After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

Last week, augmented reality startup Proxy42 released Father.IO, a multiplayer game that turns any indoor or outdoor space into a laser tag arena.

There are a lot of Android phones out there, and chances are that someone in your life is looking for one this holiday season. Well, there also happens to be a lot of Black Friday deals on Android phones this year. So we've rounded up the best deals taking place on Black Friday weekend to help you save big.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

A deadly type of brain tumor and Zika-related brain damage in developing fetuses are devastating brain conditions that, at first glance, may seem unrelated. However, thanks to new research, their paths seem to cross in a way that could benefit patients. A new study has shown that Zika kills brain cancer stem cells, the kind of cells most resistant to treatment in patients with glioblastoma, a deadly brain tumor diagnosed in about 12,000 people in the US each year.

A vaccine against HIV might prevent the disease that we can't seem to cure. Some HIV patients make antibodies that can take down the virus, much the way a vaccine might. But, scientists haven't been able to provoke that type of response in other people. However, in a process that might work in humans, a group of researchers has successfully generated antibodies in cows that neutralize multiple strains of HIV.

The next time you suffer a cut or abrasion, think twice before you reach for the Neosporin. It's time, and mom, tested — you get a cut, you wash it carefully, then apply some triple-threat antimicrobial ointment. You may or may not slap on a band-aid. We won't cover it here, but so that you know, covering the wound with a sterile dressing or band-aid is a good idea.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Significant strides have been in the race to find antibiotics to treat superbug infections — those caused by bacteria resistant to the antibiotics used to treat them. Now, an international team of scientists has discovered a new antibiotic produced by a microbe found in Italian soil.

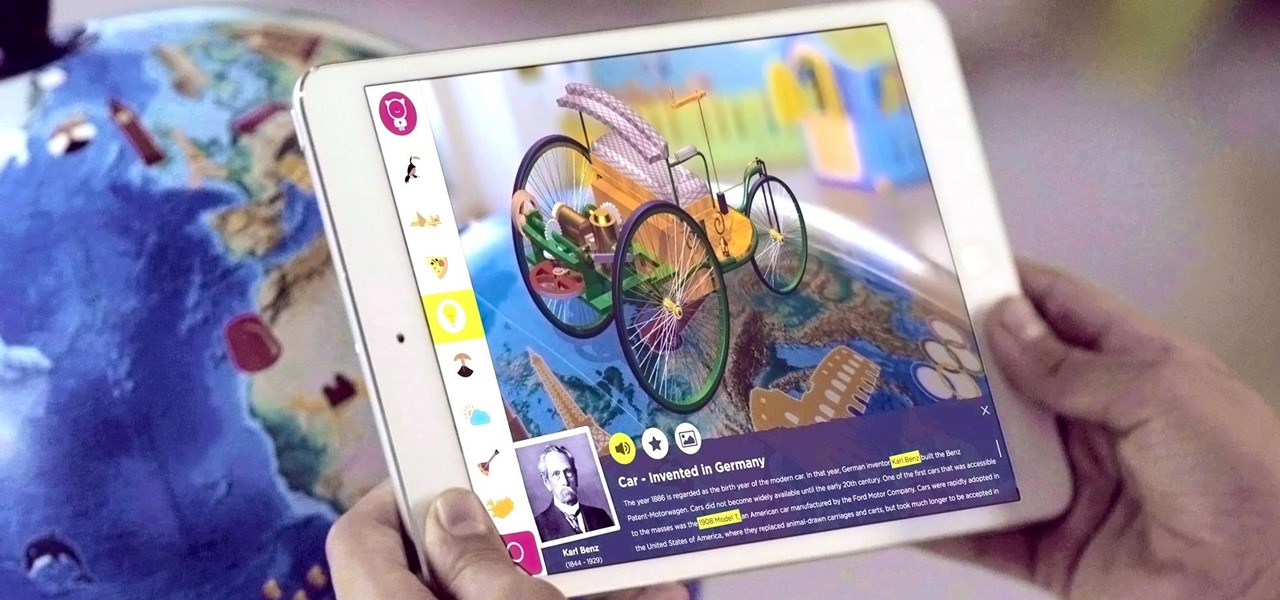
Globes used to be standard in households, usurped in many ways by modern mobile and desktop applications. But one company believes they can upgrade the globe for the 21st century.

As you may have heard, Verizon has jumped on the "giving up users' data to whomever will pay" bandwagon with its new AppFlash spyware app that's all set to be pre-installed on at least one of the Android phones they sell.

Tremendous strides have been made in the treatment and outlook for patients infected with HIV, the human immunodeficiency virus. Treatment with a combination of antiretroviral drugs can keep patients with HIV alive for decades, without symptoms of the infection. The trouble is, if HIV-infected people stop taking their medications, the virus takes over in full force again—because the virus hides out quietly in cells of the immune system, kept in check, but not killed by the treatment.

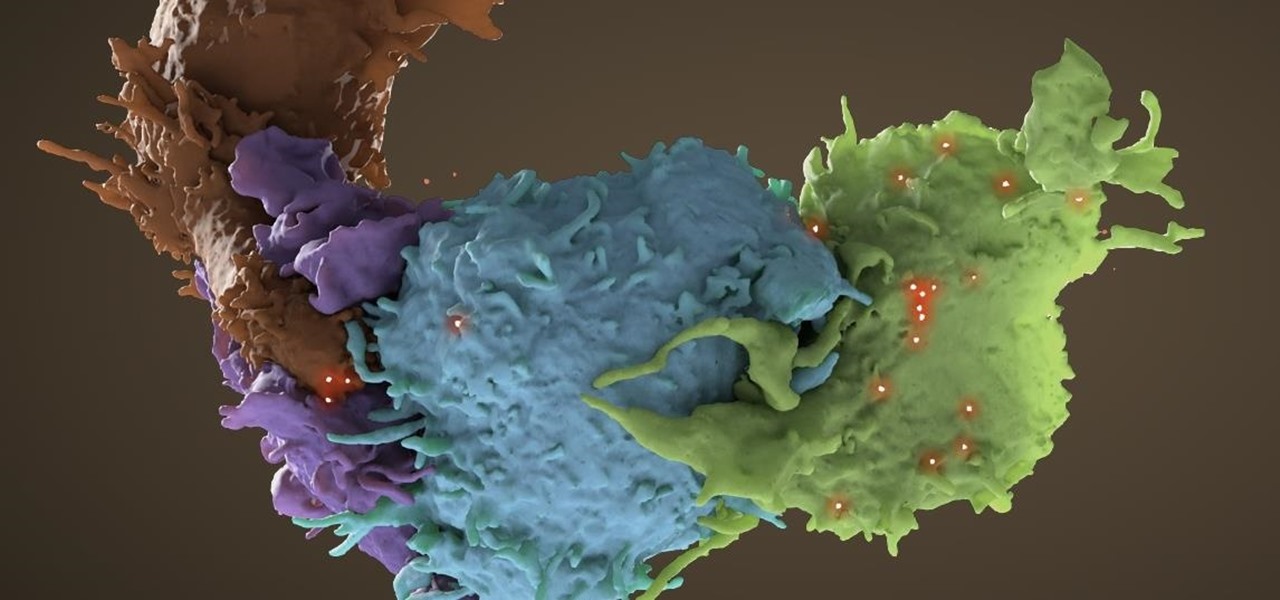
A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.

It hasn't even been eight years since Candida auris was discovered—cultured and identified from the ear canal of a patient in Japan—and now it's drug-resistant, setting up residence in hospitals, killing patients, and wreaking havoc across the globe.

Welcome back to this series on making physical objects come to life on HoloLens with Vuforia. Now that we've set up Vuforia and readied our ImageTarget and camera system, we can see our work come to life. Because in the end, is that not one of the main driving forces when developing—that Frankenstein-like sensation of bringing something to life that was not there before?

The story of Helicobacter pylori is a real testament to the tenacity of medical researchers to prove their hypothesis. It took decades before the scientific world would accept that the bacteria H. pylori caused ulcers.

Findings from a mouse study suggest that the Zika virus infection may have serious reproductive consequences for men.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Halloween is only a few short weeks away, and most people are scrambling to get their costumes together before the big night. The secret to a great getup is all in the details, and including your pet in the fun can be exactly what you need to take your costume to the next level.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

In this how-to video, you will learn how to make Cobra-style paper airplane. All you need is a regular piece of paper. This style is useful for hitting targets or flying straight. Fold the paper in half vertically and unfold. Take the top corner of the paper and fold it to the edge of the middle crease. Repeat with the other corner. Take the tip of the center and fold it to the horizontal line created by the folded corners. Make sure you make tight folds. Open it up and make a fold horizontal...

See the angled edge of the blade? This is the bevel angle. Match this to the face of the whetstone. For a clever-like tool like a machete, this should be at a high angle--15 to 25 degrees.

Make sure the bike is properly fit to the child. She should just be able to stand over the top bar of the frame without touching.

Ladies, it seems to be the trend to wear boyfriend cuts in clothes so here’s a video that will show you how to create a creative super cute and girly top using a guys shirt and tighty-whities. You can wear guy clothing and still look very feminine.