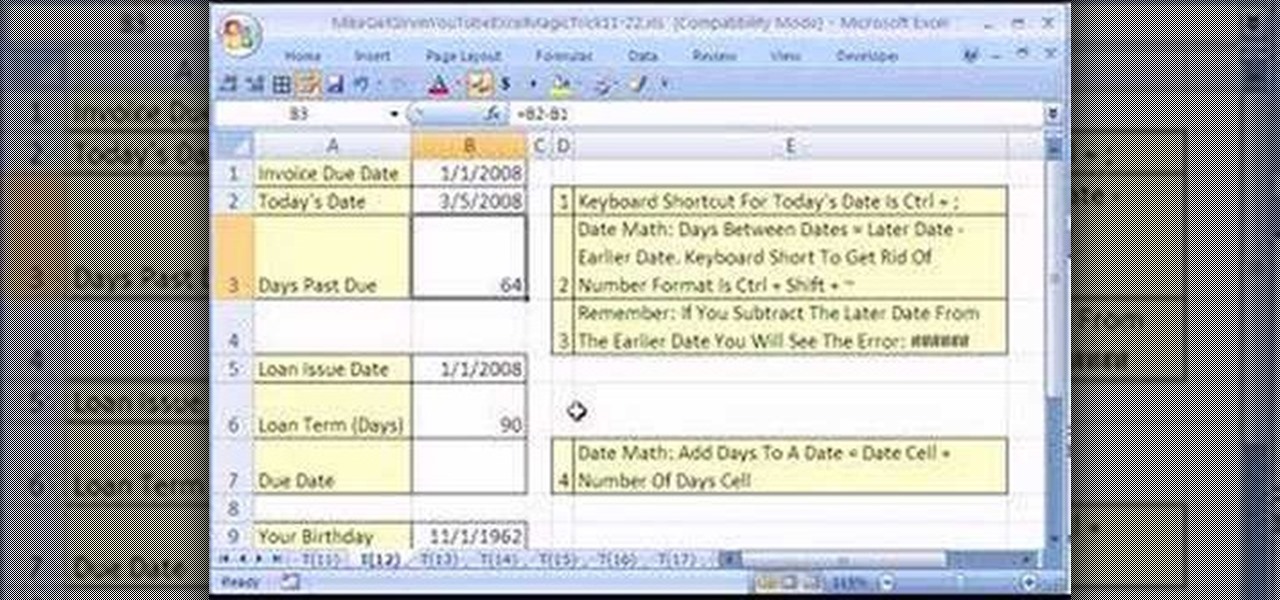
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 12th installment in their series of digital spreadsheet magic tricks, you'll learn how to calculate the time between 2 dates like invoices past due. Learn how to calculate a loan due date or how many days you have been alive!
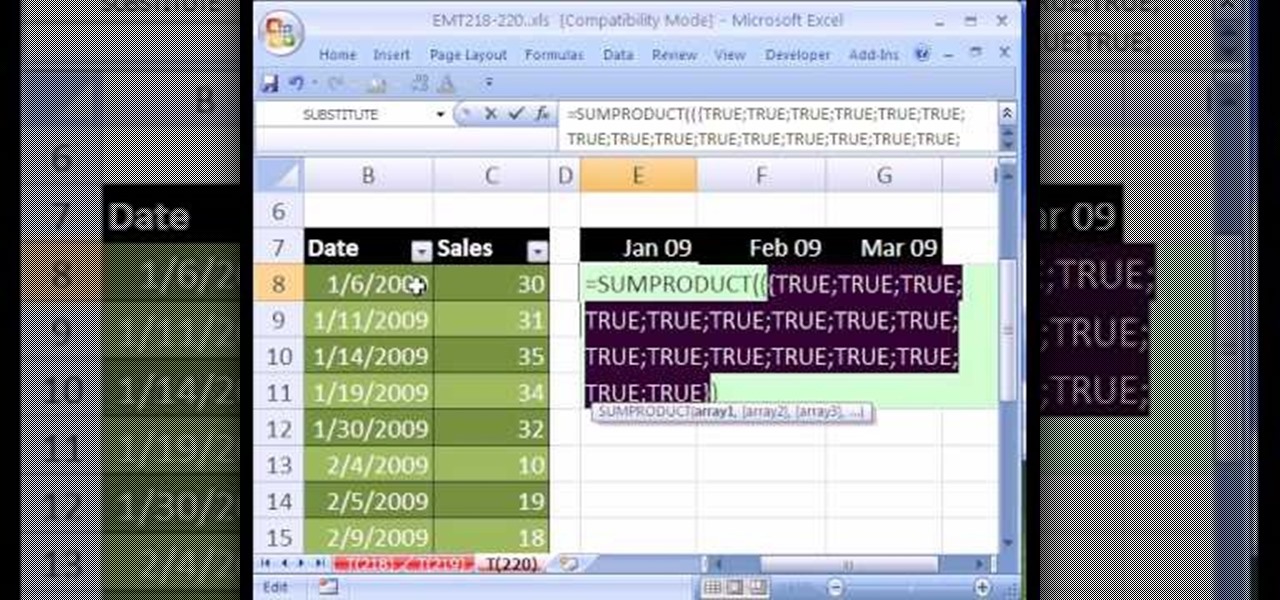
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 220th installment in their series of digital spreadsheet magic tricks, you'll learn how to create a formula with the SUMPRODUCT and EOMONTH functions that count the dates in each month for a given range of dates.

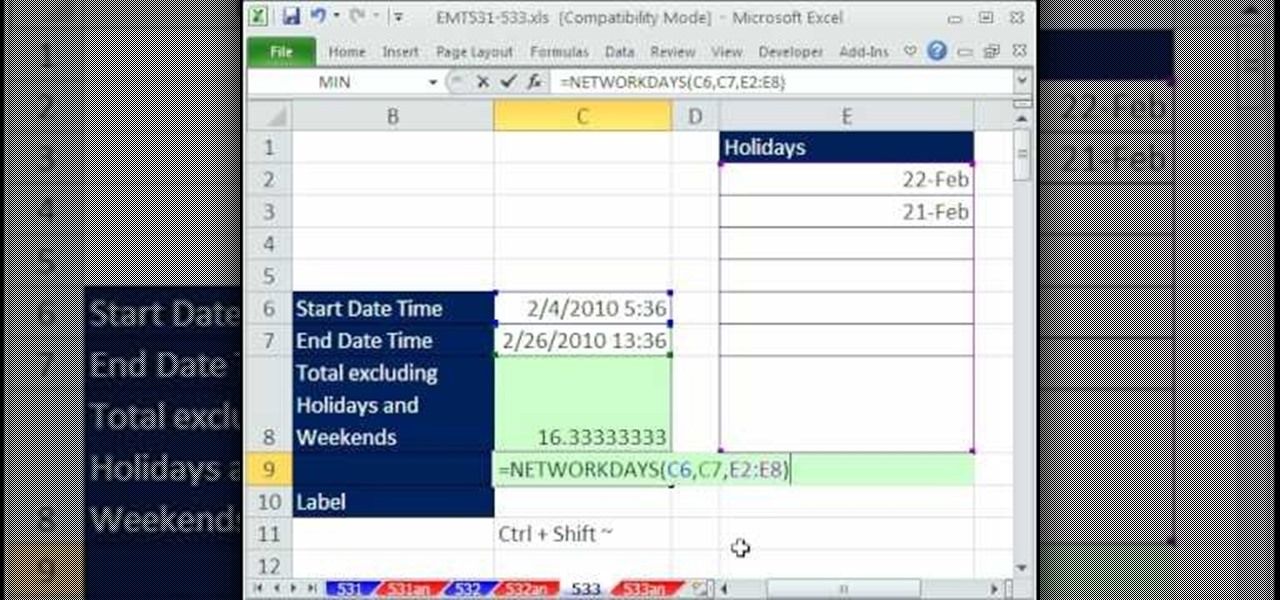
New to Excel? Looking for a tip? How about a tip so mind-blowingly advanced as to qualify as a magic trick? You're in luck. In this Excel tutorial from ExcelIsFun, the 533rd installment in their series of digital spreadsheet magic tricks, you'll learn how to create a formula to calculate the difference between start date/time & end date/time excluding holidays and weekends. This is accomplished with recourse to Excel's NETWORKINGDAYS and MOD functions.

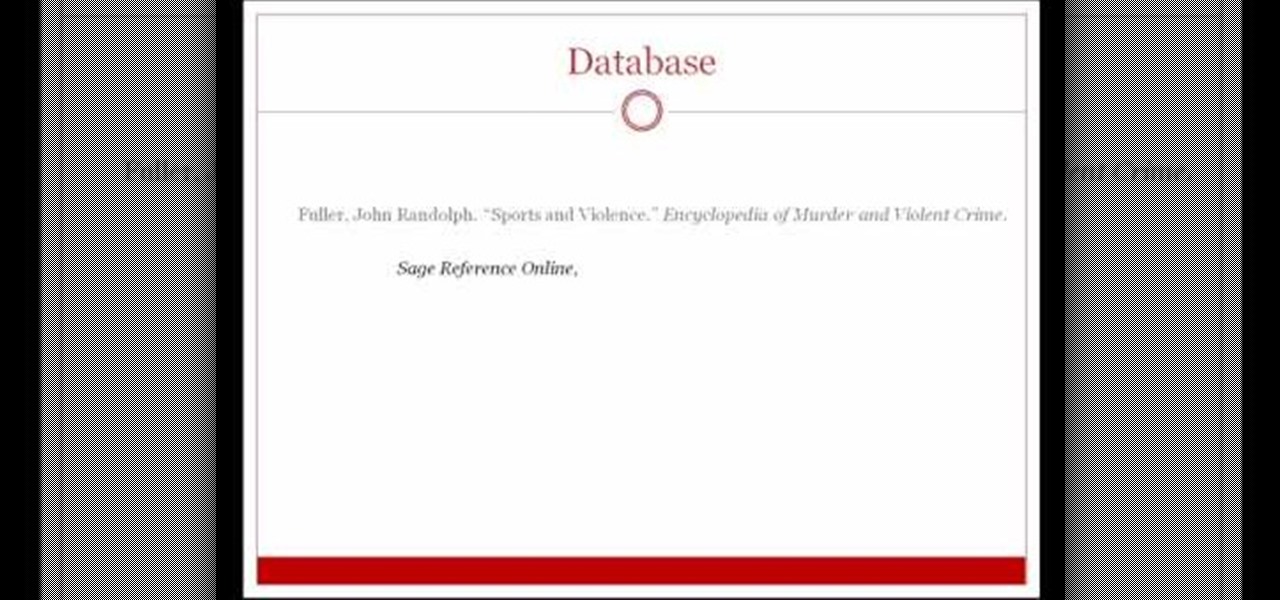
In this video tutorial, viewers learn how to cite reference books in MLA formats. Citation is a reference to a published or unpublished source. Viewers will learn how to cite an article in an online reference book and an article in a print reference book. The format for the online reference book is:

Practice lineout throws for rugby from the Ford Academy in Australia. Throwing the rugby ball with two hands overhead. It is important to focus on targeting, speed and your teammates. A lineout throw is made when the ball goes out of bounds and you need to reenter it into play.

Want to improve your tennis skills? Check out this instructional tennis video that demonstrates how to hit a tennis ball across the court in this video tennis lesson.

Check out this instructional baseball video that demonstrates how to play infield. This video offers a few tips for fielding ground balls. Learn how to make a play on a grounder from a professional in this baseball video.

There is not better way to get in shape and target trouble zones than with the help of some experts in fitness and some simple workout equipment. In this how to video tutorial SELF Magazine shows you how to tone and sculpt your body with a simple beach ball. Tone difficult areas with tilt-a-whirls, dipsy dos, squeeze play, close reaches, reverse lunges, pendulums, hold your own and tummy toner exercises.

Don't have time for a workout? Then watch this how to video to learn how to do a five minute workout that will get you six pack abs. These exercise will target your upper abs, lower abs, and obliques.

Watch this photography video tutorial to learn how to put date and time on your photos only when you want it. Date and time stamping on your Canon A550 will be easy once you've mastered the tips in this helpful how-to video.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

After opening up its Spark AR platform on Instagram for all creators, Facebook is already expanding the platform's capabilities on its Snapchat killer.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

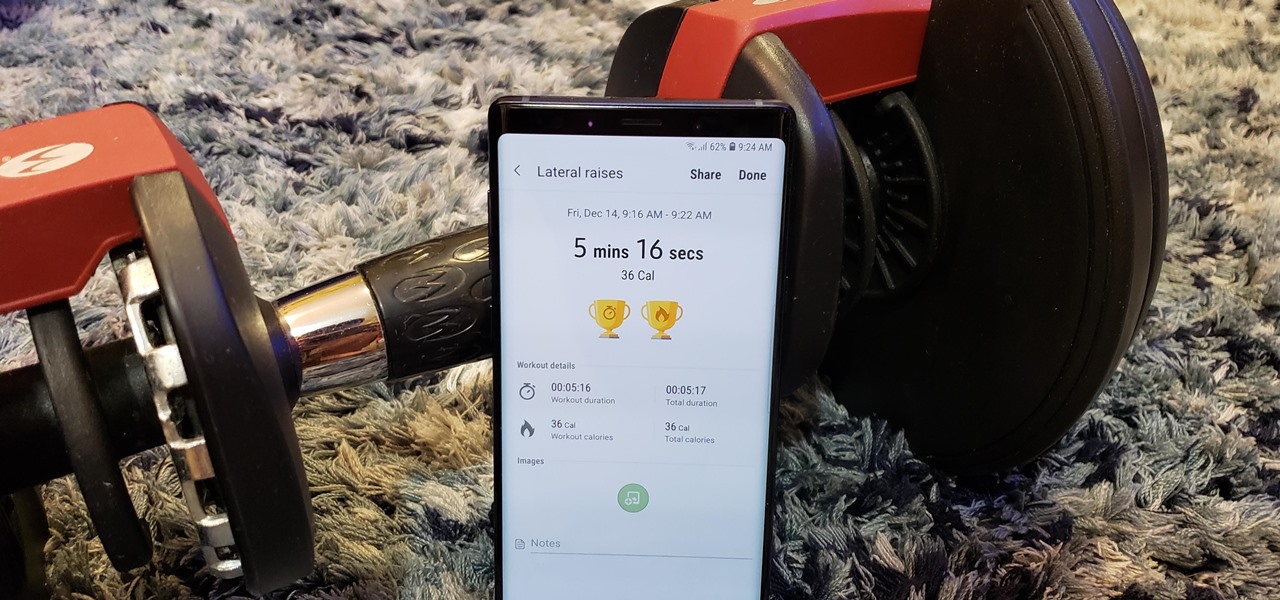
Keeping track of your physical activities can be difficult, especially if you have a hectic lifestyle with responsibilities to constantly stay on top of. Thankfully, Samsung Health is there to help you log your workout routines, leaving you with one less thing to keep track of as you go about your busy day.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Virtual reality headsets aren't new, but they may be something you or someone on your holiday shopping list hasn't experienced yet. If you're going to dive into the world of smartphone-based virtual reality, the best time to do it is during Black Friday when all the good sales are going on.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

As with any new releases, full updates that completely revamp the look and feel of your iPhone's operating system will have teething problems that eventually get ironed out with incremental updates. iOS 11, with its issue of not being able to connect to the App Store on some iPhones and iPads, is no exception.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

bObsweep robotic vacuums automatically clean whenever instructed to do so by an owner or because of a pre-programmed schedule.

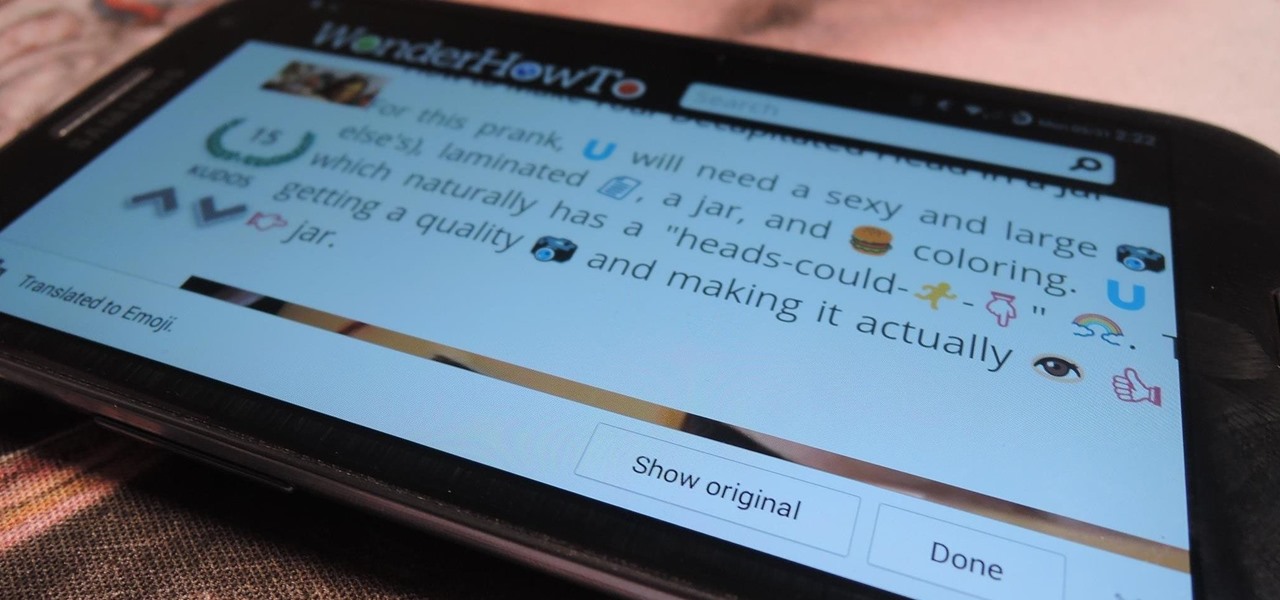
First, they came for our Pokémon...now it's an emoji takeover. Adding to the flurry of Google related April Fool's Day jokes, Chrome for Android and iOS has a new hidden functionality: translating the web to emoji!

DATING & RELATIONSHIP IN FRANCE VS. THE U.S This video compares and helps understand dating and relationship concept in France Vs. in the U.S.

Wine and dine your way into her pants by pudding. This snarky lesson on dating will help you to land a girl through proper dinner. Pants by pudding. Meaning you want to get is a good meal and a girl in love with you.

Playing hard to get doesn't work with a Scorpio; they only respond to slavish devotion. So drop everything and dedicate your time solely to the Scorpio in your life. Learn how to use astrology advice in dating, by watching this how-to video. Pick up tips on making a relationship with a Scorpio work.

Are you on the prowl looking for a boyfriend? Are you in need of some flirting techniques? Watch Love U to find out how to hook your honey in a hurry. Learn how to flirt like there's no tomorrow with this dating instructional video.

How To Make Yourself Irresistible to Girls. You don't have to be tall, dark, handsome, and rich to be a ladies' man. Just learn to recognize what women want. Female friends can provide some insight. Watch this video dating tutorial and learn how to make yourself appealing to women.

Looking for a yummy, nutritious on-the-go snack? Granola bars are perfect for easy to carry breakfasts or mini-meals. With this tutorial, learn how to make two different granola bar flavors at home, and save yourself the trip to the grocery store!