Swipe keyboards such as GBoard, SwiftKey, TouchPal, and Swype are handy for quick one-thumbed typing on an iPhone, but Microsoft upped the game with its experimental Word Flow Keyboard. In short, the keyboard fans out to occupy the natural range of your thumb, where you can type or rely on predictive swiping.
If you get a ton of emails each day, your mailbox probably has thousands of unread messages, and that annoying badge icon will keep reminding you of it. Fortunately, iOS comes with some tools to help you bring some sense of order to that chaotic mailbox of yours.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Logan's Run is one of my favorite movies of all time. The dialog is cheesy, the set design and special effects are wonky, and the main villain looks like he was conceived and built by an eighth grader in shop class—oh, and his name is Box.

Since its purchase by Microsoft in 2014, Minecraft has regularly been pushed to new platforms such as Windows 10, Wii U, and Fire TV. In that spirit, Microsoft-owned Mojang has been developing virtual- and augmented-reality versions of the blocky sandbox game.
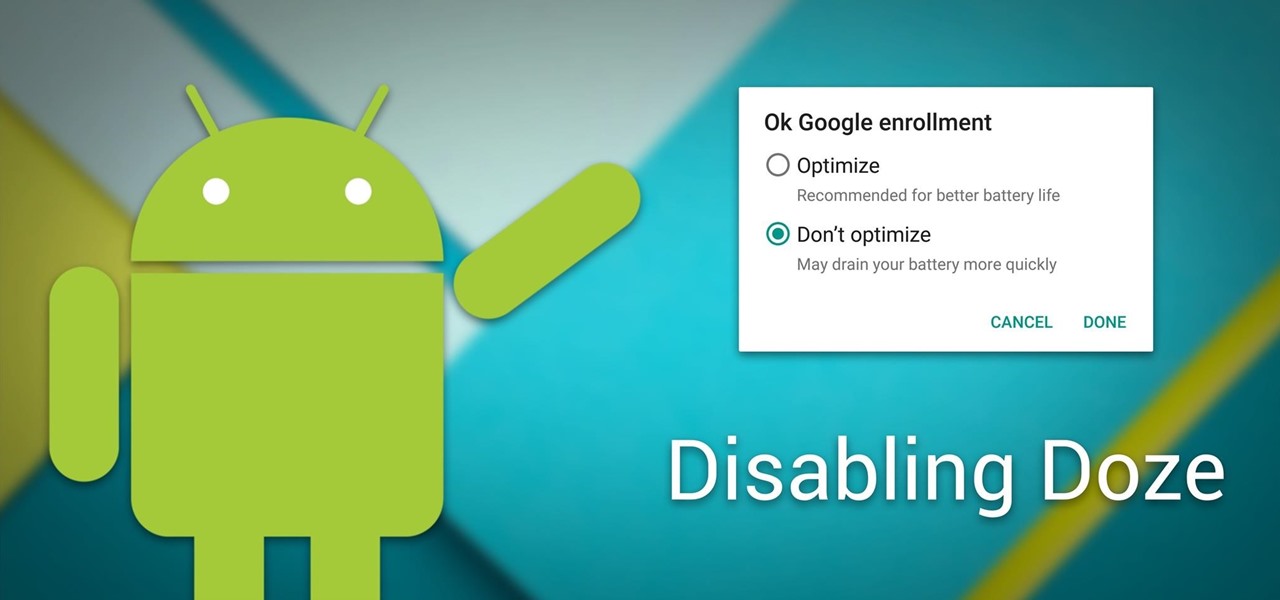
Android Marshmallow introduced a pair of new battery-saving features called Doze and App Standby, and according to the general consensus, both features are a rousing success. Average battery life has increased dramatically for virtually every phone or tablet running Android 6.0, so there's nothing to complain about here, right?
If your company has already released some popular and addictive game and you're thinking about creation a sequel, this article is just what you need. We gathered the main tips and advices that will be useful for the building a strategy and a sequel itself. Check out the following instructions and recommendations that can lend you a hand in making a sequel for your game.

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

All across the web, you'll find guides on setting up various apps and mods for your Android device—but while these are certainly useful, they all seem to be working under the assumption that the reader has a certain level of knowledge about Android. For someone that's just getting started with the world's most popular mobile operating system, the basics of Android simply aren't covered as well as they should be.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

Microsoft decided to give users a free upgrade to Windows 10 if they were previously running Windows 7 or 8—but it came with a catch. Their main motivation for knocking off over $100 from the normal going rate was to get more people using new Microsoft services like Cortana and the Windows Store. To bolster these services, Microsoft implemented a host of new tracking "features" in Windows 10.

If you have a specific app you want to lock so that others can't access it, the most secure way of doing so is with biometrics. While there are options to lock apps with either a PIN or pattern, these can easily be figured out with a simple glance over your shoulder. It's much more difficult for someone to crack your fingerprint ID, unless they chop off your finger, of course.

Cauliflower has become trendy again, and it's mostly thanks to the low-carb crowd who use its mild flavor and soft texture as a replacement for things like rice and pizza dough.

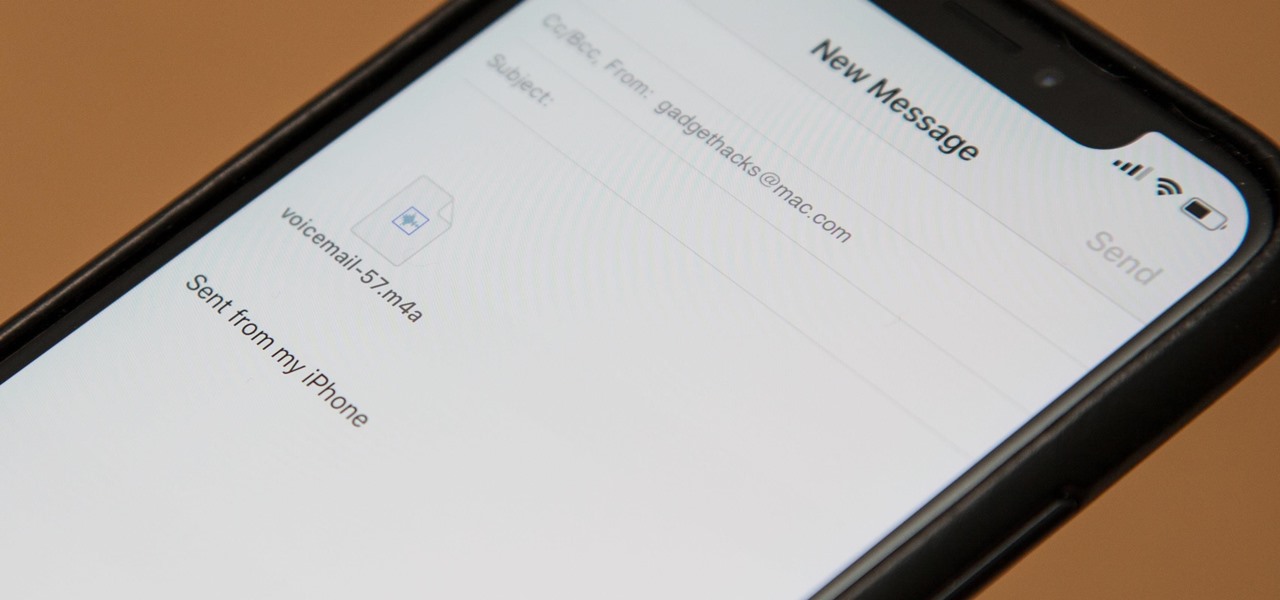
Eventually, your voicemail inbox on your iPhone will get full, and you'll have to delete some messages in order to make way for new ones. If all the voicemails you currently have are super important, you're not going to want to delete them before saving them first, of course. Luckily, this is a super simple task, and you can even forward them to someone else if needed.

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.

Who doesn't experience food cravings? Whether you're trying to adhere to a strict diet, or simply hoping to avoid sugary, fatty foods, curbing cravings can feel like a monumental task.

Do you ever walk into a nice boutique, a friend's house, or a fancy restaurant, and think, “I wish my house smelled like this”? Because I sure do.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

Cortana, Microsoft's personal assistant for its Windows Phones and Windows 10, will soon be released for Android. That is, officially released. It's hard to keep a good thing locked away, and to that end, Cortana for Android has been leaked, thanks to APK Mirror.

When you go to the grocery store, chances are you're confronted with the usual piles of apples, berries, bananas, and melons. All well and good, right?

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Saying that I was obsessed with Pokémon as a child would be a serious understatement, and even though I'm not the Pokémon fanatic I once was doesn't mean I don't love playing still. However, I do often find myself dumbfounded by all of the new features and characters in each generation.

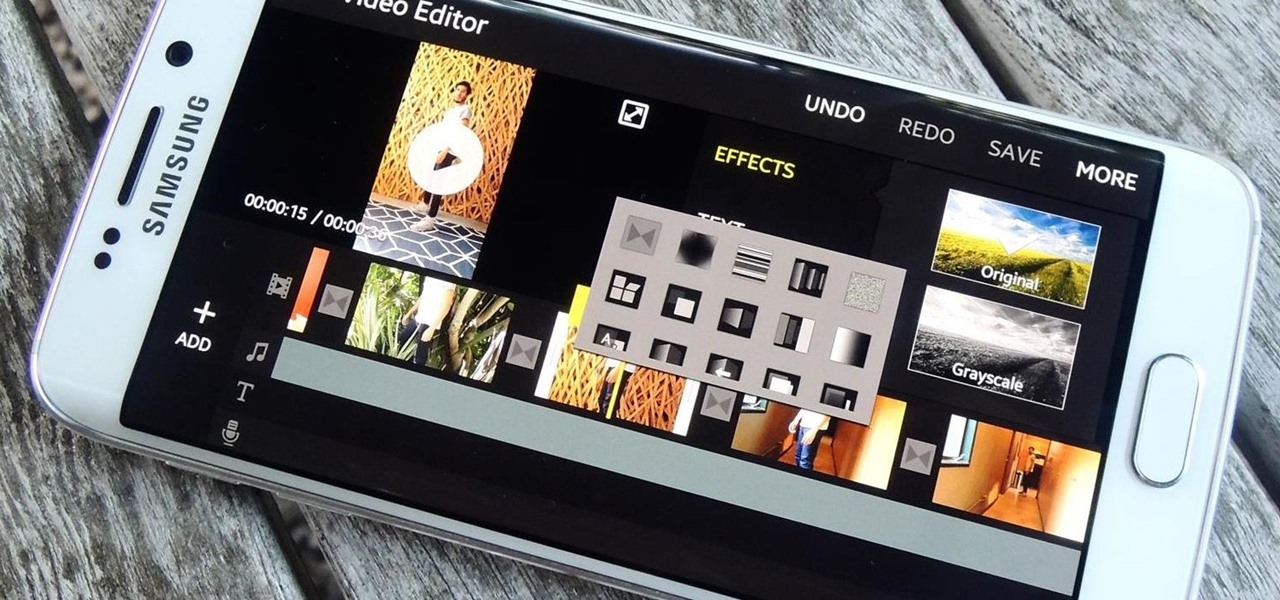
Editing a video by trimming or adding audio is fairly simple on Galaxy devices, but if you want to include other clips or transition animations and really get those creative juices flowing, you might find the standard editing tools limited—unless you know how to unlock Samsung's hidden video editor.

It sounds like a dream come true: just press a button on your phone, and 30 seconds later, a machine produces a custom-made, ready-to-eat meal. Finally, science comes through for the truly lazy!

With audible alerts and subtle vibrations, the Apple Watch makes it difficult to miss incoming notifications. But soon enough you'll realize that not every notification is worth receiving on your Watch and can ultimately render the experience annoying under particular circumstances—like when your popular Instagram post floods in notification after notification.

They might be a little late to the party, but the Cyanogen team has finally released their newest ROM for the OnePlus One, Cyanogen OS 12. The launch had to be pushed back a few times due to some technical issues, but now we finally get to see what the Cyanogen team has cooked up for Android Lollipop.

With platforms like Facebook, Instagram, and Snapchat available for anyone to take advantage of, I'm all about differentiating from the mundane and repetitive images we see on social media everyday.

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

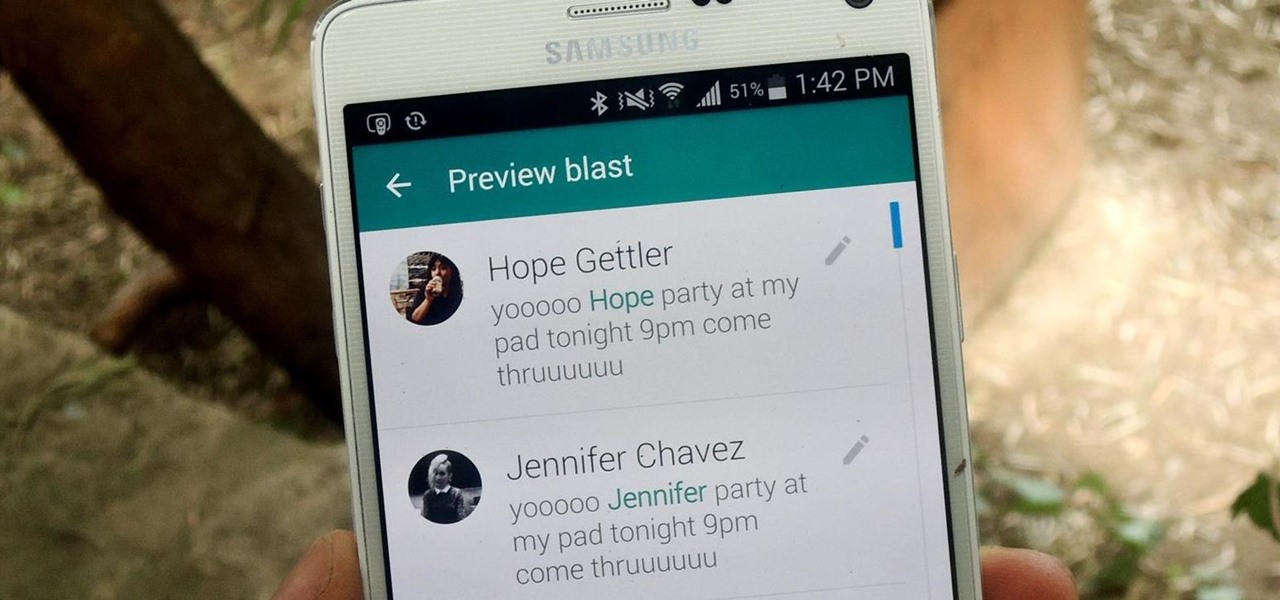
We've all received those impersonal mass text messages, whether we're getting invited out to a birthday party, graduation celebration, or just a group dinner or outing.

Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps that could accomplish roughly the same thing.

It's been over a year now since Google introduced a visual way to track down which tabs are playing audio in Chrome, something that was previously only available using third-party extensions. However, they still didn't give an easy option for shutting those tabs up without having to stop what you're doing.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

From my experience, the recent contacts in the iOS 8 app switcher is a love-hate feature. On the plus side, it's a speed dial for not only phone calls, but messages. On the downside, it's a way for others to see your favorite contacts and who you've contacted most recently.

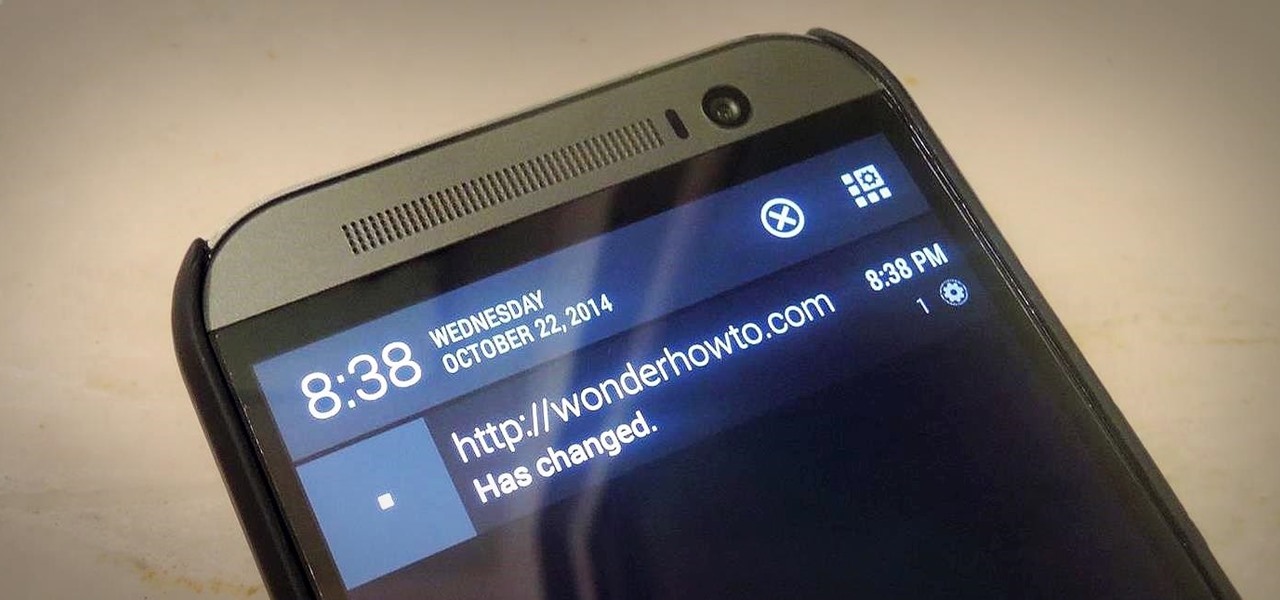
The problem with striving to be on the bleeding edge of what's new for your smartphone, or really anything else in life, is having to constantly check websites and forums for new content. And with lots of that browsing happening on our phones, the aimless page loading and refreshing is not just annoying when there isn't new content, but can lead to wasted data usage, not to mention time.

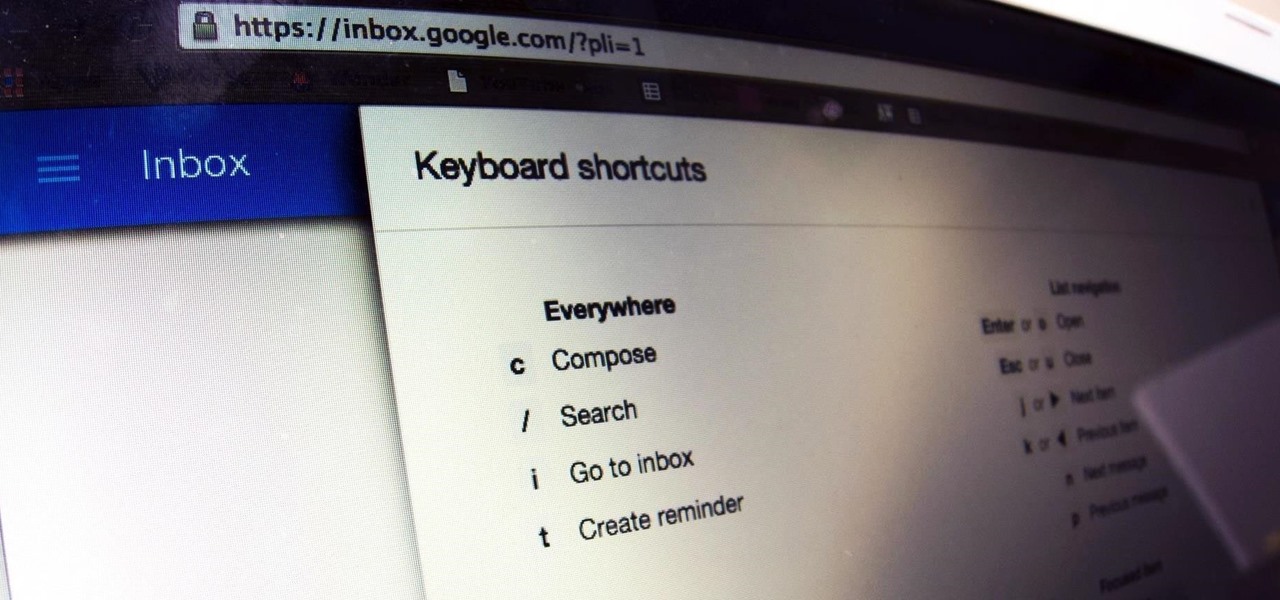
While the new Google Inbox is currently invite-only, if you were able to snag one, you'll want to learn the best ways to navigate it. Google Inbox coins itself as "The inbox that works for you," and after a brief run through of it, we think it's definitely living up to that slogan.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

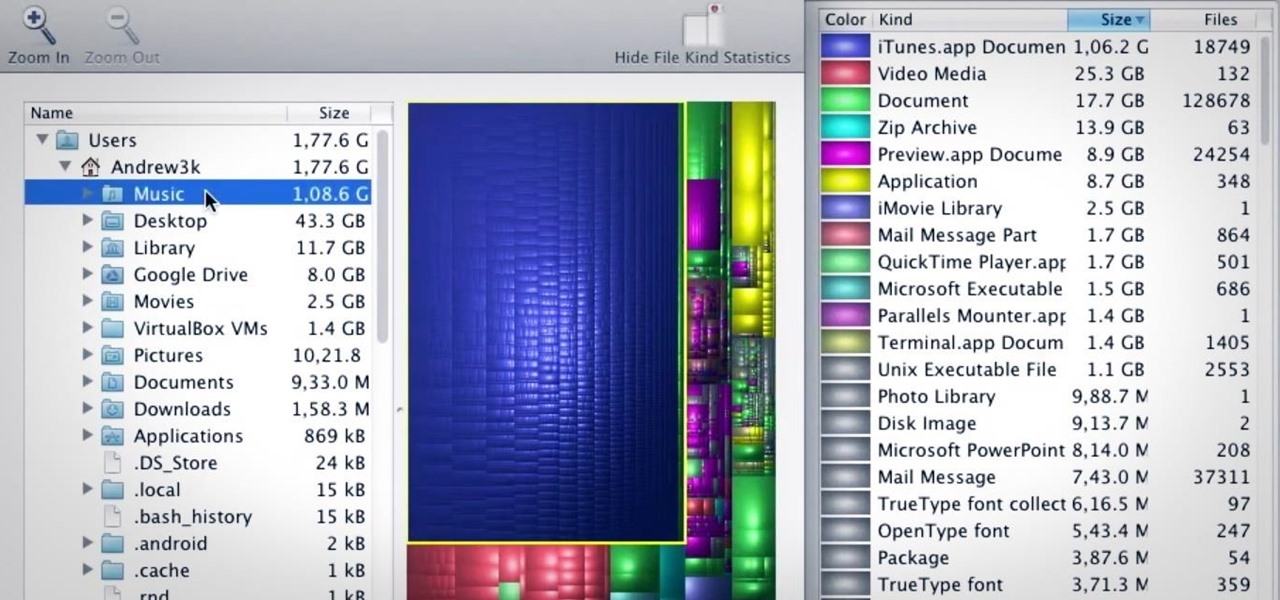
I love my MacBook Air, but the fact that it runs on only 128 GB of flash storage causes me to move most of my files to the cloud. I don't mind having to be connected to the internet in order to access my files, but it's definitely a hassle trying to figure out which files I should move in order to save the most space. Usually, I don't even bother even trying until I see the dreaded "Your startup disk if almost full" warning. Currently, the only real way to find your biggest files in Mac OS X ...