Mobile data is expensive. The internet connection that comes with your cell phone plan is generally limited to a certain amount of gigabytes that can be downloaded before your monthly cap kicks in, at which point you run the risk of incurring costly overage fees.

It's no secret that Google stores your search history in order to provide you with targeted ads when surfing the web. What's even more interesting (or freaky) is that your Google Now voice searches are also being stored, and you can actually listen to them right now.

Amazingly enough, some of us still have to worry about exceeding our monthly mobile data limits. You'd figure carriers would have given the customers what they want by now by offering truly unlimited plans, but with two conglomerates sitting atop the U.S. cellular market with fat pocketbooks that make for limitless lobbying, they can basically do whatever they want.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.
This video will show how to target your facebook post for a specific audience. With this tutorial video you could target a set of audience who has interest about the post.

Smartphones are becoming pocket computers, jammed full of data essential to our personal and professional lives. With AT&T's 360 Backup app you can protect your important information with the push of a few buttons.

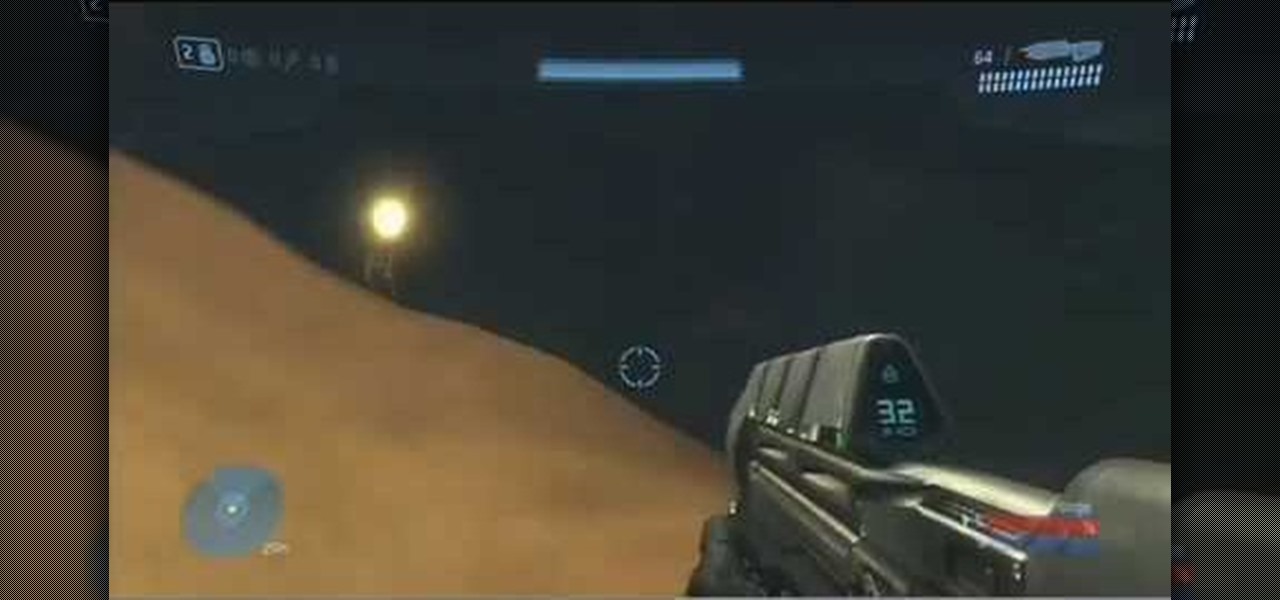
In this tutorial, we learn how to unlock the Tank Dropper achievement in Halo 3. This is an easy achievement that you will do when you first start out in the level. This is where you have to drop a tank onto someone and kill them. To do this, you need to stand up on a higher area and find your target. Once you do this, you will be able to grab the tank and then drop it onto the target you have found. After this, you will get the achievement and you will be able to continue on. If you miss, ju...

If you picked up a new Xbox 360 Slim, the first thing you're going to want to do is transfer all your old saved game data from your old Xbox 360 to the new internal hard drive in the Slim 360.

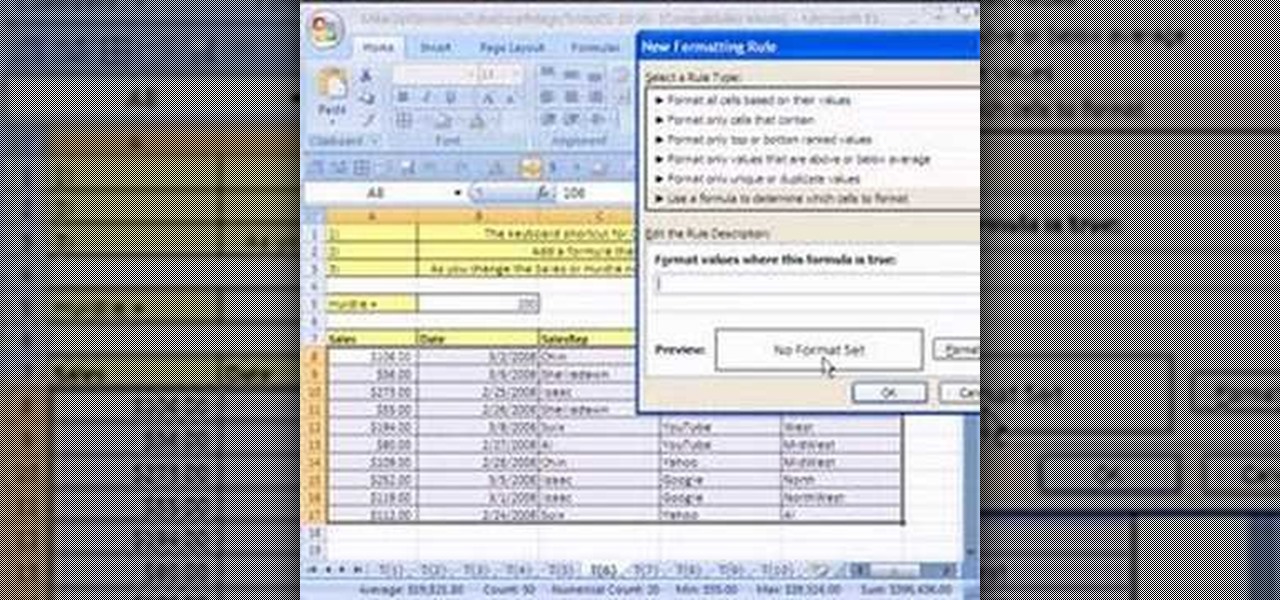
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 6th installment in their series of digital spreadsheet magic tricks, you'll learn how to add conditional formatting to a whole row of data in an Excel sheet.

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 241st installment in their series of digital spreadsheet magic tricks, you'll learn how to create a data validation drop-down cell list where the list shrinks as you select values.

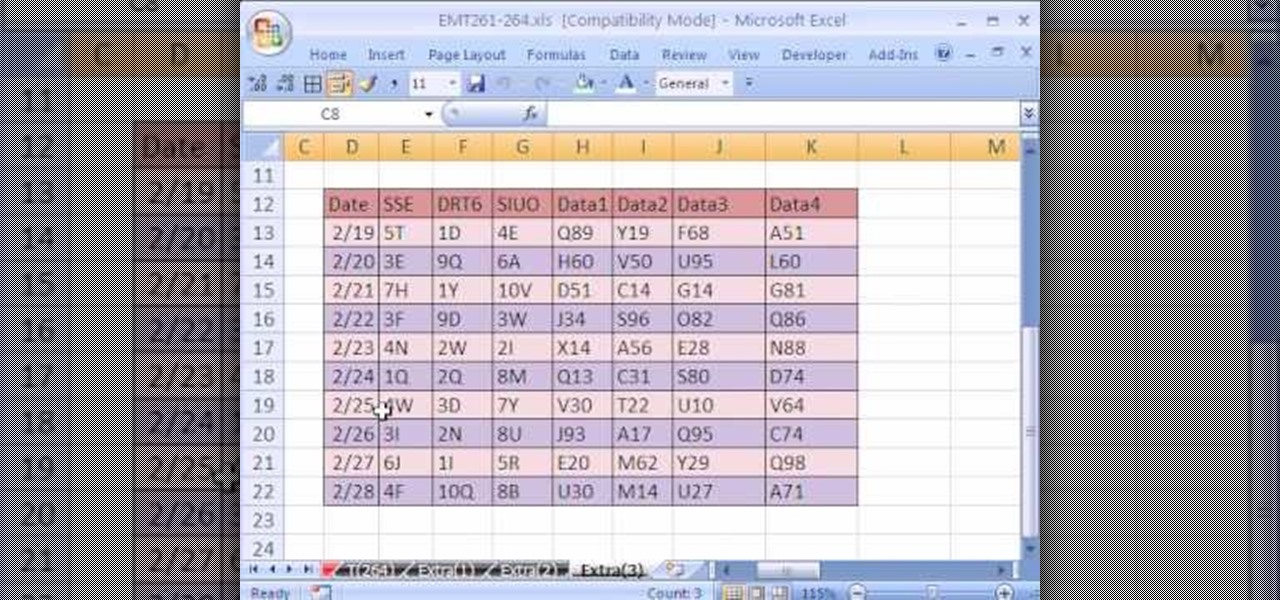
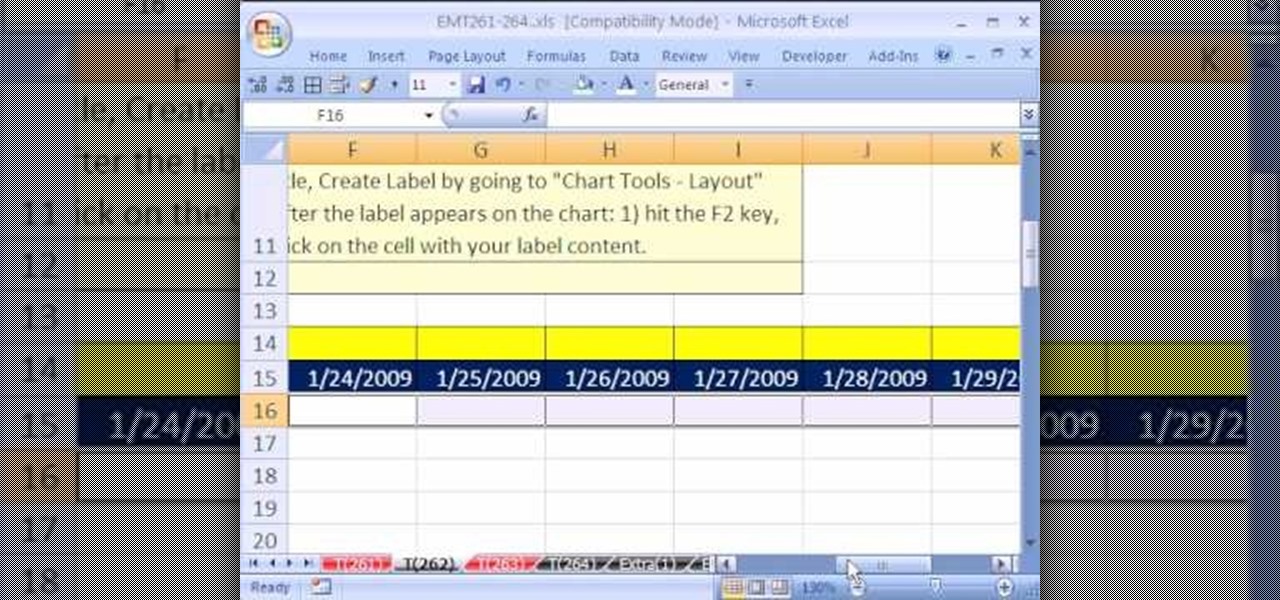
New to Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this Excel tutorial from ExcelIsFun, the 264th installment in their series of digital spreadsheet magic tricks, you'll learn how to use a recorded macro to take a data set and add a new column, concatenate data from 3 columns, and delete unwanted columns.

New to Excel? Looking for a tip? How about a tip so mind-blowingly advanced as to qualify as a magic trick? You're in luck.

In this video the instructor gives tips on how to erase a PC hard drive. An MIT study shows that 74 percent of the discarded hard drives contain private data on them that can be read and recovered by others. So you should learn how to completely erase all the data so that no one can recover or read from it later. Now formatting the drive or deleting a few files wont do it. For this you will need to have a proper software that meets or exceeds that US Department of Defense standards for data r...

MySQL is a database for serving data on the web. This video teaches viewers how to connect to a database and add data in PHP & MySQL. PHPMyAdmin is an interface that allows you to interact with MySQL more easily. Use the form in the program to create a database; choose the name for your database and select 'create'. Next you can create tables within your database, also using the forms provided. Within the tables you can set your variables; PHPMyAdmin has fields that allow you to choose the ty...

The new Pyro FX in Houdini 10 are very impressive with improved workflow. The Pyro FX are great for creating 3D fire and smoke effects. And in this video tutorial series, you will learn the Pyro FX workflow in-depth and the parameters used to create fire and smoke effects. You will also see how volumetric data is created and recorded, and how to visualize it.

Microsoft ASP.NET is a free technology that allows programmers to create dynamic web applications. ASP.NET can be used to create anything from small, personal websites through to large, enterprise-class web applications. All you need to get started with ASP.NET is the free .NET Framework and the free Visual Web Developer.this video tutorial will demonstrate the new ListView control in Visual Studio 2008. Because the ListView is data-driven, you will need a data source. You can use any data so...

Microsoft ASP.NET is a free technology that allows programmers to create dynamic web applications. ASP.NET can be used to create anything from small, personal websites through to large, enterprise-class web applications. All you need to get started with ASP.NET is the free .NET Framework and the free Visual Web Developer. By creating a new website, this video tutorial will demonstrate the new ListView control in Visual Studio 2008. Because the ListView is data driven, you will need a data sou...

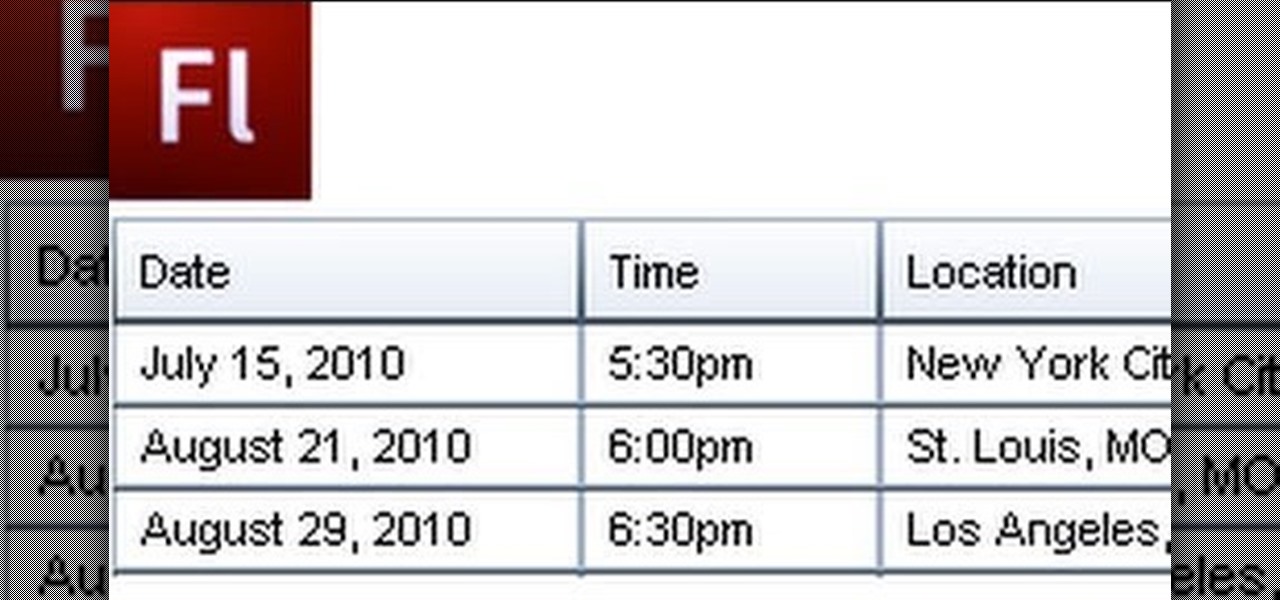
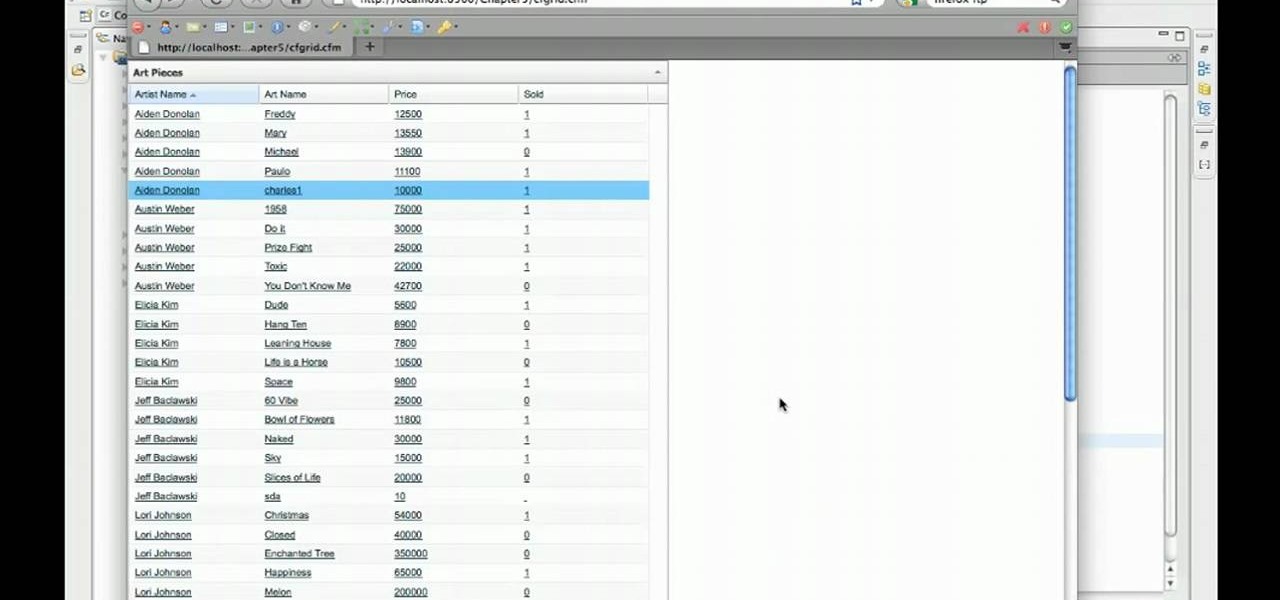
A Data Grid lets you organize information on your website or other Flash project. Create lists or schedules, like concert dates, by using the Data Grid component included in Adobe Flash CS4, and then modify it using Action Script 3.

Learn how to create a summary of your budget data. Whether you're new to Microsoft's popular digital spreadsheet application or a seasoned business professional just looking to better acquaint yourself with the Excel 2010 workflow, you're sure to be well served by this video tutorial. For more information, and to get started summarizing your own budget data, watch this free video guide.

Quickly and intelligently organize your information through use of ColdFusion 9's ever-useful data grid feature. Whether you're new to Adobe's popular rapid Internet application development platform or simply wish to become better acquainted with the program, you're sure to find benefit in this free video software tutorial. For more information, including specific, step-by-step instructions, take a look.

Want to know how to back up your data to an external hard drive? Protect yourself against data loss and heartbreak with this free home computing how-to from the folks at CNET TV, which offers complete instructions on how to back up your important files either manually or automatically. For specifics, and to get started backing up your own stuff, watch this handy how-to.

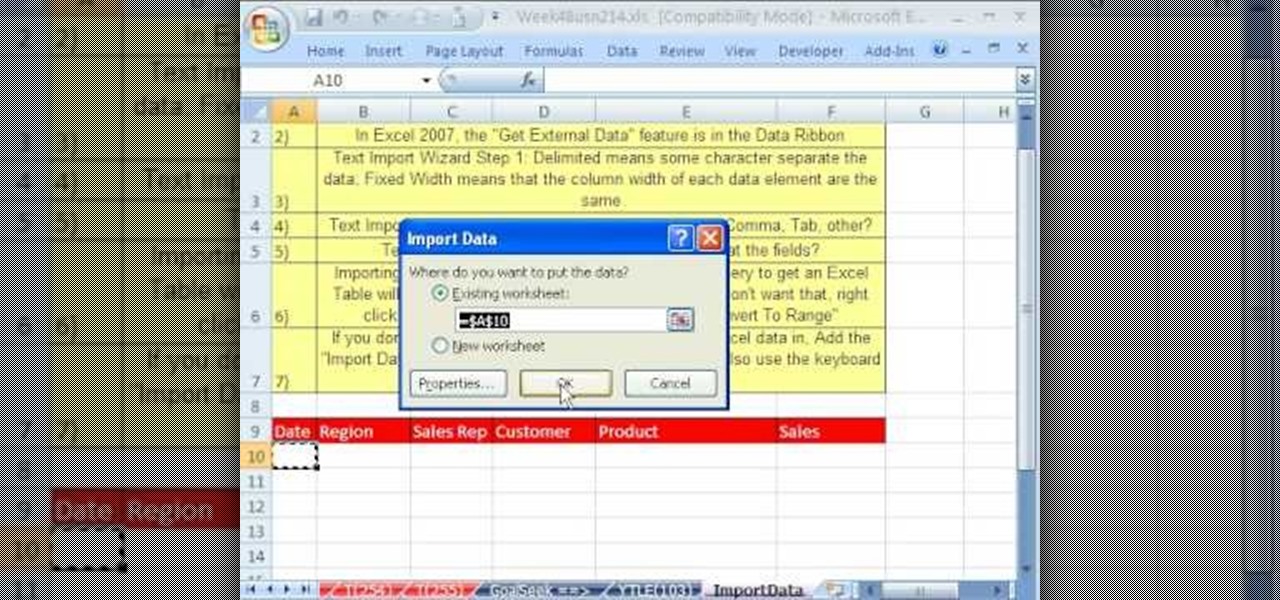
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you're in the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 23rd installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to import data into Excel from text files, web sites, Excel files and Microsoft Office Access files. Also see how to import currency rates and major indicies from ...

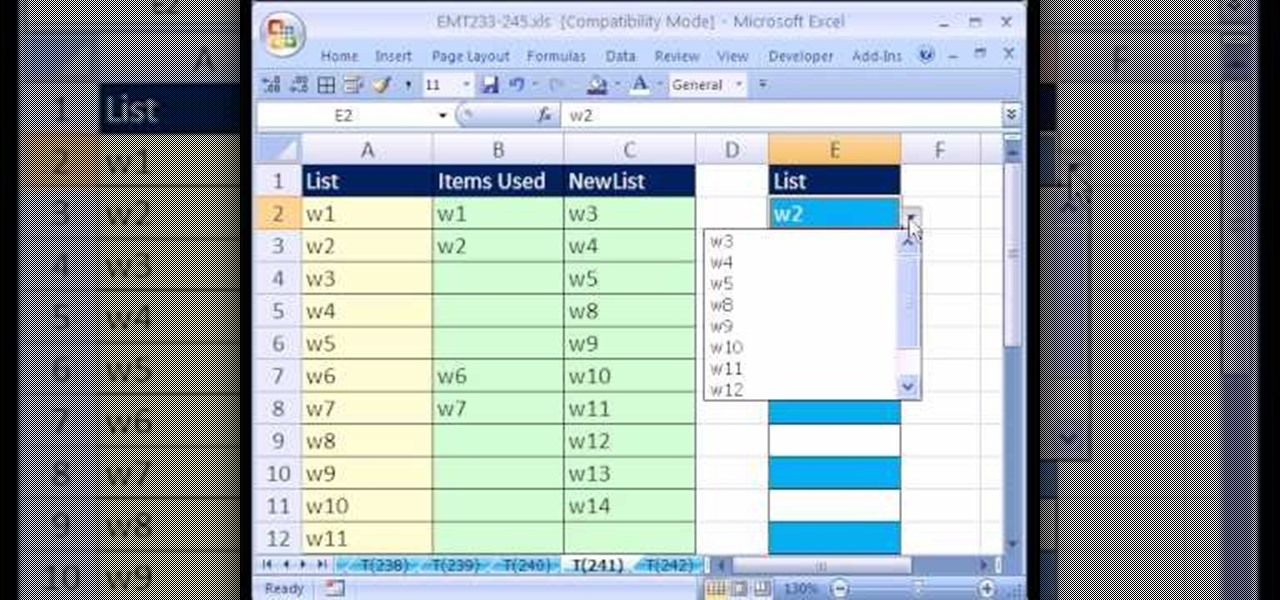
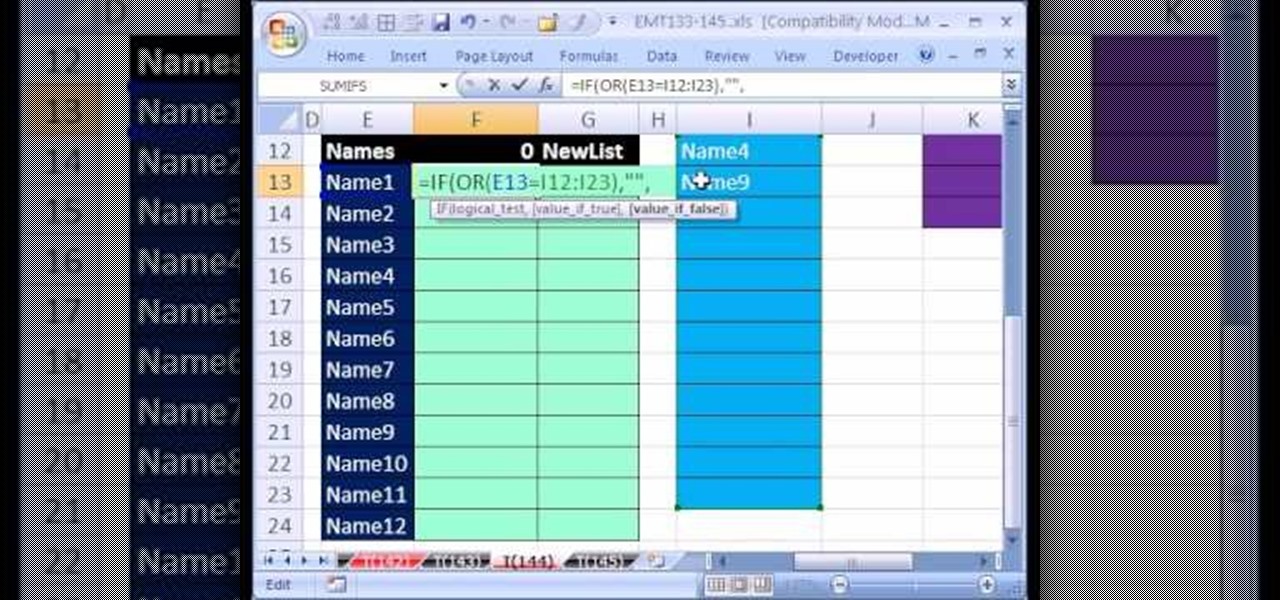
Love Microsoft Excel? This clip contains a tip that just might induce you to. With this free video tutorial from ExcelIsFun, the 144th installment of his "YouTubers Love Excel" or YTLE series of free video MS Excel lessons, you'll learn how to work around data validation's one-rule limit by creating a second shrinking list that looses values as they are used in the data validation area.

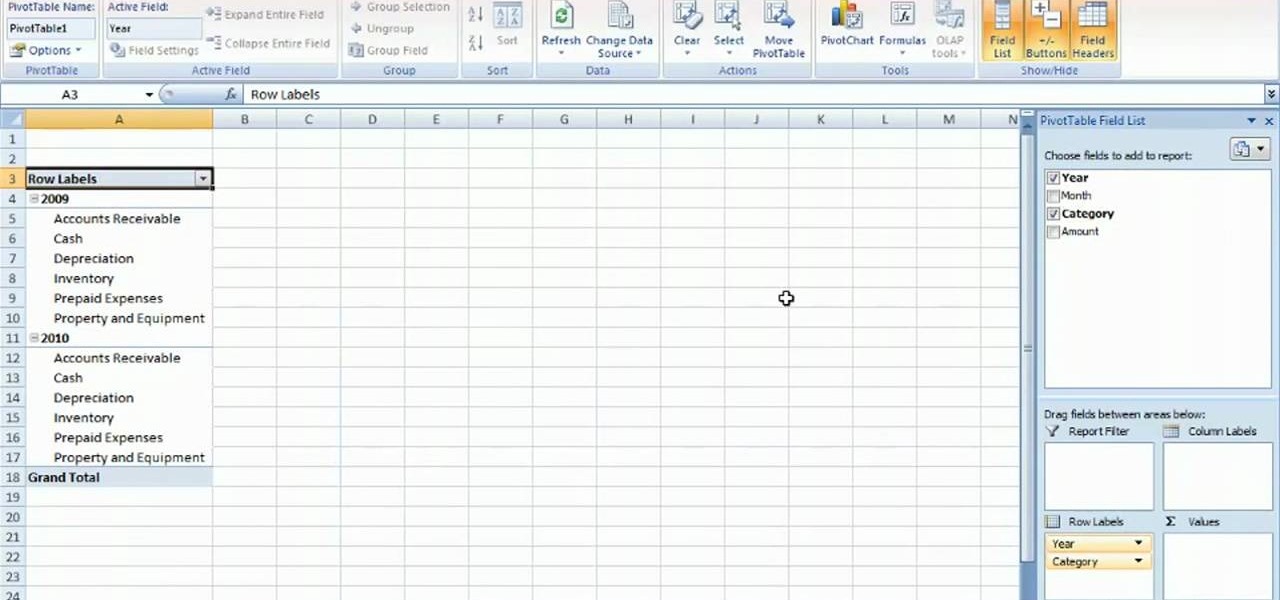
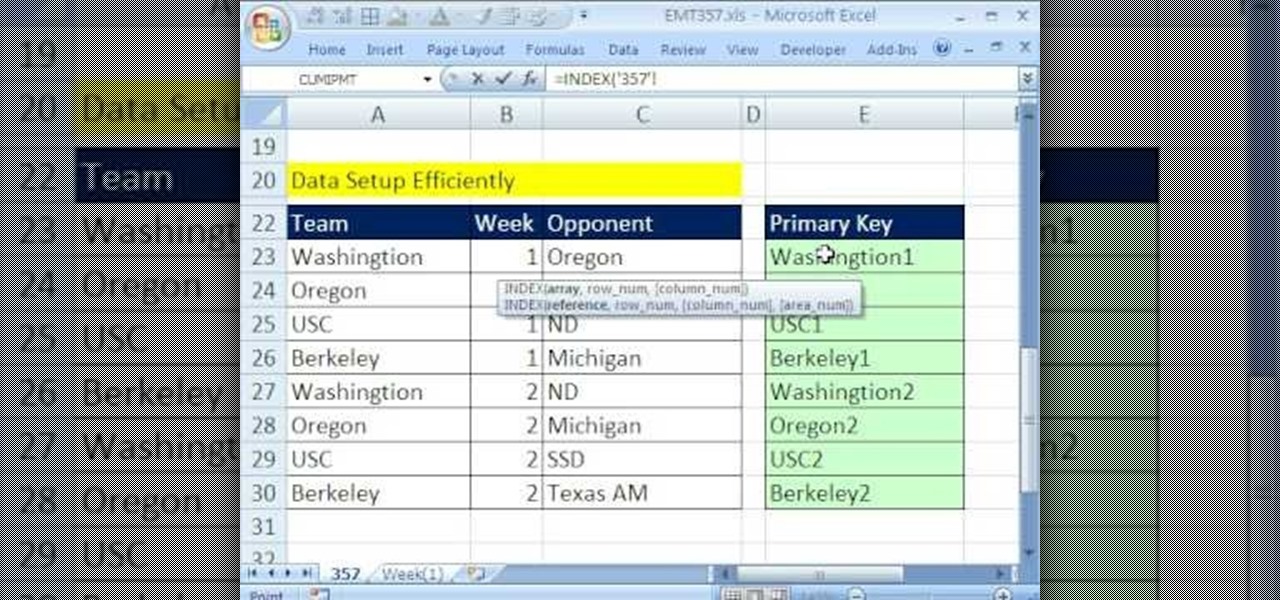
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 357th installment in their series of digital spreadsheet magic tricks, you'll learn how to pull data from individual sheets to a single master sheet given improper data setup.

Your data is your most important asset on your computer. Learn how to keep your data safe using Carbonite.com

QR codes allow you to quickly and easily store and retrieve data within a single image. Much like barcodes at grocery stores, QR codes are images that can be scanned to discover data, such as an online website URL. Additionally, they can also be created by inputting text data into a QR code generator. Try scanning some of the QR codes in this video with an app on your phone or tablet to see how they work!

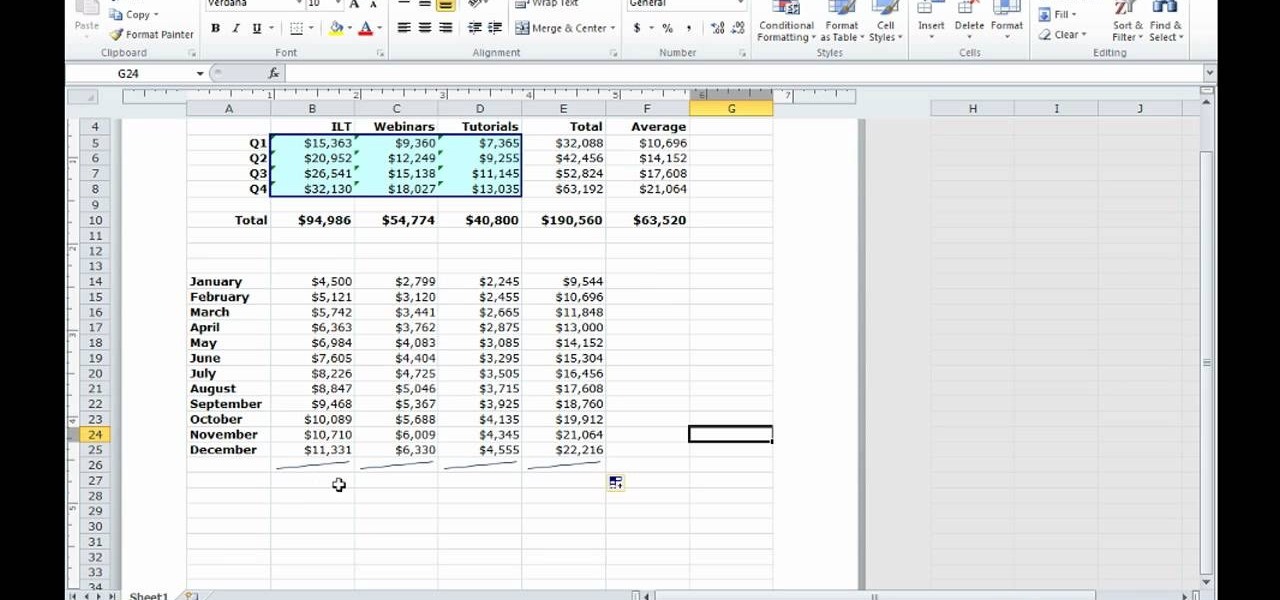
There is a new function in MS Excel 2010 called ‘Sparkline’ which helps you quickly find trends associated with a set of data. To create Sparkline, you can go to ‘Insert’ tab and then select ‘Sparkline’ section and then select the graph type. After you enter the data range and location range, the Sparkline will show up indicating the trend based on the data range you identified earlier. You can change the types and styles of your Sparkline easily. As the video demonstrates, whenever you use E...

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.