
How To: Sculpt your shoulders with medicine ball scoop tosses
Learn how to do medicine ball scoop tosses. Presented by Real Jock Gay Fitness Health & Life. Benefits


Learn how to do medicine ball scoop tosses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do seated arnold presses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do dumbbell lateral to front raises. Presented by Real Jock Gay Fitness Health & Life. Benefits
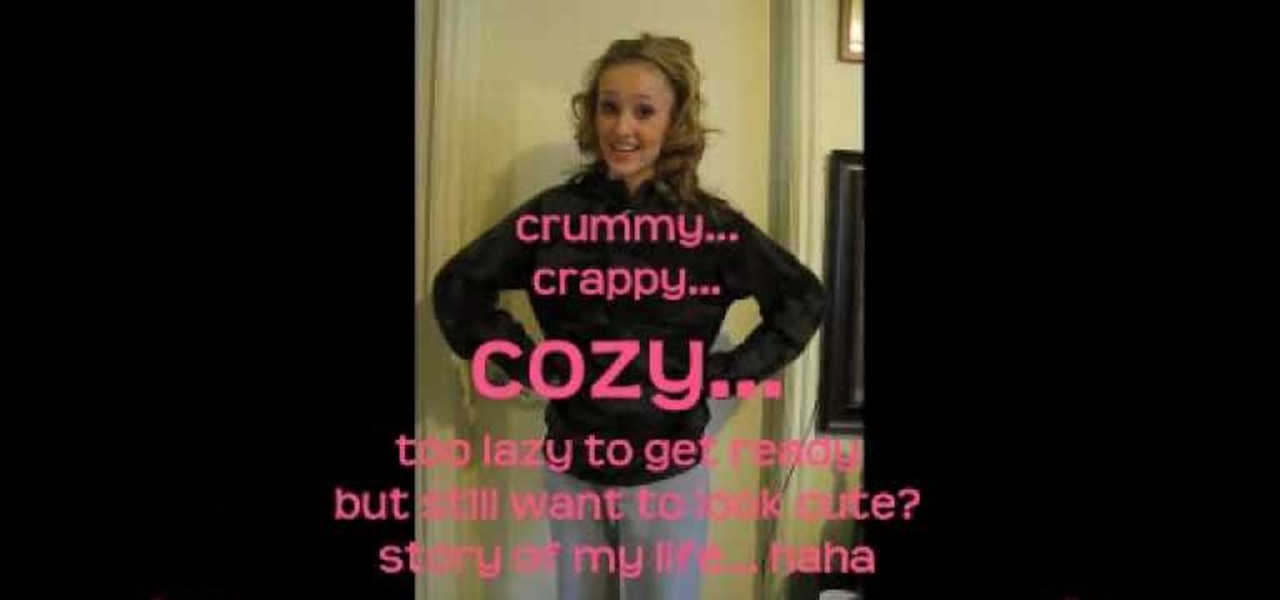
Track suits and Uggs are the way to go if you're feeling lazy, and just want to stay comfortable. But don't give up on looking cute at the same time, because it's totally possible. Watch these tips for feeling crummy and crappy, but looking cozy and cute. You don't even have to style you hair! With just a few changes, you'll go from grubby to cute and trendy.

Apple iPhone's are the world's best electronic wonder, as of today. The whole world is totally entranced by this cellular devices, but the battery life in them can be a bit annoying. If you're iPhone battery has been dying rapidly after each use, there's one thing you could try to maximize your battery life. Lower the brightness to its minimum level to help it last longer. Eureka!

If your into anime and manga, and even cosplay, then you probably have tons of homemade wigs laying around.

While Snapchat is no stranger to location-based AR scavenger hunts, the app's new world-facing game adds some environmental understanding to the mix.

Silicon Valley-based startup 8th Wall has spent much of the last few years building a reputation for enabling AR experiences that are platform agnostic via web browsers and mobile apps. Now, 8th Wall is promising to give developers the freedom to build and host AR experiences from anywhere via a simple web browser.

Viewing and reading content on websites is inherently harder to do on an iPhone due to the relatively small display. Even if you have an iPhone XS Max or 11 Pro Max, you'll probably struggle sometimes to read through tiny text while browsing online. Thanks to a feature found within Safari's view menu in iOS 13, your eyes can rest a little easier.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.
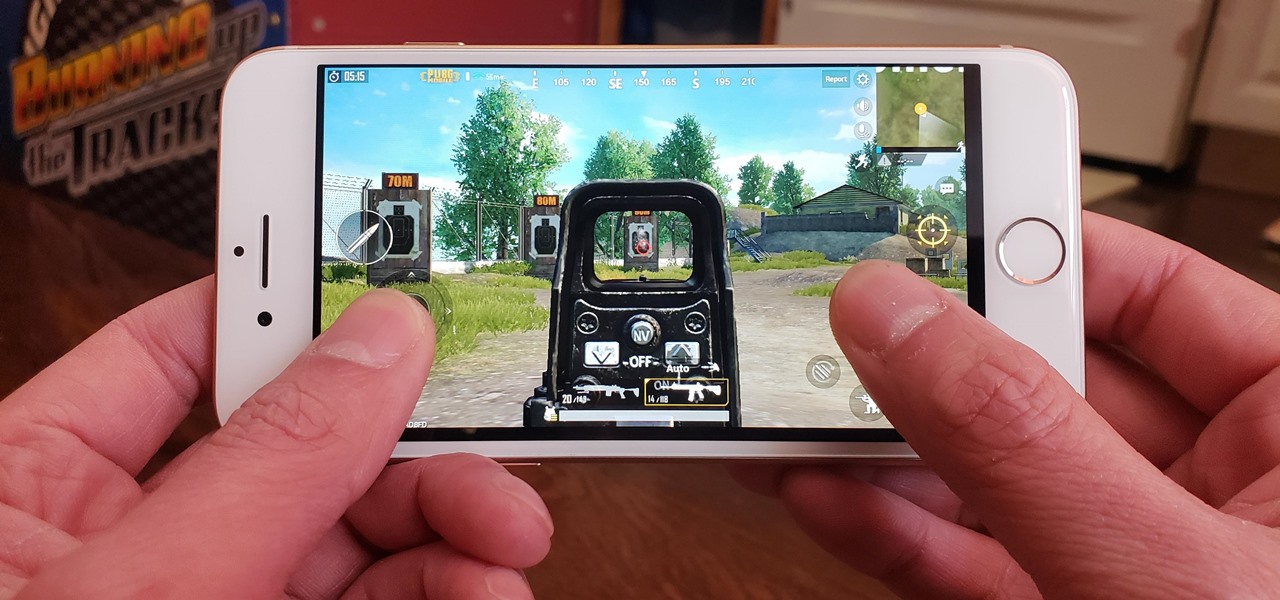
PUBG is continually getting better and more intuitive with each update, and version 0.4.0 is no exception. Besides a new training map to help you practice and a faster-paced arcade mode for on-the-go gaming, the newest version of PUBG now includes a feature that exclusively caters to iPhones from the 6S on up.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

With a new installment of the Saw horror series opening in theaters nationwide this weekend, Lionsgate is betting its ad dollars on immersive advertising to sell tickets.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.
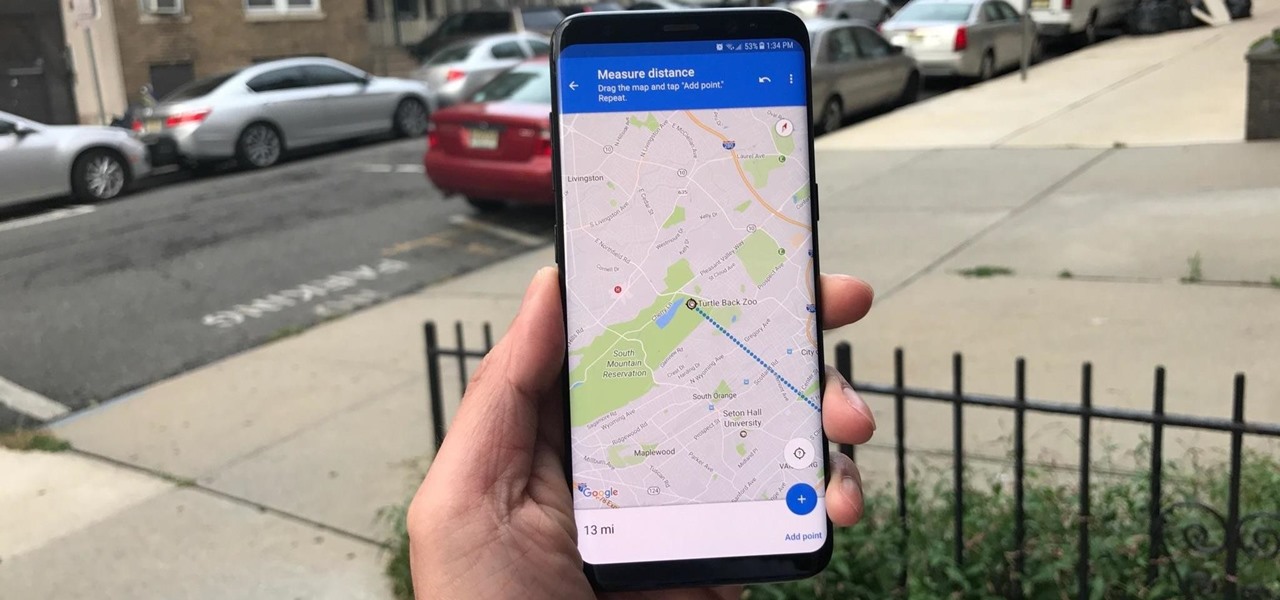
If you want to find out the linear distance between your hotel and a landmark or restaurant you want to visit, Google Maps has a great feature that lets you quickly measure the distance between two or more points. It's perfect for getting an idea of how far places are in relation to each other, which can help you plan trips more efficiently.

Natural remedies used through the ages abound, especially in Asian medicine. The willow-leaved justicia plant, found throughout Southeast Asia, has traditionally been used to treat arthritis, but scientists have just discovered it contains an anti-HIVcompound more potent than AZT. AZT was the first drug approved to treat HIV, and is still used in HIV combination therapy today.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

Well, well, well. Uber, we knew you were investing a ton of money into creating self-driving taxis and flying cars, but what we didn't know is that you were already testing out your driverless vehicles on the streets of New York City.

When the mosquito that carries the malaria parasite (Plasmodium falciparum) bites someone, the parasite must travel to the liver where it undergoes part of its lifecycle before infecting red blood cells and spreading to its next host. Until now, the first step of how the parasite gets to the liver hasn't been clear.

The rate of preterm birth has been increasing in the United States for unknown reasons, causing increased health risks for infants born too soon. But researchers may have found a signal that could help doctors plan ahead for, or even prevent, early birth with a simple swab of the vagina and cervix during pregnancy.

As a commercial and potentially consumer product, one might assume it very unlikely to see the Microsoft HoloLens in the military marketplace. And that assumption would be completely wrong. One company from the Ukraine is currently working on using the mixed reality head-mounted computer for 360-degree vision inside armored tanks. If a tank crew could see the entire battlefield there are in, they would likely have a better chance of accomplishing their mission and avoiding damage. Tanks are l...

Since the days of flip clocks, alarms have always had one function—make a bunch of annoying racket early in the morning to ensure that you wake up in time. And this simple MO has stayed in place while technology advances at a breakneck pace, almost in spite of the fact that today's devices are capable of doing far more than beeping at 7 in the morning.

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Black Friday and Cyber Monday are becoming almost synonymous these days, but there are still plenty of awesome deals that you can only get starting on the Monday after Thanksgiving. Amazon, for instance, will be hosting a week-long Cyber Monday sale, and of course, most big-box retailers will follow suit with their online stores.

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"
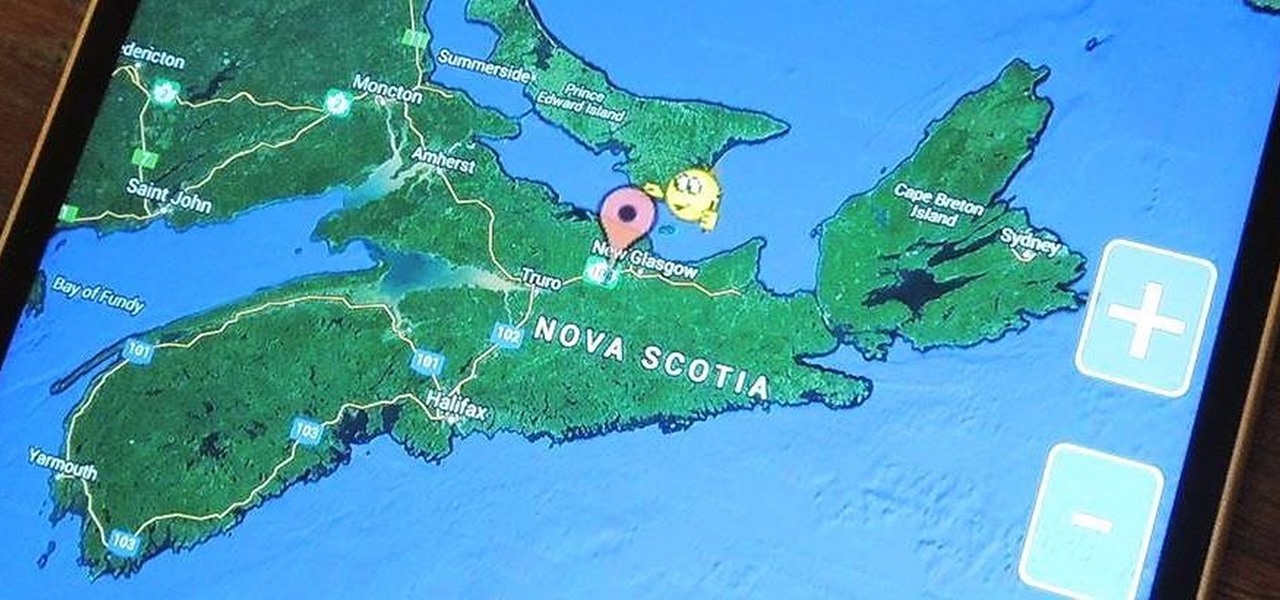
You wouldn't send your GPS coordinates to a completely random stranger just because he or she asked you for it, right? So why are you constantly sharing your location (and other data) to apps on a daily basis?

It took many months of cries from all around the internet—and a particularly large groan from an ex-Lifehacker editor-in-chief—but Apple has not only acknowledged the existence of its iMessage problem, it's promising a fix.

The lengths people will go to for a grilled cheese sandwich are amazing. They'll use irons, wafflemakers, or whatever appliance that produces enough heat to produce the perfect combination of golden, grilled bread and oozy, melting cheese. I personally favor my cast-iron skillet or the oven for making a really great grilled cheese sandwich. If I'm feeling lazy, then a toaster oven will do. But what if you're at work or in a dorm and the break room only has a toaster?

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.

When you post something online, it pretty much stays there. So it's no surprise that Snapchat, the self-destructive photo-sharing app, became such a huge hit, boasting an estimated 50 million users. Its ephemeral nature has proven popular, especially with teenagers—who are now well aware of the burden that permanence on the internet has.

Welcome back, my hacker novitiates!

You (or your partner, or both) are a Steampunk. Let's get away from all the mindless, unfeeling commercialism for a few minutes and think about dates instead of gifts—where do you take your significant other for Valentine's Day? What would be the ultimate Steampunk Valentine's Day date?

Summer is in full swing! Everywhere you look, plants are in full bloom and green is a way of life. Gardeners are clearly living up to their full potential. I cannot think of anything else that personifies summer better than gardening.