Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

Big-box retailer Target has been on a bit of an augmented reality advertising shopping spree via Snapchat lately.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.
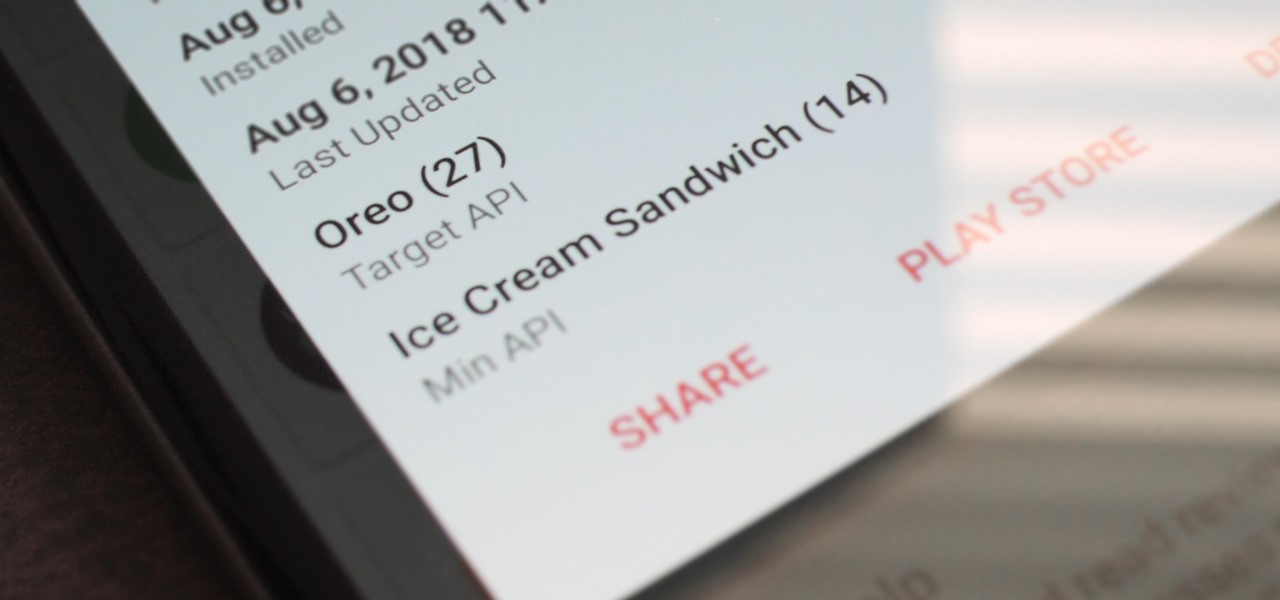
Starting November 1, 2018, Google will require that all new apps and updates to existing apps target Android 8.0 Oreo or higher. This move means the developers behind many of your favorite apps are now scrambling to get their software modernized, while others are considering abandoning outdated apps altogether.
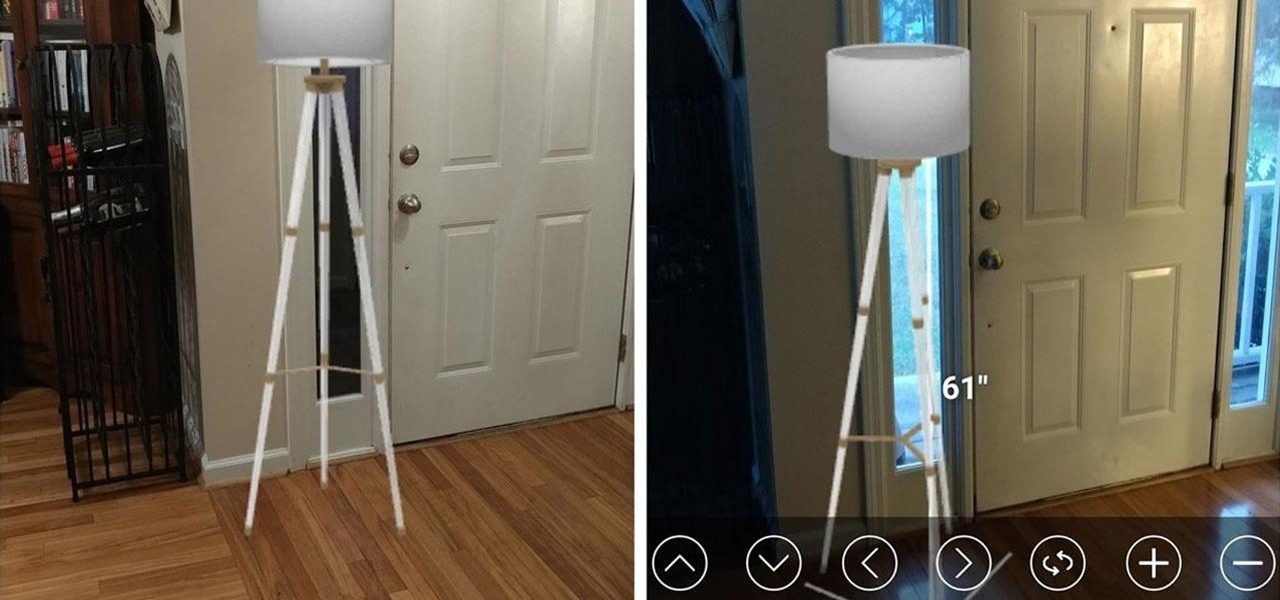
While some companies like IKEA and Lowe's zig towards ARKit to entice shoppers, Target has opted to zag to broader appeal with an augmented reality see-before-you-buy tool for its mobile website.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

This video explains how to throw a football like a quarterback. With your elbows bent at a 90-degree angle, hold the ball in front of your chest with the fingers of your throwing hand across the laces of the football.

In this free video exercise lesson, you'll learn a popular variant on the push-up, one designed to target your triceps. With pushups, as with any body-sculpting exercise, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. For more information, and to get started using this exercise yourself, watch this handy home-fitness how-to.

Learn how to use the Target Adjustment feature in Adobe Photoshop CS5. Whether you're new to Adobe's popular image editing software or a seasoned graphic design professional just looking to better acquaint yourself with the unique features of Photoshop CS5, you're sure to find something of value in this free video tutorial.

There comes a time in many tattooed individuals when they want to remove their tattoos. There are a lot of different ways to remove tattoo but they all cause scar. Dr. Neal Schultz explains only laser tattoo removal will not leave a scar and give a cosmetically-superior result. Laser energy is specifically targets the colored pigment of the tattoo so it only damages the colored pigment. It does not damage any of the surrounding skin. When people are treated for tattoos, it can take 8-12 treat...

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Department store chain Target is the latest retailer to offer an augmented reality cosmetics app for customers to virtually try on lipstick.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

This video will show how to target your facebook post for a specific audience. With this tutorial video you could target a set of audience who has interest about the post.

It's a real challenge to create exploding targets that can be set off by low velocity projectiles, yet remain safe to handle without risk of ignition during construction.

In this tutorial, we learn how to unlock the Tank Dropper achievement in Halo 3. This is an easy achievement that you will do when you first start out in the level. This is where you have to drop a tank onto someone and kill them. To do this, you need to stand up on a higher area and find your target. Once you do this, you will be able to grab the tank and then drop it onto the target you have found. After this, you will get the achievement and you will be able to continue on. If you miss, ju...

NJStar is a program which you may purchase online, and which will allow you to translate individual Chinese characters. This tutorial shows you how to use the software, and explains the limitations of the progam (it cannot translate whole paragraphs, for instance).

In this video we are shown a workout that targets your stomach and helps you to lose belly fat and tighten your lower abs.

This video details how to do easy yoga poses for beginners. To start out, assume 'mountain pose' which involves placing the feet at about a hip width distance apart. After the feet are placed, lengthen up through the spine and roll the shoulders back while also tucking the chin slightly back. Arms are then raised upward while inhaling, and lowered while exhaling and in the same exhale lift out of the hips, hinge, then enter a forward bend. Note, it is acceptable to bend the knees in this proc...

Learn how to mingle. If the idea of walking into a room full of strangers strikes fear into your heart… welcome to the club. But there are ways to overcome this common social phobia.

This tutorial teaches you how to apply individual false eyelashes video tutorial. Applying individual false eyelashes is a great way to achieve a dramatic and glamorous evening look. You will need individual false eyelashes, individual false eyelash glue, a piece of tin foil, a small pair of scissors and a pointed pair of tweezers. Apply your desired eyeshadow first, a light shimmery eyeshadow creates the best effect for this look in terms of contrast against the false eyelashes. Pour a very ...

Take a look at this instructional video and learn how to fit a projected image onto a target surface with Johnny Chung from Carnegie Mellon University. Typically, you'd need to use a screen to be directly in front of the projector and at a very specific orientation to get an undistorted image. What this tutorial is trying to accomplish is to place a screen at any location that is convenient and then calibrate the projector onto the target surface. This technique is used to automatically disco...

This video tutorial demonstrates the steps for drafting a sloper that shows the exact shape of an individual's body between the waist and the hips. It can be used to create skirts for women, the top of pants for men and women, and body doubles (aka Dress Forms). Learn how to draft a lower torso sloper by watching this video fashion design tutorial.

The object is to pass to ball between the cones in as few shots as possible, watch and learn how to do this target passing soccer drill.

All-American Skeet Champion Todd Bender explains the safety "does and don'ts" of shooting clay targets. He shows how everyone in the family can enjoy the game and still use proper gun handling techniques.

People like Ralphige and The Jerky Boys have elevated prank phone calls to an art. Here’s how you can get in on the fun.

In this video tutorial, Chris Pels will show how events are handled in master and individual content pages. Even though the end result of a master and individual content page is a single ASP.NET page rendered in the user's browser the event handling in each type of page is handled separately. If a control is located in the master page the corresponding event handler is located in the master page by default. The same is true for controls in the content page. See two approaches to having the ev...

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

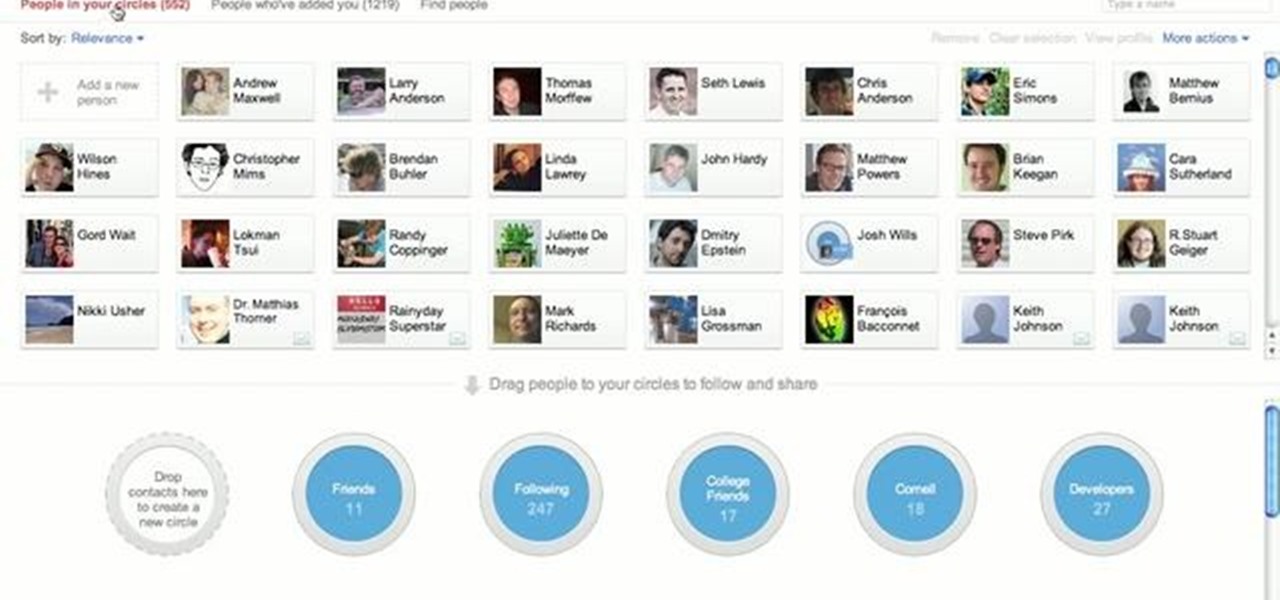
In addition to being a great way to share content and information that are also using Google+, additional sharing features in Google+ allow you to send content and information to other individuals who do not use the service. You can even import your address book to make sharing even easier.

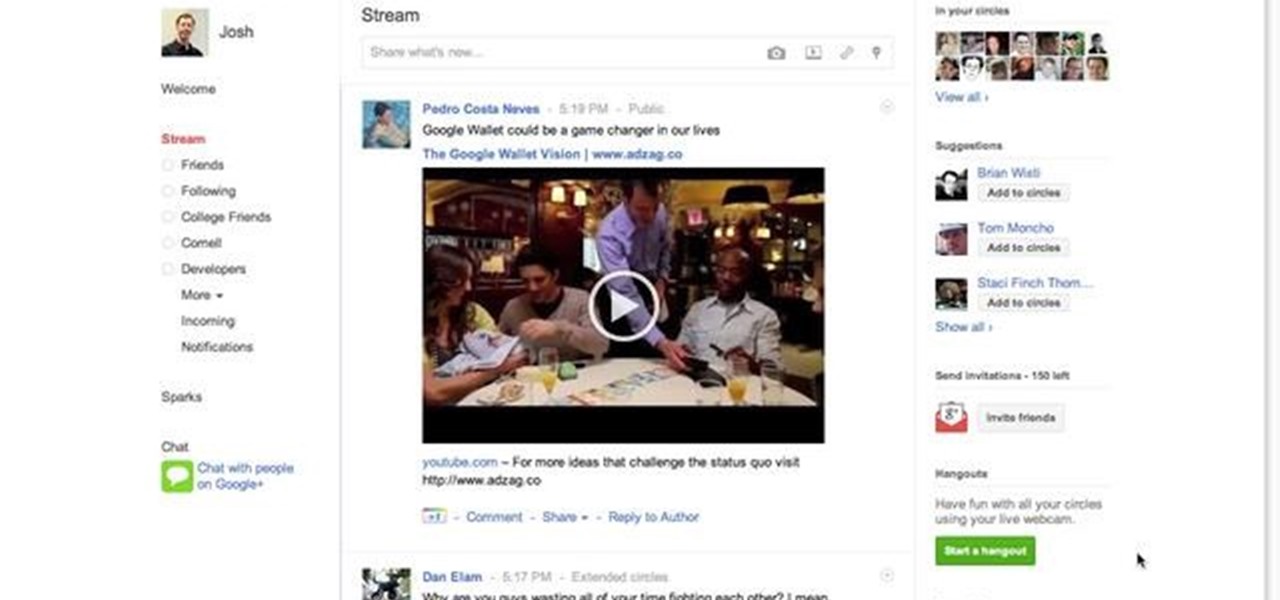
The Hangouts feature of Google+ allows you to interact with and talk to different Google+ users and circles via your webcam. Hangouts is a great way to have a video conference with several different individuals and is similar to the Group Call feature of Skype.

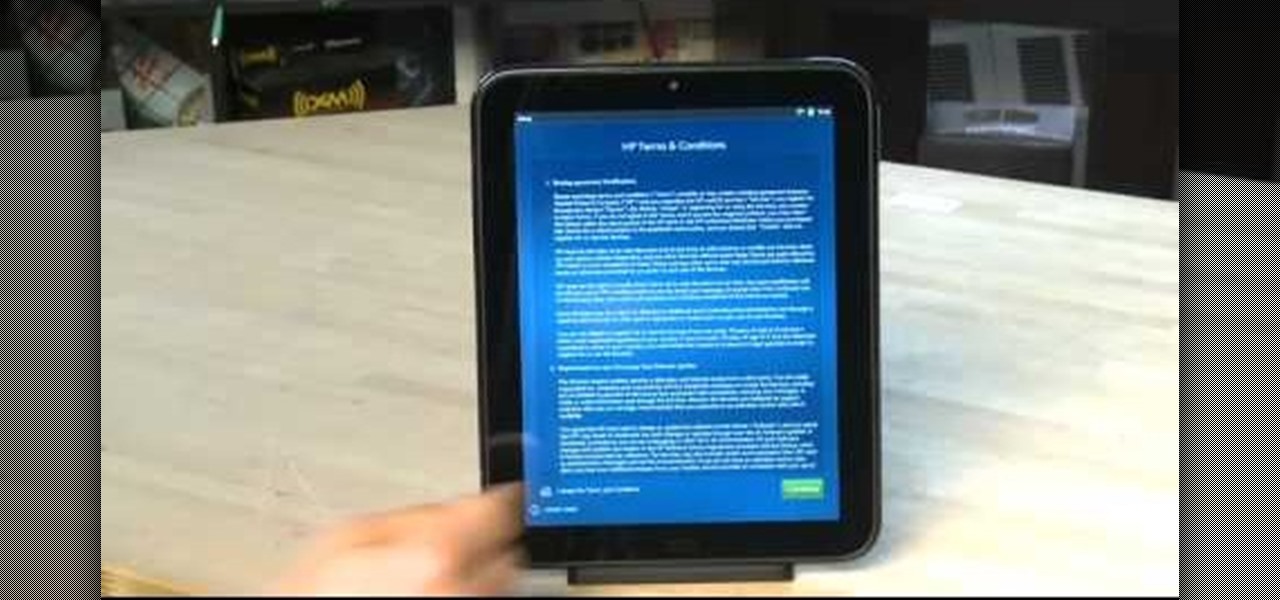
If you were one of the lucky individuals to score a TouchPad before HP discountinued them, you will need to proceed through the initial setup wizard when you turn on the device for the first time, or after performing a data wipe and reset on the tablet. This guide will walk you through everything from accepting the terms & conditions, connecting to a Wi-Fi network, and creating a webOS account for the first time.

Now that you've imported your footage into Windows Live Movie Maker, you're ready to edit it. A good first step is to trim the beginning and end points of the individual clips that will go on to make up your movie. This clip from Vimeo's excellent Video 101 series of video tutorials will teach you how to do precisely that.