
How To: Paddle a 'Into the Eddy' boof in whitewater kayaking
Shane goes into detail on a specific type of boof in which the paddler comes across the drop with angle and boofs into an eddy.


Shane goes into detail on a specific type of boof in which the paddler comes across the drop with angle and boofs into an eddy.

They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.

Suspect that your bovine (bull, cow) is pregnant. Well, there's only one way to be sure. Put on a plastic glove and insert your hand into the rectum, with your fingers together. See how to find out if your cattle is pregnant with help of this video tutorial.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.
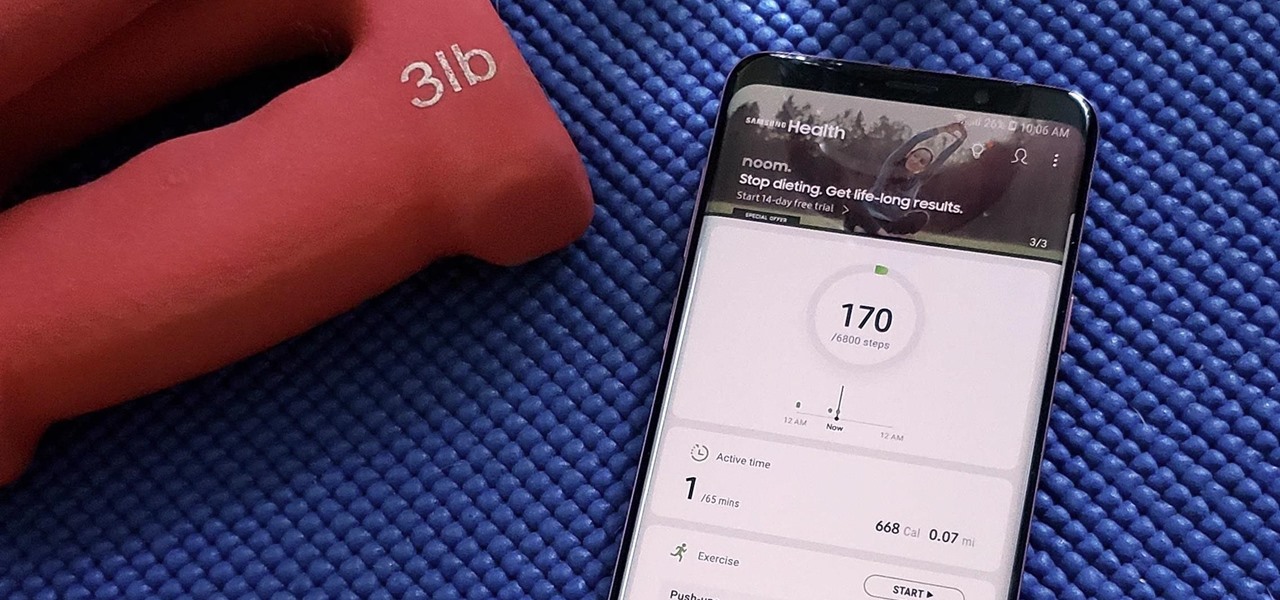
Samsung Health has become one of the most comprehensive wellness apps thanks to features that cover everything from step counting to nutrition logging and symptom diagnosis. But because the app has so much to offer, it can be easy to overlook some smaller, but useful features.

With the macOS stager created and the attacker's system hosting the Empire listener, the malicious AppleScript can be designed and disguised to appear as a legitimate PDF using a few Unicode and icon manipulation tricks.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

I truly don't understand why anyone would pay $10.99 for a case of carbonated water just to feel like a Midwest mom on a diet. Every time I talk about LaCroix, pronounced La-CROY (rhymes with enjoy), it's like I take all the money I spent on my French major and light it on fire.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Want massive, Arnold Schwartzenegger-worthy shoulders? Well, you'll have to work for it, but they're achievable with a few strategic exercises. Building muscle, especially big muscles like your biceps, requires heavy resistance.

Kristen Stewart is a well known tomboy who really doesn't care whether she's wearing Chanel or Target when she's out and about. But the sister knows how to glam it up big time on the red carpet and for photo shoots, where she brings out her hidden sultry, feminine side.

Southwest Yard and Garden featuring John White, Dona Ana County Extension Agent, hosts a 6 minute clip with co-host Master Gardener Valois Pearce both of Dona Ana County, New Mexico host a short web show featuring plants that can easily survive on smaller amounts of water over typical plants. They begin by discussing the full sun Ice Plant, which comes in many species and colors as well as their hardiness, but unfortunately are easy targets for wildlife. They then move onto the Gopher Plant, ...

There comes a time in many tattooed individuals when they want to remove their tattoos. There are a lot of different ways to remove tattoo but they all cause scar. Dr. Neal Schultz explains only laser tattoo removal will not leave a scar and give a cosmetically-superior result. Laser energy is specifically targets the colored pigment of the tattoo so it only damages the colored pigment. It does not damage any of the surrounding skin. When people are treated for tattoos, it can take 8-12 treat...
Ever since Snapchat rebuffed its acquisition attempts, Facebook has morphed Instagram with features from Snapchat, such as stories, chat, and, of course, augmented reality.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

What does mainstream augmented reality look like? I'm not talking about the stuff you see in concept videos and science fiction films. No. What does it really look like?
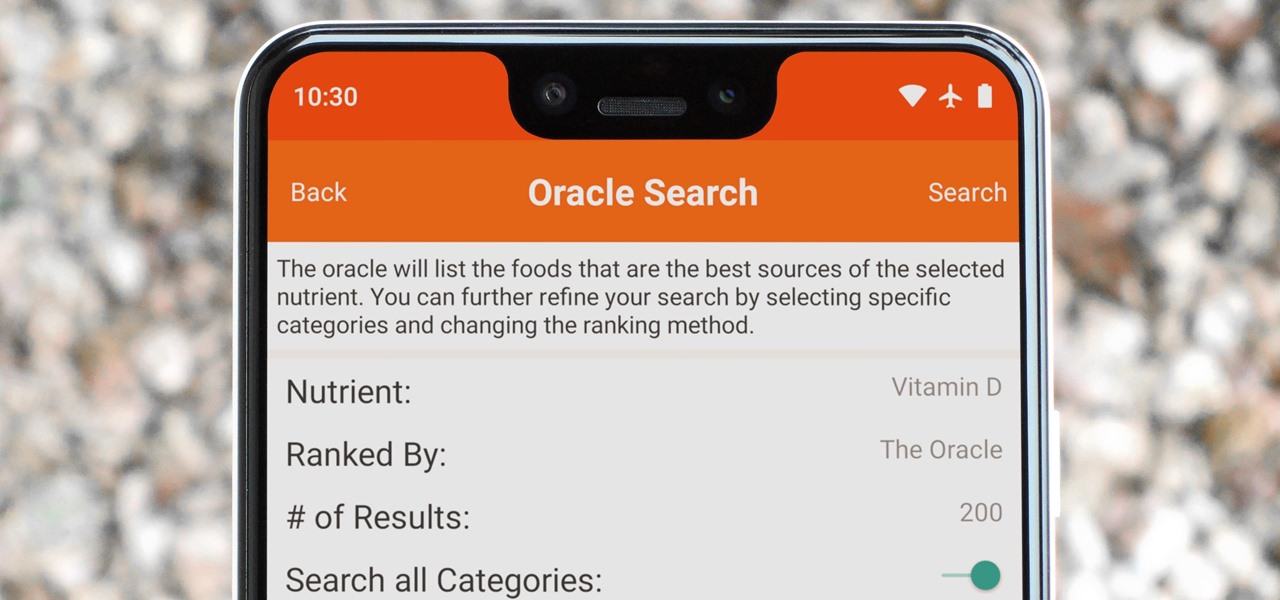
Micronutrients are essential to our health. Unfortunately, many of us aren't getting enough of each nutrient from our diets. It isn't that the food we're eating is bad, but rather we are not eating enough of the right food to get our recommended daily allowance. But with the help of a micronutrient tracker, we can change this.
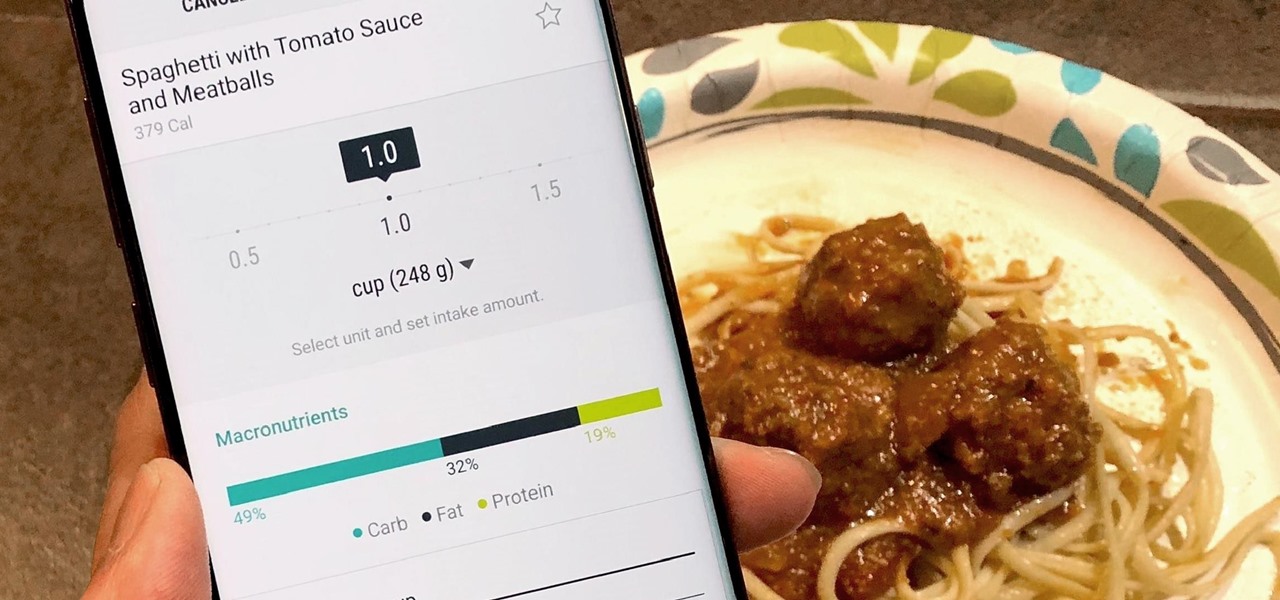
The most essential part of a healthy lifestyle is managing your diet — after all, what would be the point of a daily workout regimen if you were eating junk food? Thankfully, Samsung Health makes it easy to record your calorie and nutrient intake to get a clear picture of your dietary habits and how you can make them better.

Signaling a new direction forward for the company, Magic Leap shook up its executive suite by re-assigning to top leaders to new advisory roles. Meanwhile, a new startup backed by Hollywood executives, tech venture firms, and notable angel investors plans to bring new life to AR for marketing entertainment properties.

The holiday season is upon us, and that means all the big-box stores are competing against each other to offer the best prices on electronics. What was once a 24-hour period of flash deals the day after Thanksgiving has now become a holiday in and of itself — Black Friday is an event you don't want to miss.

If you or someone you're shopping for has a newer iPhone model or an Android smartphone like the Galaxy Note 9 or Pixel 3, they come with wireless charging capabilities. Problem is, they don't come with wireless chargers. But there's no better time to snag one than on Black Friday, and we've found the best deals out there for 2018's holiday season.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

If you've ever been on the receiving end of a threatening phone call, you'll immediately know the value in being able to record phone conversations on your iPhone. Beyond that extreme example, however, recording calls is still an extremely useful feature to have for important conversations like business meetings and verbal agreements, and it's totally doable with a third-party app.

The march towards mainstream adoption of eSIM technology got a massive boost with the arrival of the iPhone XS, XS Max, and XR. We're now one step closer to ditching physical SIM cards altogether. If you're on the fence about this new technology, you may be surprised by the benefits it brings to the table.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.