This video explains how to throw a football like a quarterback. With your elbows bent at a 90-degree angle, hold the ball in front of your chest with the fingers of your throwing hand across the laces of the football.

Want to perform an unplugged version of Blink 182's "Easy Target"? See how it's done with this free video guitar lesson, which presents a complete breakdown of the song and its chords. While this tutorial is geared toward those who already have some knowledge of the guitar, players of all skill level should be able to follow along given adequate time and effort. For more information, and to get started playing "Easy Target" on your own acoustic guitar, take a look!

Traveling often is super fun, but sitting through 13 hours on the flight from California to Bangkok is killer on your skin, especially since the airplane recycles air and therefore dries out your skin.

Big-box retailer Target has been on a bit of an augmented reality advertising shopping spree via Snapchat lately.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

It's a real challenge to create exploding targets that can be set off by low velocity projectiles, yet remain safe to handle without risk of ignition during construction.

In this free video exercise lesson, you'll learn a popular variant on the push-up, one designed to target your triceps. With pushups, as with any body-sculpting exercise, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. For more information, and to get started using this exercise yourself, watch this handy home-fitness how-to.

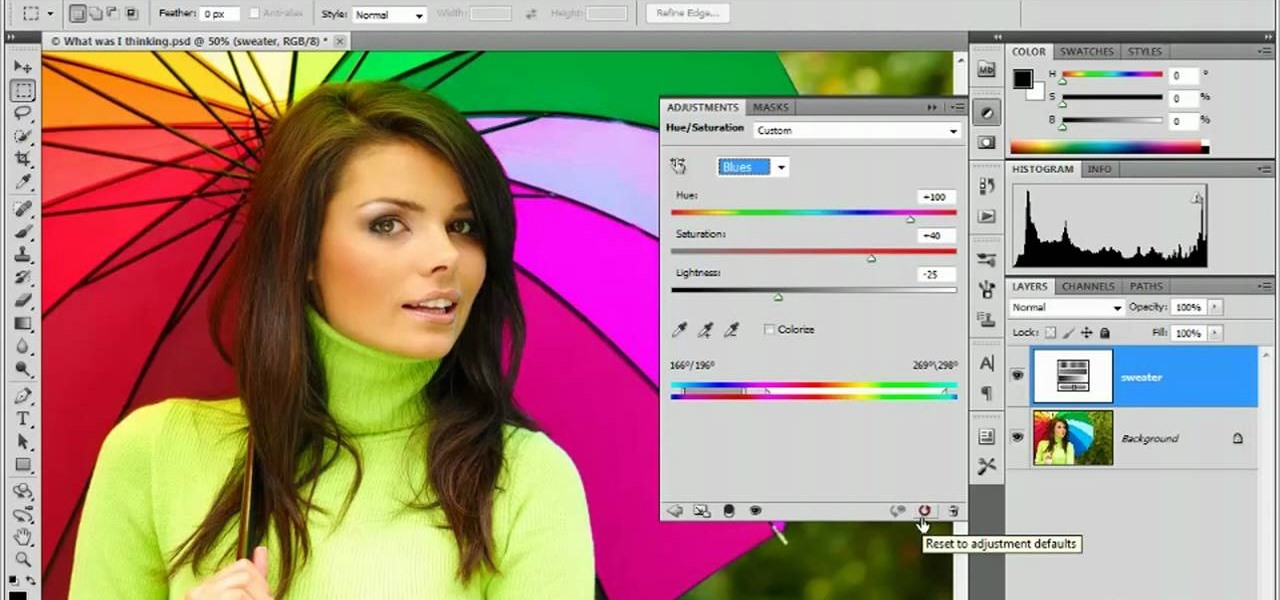
Learn how to use the Target Adjustment feature in Adobe Photoshop CS5. Whether you're new to Adobe's popular image editing software or a seasoned graphic design professional just looking to better acquaint yourself with the unique features of Photoshop CS5, you're sure to find something of value in this free video tutorial.

In this clip, you'll learn how to create a new material resource when using MS Project 2010. Whether you're new to Microsoft's popular project management application or are just looking to better acquaint yourself with the Project 2010 workflow, you're sure to benefit from this free video software tutorial from Lynda. For more information, including detailed, step-by-step instructions, take a look.

This video describes how to free up system resources on your Mac, resulting in better Pro Tools performance. Whether you're new to Digidesign's Pro Tools 8 or simply looking to pick up a few new tips and tricks, you are certain to benefit from this free software video tutorial. For complete instructions, take a look.

Watch this ASP.Net video tutorial to learn how to create culture-aware and locale-specific web content with no additional code. Use the Resource Editor to create page-level and application-level resources.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

Department store chain Target is the latest retailer to offer an augmented reality cosmetics app for customers to virtually try on lipstick.

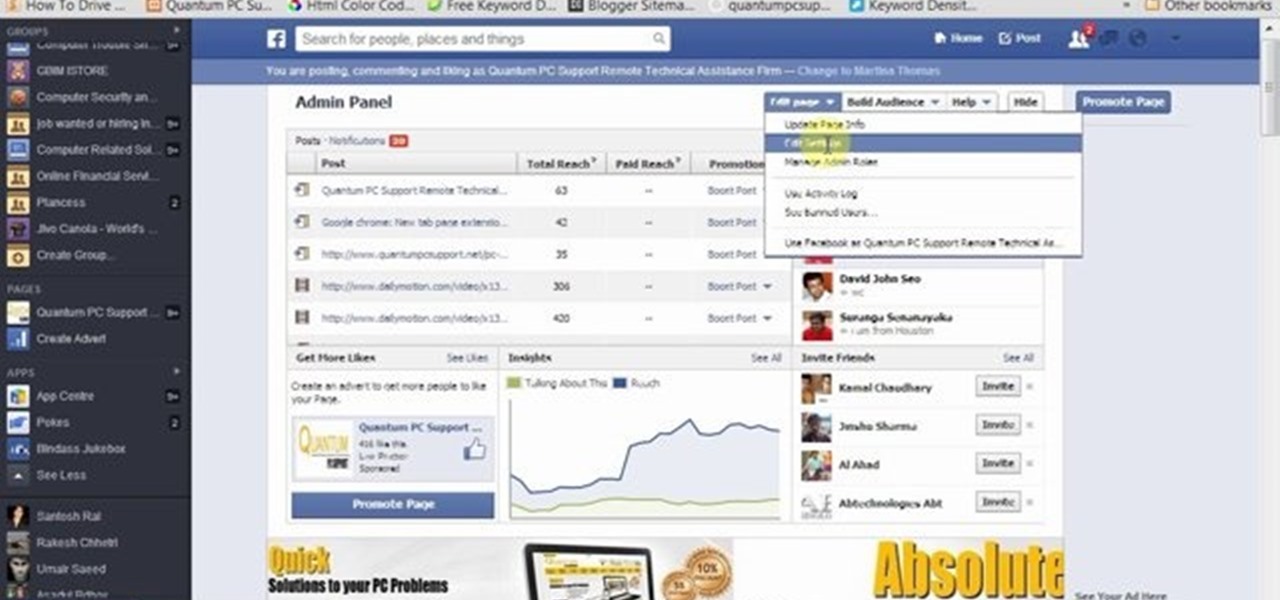
This video will show how to target your facebook post for a specific audience. With this tutorial video you could target a set of audience who has interest about the post.

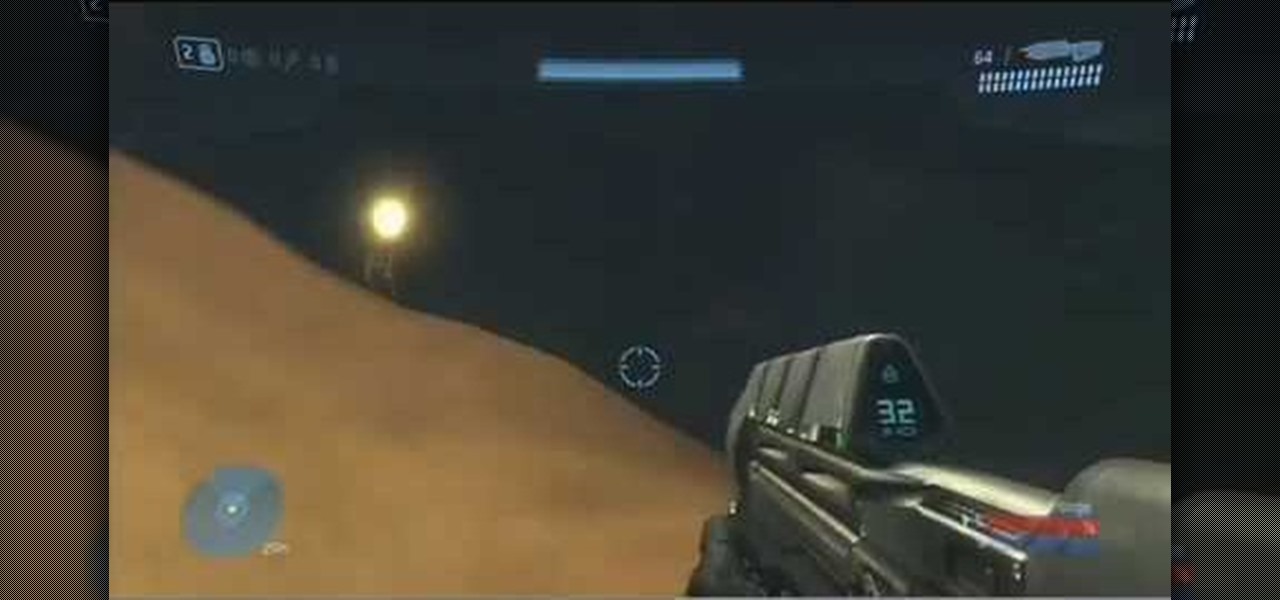
In this tutorial, we learn how to unlock the Tank Dropper achievement in Halo 3. This is an easy achievement that you will do when you first start out in the level. This is where you have to drop a tank onto someone and kill them. To do this, you need to stand up on a higher area and find your target. Once you do this, you will be able to grab the tank and then drop it onto the target you have found. After this, you will get the achievement and you will be able to continue on. If you miss, ju...

In this video we are shown a workout that targets your stomach and helps you to lose belly fat and tighten your lower abs.

Take a look at this instructional video and learn how to fit a projected image onto a target surface with Johnny Chung from Carnegie Mellon University. Typically, you'd need to use a screen to be directly in front of the projector and at a very specific orientation to get an undistorted image. What this tutorial is trying to accomplish is to place a screen at any location that is convenient and then calibrate the projector onto the target surface. This technique is used to automatically disco...

The object is to pass to ball between the cones in as few shots as possible, watch and learn how to do this target passing soccer drill.

All-American Skeet Champion Todd Bender explains the safety "does and don'ts" of shooting clay targets. He shows how everyone in the family can enjoy the game and still use proper gun handling techniques.

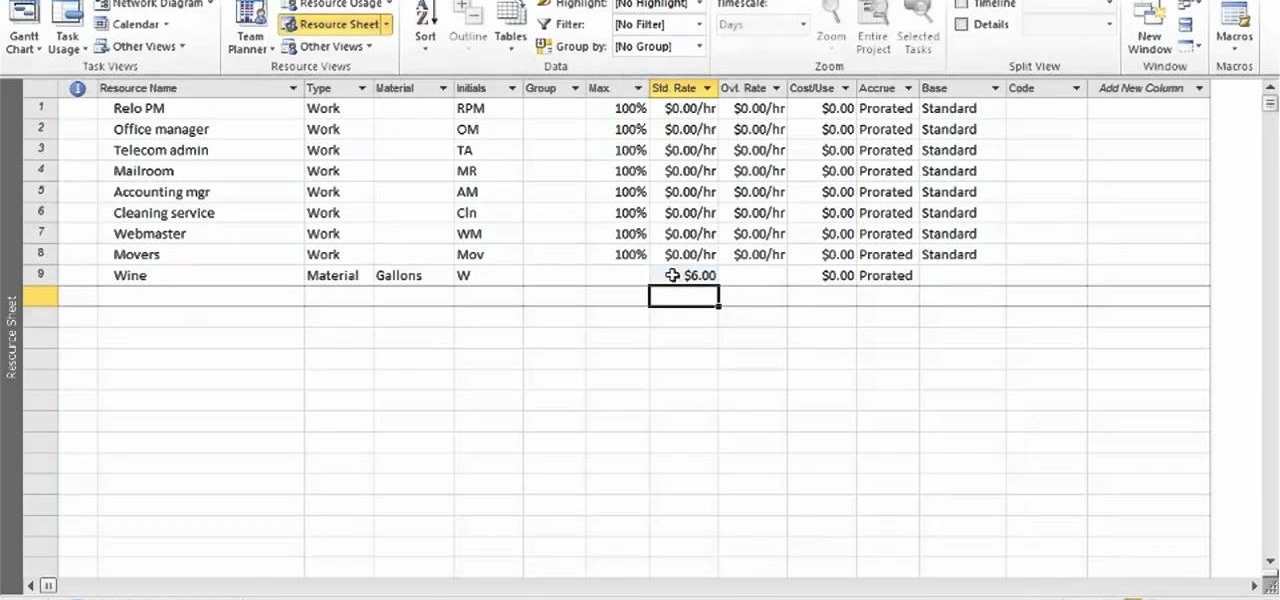
In this tutorial, we learn how to set up work resources in MS Project 2007. First, go into your chart and click on the resource sheet from the file menu. Now, you will be able to change the different sections that show up on this sheet. Go through the different columns to change the information and type in additional information, the more you insert the better. When you click on the tabs, you will have more options where you can enter in notes and make custom fields. Go through the entire she...

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

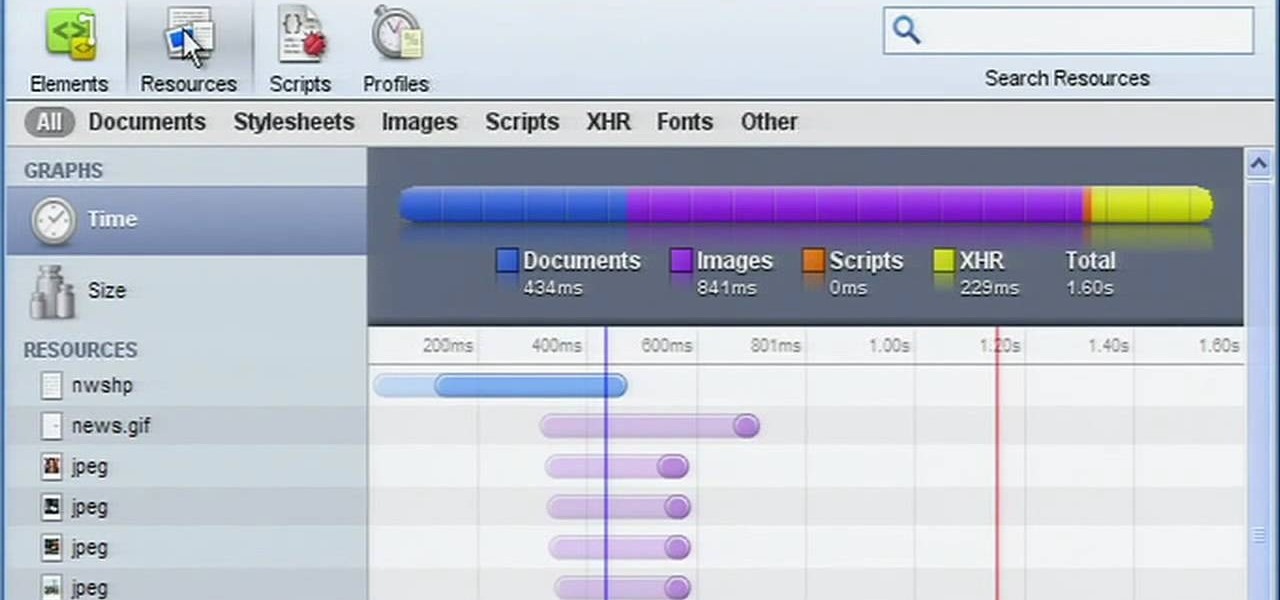
In need of a quick orientation on how to use the elements and resources panel in the developer tools of the Google Chrome web browser? This brief, official video guide from the Google Chrome team will teach you everything you'll need to know.

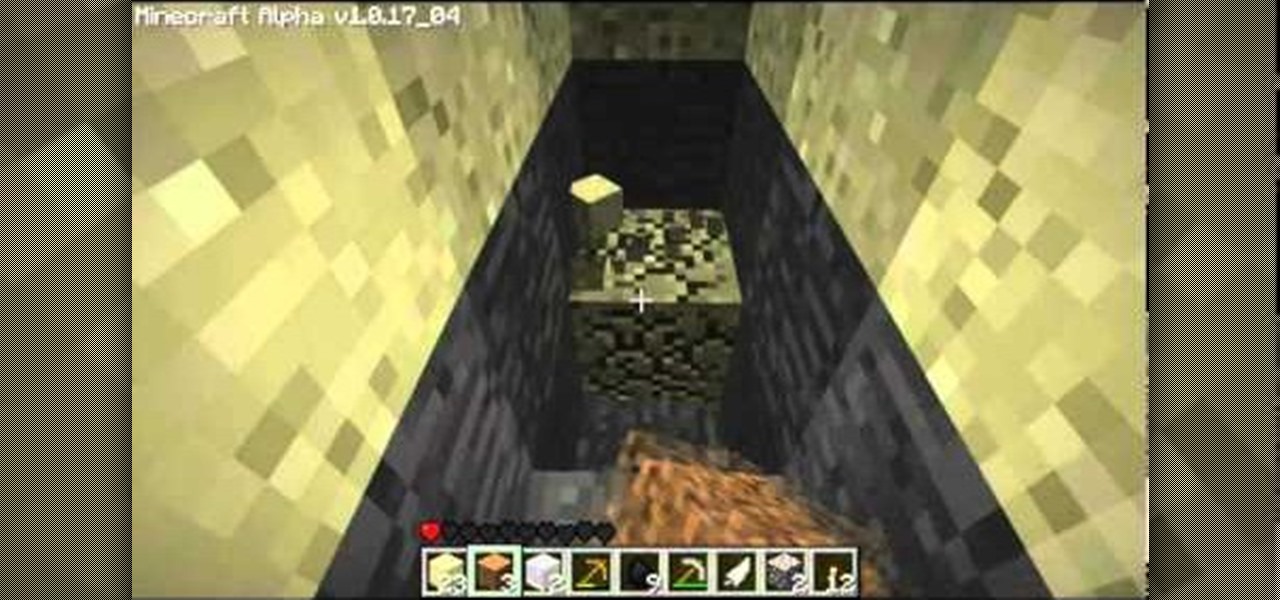
Minecraft is the surprise indie hit of 2010 and it's still only in Alpha! And one of the mainstays of the name, "mining" is a key element to not only survival but advancement in the game and the construction of bigger and better items, tools, armor, buildings, ect. If you're confused on how to find the materials, or maybe an effective way of actually creating a good mining tunnel, this video tutorial will guide you. You'll learn what types of materials you'll need, as well as what some of the...

Starcraft 2 is finally upon us after 12 years of waiting, and it is just as majestic as you would hope it would be. If you're new to the series or just haven't played in five years, the barrier to entry for the unskilled can high, especially if you prefer playing online multiplayer. Fortunately for you, we've compiled videos on just about everything you need to know about the game, including strategies and tips for winning with different races in different modes and situations, and even how t...

Windows users probably remember the system resource tab in the task manager which showed you your resource usage. Well, in Windows 7, this feature has been revamped. This tool will give you real-time reports for CPU, disk, network, and memory usage.

A short tutorial on how to view server resources usage using cPanel. This video is provided to you by Scandicsoft.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).