Link shorteners like TinyURL and Bitly are great for Twitter (or anytime you're limited on space), but they're also great for hackers. It's easy to hide a malicious link in an innocent-looking shortened URL, which increases the chances that people will click on it.

As if you needed another reason to lock down your Facebook profile, the company's sketchy new partnership with data mining firm Datalogix is geared towards giving advertisers more information on what you're doing—even when you're not online. It's just not enough that they can target ads based on your preferences, now they want to know how those ads are influencing your buying habits in the real world.

Are you determined to go running every single day? Even during the winter? If the snow and cold can't deter you, you might as well learn how to run safely in the winter months. It's all about how you dress. Dressing warmly is the key to having safe jog. Here are some tips from the members of the morning run club at St. Louis Park Lifetime Fitness.

To make silly putty start by putting four tablespoons of Elmer's Glue into a glass jar. Next you will add two tablespoons of liquid starch into the glass jar with the Elmer's Glue. Use a metal fork to stir up the glue and starch mixture. Stir it until it is thoroughly mixed up. Then take the glue starch mixture out of the jar with the fork and put it onto some aluminum foil that you have laid out on the table. Take the mixture and squish it with your hands. Flatten the mixture out into a patt...
Wouldn't it be great if we could all enjoy the music, photos and movies on our home computers even when we're not home? Some would think it a luxurious feature, but it's totally possible for anyone who has Windows 7 and an internet connection. See how!

Ron the Builder demonstrates how to plaster a wall. Mix the sealant with water to achieve the right proportions and spread evenly over the wall with a paint roller. Once the sealant is dry, you may begin plastering. Combine half a bag of plaster with the appropriate amount of water in a large bucket with an industrial mixer. Mix until the plaster is smooth. Pour the plaster onto a flat board. Using a trowel, scrape some plaster onto your hawk. Then, using a flick of the wrist, quickly scoop s...

Whether you're at a concert or on a road trip, sometimes you need to camp out. Check out this video if you are planning a car trip where you will be camping along the way. Car camping requires plenty of preplanning and patience but will be totally worth it in the end when you have one sweet road trip!

There is a lot of stigma around prenuptial agreements but they can be a good chance to work on difficult issues as a couple and make sure you're on the same page. Prenuptial agreements don't have to be a horrible experience and can give a soon to be married couple some peace of mind.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

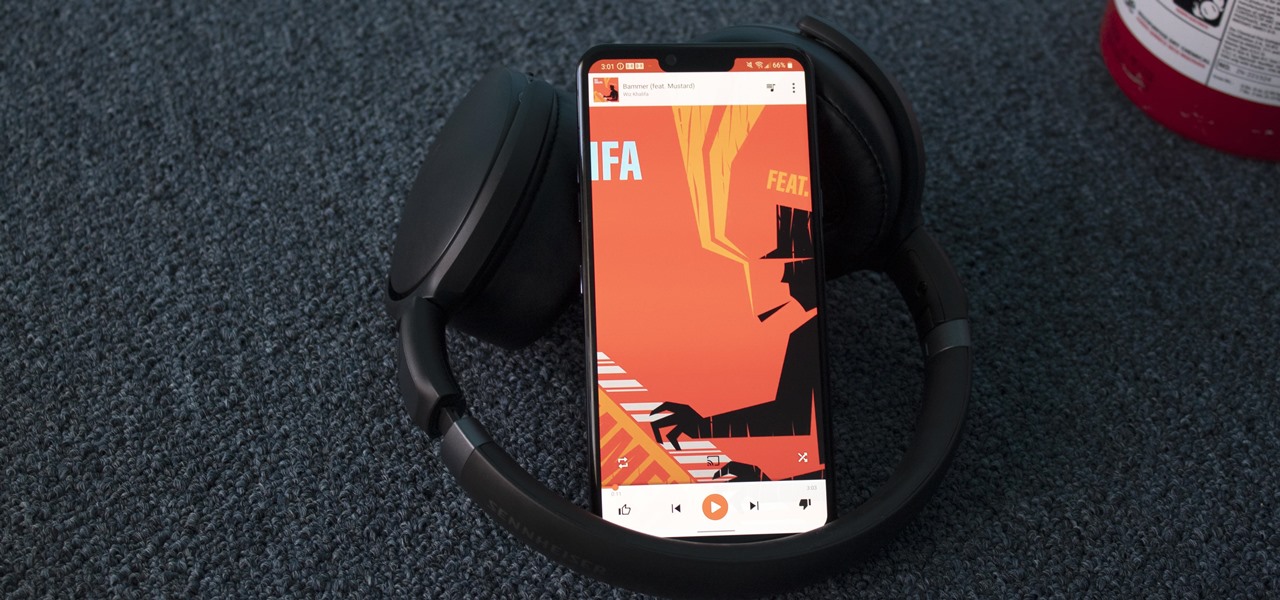
For audiophiles, few smartphones come close to LG flagship devices. With either the latest G series or V series phone, you can be sure you're getting the best audio experience of any smartphone thanks to Quad DACs and headphone jacks. And with some tinkering, you can make this experience even better.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

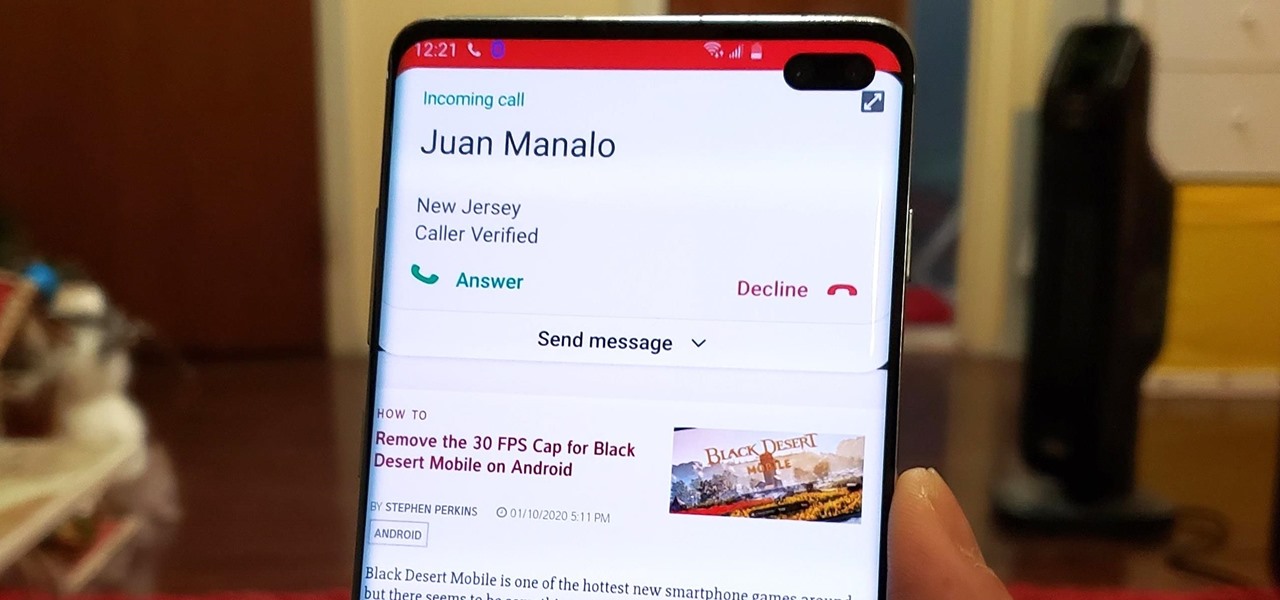
With all the things you can do with your Galaxy, it's easy to forget it's still a phone at heart, and incoming calls that take over your entire screen serve as a rude reminder of this fact. Thankfully, Samsung handsets like the S10 and Note 10 come with a setting built-in that aims to keep these interruptions to a minimum.

iPhones aren't immune to occasional bugs. But starting with the iPhone X, performing a reboot to fix minor issues has gotten a little more tedious. Thankfully, iOS 13 has a hidden option that makes the process a whole lot simpler.

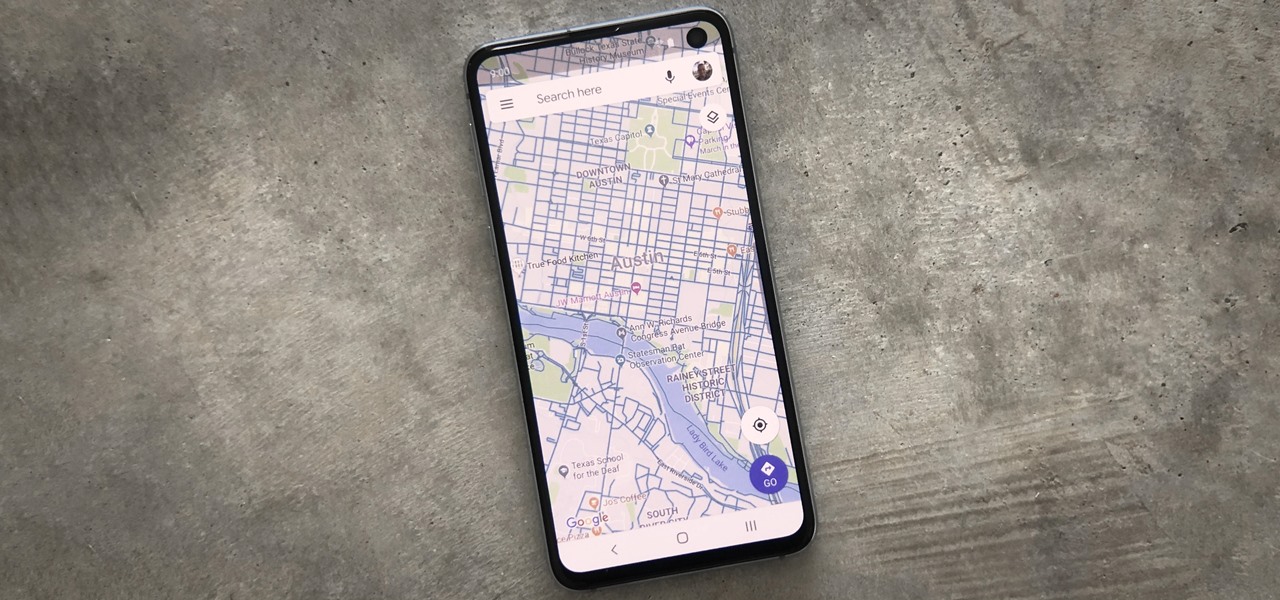
When you're going somewhere for the first time, it's nice to know what the destination will look like. Street View in Google Maps is the perfect tool for that, though it's always been a little awkward to access. But now, Google added a new overlay that will put Street View content literally one tap away at all times.

Apple slowly rolled out its new credit card, Apple Card, throughout August, but announced on Aug. 20 that it's now available to all qualified users in the US. Here's the problem: it's not totally obvious how to apply. Without any notification, directions, or clear settings, how do you even fill out an Apple Card application? Luckily for you, we're here to show exactly how to find it.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

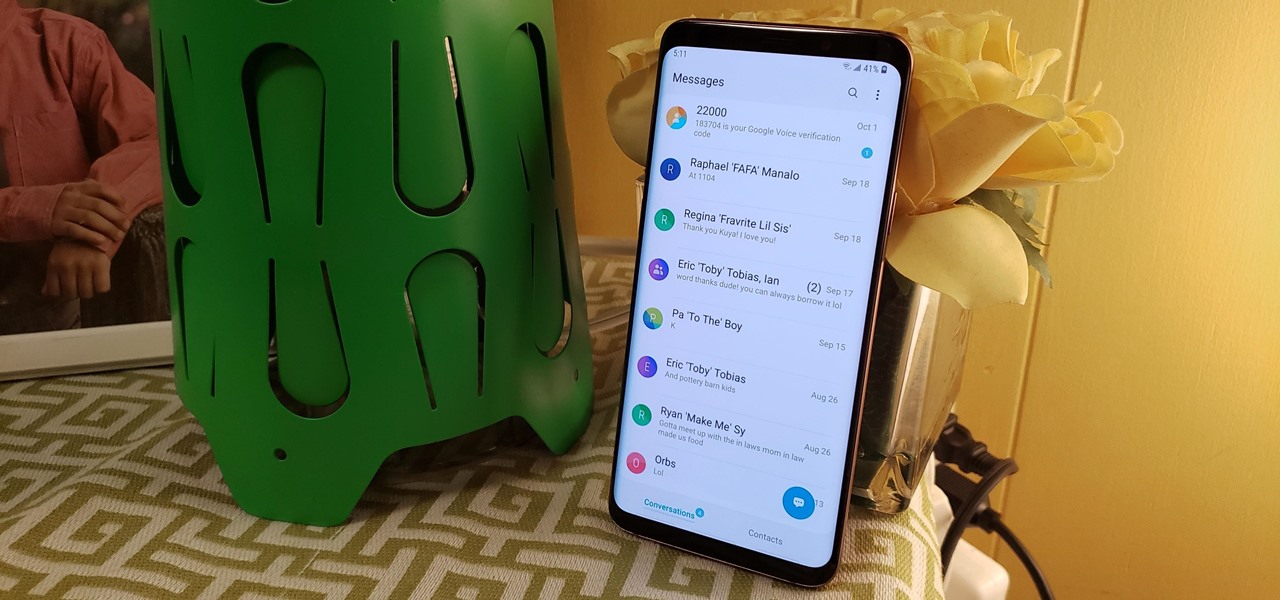
Samsung's version of Android Pie has landed on Galaxy handsets like the Note 9, S9, and S8, though we've known what to expect thanks to leaked beta versions of the software a few months back. The newly dubbed One UI has plenty of new features and improvements, but some of the first you might notice are the visual improvements to the default messaging app.

To give you a truly immersive experience on Infinity Display phones like the Galaxy Note 9, S9, and S8, Samsung added the option to hide the navigation bar when not in use, then easily reveal it with a swipe up gesture for quick access. If you've always found this process a little too cumbersome, Samsung has introduced a nifty feature in One UI that'll make it a lot more intuitive.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

Before Google Chrome entered the scene and subsequently dominated the market, Firefox trailed only Internet Explorer as the most popular web browser. Now, Mozilla has its sights set on a new opportunity to revive its browser for immersive experiences.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

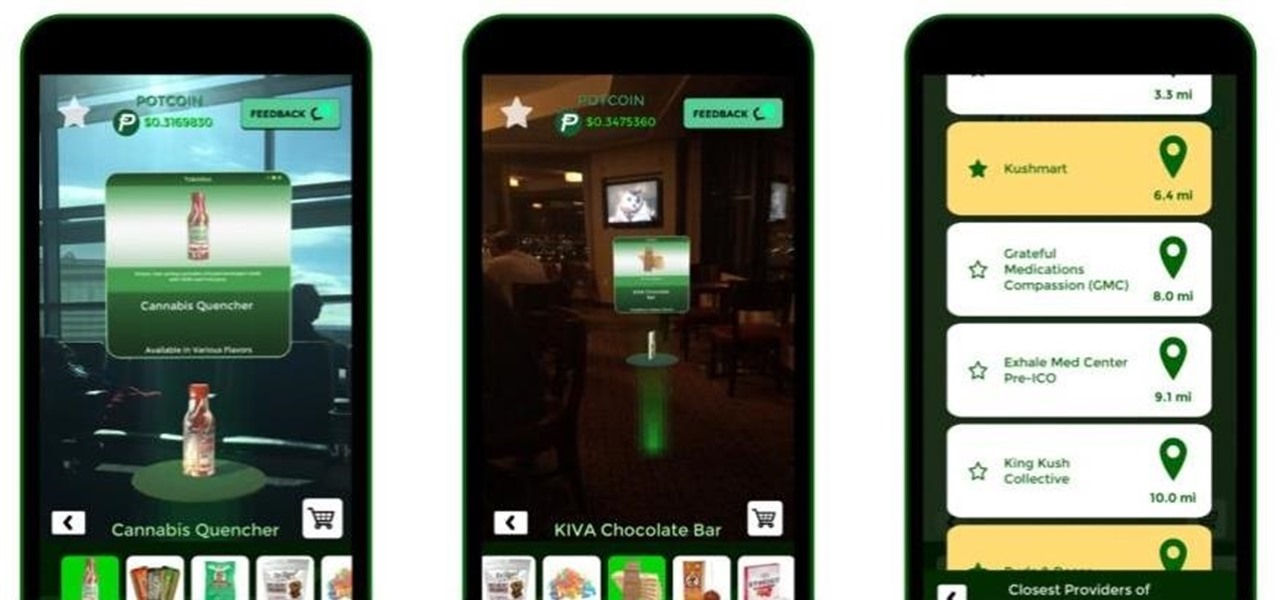
If there's one augmented reality app idea that should have gone up in smoke, it's probably Tokédex, an app that brings cannabis to the world of AR.

Razer just made a big step into the mobile industry by releasing an absolute beast of a smartphone. The gaming-centric Razer Phone tries to provide the best experience for its target audience: Gamers. With that in mind, they created a top-tier device with some of the best specs available on Android. But how does it compare to the current spec champion, the Samsung Galaxy Note 8?

A few months ago, a video went viral of a boy playing Super Mario Bros. in the middle of Central Park using augmented reality and the HoloLens.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

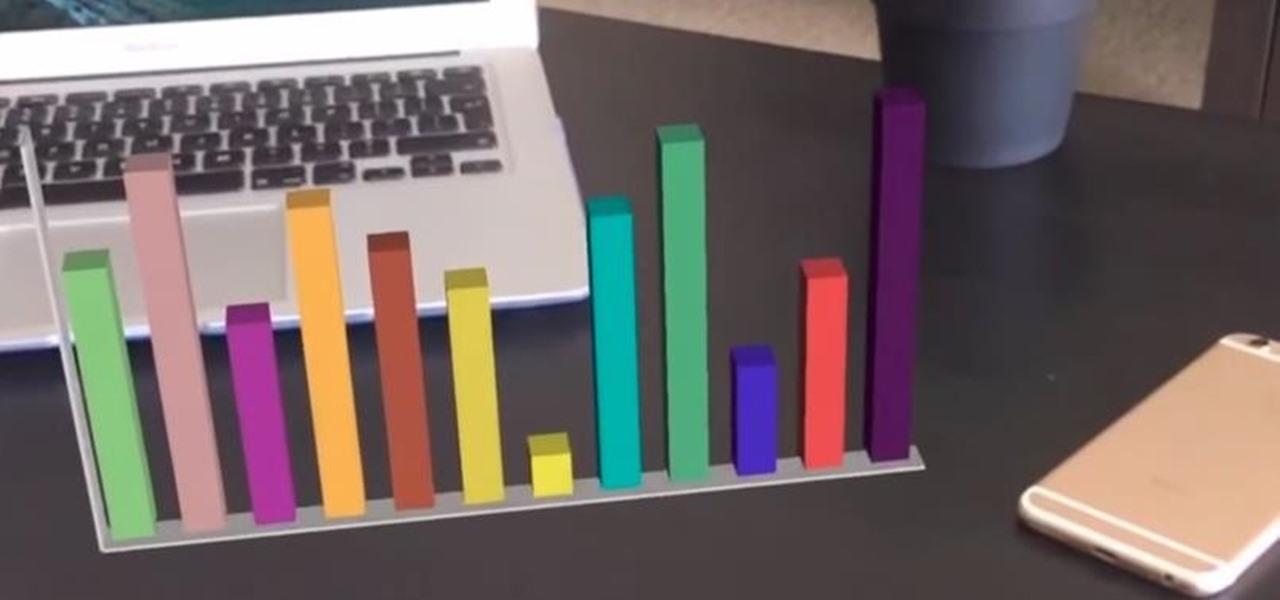
It's certain that the release of Apple's ARKit is going to be game changing for businesses. This demo video was created by YouTube user hdsenevi who used the ARKit to create a simple bar chart. The chart has adjustable settings, allowing the user to make each bar larger or smaller and change their colors. Not only that, but there is an "animate" option.

I've possibly been really out of it for a long time not to have realized that Instagram has a bunch of hidden filters. Clarendon seems to be by number one filter for pics and videos, but maybe that's exactly what I've been doing wrong.

The winter holidays are right around the corner and that can only mean one thing—dessert. Leave it to the French pastry chefs to come up with something totally unique, like this glittery, chocolate Slinky by Amaury Guichon of Jean Philippe Patisserie inside the ARIA Resort and Casino in Las Vegas.

If you're looking to mix up your home décor with something a little bit outside the traditional cabinet box set, check out the amazing Wave cabinet from NYC-based, Chilean designer Sebastian Errazuriz. This revolutionary design will change the way you think about interior decoration and furniture functionality.

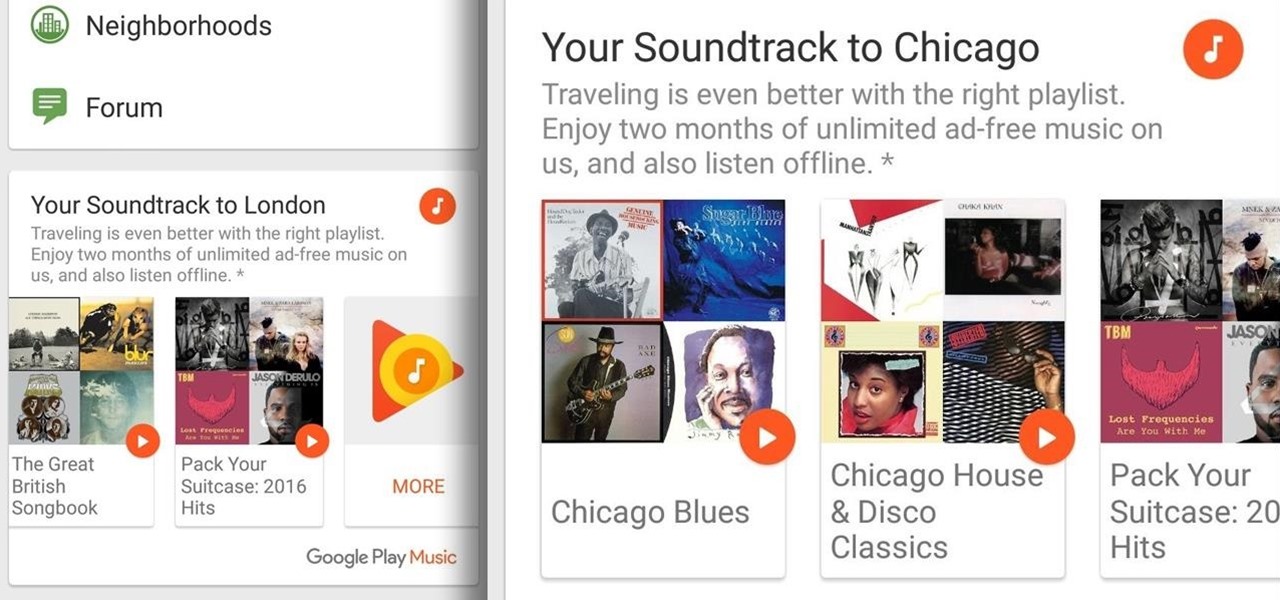
Google Play Music has teamed up with TripAdvisor to make planning your next vacation a little more fun, and they're throwing in a nice deal for good measure.

Samsung's next Galaxy Note smartphone is expected to contain some nifty new additions that the company hopes will give it the long desired edge it has been seeking over Apple. One of those features that might make the difference? An iris scanner, which could make it the first major smartphone on the market to have that technology included.

Yes, the Indian wedding season is just around the corner, and I am going crazy with excitement! Check this super easy Indian Wedding Nails by superwowstyle for Bindi nail designs. And do not worry, this is totally a No Tools Nail Art, and perfectly easy for even those who are not used to doing their nails!

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Sometimes just drinking your alcohol can feel a little dull and boring. Eating your alcohol, however, is always a party.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.