It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Welcome back, my greenhorn hackers!

This five-part series on C# programming covers many things. First, you learn how to save to the Microsoft SQL Server. Then, you'll learn how to retrieve that data. You'll also learn how to navigate the DataSet, edit SQL data, and delete data. If you have Microsoft Visual Studio and SQL Server, give this lesson a try.

In this video tutorial, viewers learn how to create drop down menus in Microsoft Excel. This task is very easy, fast and easy to do. Begin by highlighting a desired cell. Then click on the Data tab and click on Data Validation under Data Tools. When the Data Validates window opens, click on the Error tab and deselect "Show error alert after invalid data is entered". Then click on OK. Now simply type in the data into the selected cell. This video will benefit those viewers who use Microsoft Ex...
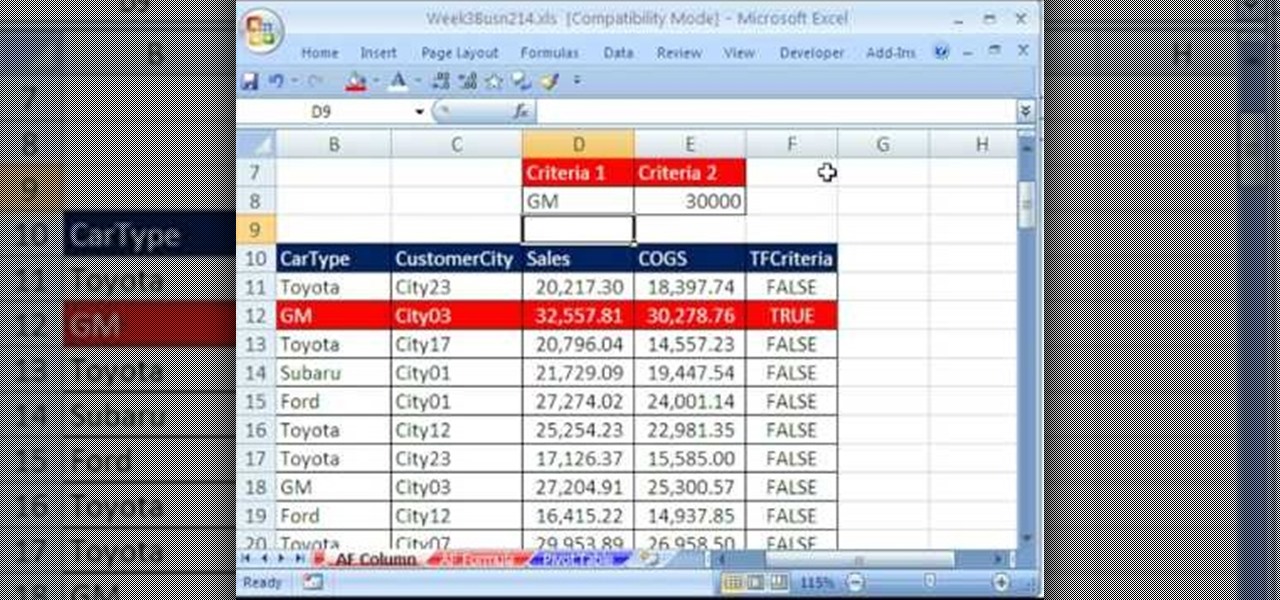
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you're in the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 19th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn about using Advanced Filter to extract data from an Excel List/Table/Database. See these 7 Advanced Filter examples:

Core Data is a powerful data-management framework introduced with Mac OS X v10.4 Tiger. When you take advantage of Core Data, it slashes the amount of custom code you need to write in order to manage application data. Opening, saving and undo management can all be handled by Core Data, freeing you to concentrate on creating unique features for your application. This video tutorial, which presents a general introduction to using Core Data, will walk you through the process of building a simple...

Want to perform an unplugged version of Blink 182's "Easy Target"? See how it's done with this free video guitar lesson, which presents a complete breakdown of the song and its chords. While this tutorial is geared toward those who already have some knowledge of the guitar, players of all skill level should be able to follow along given adequate time and effort. For more information, and to get started playing "Easy Target" on your own acoustic guitar, take a look!

Traveling often is super fun, but sitting through 13 hours on the flight from California to Bangkok is killer on your skin, especially since the airplane recycles air and therefore dries out your skin.

Even Halo: Reach on the Xbox 360 has hidden collectable items! All in the convenient (for the people hiding them) size of a small data pad! Earlier you got access to the first 9 data pads that you can get on any difficulty. Next, you will get a look on the next 9 data pads that you can only acquire while being on Legendary difficulty!

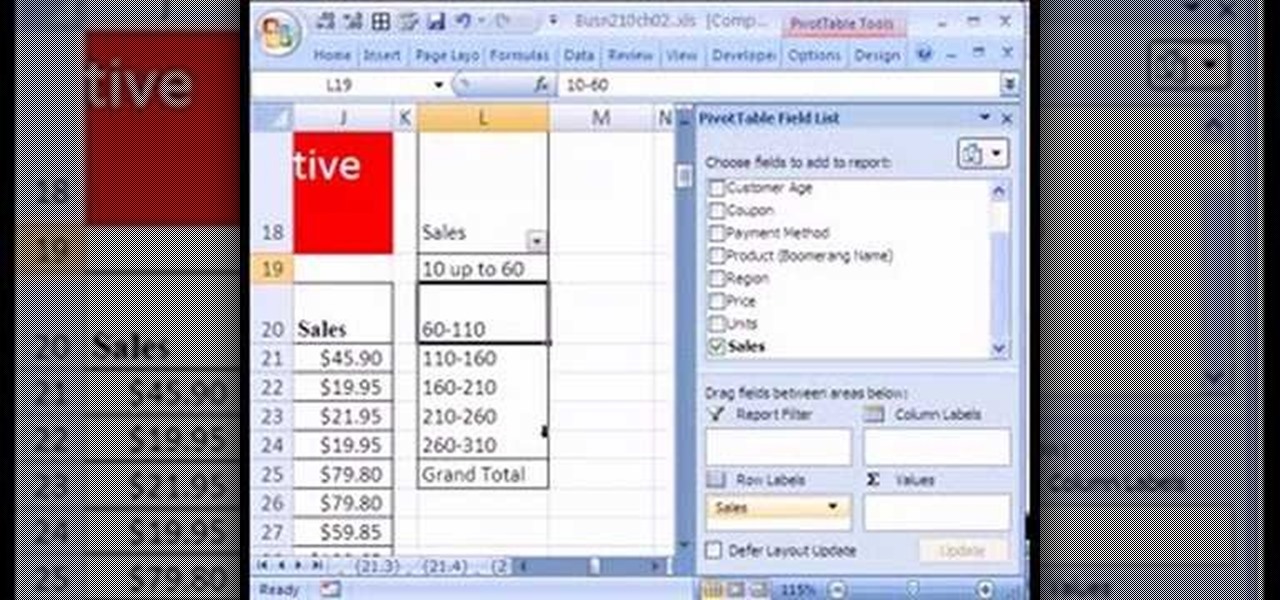
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 32nd installment in his "Excel Statistics" series of free video lessons, you'll learn how to group when the quantitative data are whole numbers, integers or discrete data and how to group when the quantitative ...

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 255th installment in their series of digital spreadsheet magic tricks, you'll learn how to create a two-variable data table in Excel for what-if analysis. See the PMT function and learn about the formula equivalent to a data table.

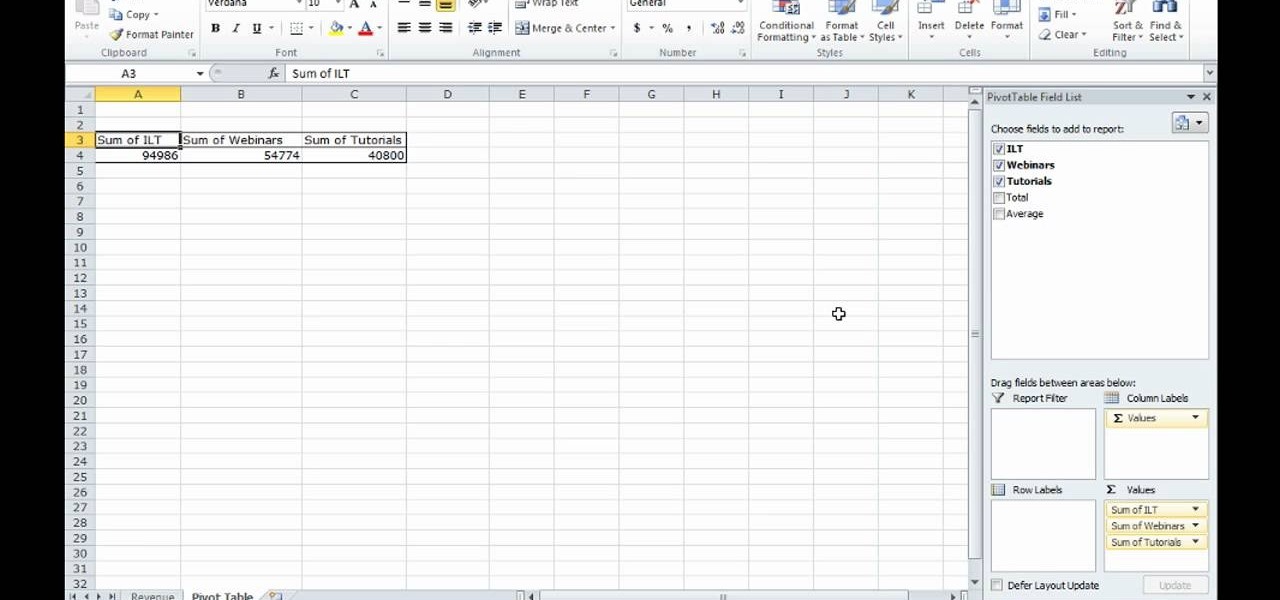
This video shows how to make a quick pivot table data filtering by using Excel 2010's ‘Slicer’ functionality. ‘Slicer’ delivers enhanced visual filtering method to allow you to get the data you need more quickly. When selecting a cell in the pivot table you will find ‘Slicer’ in the filter group of the ‘Insert’ tab. Click on ‘Slicer’ and an 'Insert Slicer' dialogue shows up where you can pick particular data fields from the slider list. Once you click on ‘OK’, the ‘Slicer’ objects with filter...

Data thieves don't have to be programming wizards to get their hands on your personal information. They often find hard drives that contain financial and other sensitive data at flea markets, charity shops, the city dump—even on eBay. In this video tutorial, PC World explains how to completely erase sensitive data from old drives before recycling or discarding them. Wipe your old hard drives with this how-to.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Filmic Pro harnesses the full native power of your iPhone or Android phone — and then some. If your smartphone shoots in 4K resolution, Filmic Pro will let you choose that resolution. However, it's not all about the pixels — bit rate is an essential factor in determining the overall quality of your 720p, 1080p, or 4K video, something Filmic Pro gives you full control over.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

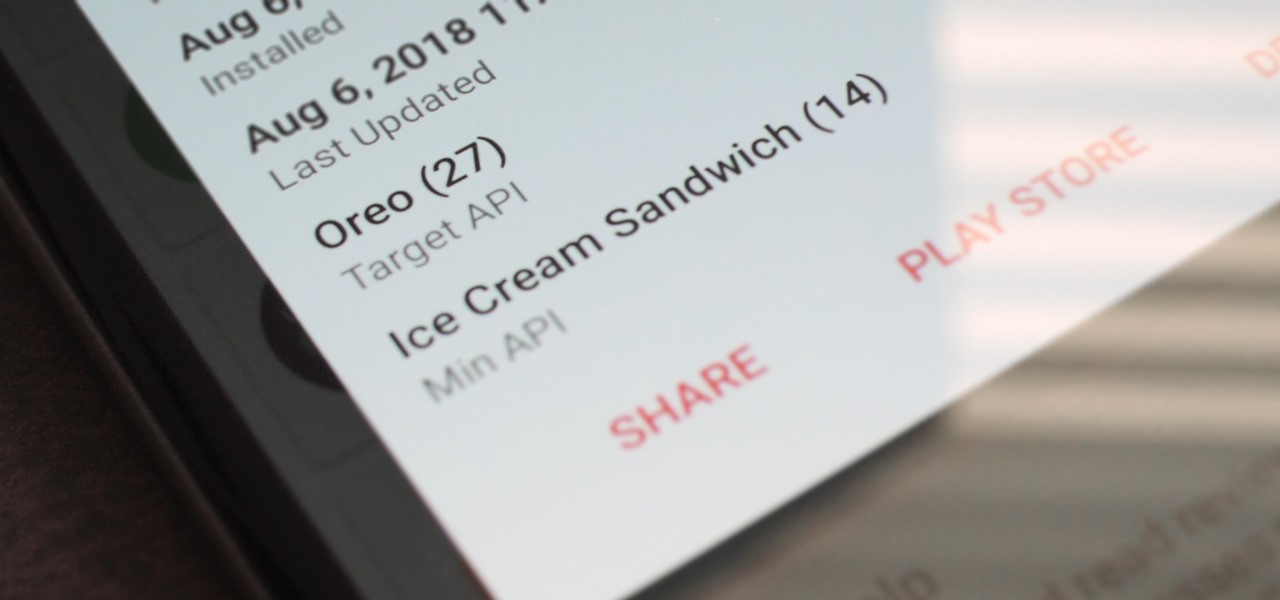
Starting November 1, 2018, Google will require that all new apps and updates to existing apps target Android 8.0 Oreo or higher. This move means the developers behind many of your favorite apps are now scrambling to get their software modernized, while others are considering abandoning outdated apps altogether.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

We're all aware that Google collects a notable portion of our data. Thanks to the increasing awareness, Google has added a number of privacy controls to limit data collection. But Google doesn't just collect personal data for no reason — many of your favorite apps will use this info to improve their services and add new features.

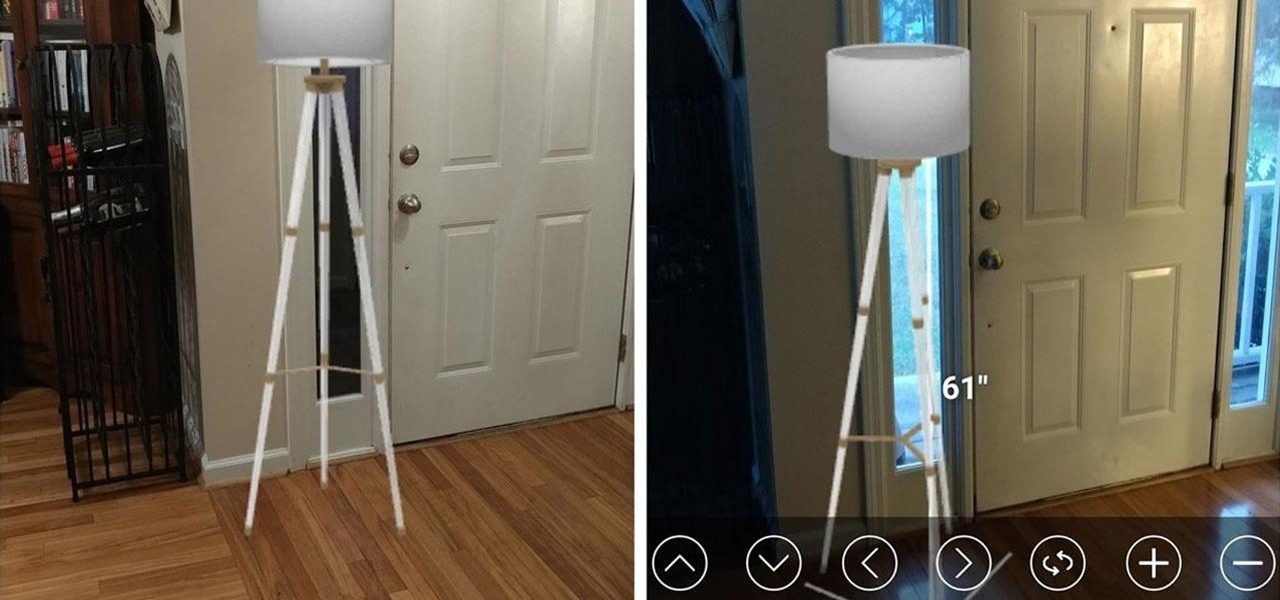
While some companies like IKEA and Lowe's zig towards ARKit to entice shoppers, Target has opted to zag to broader appeal with an augmented reality see-before-you-buy tool for its mobile website.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

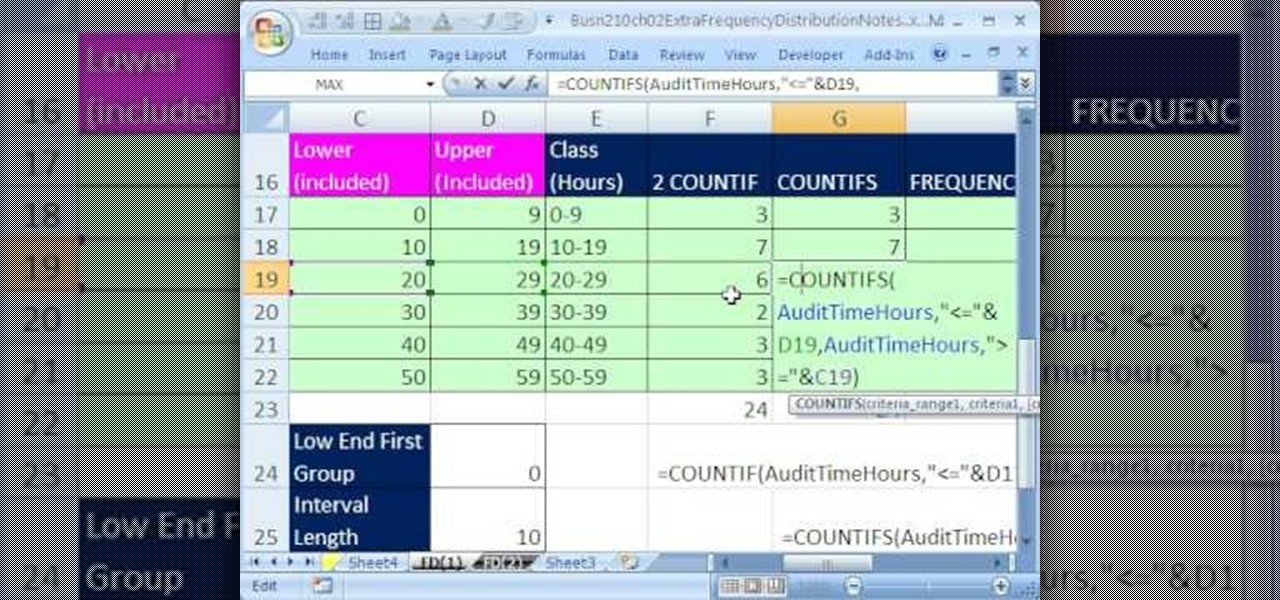
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 24th installment in his "Excel Statistics" series of free video lessons, you'll learn how to create quantitative data frequency distributions with pivot tables. See how to create the correct unambiguous labels ...

If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 12th installment in his "Excel Statistics" series of free video lessons, you'll learn how to use Advanced Filter 'Unique Records Only" to extract a list of unique items from a data base, and then use the COUNTI...

Check out this informative video tutorial from Apple on how to format data values with the format bar in Numbers '09.

In this free video exercise lesson, you'll learn a popular variant on the push-up, one designed to target your triceps. With pushups, as with any body-sculpting exercise, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. For more information, and to get started using this exercise yourself, watch this handy home-fitness how-to.

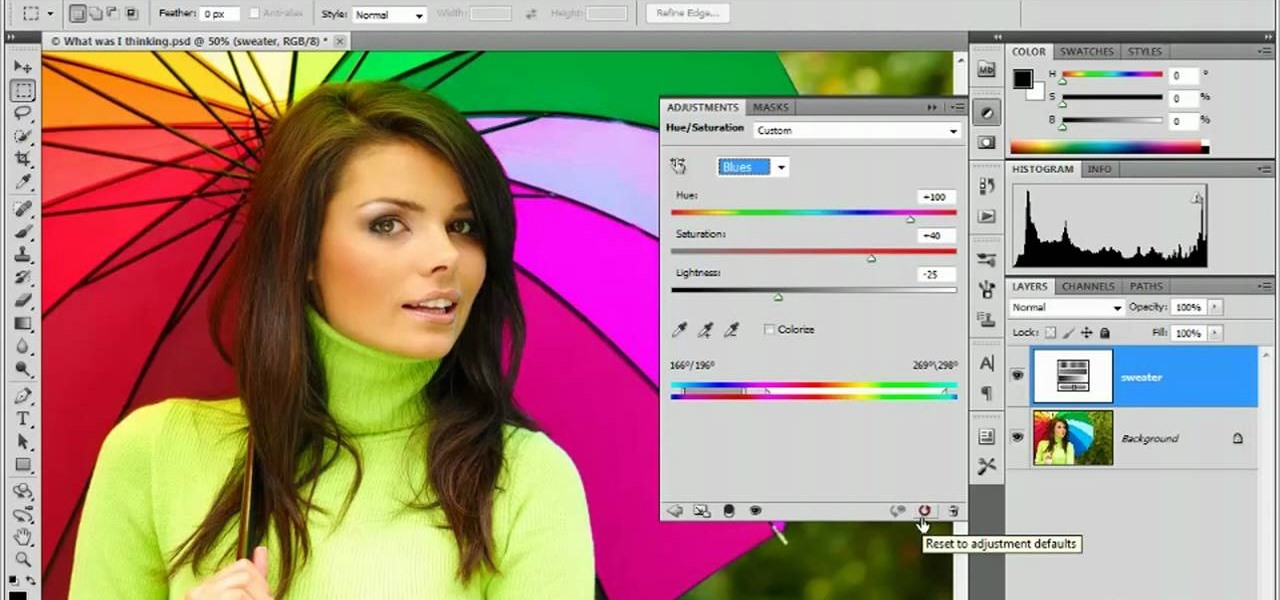
Learn how to use the Target Adjustment feature in Adobe Photoshop CS5. Whether you're new to Adobe's popular image editing software or a seasoned graphic design professional just looking to better acquaint yourself with the unique features of Photoshop CS5, you're sure to find something of value in this free video tutorial.

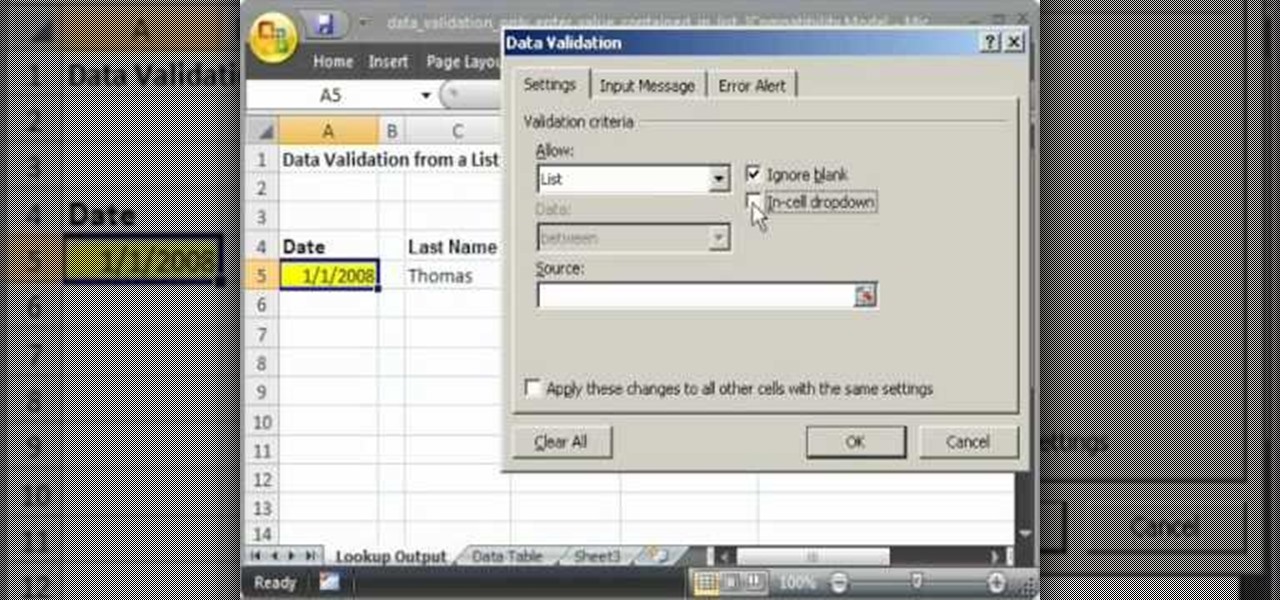
This video shows you how to idiot-proof a data set in Excel pretty much. It demonstrates how to enable data validation in a cell, so that when you type something in it must be in a predetermined list or will not work. Start by typing in your data table in a second tab. His example is a date, then information about certain employees based on that day. To enter the data validation menu, click the cell you want to use and then hit ALT+D+L to bring it up. Go to settings, then under the Allow menu...

This video explains how to throw a football like a quarterback. With your elbows bent at a 90-degree angle, hold the ball in front of your chest with the fingers of your throwing hand across the laces of the football.

Looking to find the standard deviation of your set of values? Standard deviation quantifies how diverse the values of your data set are, and is useful in determining how different your numbers are from each other.

We all have our reasons for erasing personal data from a phone. Whether you just ended a bad relationship whose face you never want to see again (lots of text messages) or just want to restore your privacy on the cell phone, erasing may be your only option.

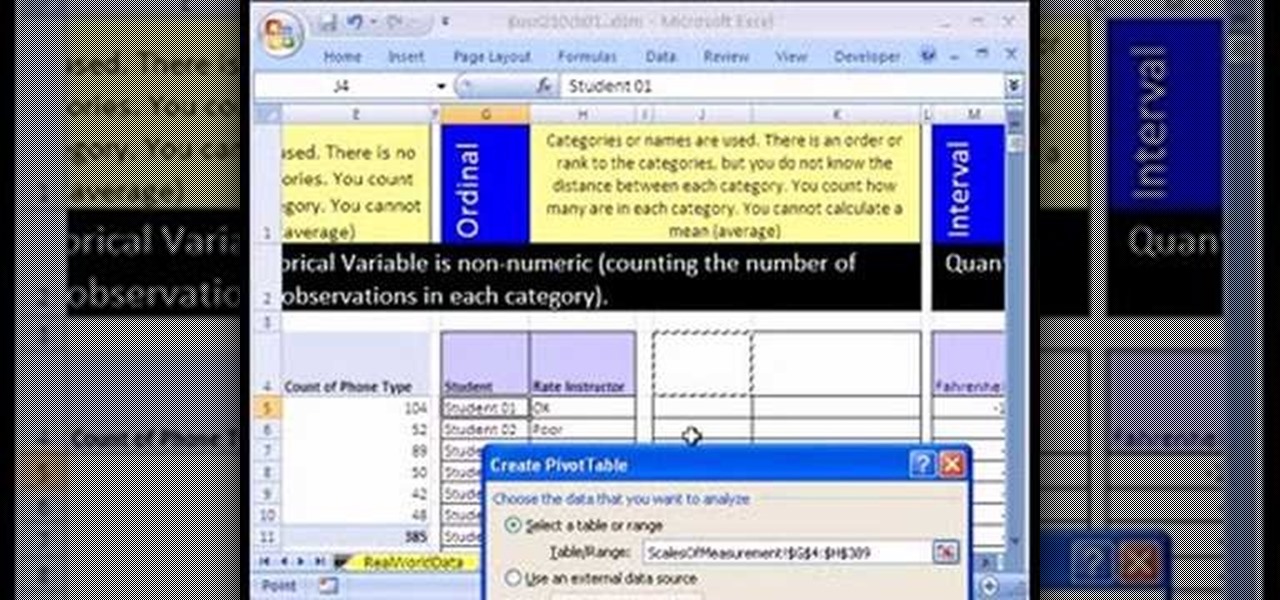
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 10th installment in his "Excel Statistics" series of free video lessons, you'll learn how about data sets and the nominal, ordinal, interval and ration scales/levels of measurement and see two Pivot Tables that...

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.