Google and eight top Android partners have just signed the Android Networked Cross-License, nicknamed PAX. On the surface, this looks to be a peace treaty of sorts that could end several patent wars.

We usually associate Salmonella bacteria with a dangerous type of food poisoning, but they actually are pretty good at seeking out tumors. That trait made the bacteria a great candidate to deliver a protein that would help knock tumors out.

Nintendo's first ever game for Android has finally touched down (unless you actually count the abomination that is Miitomo). Fire Emblem Heroes, a classic turn-based RPG optimized for mobile gaming, has come out for Android and iOS in Australia, Europe, and Japan, and is due out in North America and other worldwide locales very soon. Due to Nintendo's staggered release, the game isn't available to us in the United States at the time of this writing, but fret not—there's another way to downloa...

The YouTube app for Android doesn't exactly offer the greatest user experience. For one thing, it opens to an arbitrary "Home" tab instead of your subscriptions, so you see a list of what YouTube thinks you want to watch instead of your favorite channels. In addition to that, videos are loading at a mere 144p playback resolution for many users lately, which is downright terrible quality.

In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.

Since the 1960s, bacteria have been hopping a ride into space on space vehicles and astronauts, and have been cultivated within experiments on space shuttles and the International Space Station (ISS). The extreme growing conditions and the low gravity environment on the Earth-orbiting vehicles offers a stable research platform for looking at bacteria in a different light.

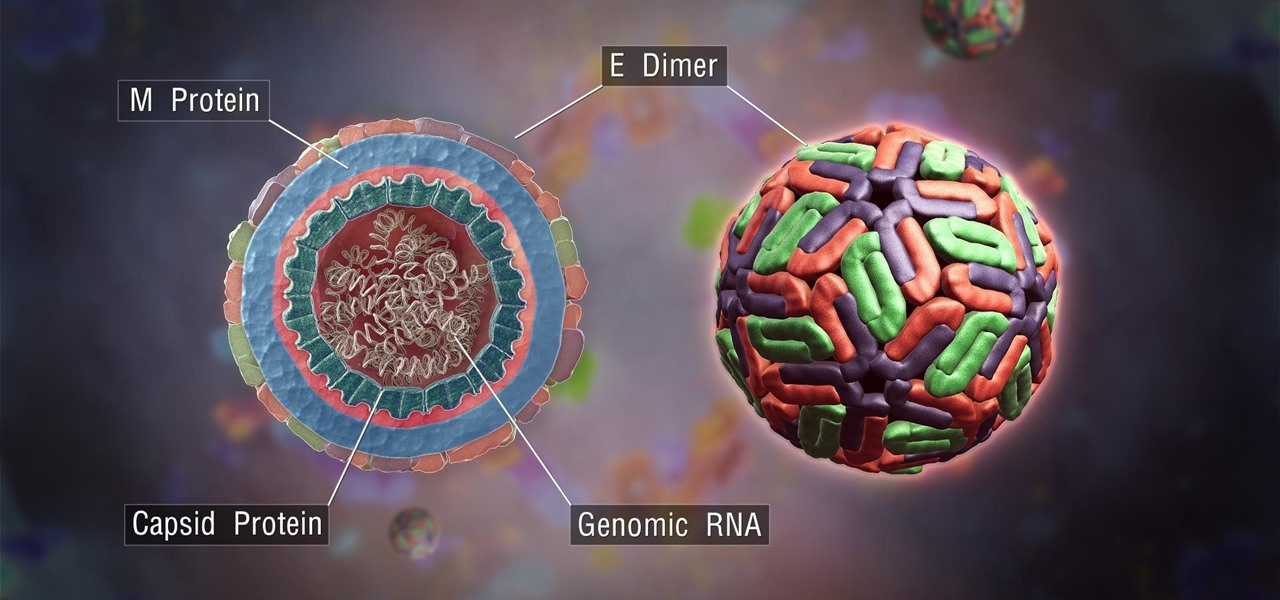
The mention of Zika can strike fear in the hearts of pregnant women. With infections increasing around the world, including in the US, researchers are fighting the clock to figure out how the virus can have such horrific effects in some people.

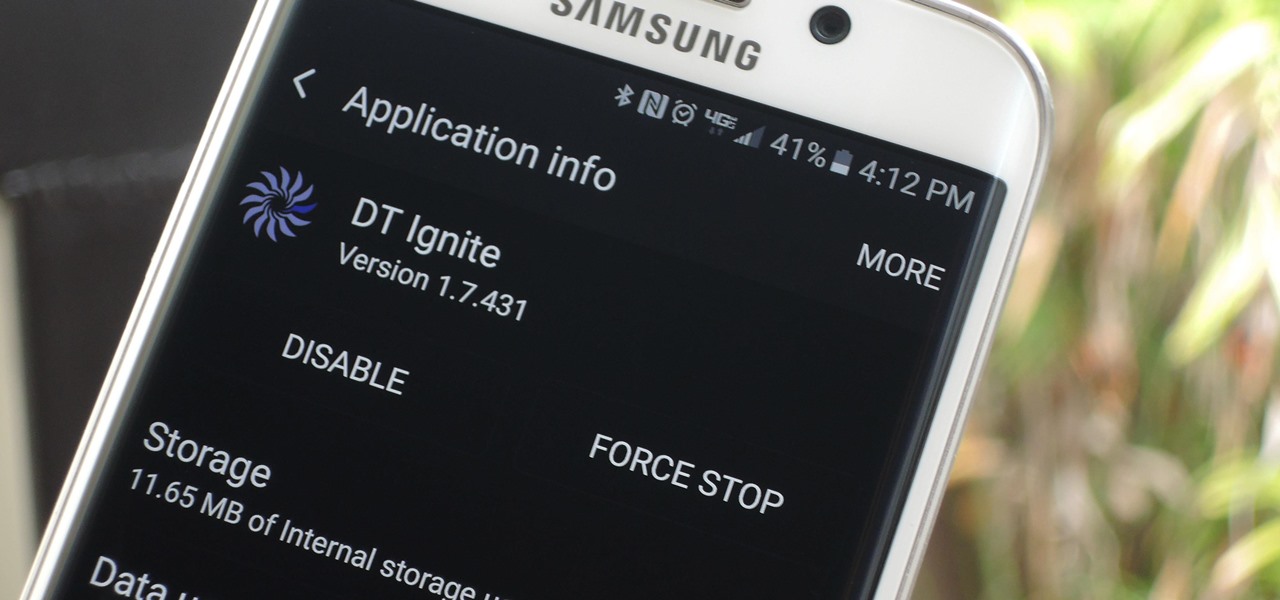
A few months ago, it was discovered that Verizon was installing an extremely shady app called "DT Ignite" on some of its smartphones—most notably, the Galaxy S7 and S7 Edge. The app, created by Digital Turbine, monitors your smartphone usage, then uses the data it collects to silently install "recommended" apps without notifying you.

With the release of the HoloLens, Microsoft has put itself in both a great position while giving the competition a serious target to aim for. This is normally the case for anyone that is first to the market with a new idea, and now we've finally got a good competitor HoloLens coming. Stereolabs, a company known for its impressive 2K stereo camera, will be entering the mixed reality head-mounted display space with a Developers Kit as soon as early-2017.

If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government.

Virtual, mixed, and augmented reality all provide different but compellingly immersive experiences that draw us in through sight and sound. But what about our other senses? A few strange inventions are already exploring the possibilities.

Augmented reality began on smartphones but technical limitations have prevented further development. Google's Tango (formerly Project Tango) aimed to change all that, and with Lenovo's help, they now have their first device.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

Amazon has completely changed the way we purchase household items, to the point where many of us haven't visited a big box, brick-and-mortar store like Walmart or Best Buy in years. And when you think about it, all of this success comes down to two main factors—convenience and price.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

Over the course of the past century or so, media consumption has gone from a few readers enjoying their local print publication to billions of users viewing countless hours of video across the globe each day. This was a gradual evolution at first, but recent advancements in mobile connectivity have sent us into a climb the likes of which we have never seen before.

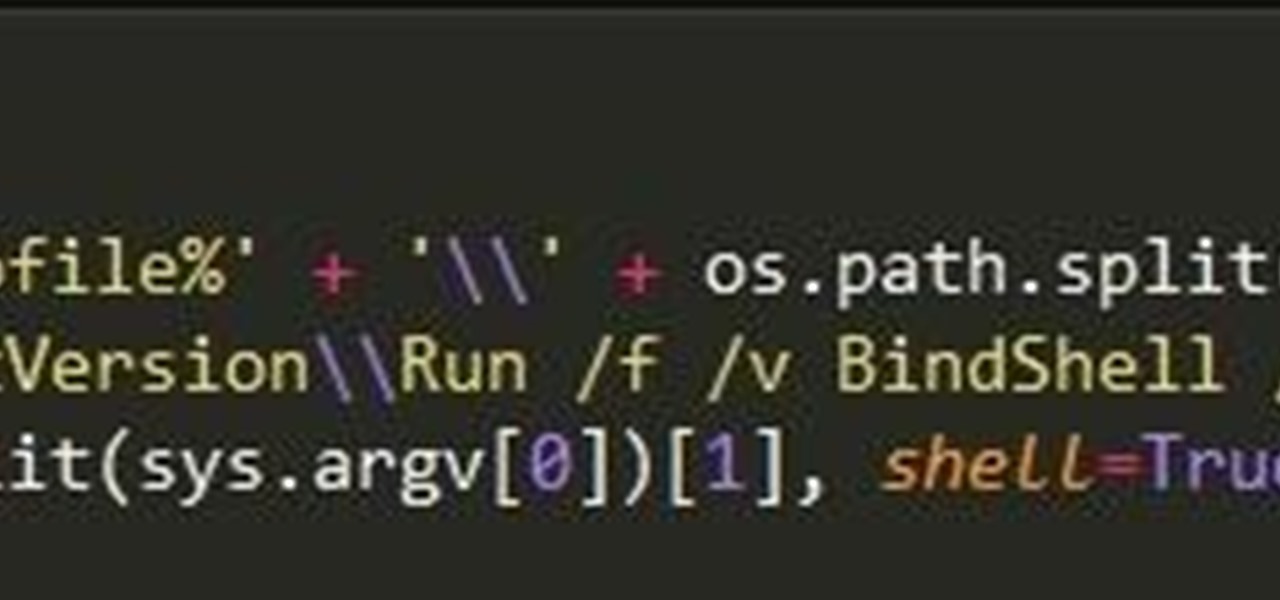
Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

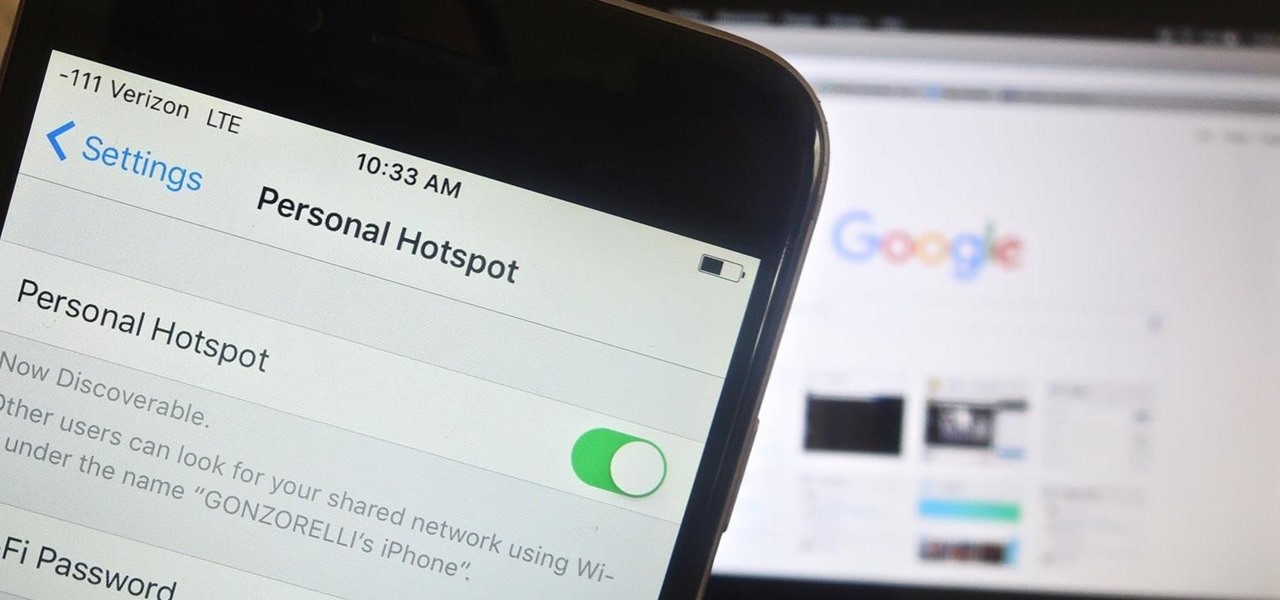
When you're in a bind and need an internet connection for your laptop, look no further than your iPhone. Using the Personal Hotspot feature in iOS, you can share your iPhone's internet connection with other devices by way of Wi-Fi, Bluetooth, or even USB.

Greetings null-bytians. Firstly, I would like to apologize for the no images thing. I guess I can't upload them.

There are going to be tons of great Black Friday deals on electronics in stores like Best Buy, Target, Walmart, etc. But if you can't endure another holiday of standing in lines and running over people to get what you want, shopping on Amazon from the comfort of your own home is the way to go.

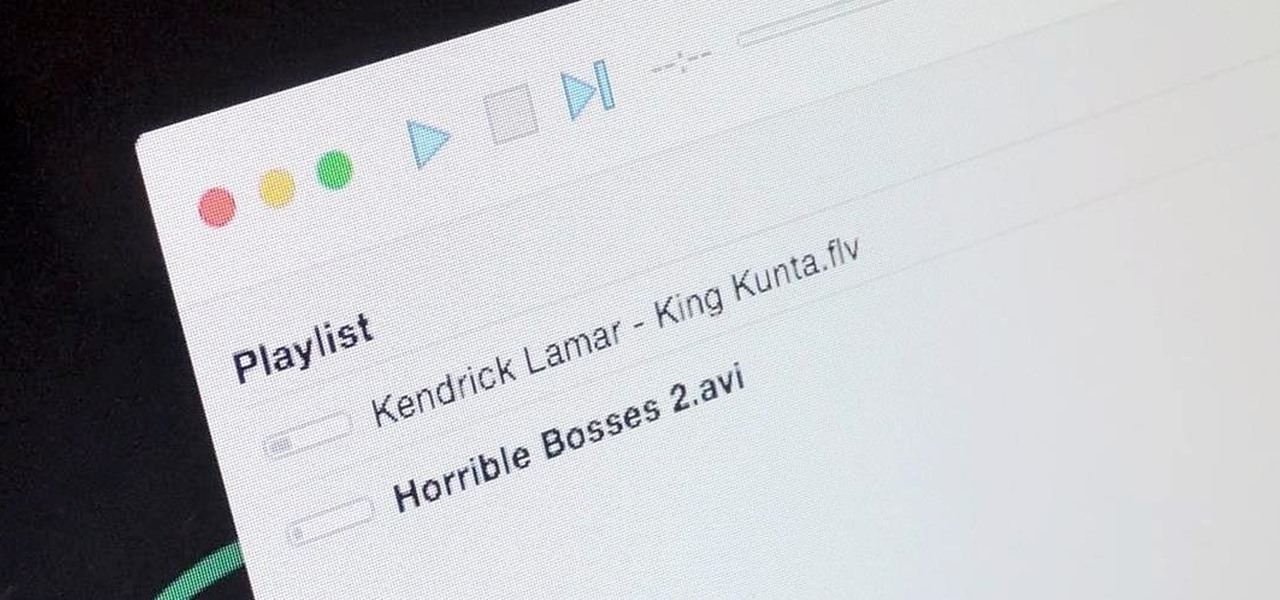
It's a breeze to send videos and music from your phone straight to your TV with an Apple TV or Chromecast, but these devices don't support all file types. While MP4 videos and MP3 music files are the norm these days, I still have a ton of AVI and FLV files that I'd like to watch on a big screen.

Slowly but surely, Microsoft seems to be steering Windows in the direction of Google's Android. First, they released Windows 10 as a free upgrade, mainly because they wanted to cash in on the revenue that they hoped would come when more users had access to the Windows Store. Then, they included tons of tracking "features" to help populate Bing with targeted ads, which has always been Google's primary method for monetizing Android.

Piracy, it can be argued, is the scourge of the internet. But when it comes to music, sometimes it's best to give a listen to a track or album before deciding to spend your hard-earned money on fully supporting it.

In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

Hi guys, I'm gonna keep this short because I got assignments and a lot of notes to study and also other how-tos and forums to reads. lol...Since I'm keeping this short...no story time just scenario. And I want to thank n3stor for giving me the idea to post this.

Everyone's favorite Android modding tool is finally available for the Galaxy S6 and S6 Edge. Thanks to some hard work by Wanam and a few other developers, we can now install the Xposed Framework on Samsung's latest mid-sized flagship phones.

Hello you sexy, savage, surreptitiously tech-savvy penetrators (Pun intended)!

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

Make no bones about it—Google is an advertisement company first and foremost. Nearly everything they do is geared towards targeting the right people with the right ads.

Let's say that we want to see what someone is doing on their computer? In this tutorial, we'll be hijacking cookie sessions to do just that!

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

Starting April 10th, you'll will be able to book 15-minute appointments online to try on an Apple Watch in person at Apple Stores across the world. With the April 24th release date just around the corner, making an appointment is a great idea for those who are unsure about which color and size to purchase—or if they'll even want one.

Beginning with KitKat, I've been used to customizing every aspect of my Android phone, but with the release of Lollipop, there is quite a bit of catching up that developers need to do. Most customization features, like quick settings rearrangement and theme support have already been ported over, but any type of lock screen customization has been noticeably absent.

If you're an Android fan, you probably made your choice in mobile operating systems based on the insane level of customization options that Google's software offers. Don't like your home screen app? Simply replace it. Not a fan of a particular app's sharing system? No big deal, just share through a third-party app.

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.