PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

Black Friday is fast approaching, and just like every other day-after-Thanksgiving, there will be too many tech deals you won't want to pass up. If you've been saving up all year just for this sometimes-chaotic shopping holiday, we'll help you figure out the best tech sales to take advantage of and when, whether it's Black Thursday, Black Friday, or Black Friday weekend.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Antibiotics are one of our main weapons against infections. The problem is that many bacteria are becoming resistant to most of the antibiotics we use to treat them, and those 'superbugs' have created an urgent threat to our global health. A research group found a new way to hit a well known bacterial target and have developed a drug to hit it.

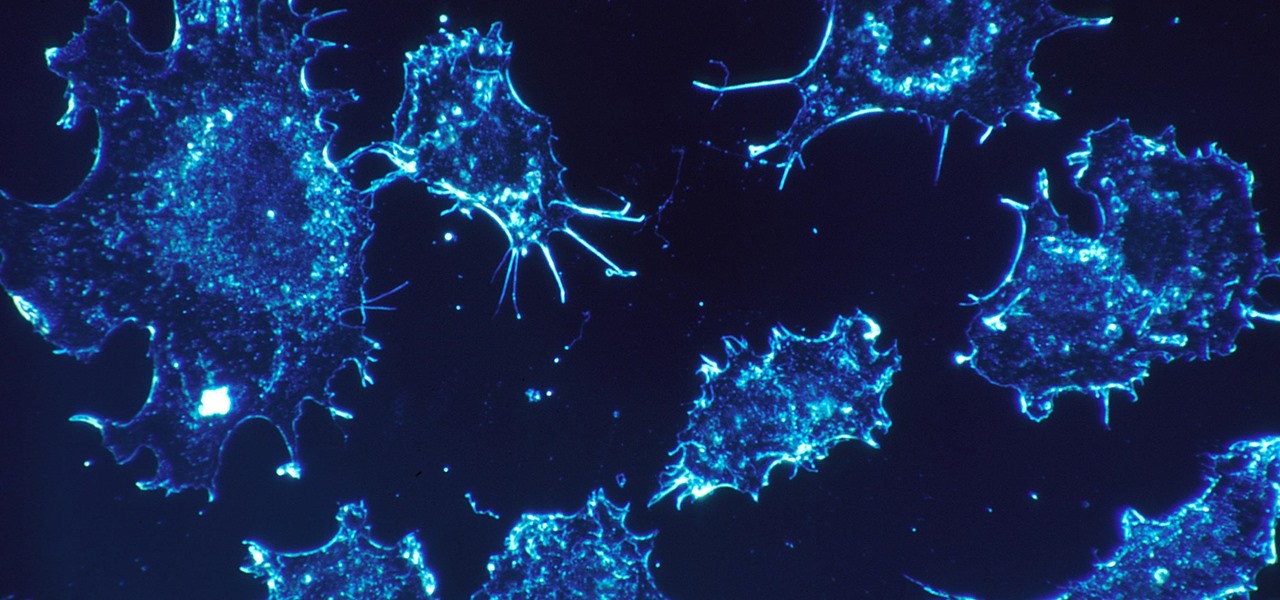
As our cells age, they eventually mature and die. As they die, they alert nearby cells to grow and multiply to replace them. Using a special imaging process that combines video and microscopy, scientists have observed the cellular communication between dying and neighboring cells for the first time, and think they may be able to use their new-found information against cancer cells, whose damaged genomes let them escape the normal dying process.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Super Mario Run was released for iOS on December 15, 2016. Even though it debuted as a "free" app, almost all of the playable content was hidden behind a ridiculous $10 unlocking package. Despite coming with such a hefty price tag and receiving a two-star rating on the day of its release for iOS, Android users are still very much interested in giving this game a whirl.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Video: . This Video will Show you how to Season and Clean

Here is a video that shows 90 seconds that could save your life. How to actually MAKE A FIRE with a lens, rather than just burning a hole in a leaf. (Or frying ants, which seems to be the other thing that kids like to do with magnifying glasses.)

90 seconds that could save your life. How to actually MAKE A FIRE with a lens, rather than just burning a hole in a leaf. (Or frying ants, which seems to be the other thing that kids like to do with magnifying glasses.) By forming your target material into an efficient ball, you will be able to start a fire even with very small lenses. Like less than an inch across small. The finer the individual fibres, and the more densely they are packed, the more effective is your ball of smigtin (smoulde...

Sony is ready to get into the micro-console gaming fight, with its PlayStation TV set to debut this fall.

Last year, Todd Blatt ran a Kickstarter campaign to make 3D-printed accessories for Google Glass, and has turned it into a company: GlassKap.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

White is the traditional American wedding gown color, so why not match your makeup with your dress? Many brides go with a natural, flatteringly neutral makeup look when walking down the aisle, but silvery white eyeshadow is a steely yet gorgeous alternative.

This video demonstrates how to change the color of hair, dress, car or any thing of your choice using photoshop. This is really simple. Select the photo in which you need to change the color. Create a new transparent layer. Click on the brush tool and select a brush type with the right size required. For hair, you could use a brush with a fuzzy edge while sharp edges for clothes and car. Select the white color in the task bar. Click and drag carefully along the edges and fill in the area wher...

Paul demonstrates to viewers how to properly set up a turntable. Each turntable has the same basic parts, so this tutorial should work for most users. There are several components: the platter is the part that spins and it has a slip mat on top. The tone arm is to the right and it has a head shell and stylus cartridge (needle) mounted on the end. The queueing lever is at the base of the tone arm and it raises and lowers the tone arm base. There is also a VTA (Vertical Tracking Angle) adjustme...

The perfect way to avoid boredom at work or in the classroom is with a good old-fashioned prank, and this one is for tech-minded. In the video below, you'll see how to change your coworker's (or classmate's) computer screen to be display upside-down, which will totally freak them out when they return from lunch or the restroom. The best part is watching them try to revert it back to normal!

Have a date and looking to impress? First dates can be nerve racking and totally awkward. Watch this video on how to impress a man on the first date and stay calm.

Having problems with your anti-virus software on Windows? Learn how to remove the fake virus protector Personal Antivirus! Personal Anti-Virus is NOT a legitimate anit-virus software and will use spyware to steal info from your computer. Personal Anti-Virus is hard to get rid of and is totally annoying. To get rid of it, you don't have to download anything.

Check out this 6 coin puzzle bar trick from Revision3, Scam School and Brian Brushwood. Brian introduces a new diabolical coin puzzle to stump your friends.

Brian Brushwood and Scam School give you another way to score free booze at the bar. Memorize a few configs and you'll hold the key to another unbeatable game and loads of free drinks!

Do you wish there was a way to make more organic objects in Second Life? Are you an online Flash programmer looking to make your Papervision3D projects run faster? Do you like model rockets? If your answer to any of these questions is yes, then wait until you here about Sculpting Primitives. In this tutorial, Alex goes over the basics of what 'Prims' are and introduces a program called Sculpty Paint, which will help release the Michelangelo trapped inside you.

Group chats in Facebook Messenger can devolve into outright noise pollution as people chit chat randomly and bombard you with distracting notifications. Unfortunately, leaving the group outright alerts everyone inside, so if you want to get out of the thread unnoticed, what exactly can you do?

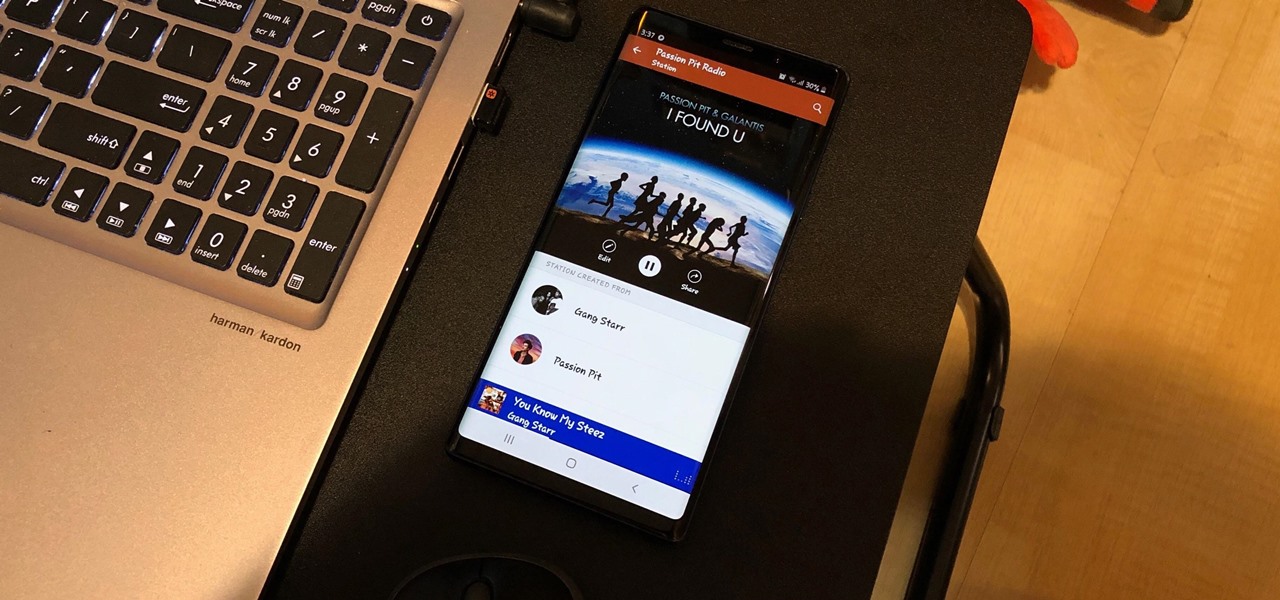
Whether you're out for a drive, commuting to work, or just taking a stroll, listening to your favorite tracks on Pandora takes the legwork out of choosing which songs to play next. After a while, however, you go-to playlist can get repetitive, as the same songs from the same artists seem to play over and over. Luckily, Pandora makes it easy to add variety to your stations in just a few taps.

Cosmetics augmented reality specialist ModiFace appears to be really benefiting from the brand power of L'Oréal, which acquired the company last year.

After getting its start with models of augmented reality planets that serve as targets for augmented reality experiences, AstroReality is diversifying its portfolio by paying tribute to one of the space agencies that made its products possible.

Simulated training can help soldiers and sailors learn how to use their weapons safely, but simulations can sometimes lack the stressful environment of a real firefight.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.