Check out this instructional baseball video that demonstrates how to play infield. This video offers a few tips for fielding ground balls. Learn how to make a play on a grounder from a professional in this baseball video.

There is not better way to get in shape and target trouble zones than with the help of some experts in fitness and some simple workout equipment. In this how to video tutorial SELF Magazine shows you how to tone and sculpt your body with a simple beach ball. Tone difficult areas with tilt-a-whirls, dipsy dos, squeeze play, close reaches, reverse lunges, pendulums, hold your own and tummy toner exercises.

Going towards the infinite white light means something totally different these days. When we talk about the infinite white light, we're thinking less spiritual and more aesthetically pleasing. That's because a background consisting of a blurry, infinite white light is one of the most flattering you can use for a human subject.

When shooting a shotgun, you don't really have to aim--just point and shoot. Whether you hit what you're shooting at depends on how well you did your homework. "Patterning" your shotgun allows you to choose exactly the right brand of shells, size and type of shot and type of choke required for the game you're pursuing. Set yourself up 40 yards from a 30-inch circle target, and bring along several brands of shells in various shot sizes. Use some form of rest like sandbags on a table or a rolle...

In this ESL language tutorial we look at English slang. Slang is when you replace a common word or sentence with a totally new one. English slang often depends on the country and then region of the country you are in. This how to video teaches you some widely used slang words and phrases that you can say in English. Try out the words in this lesson and you will be "shooting the breeze" in English in no time.

Don't have time for a workout? Then watch this how to video to learn how to do a five minute workout that will get you six pack abs. These exercise will target your upper abs, lower abs, and obliques.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

After opening up its Spark AR platform on Instagram for all creators, Facebook is already expanding the platform's capabilities on its Snapchat killer.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

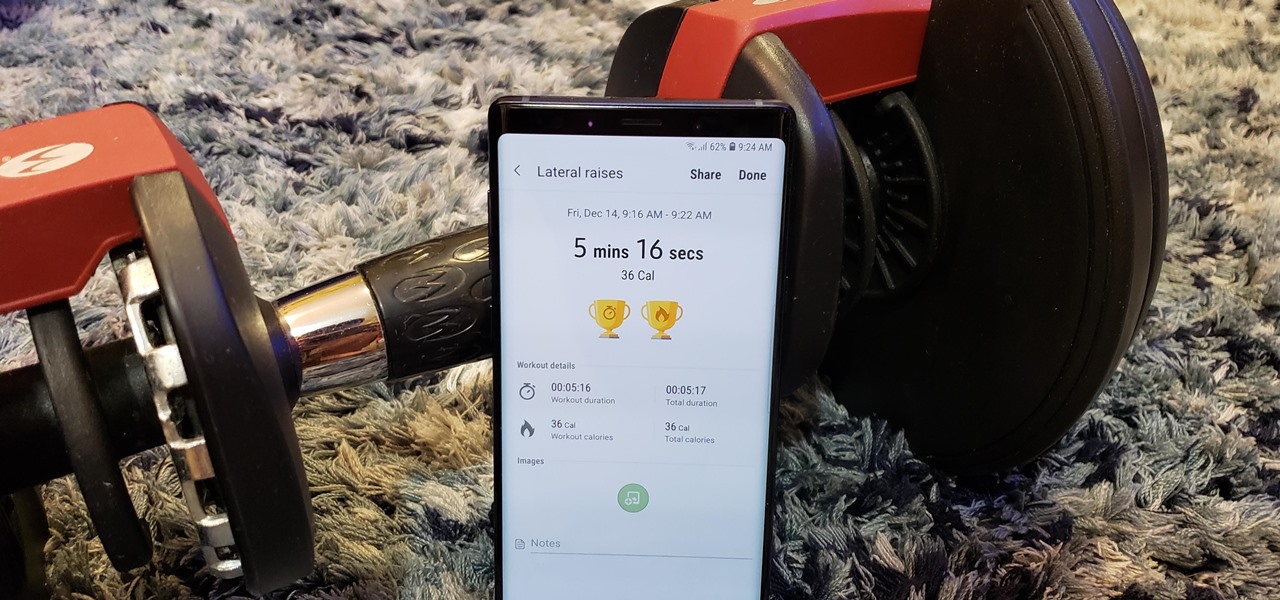
Keeping track of your physical activities can be difficult, especially if you have a hectic lifestyle with responsibilities to constantly stay on top of. Thankfully, Samsung Health is there to help you log your workout routines, leaving you with one less thing to keep track of as you go about your busy day.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

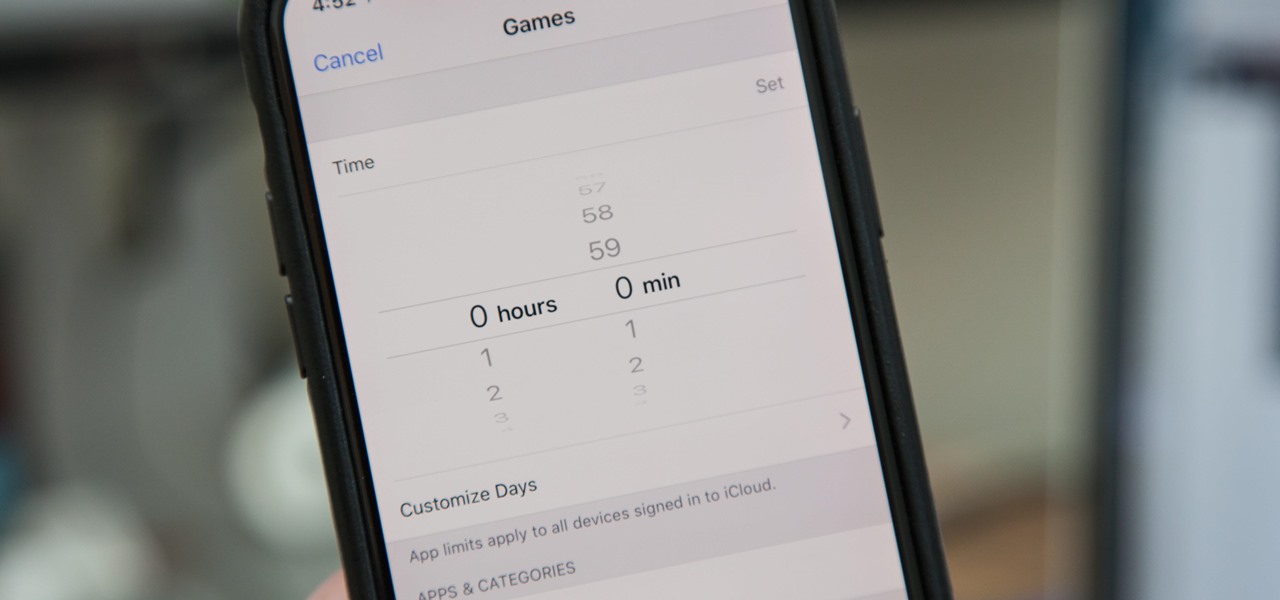
Most of us have, at one point or another, found ourselves glued to our smartphone in a trance-like state, totally unaware of what's around us. Well, Apple has a way to curb overuse with an awesome tool for iPhone starting in iOS 12. It can help nudge us away from our phones to spend more time attending to real-life matters.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

Virtual reality headsets aren't new, but they may be something you or someone on your holiday shopping list hasn't experienced yet. If you're going to dive into the world of smartphone-based virtual reality, the best time to do it is during Black Friday when all the good sales are going on.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done...

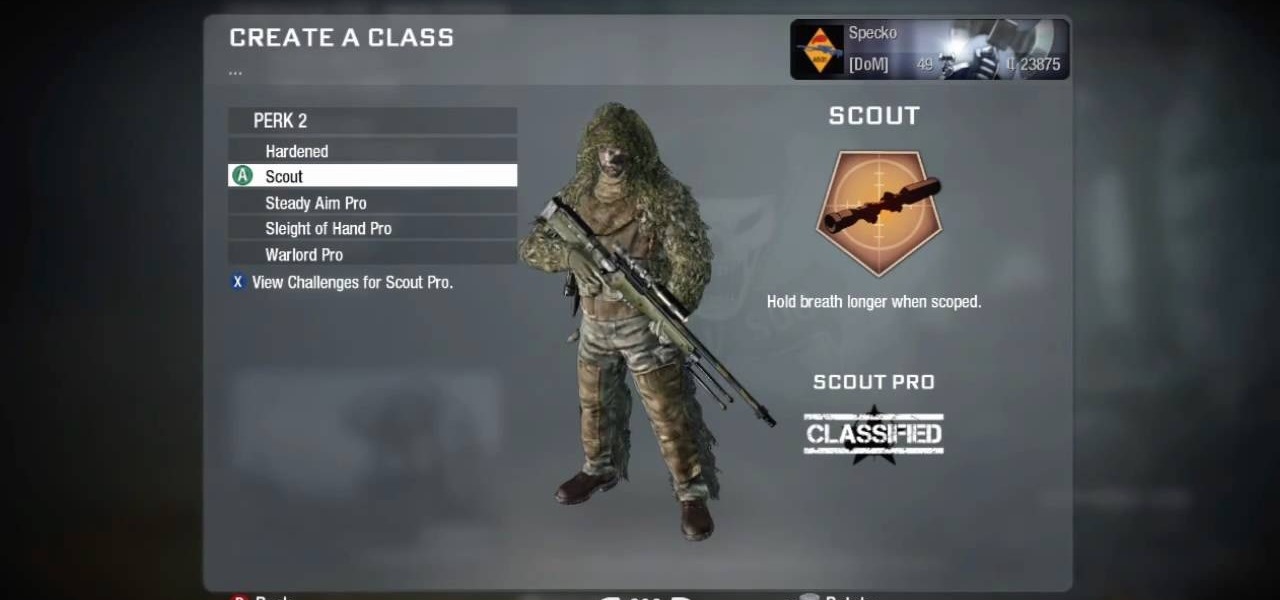
Creating your own emblem is a great way to show off your creative skills and show those stock-emblem clowns what's really up. And in the new Call of Duty: Black Ops 2, Treyarch decided to revamp the emblem editor, so now you can make more colorful and elaborate emblems.

Consider this reason 1,001 why we love the internet: Using Google, you can hack into almost any webcam or security cam, in any part of the world and even control the webcam to move around so you can get your full panoramic shot. Don't believe us? Then check out this video tutorial to learn the steps you need to take.

Friendship can't be bought with money or gifts, but an existing friendship can certainly be bolstered by some handmade wrist wear. While you can totally hit up Claire's and purchase their twosome friendship bracelets, the special letter-embellished bracelet in this video is so much more personalized.

You don't need to invest in fake hair - AKA hair extensions - to look like you have a head full of enviable voluminous, thick hair. In fact, all you need to do to create buxom hair looks is a few tricks, and a few hairstyles targeted towards making your hair look fuller.

Baking soda is like a miracle in a box. Whether you need to clean a doggy doo doo stain on your carpet, need to deodorize your refridgerator, or need an all-natural face scrub, baking soda has a cure for it all.

Did your little boy or girl see "How To Train Your Dragon" and totally fall in love with the the cool graphics and awesome - and, as it turns out, friendly - dragons? Then what better cake to bake for them on their birthday than a "How to Train Your Dragon" cake? Take a look at this cake decorating video to see how to create the mountain portion of the cake.

Sniping is a good skill to pick up when playing war games, since it allows you to kill enemies with great accuracy at long range. You'll need to find good spots with decent cover that give you access to enemy targets without revealing your own location.

Have you ever wanted to order coffee in another language? Well if you have, this is the video for you! When watching, make sure your audio is turned up so you can hear exactly how the phrases are said in Polish. Listen to the voice and get the different parts of the word down right so you have the correct sounds. If you don't have this right, you can end up saying a totally different phrase. Practice this a lot and then when you learn how to say it, you can speak it with ease! Have fun and en...

In this tutorial, we learn how to say basic phrases in Polish: "may I use...". Listen to the video and read the text as you practice saying each of these phrases. It's important to get the accent down right, or you can be saying a totally different word or phrase than you mean to. If you use these everyday, you will become more familiar with the answers you get to the questions as well! Just make sure you practice and go slow with these, no rush. Once you learn these, you will open your mind ...

In this tutorial, we learn how to lay down ceramic tile. Start off by laying down the mortar for the base. After this, scrape it around with the ridged laying tool. Then, lay the tile down flat and place a spacer in between the one that it is next to. Once you are finished with this one, continue the same process for the rest of them. Make sure you are laying the tile down totally flat and it is lined up with the other ones. There should be spacers in between all of the different tiles that a...

Love the idea of a superhero MMO, but prefer the feel and controls of a first person shooter? You can actually set up your controls and targeting system in the game to make the interface behave more like your favorite FPS!

What's better than delicious, fluffy cupcakes and ice cream? Delicious, fluffy cupcakes FILLED with icing! We're totally digging this comfort food love child, and you and your kids will too this Halloween.

Cheryl Cole is a very pretty lady, so she could wear any makeup look - or none at all - and still look fabulous. The hostess/singer looks especially beautiful in her new music video for "Promise This," in which she rocks a hardcore rock'n'roll inspired look with smoked out black cat eyes, contoured cheeks, and a nude mouth.

Got lots to do on Halloween and have little time to spare for throwing on a costume or putting on fierce makeup? Then you've hit the right makeup video. Whether you're simply in a pinch for time or you don't feel like going with the whole shebang for Halloween, this zombie makeup look is totally festive and creepy but so easy and quick to do.

Oh, how we wish we could live in the "Mad Men" era. We'd forgo the lack of women's rights (the women's right's movement was at the time still gaining speed), but we would totally love to raid Joan Holloway's fantastic wardrobe and learn her hair and beauty secrets.

Rompers aren't just for babies anymore! Rompers and jumpsuits are totally in style these days, but not everyone can pull them off, but that's only because they don't really know how to wear them. There's a romper and jumpsuit out there for virtually everyone, no matter how big, small or curvy. One of the big worries with rompers is the dreaded cameltoe. If the romper you're trying on gives you a camel toe, then just go for a bigger size, and then you can tighten it up to your shape with acces...