How To: Add 3D objects to your videos
Software needed: Voodoo motion tracker, virtual dub and blender


Software needed: Voodoo motion tracker, virtual dub and blender

First of all you have to understand that this exercise is very versatile and you can actually target different areas of your chest just by twisting your wrists. First of all lie down on the bench and hold the dumbbells in your hands. You can do this upper chest exercise to build your upper chest muscles using dumbbells. Now bring your dumbbells down and then again take them up. While bringing your dumbbells you have to twist your wrists towards inside such that your palms are facing away from...
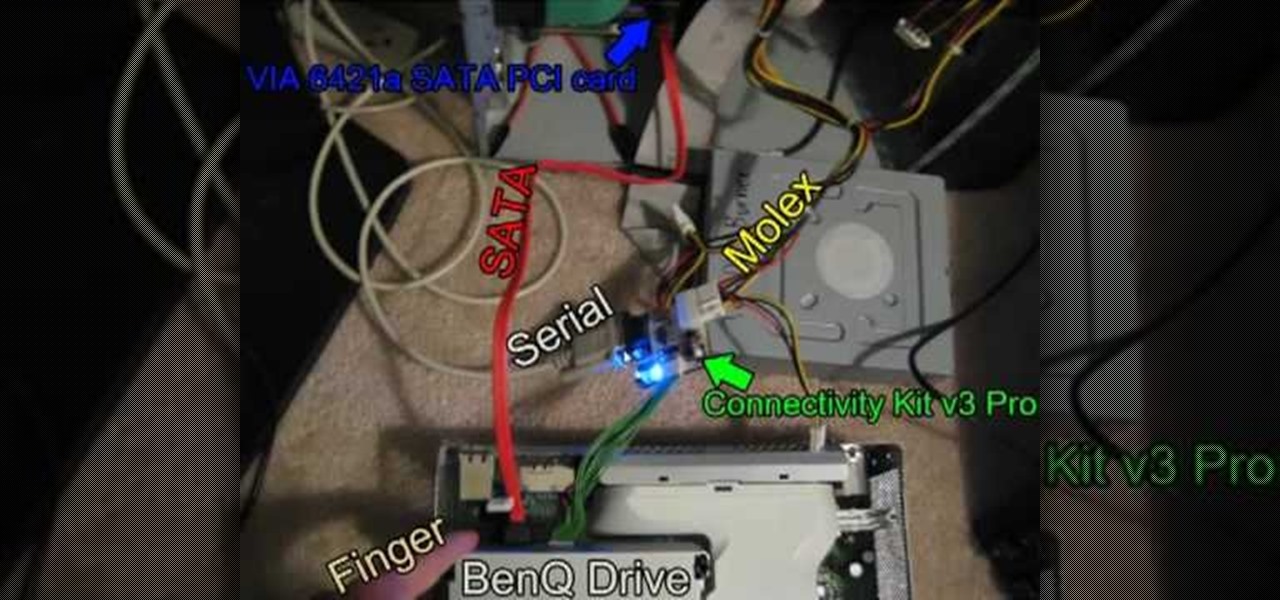
In this Video Games video tutorial you are going to learn how to flash the Benq VAD6038 Xbox 360 DVD drive. This video will show how to do this with the connectivity kit and the jungle flasher. You will need a compatible card for this. VIA 6421a SATA PCI card is probably the best card. Install the VIA card and make the connections as shown in the video. Before you power on the connectivity kit, install the port IO 32 drivers and also the USB drivers for the connectivity kit if you are using U...

If you're tired of getting sand kicked in your face at the beach because of your tiny chest muscles then the dumbell press exercise is for you. This professional tutorial demonstrates the simple workout that can build up your pectoral muscles in a healthy manner. The dumbell bench press is an awesome functional, athletic movement for you athletes. You will work the target muscle better by visualizing the target muscle. Go slow (a 3-1-3 tempo), and visualize that you are squeezing water out of...
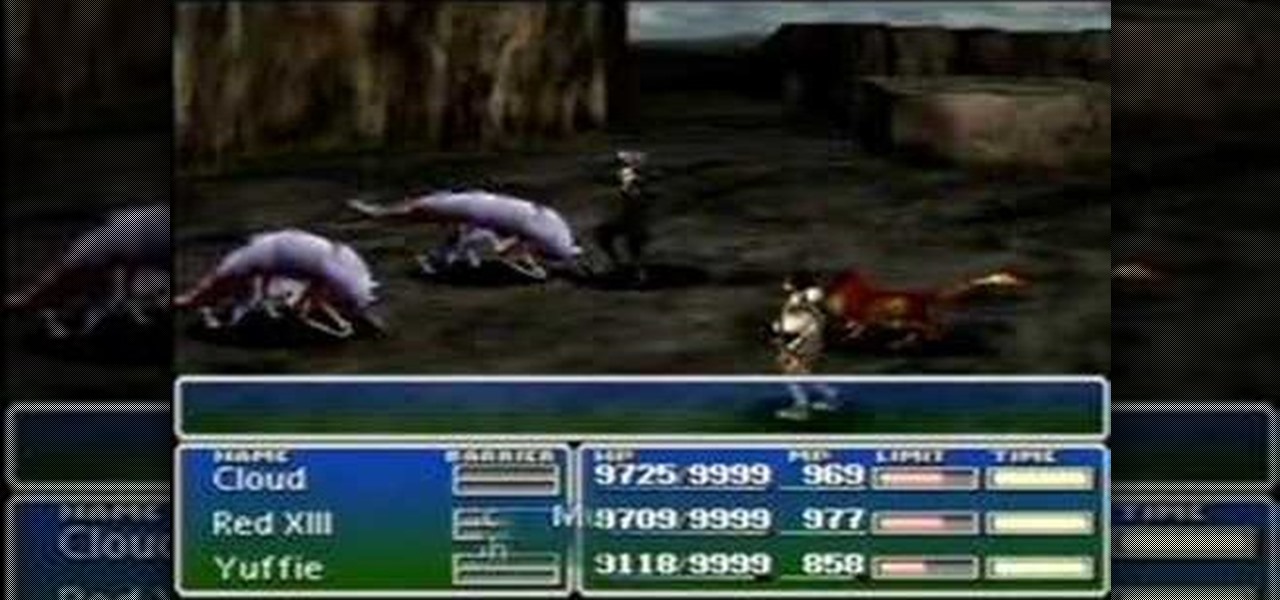
In Final Fantasy VII, it's possible to max out vitality without any store-related progress needed if your strength stat has already been maxed. Take a look at this video and learn how to max out vitality simply by targeting an enemy called "spiral".

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Our smartphones have outlived the Walkman, iPod, and even stereo systems, to some degree. So it makes sense to treat your iPhone or Android device to a quality pair of headphones, whether you're a hardcore audiophile or just an everyday music lover. This doesn't come cheap, of course, so why not buy them on Black Friday?

Speakers today are a marvel for their portability and sound quality. No longer do we need giant boxes to bring down the house — a speaker that can fit in your hand can fill a room with your favorite music. This is even more important when you pair it with your smartphone, and there are lots of smartphone-friendly speakers on sale this Black Friday.

There's a good chance that an iPhone is on one of your Christmas shopping lists, but these things are uber-expensive now, making it hard to justify as a holiday gift — even for yourself. That's what Black Friday is for, though, which can help you save a little bit of cash on an iPhone purchase — or at least, give you something in return to help you get even more holiday presents.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Greetings my fellow hackers.

Back for the second part,

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!
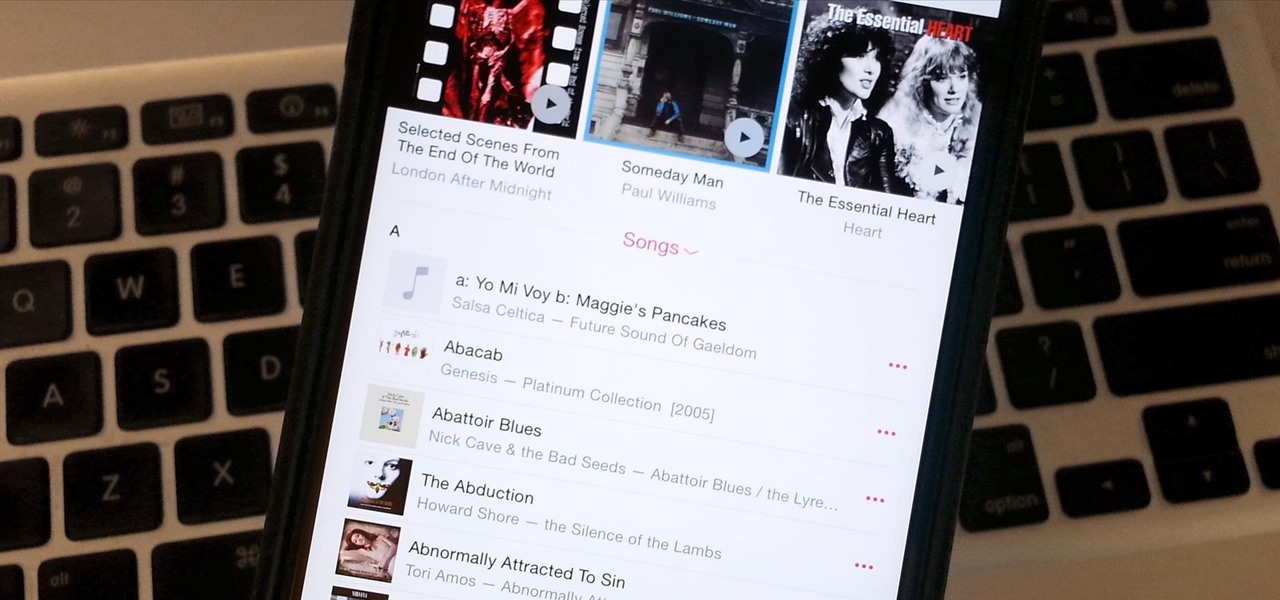
If you updated to iOS 8.4 already to try out the new Apple Music service, there's one important change you need to know about—there's no longer a "Shuffle" option for all songs in your library.

Welcome back, my budding hackers!

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

When it's most important for me to browse the web incognito, I always seem to forget to enable private browsing. If that sounds like you, it's time you stop making that mistake for good. Manually deleting the cache and browser history is a thing of the past, and as it turns out, so is manually switching to incognito mode.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Get rid of your water-wasting sprinkler system— but not entirely! Keep your landscape and garden maintained by converting those sprinklers into eco- and pocket-friendly drip irrigation. In this how-to video, Paula Mohadjer from the Cascade Water Alliance explains how you can easily convert your sprinklers into a drip irrigation system.

Acne sucks - or, more correctly, acne oozes. Which is why it's so important to take care of your skin with oil-reducing, calming products. Most anti-acne medications you can buy are severely drying and irritating, meaning they can cause the adverse effect of making your skin compensate by producing even more oil.

Is your Christmas tree looking a little too "I got everything from Target" generic? Then it's time you learn some decorating tips from interior designer Rebecca Robeson.

Do you play an intensive sport, like soccer or football, that requires you to be able to not only run quickly towards a target area far away, but also to be able to catch a flying ball with precision that far away? Then you'll benefit from the speed and quickness training methods presented in this video.

Imagine… your friend is drinking an ice-cold soda out of his/her styrofaom cup, and everything's fine, until… it's starts leaking everywhere! It could be utterly hilarious, or disastrously evil, depending on who your target is.
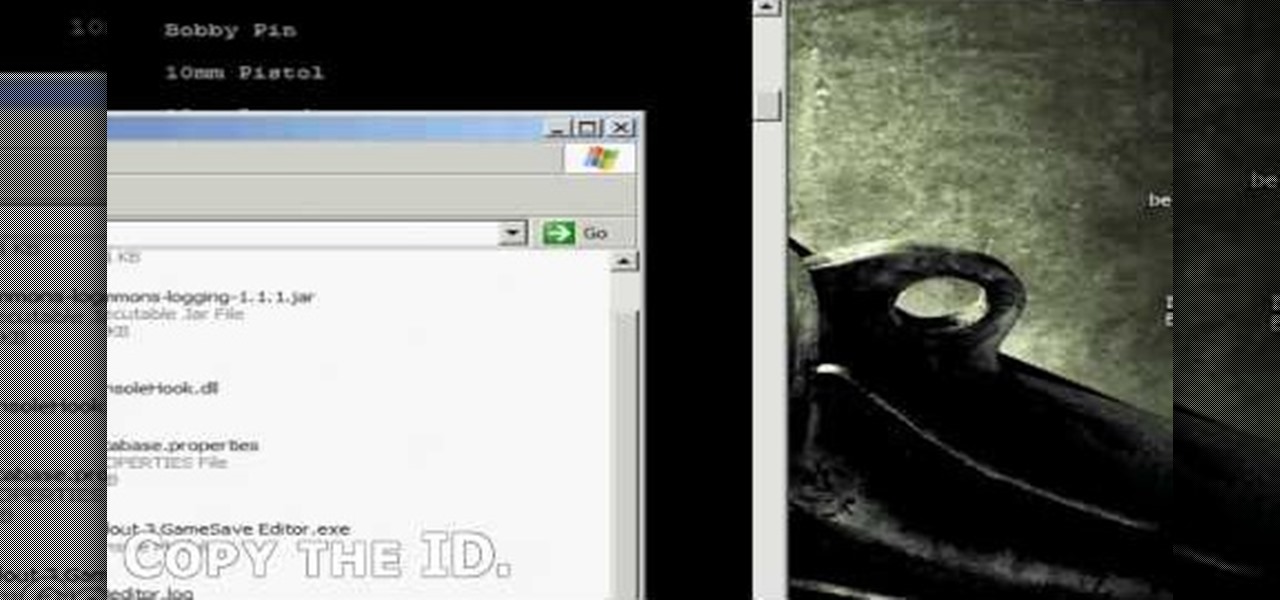
Fallout 3 is one of the most popular and biggest (content-wise) games on the XBox 360, and has thus become a popular target for hackers to mod. This video will show you how to mod your Fallout 3 saved game from the XBox 360 version using some FREE software. This does not include Modio, the popular for-money save game editor that many hackers use. Here are the files:

Four time abs is an excellent exercise for working the lower abdominals and abs workout. Try this out to tone your lower abs, which typical crunches can't get to.

Learn how to create a character rig when animating 3D models in Blender. Specifically, this clip addresses the following topics: Bone creation, splitting and re-parenting. Weighting with bone heat, mirrored weight painting and posed weight painting. IK setup, bone roll, and pole targets. Advanced foot rig with control to pivot off of the heel, toe, ankle or ball and control to lift the toes. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or...

Despite what the name may imply, triceps kickbacks don't involve kicking of any sort. Rather, this tricep-sculpting exercise move involves getting down to a near squat position and bringing a dumbbell forward and back, keeping the shoulders stead and down.

Lock and load! In this Xbox 360 tutorial, you're taken for a nifty little ride by the guys at Achievement Hunter. The main target: an easter egg. And not just any cool easter egg, it's one that puts you, somewhat, in contact with another zombie basher from a different game, Dead Rising. Yes, in this Left 4 Dead 2: The Passing, easter egg hunt, you'll be reading a little message left to you from the man himself, Frank West. So sit back and prepare for the worst. Enjoy!

You must have a certain attitude to appreciate practical jokes and pranks. Your friends (or targets) may not appreciate pranks as much as you, especially messy ones. The messy pranks are the ones that are less likely to provide a laugh from your victims, at least not right away. This ketchup prank is one of those.

Brooke Burke and Autumn Calabrese walk the viewer through a super-effective, targeted butt workout, doable in your living room in only 5 minutes. The first exercise, a "Heel Press", is done from your hands and knees. Keeping your head in line with your spine and your belly button tucked in, press one heel toward the ceiling, then bring it all the way into your chest. Brooke recommends 15-20 reps on each leg. The next exercise, "Crossovers", builds on the Heel Press. After pressing your heel t...