Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

Just because you're vegan, doesn't mean you have to substitute flavor with drab foods. Remember mayonnaise? Well, it can be substituted with something called Vegenaise, a vegan mayo substitute, perfect for potato salads. And for your southern-style greens cooked with pot liquor, you can substitute the meats with simple chipotle chili and smoked jalapeño peppers.

Commemorate the worst president in history by drawing his face to a lifelike representation and then having a dart throwing contest with your homeboys at the bar! This drawing tutorial, which teaches you how to sketch the face of George W. Bush, or W, is an excellent way to hone your targeting and aiming skills.
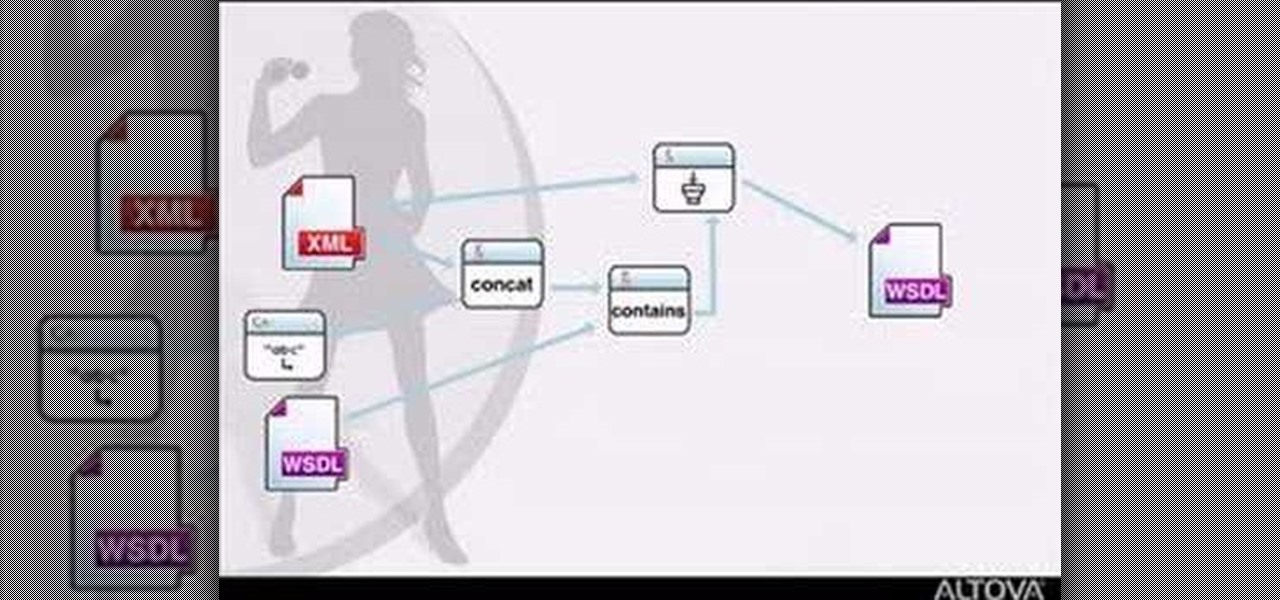
MapForce supports XML, databases, flat files, EDI and web services as the source and target of any mapping. In this tutorial, you'll take a look at how to use the different data sources available in MapForce.

Feel beautiful from the inside out with targeted exercises, like these exercises for your feet. This how-to video has a few simple exercises that will strengthen your toes and relieve some foot discomfort. Keep your feet in good shape so you can wear those high heeled shoes all night.

Brad Keller demonstrates how to throw a flying disc. The key is that whoever has the most fun wins. You need to throw the disc flat other wise you will miss your target.

This is the end of the Xbox 360 game Darksiders. It's the last level, the last quest, your last mission… the Destroyer. You'll need to summon Ruin to stand a chance against the Destroyer. Hold the Focus button to target lock onto the creature so you can keep in in view as you move around. The idea is for you to ride in close enough to the dragon and slash it with your Armageddon Blade. Watch out when you see the Destroyer's front claws glow red as this means he's coming to slash at you. Eithe...

Rumors, gossip, exclusion. Mean girls have a lot of weapons in their repertoire – here's how to combat all that nastiness.

Learn how to do single leg cable curls. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do knee tuck floor crunches. Presented by Real Jock Gay Fitness Health & Life. Benefits

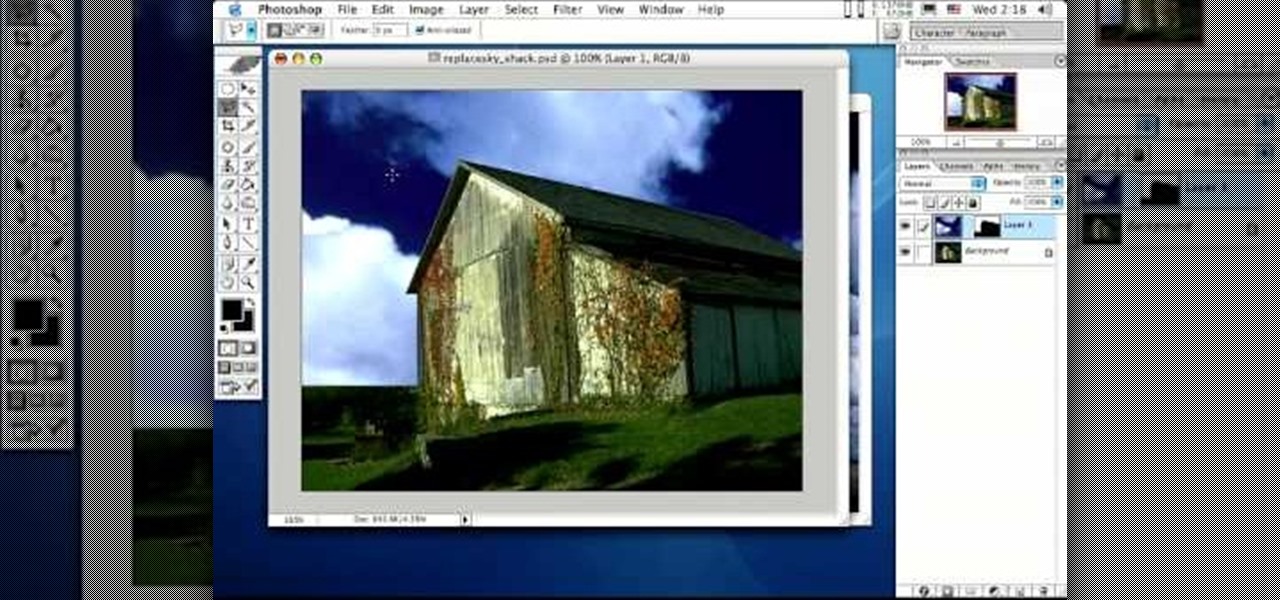
Photoshop is the perfect program to use when you want to make adjustments to photos you have taken. You can really make a sky pop in any of your pictures by using Photoshop to manipulate the color by following this tutorial.

Feeling unprepared for the next earthquake? In this tutorial, learn what to do and what not to do to survive "the big one". You'll be surprised to learn that hiding in a doorway is a myth!

Watch this video tutorial to learn how to book the best hotel room for your money. You've spent all year saving up for your dream vacation. The last thing you want is to end up in a hotel room that ruins the whole trip.

Learn how to do alternate power stability ball pikes and knee tucks. Presented by Real Jock Gay Fitness Health & Life.

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

If you're never hitting the target, maybe archery isn't the sport for you. Maybe it is, you probably just need to work on your technique a little, and this video serves up some great advice for archers when it comes time for instinct shooting. Learn a method for practicing instinct shooting with a traditional wooden bow and arrow. To see more videos about traditional bow and arrows, check out Traditional Archery Bows on WonderHowTo.

If you wish to deactivate your Facebook account you should watch this video to learn how to do so. 1. In order to deactivate your Facebook account you have to click on Settings in the top right corner of the screen. 2. Afterwards scroll down to find the option "Deactivate account" and click on it. 3. By doing so you would not be totally deleting your account as all the information will still remain saved.

Check out this great full body workout using a medicine ball and a partner with this fitness tutorial. Each of these exercises targets your abdominals, back and arms. This is a partner workout, just switch halfway thru and you both can get a full body workout. Watch this how to video and both of you can get in shape with medicine balls.

A lot of the English you hear in the real world isn't taught in the classroom. Swearing is important to know about if you're going to speak English. In this ESL how to video, you'll learn about the difference between 'bitch' and 'slut' which many ESL speakers confuse. If you look in many dictionaries, 'bitch' is defined as a female dog, so many ESL speakers think when you refer to a female woman as a 'bitch' that she has sex with any male, but this is totally wrong. Watch this how to video an...

Shawn Clement, Director of the Richmond Hill Golf Learning Centre and CPGA Professional, shows how the right grip will set up the arms and putter to hang in balance properly from the shoulders to track on the target line on it's own.

Invented by Motorola engineer Bill Smith in 1986, Six Sigma's methodology defines a series of steps with specific value targets. These targets can be used, for example, to eliminate costs and process cycle time while increasing profits and customer satisfaction.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

Black Friday is upon us. Whether you prefer to duke it out in stores or calmly shop online, there's no doubt you'll find great deals on the items you're looking for this holiday season. It's the perfect time of year to buy something expensive, like a good pair of AirPods, Beats, or Bose, at a much more opportune price.

After you've spent your Thanksgiving afternoon working through that turkey, mashed potatoes, and three different kinds of pie, you might find yourself heading to the mall to claim some unbeatable Black Friday discounts on iPhone 11, 11 Pro, and 11 Pro Max. You don't have to go in blind, though. Check out our guide below to make sure you're saving as much as possible on the iPhone you really want.

Despite the fact that over 600,000 Snap Lens filters have been created since Lens Studio debuted in 2017, and Facebook is reporting that more than a billion users have interacted with its Spark AR filters across Facebook properties, social augmented reality filters get a bad rap in the AR industry.

Before smartglasses makers can dream of taking smartglasses to mainstream consumers, they must first determine the right mix of form, function, and price that will drive customers to buy into what they're hoping to sell.

Social media accounts are a favorite target for hackers, and the most effective tactics for attacking accounts on websites like Facebook, Instagram, and Twitter are often based on phishing. These password-stealing attacks rely on tricking users into entering their passwords into a convincing fake webpage, and they have become increasingly easy to make thanks to tools like BlackEye.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

The holidays are here, which means a slew of new smartphones are set to be gifted to loved ones in the spirit of giving. Of course, a great case to compliment and protect that precious flagship is a must, regardless of whether it's a OnePlus 6T, iPhone XS, or Galaxy Note 9. And while quality cases usually come with a hefty price tag, there are plenty of Black Friday deals to keep you from going broke.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

Despite the launch of ARKit a year ago, and ARCore this year, a true killer app has not arrived for either platform, that's according to the head honcho for one of the leading development environments for 3D applications.

While Magic Leap has gained attention for its ability to raise capital, the company (now with an actual product on the market) still faces an uphill climb against the titans of the industry.

While numerous startups are competing to convert the AR Cloud from a pie-in-the-sky to a reality, Wikitude is thinking smaller with the latest edition of its augmented reality SDK.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.