This video will show you how to target your audience for Facebook post. You could set country, language, age group, qualification, etc. for watching your post. Watch the video and follow all the steps. Employ the technique in your Facebook account.
Back in iOS 6, deleting individual text messages in a conversation was just a matter of tapping the edit button on the right-hand corner of the thread, selecting which texts to delete, and then pressing delete.

Just because you need to assemble an outfit for work doesn't mean it has to look all boring and aging. As long as you stay mostly covered up and don't pull out your neon-colored cheetah print stockings, you'll do just fine accessorizing and dressing fashionably.

In this video tutorial, viewers learn how to properly shoot and sight in a compound bow. It is recommended that users use a release. Your body should be perpendicular to the target. Hold the bow vertically, and hold it with a relaxed and secure grip. When you are ready to begin shooting, learn a technique that will help you relax and steady the bow. When you draw the bow string back, you should be looking through the peephole on the bow string and where the target and pins come into view. Thi...

In this video, Tom Leese, Director of Instruction at Angel Park Golf Club, gives pointers for your pre-shot routine in golf. Important in the transition from the practice range to real games, your pre-shot routine helps you get situated and ready to play real competitive golf. Tom explains, first, how to set your lines, taking a straight and purposeful line down course where you want your ball to go, and remaining fixed on it, as you approach your tee. Then, when positioned at your ball, he t...

Hip flexors are important muscles to target when weight training to build functional strength in the legs. Learn how to do hip flexor exercises in this strength training video. Take action: knees to chest exercise targets core, hold weight between feet, raise knees as high as you can, start in push up position and bring alternate knees to elbows, and work for quick reps and endurance. Tom Clifford, the instructor in this how-to video, has a degree in physical education, fitness and health fro...

The SOFLAM is a gadget that you can use in Battlefield 3. It is a team based gadget that you deploy and use to laser target. It is different than a mortar and can be a little hard to use. This guide will show you how to get the most out of a SOFLAM so that you can tear up the other team.

This Giant Bomb walkthrough will take you through the Iron Golem boss fight in Dark Souls. The Iron Golem is the last boss in Sen's Fortress and has a long reach. You will need to target the back of its legs in order to defeat it.

Bennett Froddy brought us the Flash game sensation QWOP, and now has released a free sequel called GIRP. You control you character's individual limbs with the keyboard as before, but this time you're controlling a rock climber and using keys to grab particular handholds. It's tricky at first, but this video will show you how to beat the first 25 meters. Damn that bird!

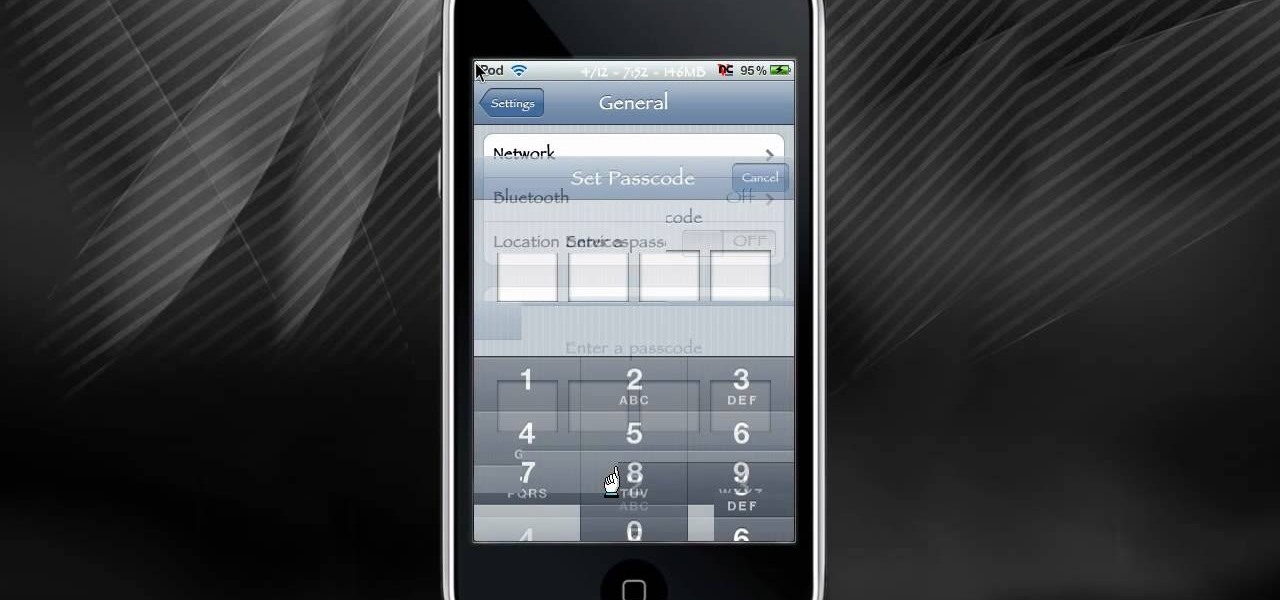
Back in the olden days, if a lock was, well, locked, you couldn't get in the door. At least, the average individual couldn't get in the door. But inventive and scheming folk (read: ye hackers of olde) devised crafty ways to pick lock keys and sometimes even created skeleton keys that opened any door or chest. This will let you unlock someones password on an ipod or iphone touch.

When you have to use 18 individual pieces to create an origami project, you know it's going to be hard. Thankfully, with this video you'll be guided through exactly how to maneuver every crease and fold.

Enhance your visual skills and demonstrate your manual dexterity as a magician by incorporating the "RockIt" card fluorish by Ayres into your repertoire. Playing card fluorishes are typically performed as part of larger magic performances and can also be shown on their own as individual exhibitions of skill.

Pretty Little Liars is the newest part of the increasingly puzzling lineup of shows on ABC Family that seem to be creating a new demographic to target as they go along. The girls on it are very pretty, and this video will show you how to create a makeup look inspired by the show's star Alison DiLaurentis.

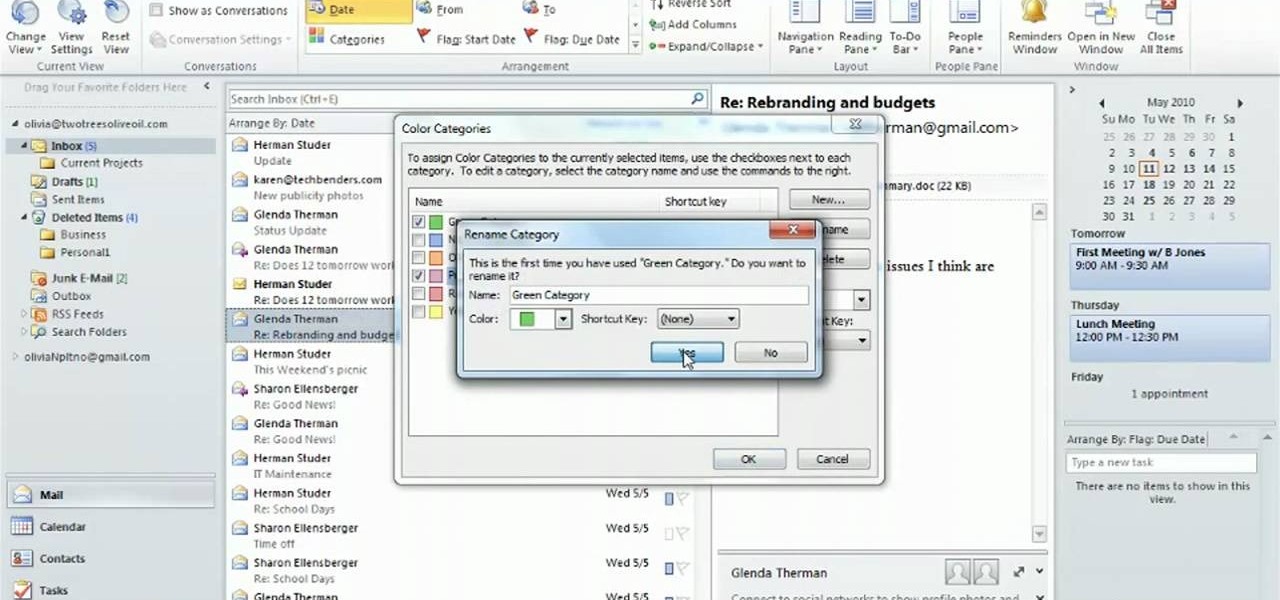
See how to organize your email by creating categories and flagging individual messages within Microsoft Office Outlook 2010. Whether you're new to Microsoft's popular email and scheduling application or a seasoned MS Office professional just looking to better acquaint yourself with the Outlook 2010 workflow, you're sure to be well served by this video tutorial. For more information, and to get started organizing your own inbox, watch this free video guide.

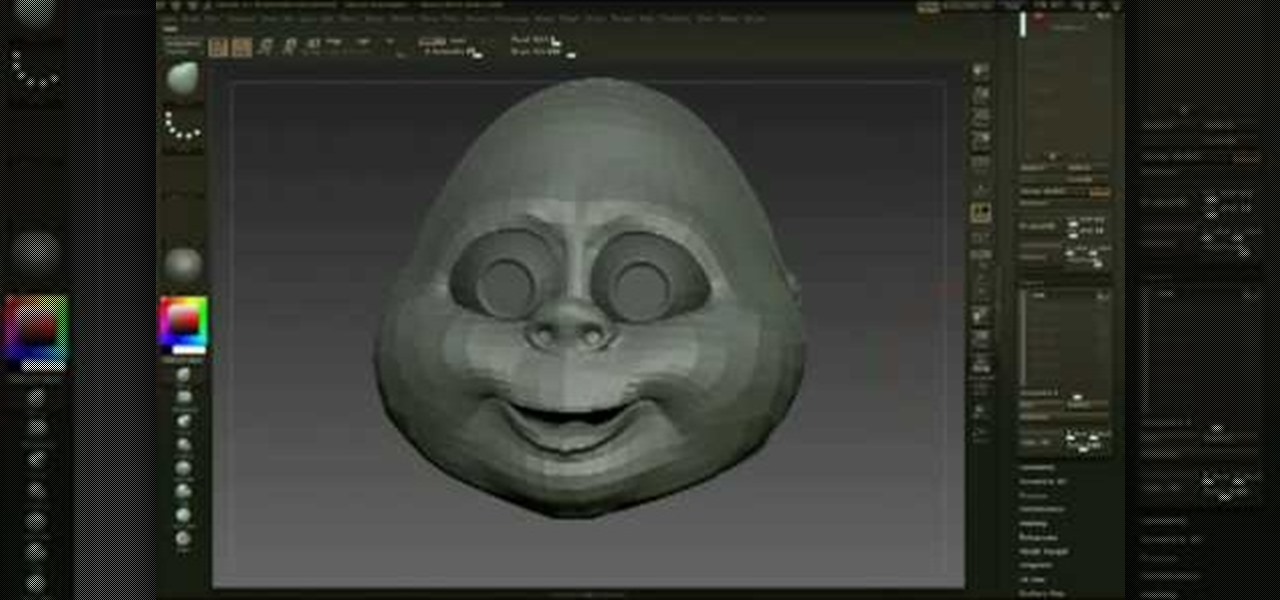
THis video from accredited 3D art instructor Andrew Klein covers how to create symmetrical and asymmetrical blendshapes using the 3D sculpting program Zbrush. This is a fairly complex process, utilizing transpose masking features, move brush, smart resym, and morph target tools to accomplish its goal of creating a really cool animated 3D mask.

Even with all the technological advancements, iPhones and Blackberries look sleek but lack individual style, their backs a basic black or silver. Turn a blah cell phone cover into a fairytale work of art by watching this video.

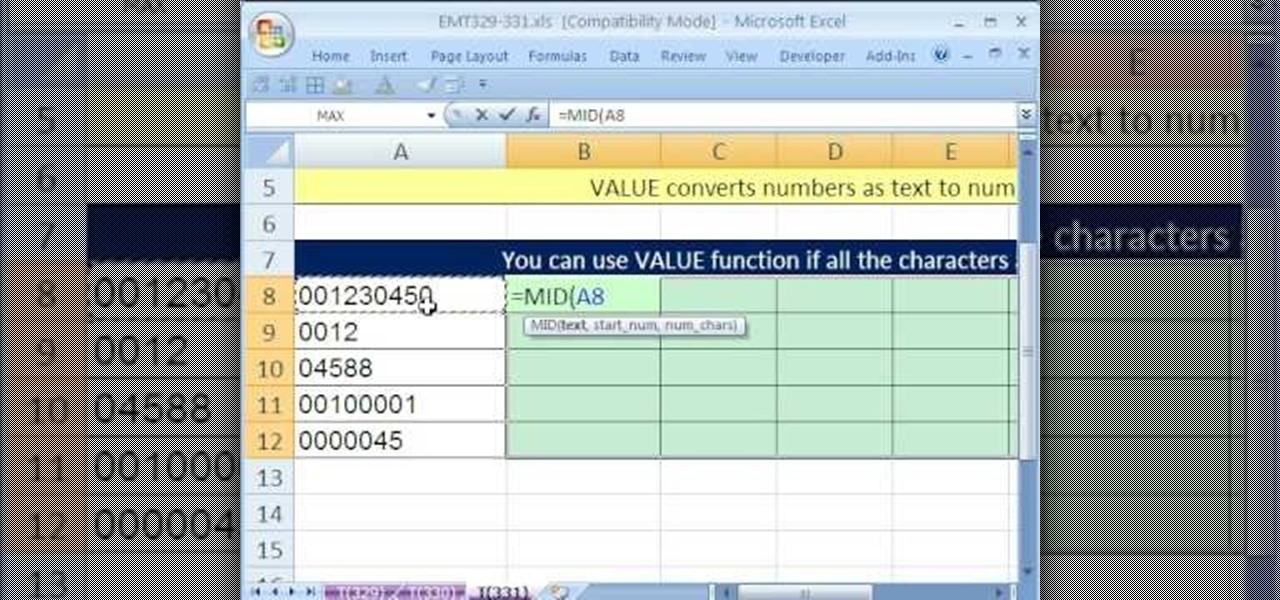
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 331st installment in their series of digital spreadsheet magic tricks, you'll learn how to extract individual characters without extracting the leading zeroes through use of the MID, VALUE and COLUMNS functions.

Here is a series of hot and complex sexy salsa dance patterns. This is a more complicated salsa pattern. It is a very long pattern, so take it in strides and small bites. We have named the individual moves to help you piece the entire salsa combination together.

How to use a can opener with one hand or without a prosthesis. This is an adaptive equipment tutorial for handicapped, disabled or individuals that have lost limbs to amputation. This trick is important to ensure healthy living and daily tasks like opening food in the kitchen. Live without limits!

A below elbow arm amputee demonstrates how to tie a shoe with his prosthetic hook. This is an adaptive equipment tutorial for handicapped, disabled or individuals that have lost limbs to amputation. The prosthetic arm outfitted with a hook or hand can be body powered or myoelectric. The operation is important to ensure healthy living and daily tasks like dressing yourself.

A below elbow arm amputee demonstrates how to turn a car key with his body powered prosthetic hook. This adapted equipment video is helpful for handicapped, disabled or individuals whom have lost limbs due to amputation. He's using a prosthetic arm outfitted with a hook to start the ignition of his car.

A below elbow arm amputee demonstrates how to hold and use a knife with his prosthetic hook. This is an adaptive living video that helps handicapped, disabled or individuals that have lost a limb due to amputation. Using a prosthetic hand or hook can be challenging in the kitchen. Using a hook to hold and use a knife is an important skill to learn when using prosthetic limb adaptive equipment.

In this Photoshop CS3 tutorial you will learn how to use the knockout feature. This advanced masking technique allows you to move a targeted layer around, revealing the layer underneath. This video will show you how to reveal a creepy skeleton under a monster werewolf right in Photoshop. This classic technique lives again! Learn the subtle qualities of the Deep, and Shallow, Knockout feature in Photoshop.

This audio editing software tutorial will show you two different types of editing in Logic Pro. First, Connor Smith shows how to edit multitrack drums in a group (to fix timing of hits) in Logic Pro. Then he covers how to ungroup your drums and take out pops, clicks (etc.) on individual drum tracks in Logic Pro.

This science video tutorial includes step-by-step instructions for extracting DNA from wheat germ, the embryonic plant attached to the wheat seed. Individual wheat seeds, or kernels, separate readily from the plant. This kernels have a tough outer coating called bran. If you want to know more, just watch this science experiment.

You can give your song texture by adjusting individual tracks to become louder and softer to emphasize particular moments. With GarageBand, this process is easy and yields professional-sounding results.

You already know you can create photo pages by selecting a photos template and dragging in individual photos from your iPhoto library. Now there's an easy way to add entire photo albums to your site, each with their own dedicated photo pages.

Katherine and Kimberly Corp show you how to do a ten-minute (1o min) pilates arm workout using stretch bands. This workout targets every major muscle group in the arms and helps maintain alignment and ab strength.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Just like in the Spy Kids 3D movie, US soldiers may soon upgrade their mission planning from 2D to 3D. Welcome to the wonderful world of augmented reality, US Army.

Jostled in the airport, someone is coughing in line. The air looks empty but it is loaded with microbes that make their way into your body. You get sick. You give it to your family, and that's pretty much it. But what if you were so contagious that you spread it to your entire community and beyond?

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

It's no secret that Google stores your search history in order to provide you with targeted ads when surfing the web. What's even more interesting (or freaky) is that your Google Now voice searches are also being stored, and you can actually listen to them right now.

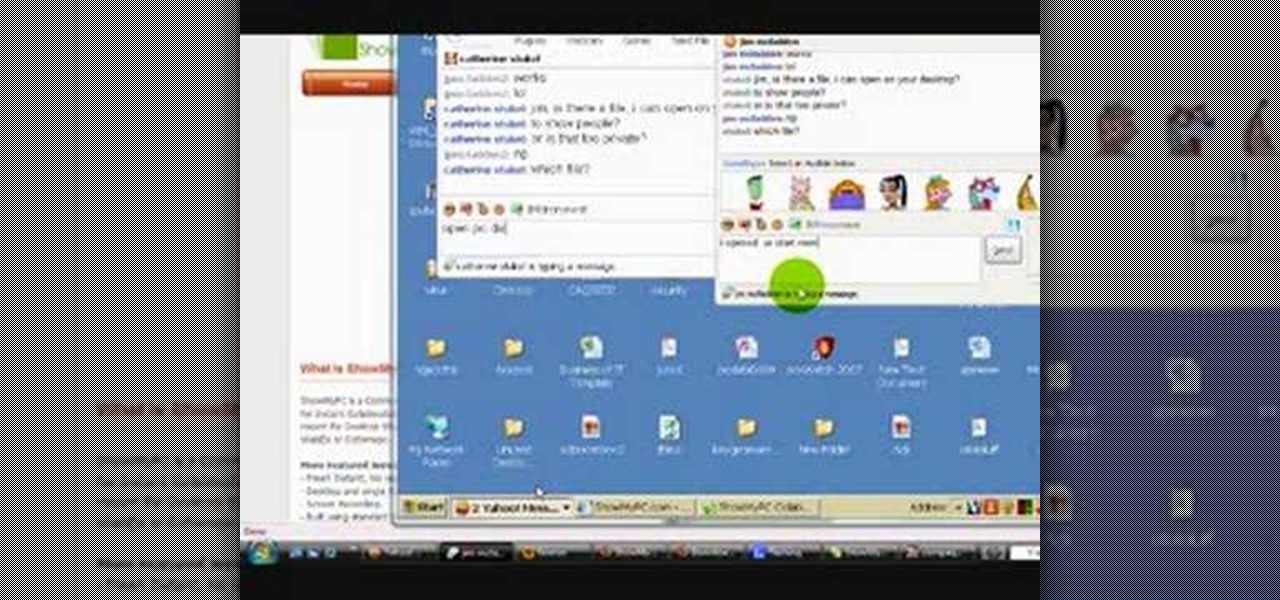
Want to be able to hack into a computer remotely? This method takes a little extra time and cunning to set up, since you will need to first install the ShowMyPc program on your target computer. Once you have installed this program, however, you will be able to go to the website ShowMyPc.com and be able to see what your target has been up to. Even better, you can use that computer and the files on it as if it were your own desktop!

What's in a name? Quite a lot. Learn how to choose a good one that targets your desired demographic. Whether you're considering the possibility of starting your own Pilates studio or already have one and just need a little help tackling a particular pedagogical problem, you're sure to be well served by this free video lesson from the folks at Balanced Body Pilates. For more information, including a comprehensive overview, watch this video guide.