Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.
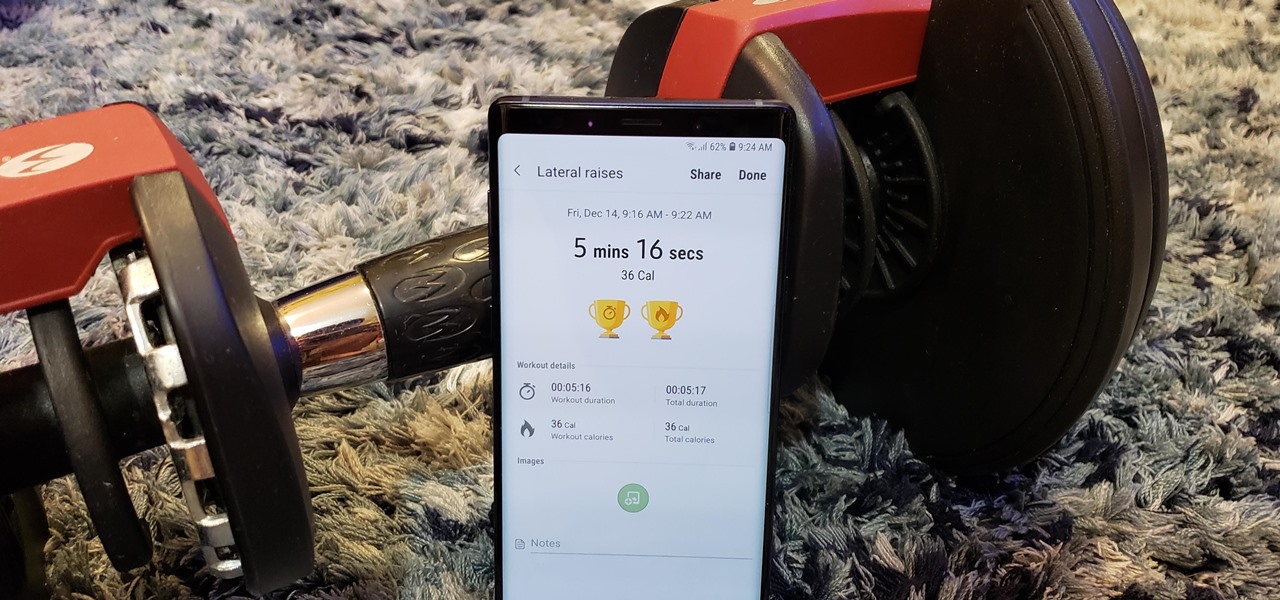
Keeping track of your physical activities can be difficult, especially if you have a hectic lifestyle with responsibilities to constantly stay on top of. Thankfully, Samsung Health is there to help you log your workout routines, leaving you with one less thing to keep track of as you go about your busy day.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Virtual reality headsets aren't new, but they may be something you or someone on your holiday shopping list hasn't experienced yet. If you're going to dive into the world of smartphone-based virtual reality, the best time to do it is during Black Friday when all the good sales are going on.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

If you've accidentally turned on "Read Receipts" for all of your iMessages, there's an easy way to disable it so that no one knows when you're actually reading their incoming messages. You could also pick and choose which conversations can see that you've read their messages if you don't want to kill the feature entirely.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Composite figures are composed of several geometric shapes and are three-dimensional shapes. The first composite shape is a combination of a rectangular prism and a pyramid. To find the volume of the entire shape you find the volume of each individual shape and add them together. The second figure consists of a cylinder and a hemisphere. Check out the video below for the full lesson.

The San Diego Film Community and the families of Down Syndrome individuals band together to make this great feel good PSA with a positive message.

The fun of gambling can come at a hefty price. Problem gambling affects 331, 000 individuals and can quickly destroy families and lives. Know the risks. The Responsible Gambling Council offers a free Cost2Play Calculator app and safe gambling tips atwww.noregrets.ca

In order to curve-hook a bowling ball, you will need the following: a bowling and a bowling lane. You should start by buying your own custom ball to fit your hands. The balls available in bowling alleys aren't designed to curve-hook.

How to make a liberty spike mohawk. Gather glue, freeze spray, a blow dryer, a brush, and some rubber bands. Brush hair until it is nice and fluffy. Take rubber band and perform spikes around your entire head. After setting your hair up in the spikes use the freeze spray to spray your hair completely. Inside and outside of the spikes. To ensure proper coating run your fingers through your hair especially at the base to make sure they stay up. With blow-drying blow-dry your hair while pulling ...

As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid for most situations he may encounter. A First Class scout is prepared.

Youtube comments - some of the most beautiful pieces of rhetoric displayed on the internet. There are any number of reasons why you may wish to link directly to a youtube comment. A specific youtube comment perhaps, one that captures the essence of the emotional response a viewer might have when watching that particular Youtube video.

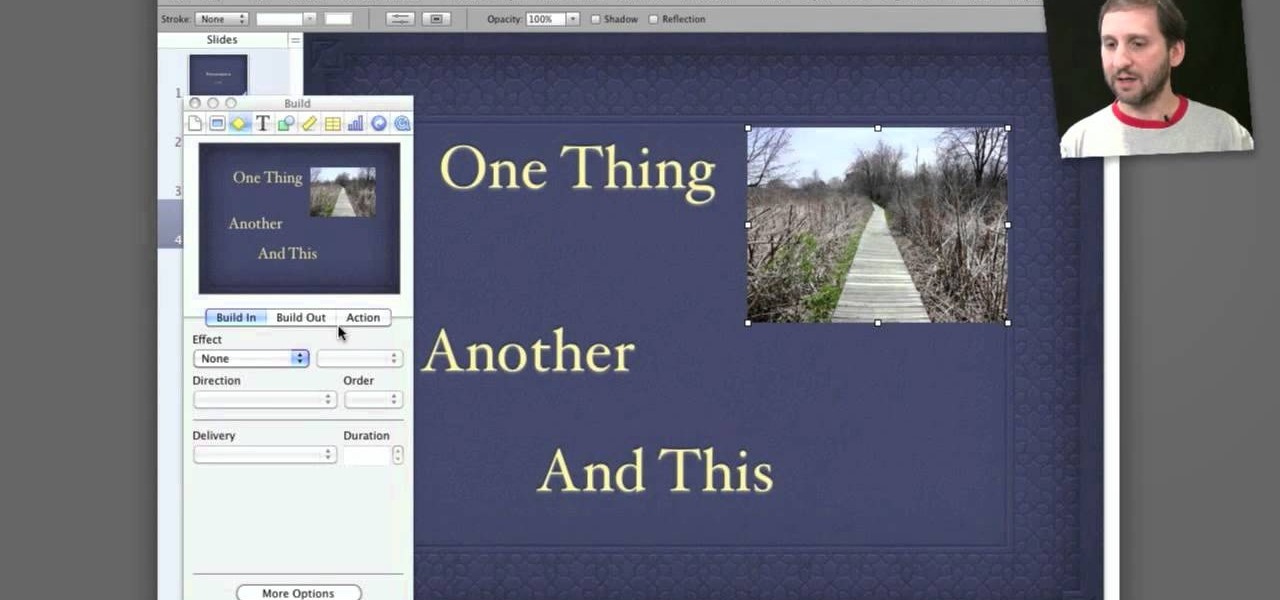
Apple's Keynote is a great piece of software, but one of the tricks is setting up transitions between slides. This how-to shows you clearly the way to get the look you want as you make your presentation.

In this video, we learn how to make spinach toast with leftover cream spinach. First, you will need to take small pieces of bread that you have leftover, as well as some cream cheese, parmesan cheese, and spinach (already cooked). Mix the spinach, cream cheese, and parmesan cheese together and add in some salt to taste. After this, spoon the mixture onto the individual pieces of bread and place into the oven. Let cook on a high temperature until the top and sides of the toast are light brown....

The Food Channel brings us this quick and easy recipe for making peach cobbler. Place the sliced peaches in a large bowl and add some sugar, lemon juice and cornstarch and mix together thoroughly so that the peaches are completely covered.

Cardtrickteacher takes us through one of his favorite card tricks, the Triumph card trick. He explains that this involves using the audience, which he adequately emulates using just himself. Showing amazing dexterity, he goes through the process of the card trick in real time at first, showing us how exactly the card trick would look in real life and leaving us astounded. He then systematically breaks down the card trick showing each individual step and explaining with such clarity that even ...

This video teaches individuals how to cook classic grilled chicken using a BBQ pit. The first step is to begin mixing one cup of vegetable oil and two cups of vinegar. The next step is to add your favorite chicken rub and mix it all together with a pinch of pepper. The instructor marinates his chicken for four hours before cooking. The next step is to put the marinated chicken into the BBQ pit grill to begin cooking. The instructor notes it only takes about 10min to seer both sides of the chi...

Changing the way the Bridge looks is a personal touch everybody can make to streamline their workflow. Changing layout settings in the bridge is actually quite easy and very helpful for customizing for individual needs. In this video tutorial, see the ways that you can change the Bridge's look and feel to suit your work environment and to free up the space necessary to have a comfortable working window. This video also covers the viewing options given to you by the Bridge to allow for quick a...

Jello shots are the perfect combination of dessert and alcohol. They're super tasty and usually beloved by everyone, but they're especially great teasers for those who are alcohol virgins and prefer to be ushered in to the world of Jack Daniels slowly. That's because Jell-o shots contain minimal alcohol and maximum flavor.

This is a video guide for measuring your foot and calf size correctly. This is important in order to properly fit shoes. It's a video intended for athletes and individuals sensitive to their foot and leg health. This is brought to you by a retailer that fits wide or narrow feet with proper shoes. You'll need a wall and a measurement guide. Measure for both feet and sometimes you have two different sized feet.

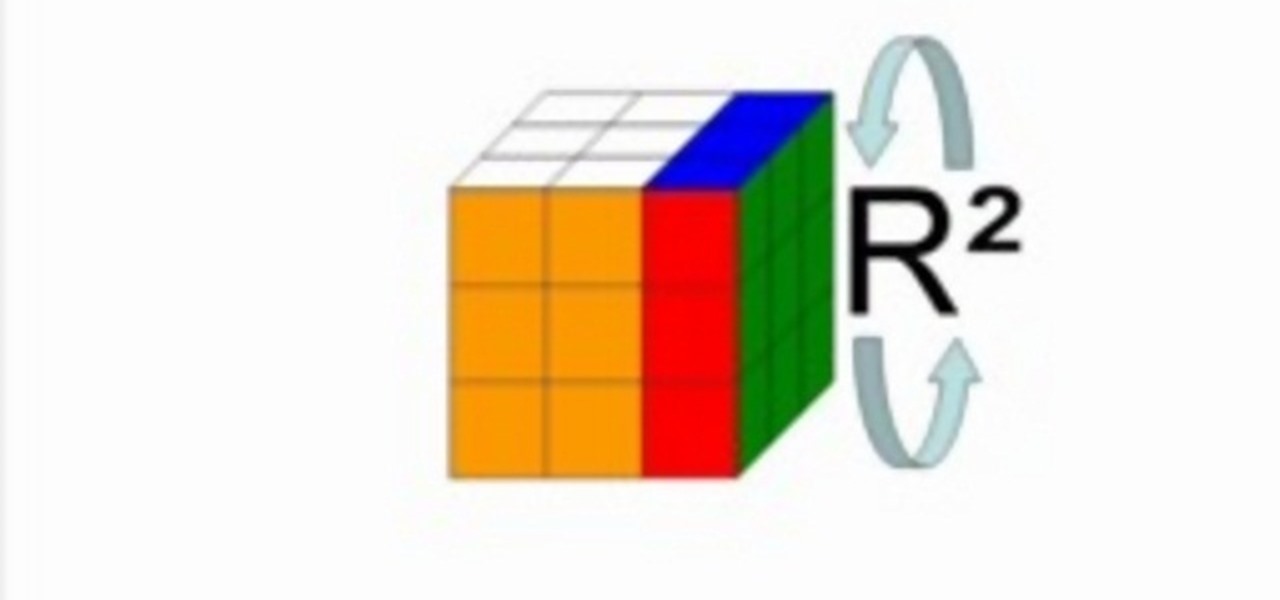
Since its invention in 1974, the Rubik's Cube has become a favorite pastime among geeks, puzzle lovers, and other similarly unique individuals. It is currently available in four basic flavors; Rubik's Mini, Rubik's Cube, Rubiks Revenge, and Professor's Cube. This video tutorial will cover the basic terminology and notation used in solutions for each.

If you are a beginner at hand embroidery, one of the first stitches you will probably learn is the chain stitch. The chain stitch has many variations, and one of them is the wheat stitch, also known as the wheatear stitch. This stitch is simple to work and produces a line that resembles a shaft of wheat. The stitch can be used in all kinds of applications - it would make great background greenery in flowers and gardens, it can also serve as a seam embellishment in crazy quilting, and it can s...

Lophophora harvest. This video is a quick demonstration on how I harvest Lophophora pups from grafted lophophora stock. When harvesting lophophora make sure of the following: Its spring or summer; You place your pups in a dry shady spot to heal; Also dust the mom and pups with sulfur to prevent rot.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

Magic Leap's legal battle against Nreal has taken an intriguing turn this week, as Magic Leap set a date to discuss the matter with Nreal. But a new partnership struck by Nreal adds another wrinkle to the duel between the two AR wearable makers.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.