
How To: Train birds with B.F. Skinner's shaping methods
This is footage from B.F. Skinner's psychological tests on shaping behavior.


This is footage from B.F. Skinner's psychological tests on shaping behavior.

Another major retailer is putting all its chips in on the relentless rise of selfie culture. Sally Beauty is rolling out kiosks to try-on "some of its best" hair dyes in 500 of its stores throughout the US. The in-store augmented reality-powered kiosks invite you to view yourself on video, overlay a punky (or otherwise) hair color, and snap a selfie on the screen to share your #glowup with friends.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

The era of AT&T and Magic Leap has quietly entered a new phase that ramps up the mainstreaming of the cutting edge augmented reality device.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

If you're looking into buying shoes from DSW on Black Friday, then you can save an extra 20% — but only if you smile more.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

After parting ways with Papa John's, the National Football League has drafted Pizza Hut as its official pizza purveyor, and the company has hit the field with an augmented reality game to entertain hungry football fans.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.
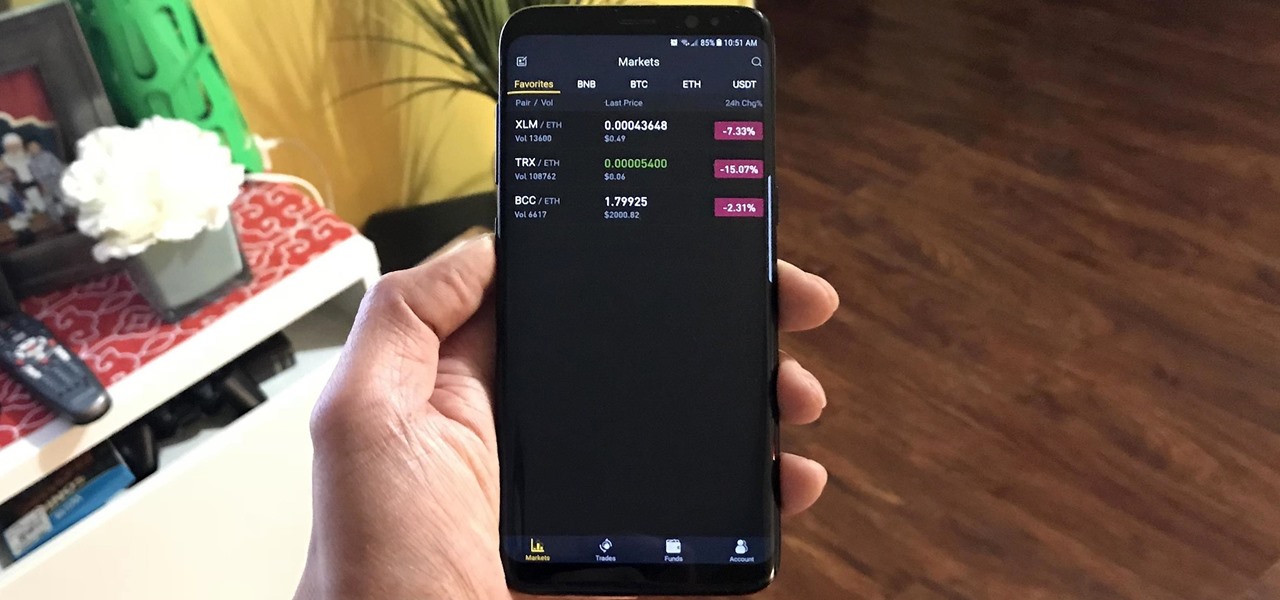
With the sheer number of alt-coins that you can buy and sell on Binance — Ripple (XRP), Stellar (XLM), and NEO to name a few — keeping track of coins you're interested in is a hassle. But with the tap of a button, you can mark trades and alt-coins that are on your radar for quick access on your Binance account.

Android's share intents system is great in theory, but the execution can sometimes be frustrating. When you tap the "Share" button next to a link, app, or file, you see a list of apps you can share that item with. But it seems like every time you use this function, the list of apps is in a different order — especially when it comes to the Direct Share targets at the top.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Snapchat has broken new ground in its augmented reality advertising efforts, as BMW has opted to show off its new X2 model in AR with the Augmented Trial Lens.

The advent of ARKit and ARCore has strengthened the demand for development tools to build augmented reality experiences for compatible iPhones, iPads, and Android devices.

Modern warfare takes on a more literal translation with the advent of new augmented reality displays revealed recently by the US Army to improve soldiers' situational awareness on the battlefield.

My message to Russian hackers is this: LEAVE BRITNEY ALONE! Russian hacking collective Turla has been targeting governments and military operations in the United States, Europe, Asia, and the Middle East for the past decade. Now, it appears that the group is targeting everyday citizens — specifically Britney Spears fans.

Tim Cook claimed 85% of new iPhone buyers are switchers from Android back in 2015. Now, after financial analysts noted a drop in the company's stock prices, Apple has unleashed a series of ad campaigns directly targeting the users it needs to win over. That's you, Android lovers.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

When Facebook purchased WhatsApp for $19.3 billion back in 2014, we all knew this was coming—it just took longer than we thought. But starting today, the data mining became official, and now, information from your favorite messaging app is no longer out of reach for the world's biggest social media site.

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.
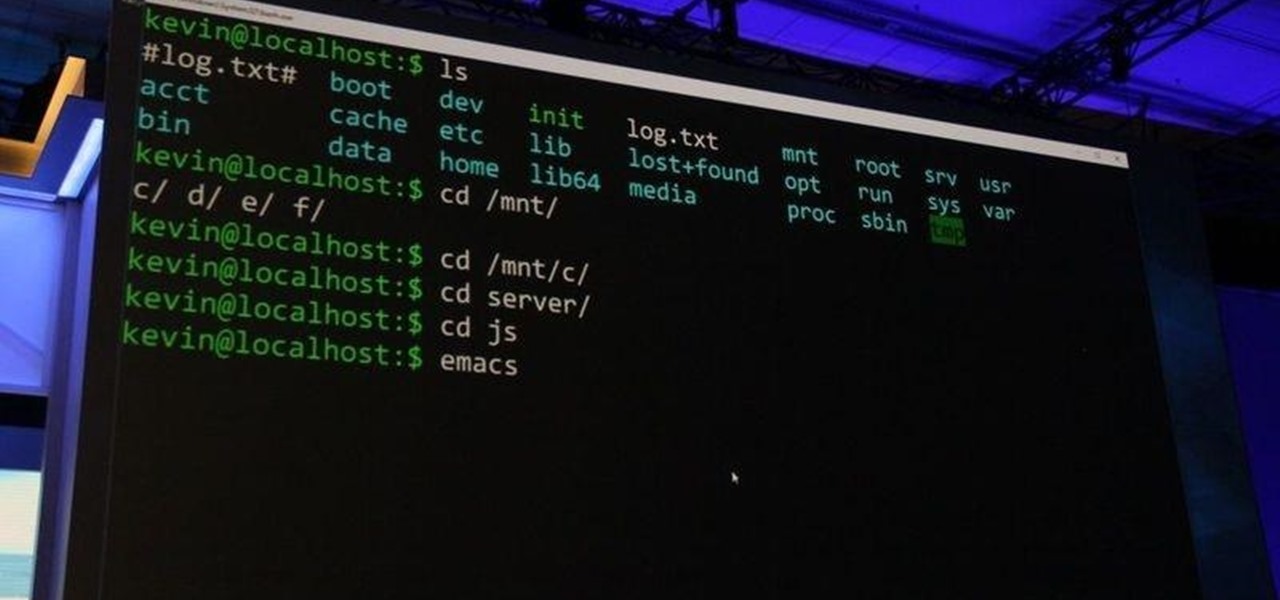
As most of you know, I am a strong advocate for using Linux for hacking. In fact, I would go so far as to say that you cannot be a hacker without knowing Linux well. I laid out various reasons for this in my "Why Every Hacker Should Know & Use Linux" article, and I even have a lengthy, continuing series on Linux Basics to help those new to Linux master it.

MagicTree is often the go-to tool for data collection and reporting for many pentesters. It organizes data in nodes in a tree-structure which is very efficient at managing host and network data. Reports can be completely customized to meet the user's needs. Also, MagicTree allows you to import XML data and has XSLT transforms for Nessus, Nmap, OpenVas, Burp, Nikto. MagicTree comes pre-installed in Kali.

Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

If you're the de facto tech support person in your family or circle of friends, you know how frustrating it can be to have to hold someone's hand and walk them through every troubleshooting step. Luckily, several options now exist for you to remotely access a Mac or Windows PC, which effectively skips the middle man and lets you get straight to fixing the issue yourself.
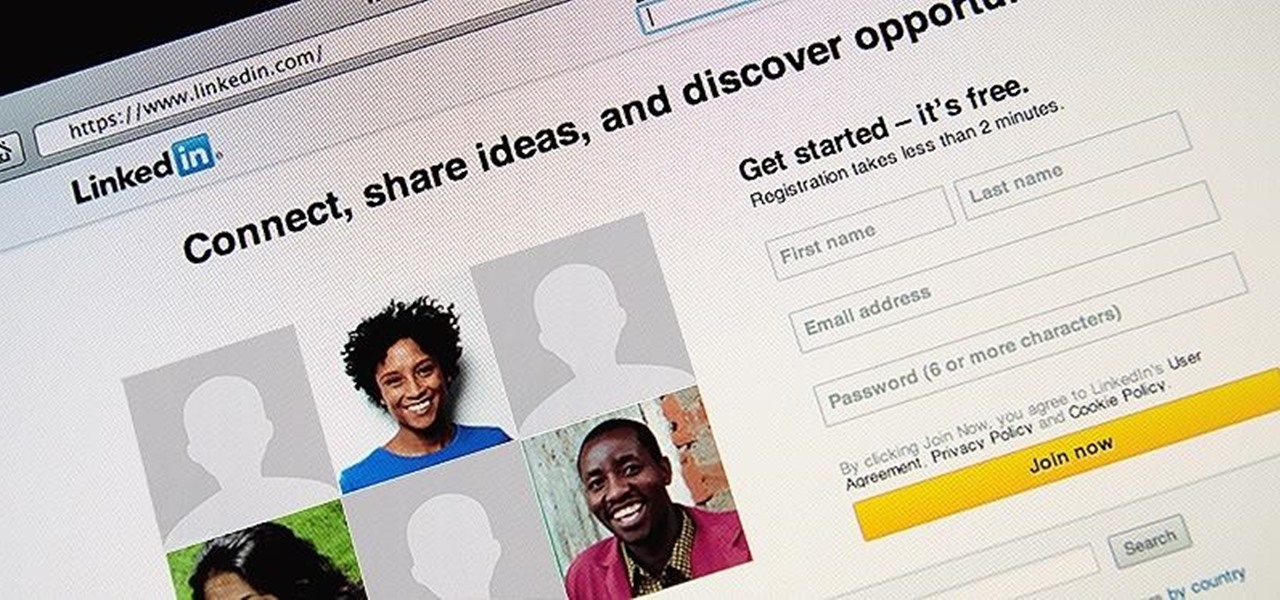
Log in to your LinkedIn profile, and you'll immediately be prompted to check out who's peeked at your profile. With one click, you can discover how many recruiters, companies, and random people have viewed your online resume.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

Skype is a great way to stay in contact with friends and family over the internet, and people tend to share a lot in their chats, so why not try and find a way to hack it! Once a Skype account is hacked, you can view all conversations within the last three months, see how long each video call was, and even access files that were shared through chat.
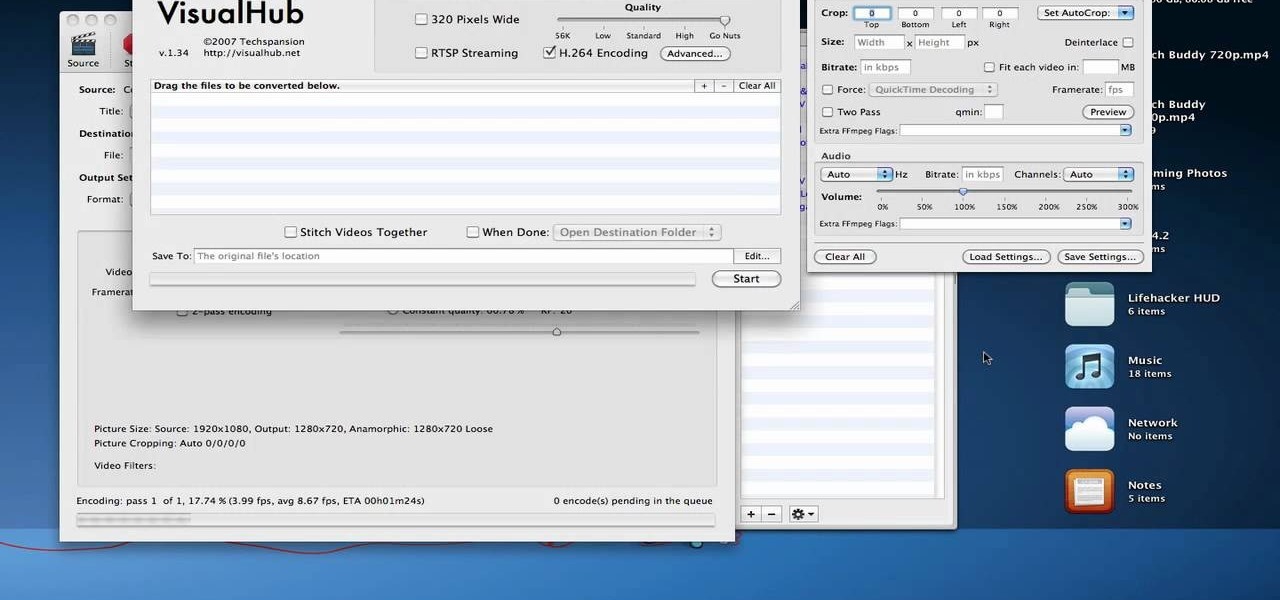
Apple recently released iOS 4.2 for all devices— iPad, iPhone and iPod Touch— and one of the best features is AirPlay, which lets you stream video directly to AppleTVs. There's only one problem— it will only stream video that meet's Apple's specifications.
You can capture almost any enemy in Dwarf Fortress, and there are all sorts of creative ways of dealing with them once you have them. This video will show you some cool ways of killing and otherwise killing your captives.
Late in the Dwarf Fortress game building machinery can allow you to pump water around the map and power mill stones to make more advanced food. This video will show you how to build and use machines safely, without destroying your fortress and the lives of your dwarves.
The siege is on! This video will show you how to defend your fortress against a human siege and also explain the most-used and best traps in Dwarf Fortress. The second part is not a how-to, but shows the defense against a human siege playing out so you can understand it better.

Box Seats! Put the art back in party furniture with collapsible tables and stools.
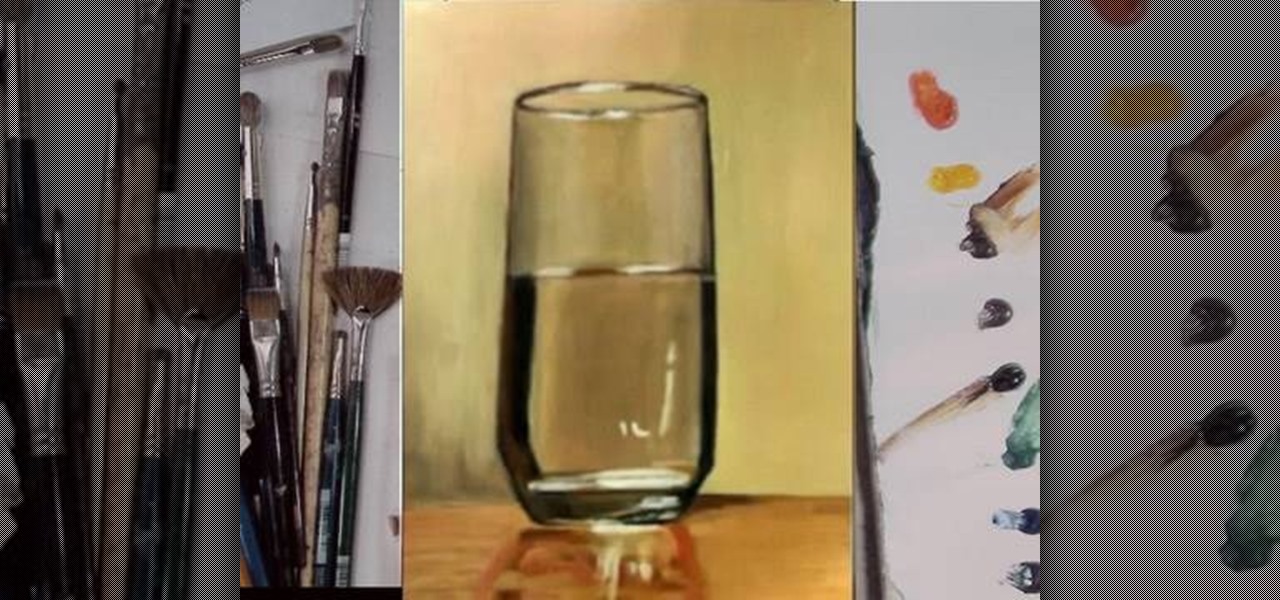
Watch this fine art video tutorial to learn how to Draw a glass of water with illustration markers, colored pencils & oil paint.

Want to hand out lollipops to your kid's class for Valentine's Day? Then don't just phone it in by scouring the shelves at Target the night before for some Dora the Explorer paper valentines that you'll tape to the lollipops.

After you purchase your first car in Gran Turismo 5 on the PlayStation 3, you'll unlock the National B License Tests. The first one (B-1) is a stopping challenge, and if you want to learn how to get the gold trophy, this video gives a perfect example of how to get it.
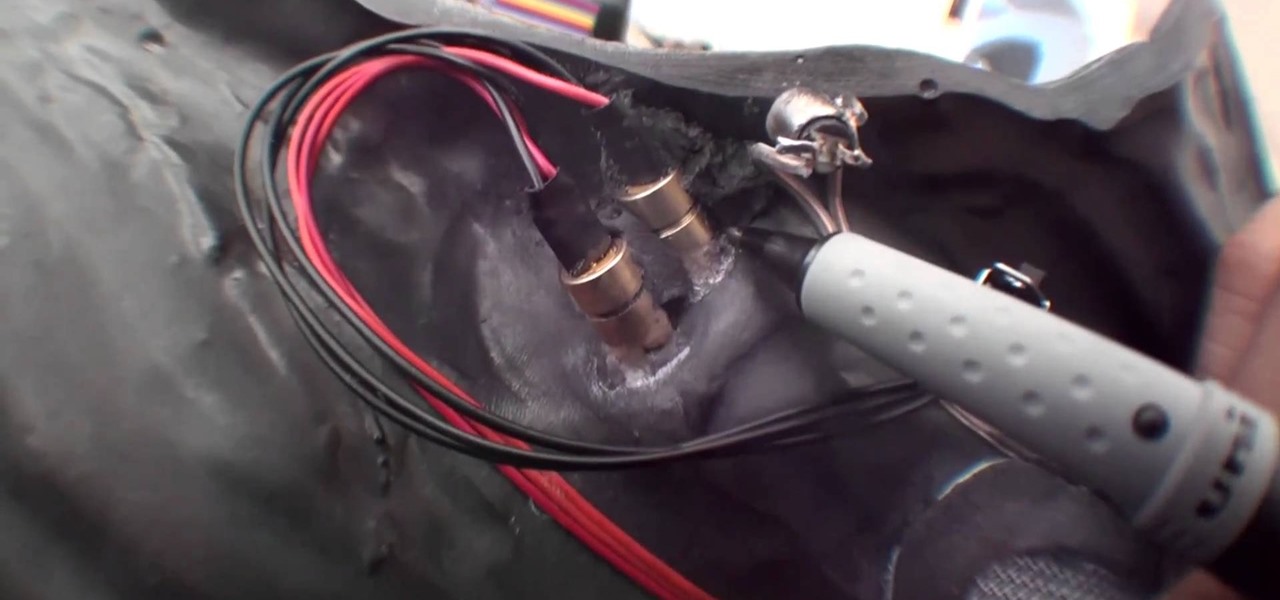
Going for a Predator outfit for Halloween or as a cameo in your film, you want to try to get as close to the real thing as possible. In this video you will learn how to perfectly align LED lights to create the targeting lights that the predator uses for its canon with a quick tutorial!

Christina Hendricks, who plays Joan Holloway on "Mad Men," recently rendered a male reporter speechless during a live interview. And honestly we're not surprised.

Back to school is the best time of the year to flaunt new clothing and accessories you scored during the summer. But since so many of us shop at the same places these days (come on, when was the last time you visited Target?), it's very likely you'll end up with a dress or necklace that someone else already has.

A bedbug is a small brownish, blood-sucking insect. Usually, infestation brings emotional trauma. So, the problem is greater than the physical problem, since the bugs bite at night, while the victim sleeps. Often, the bites are mistaken for dermatological conditions, until the bugs are found. Typically, bedbugs are going to be within 10-15 feet of your bed. They will usually be along the rim. They will also be underneath the box spring. There will be in the nightstands. There will also be blo...