As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

Since starting as a simple messenger with self-destructing pictures, Snapchat has grown into a full-fledged social media platform. As features were added, new permissions were requested, and we're all probably guilty of just tapping "OK" to try out the latest and greatest. But at some point, it's a good idea to review your settings to see what personal data you're putting out there for all to see.

Google's new AI-powered camera, Google Clips, seems to be targeted at parents of young children in its current form, but the idea itself has unique potential. Just set it up somewhere, then you'll never miss a moment trying to capture the moment — you'll have a robot photographer taking care of that stuff for you.

Coming into this year's Consumer Electronics Show (CES), the common sentiment among observers was that this was expected to be the big year for augmented reality.

| Updated February 11, 2019 with new phones. When will my phone get Android Oreo? That's a question still being asked by many, even this late in 2018. Most OEMs have answered this question in one way or another, either releasing a stable OTA or confirming their device won't be receiving the update. We consolidated all these responses, and here's where we stand.

Unscheduled pit stops go hand in hand with road trips, no matter how well-planned they are. In the past, making a stop due to low fuel or an emergency bathroom break may have snowballed into massive delays when you went off course on your own, but thanks to a feature in Apple Maps, you can do this in the most efficient manner possible.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

While ARKit and ARCore are poised to bring AR experiences to millions of mobile devices, one company is poised to anchor those experiences anywhere in the world with just a set of geographic coordinates.

For a company more associated with debugging computer programs, Google's parent company, Alphabet, is making a name for itself by taking on the real thing — mosquitoes.

Flu vaccines can help prevent us from getting or suffering the most severe effects of the flu. But, each vaccine only protects us from three different strains of the flu. If we don't have a vaccine against all types of flu, it leaves us open for an epidemic with a flu virus we didn't expect.

Malaria is a massive worldwide health problem. The Centers for Disease Control and Prevention estimate that 212 million cases of malaria occurred worldwide in 2015 and 429,000 of the infected people died.

As summer heats up, new maps from the Centers for Disease Control and Prevention (CDC) gives us our best guess at where Zika-carrying mosquitoes could be hanging out this year in the US.

Most of us have already had an encounter with the Epstein-Barr virus, or EBV, for short. As part of the herpes family, it's one of the most common disease-causing viruses in humans. We get the disease with (or without) some nasty symptoms, then we recover. However, EBV stays in our body after the illness has ended, and it's one of the few viruses known to cause cancer.

The problem with HIV is that it attacks and kills the very cells of the immune system that are supposed to protect us from infections — white blood cells. But a new technique, developed by scientists at The Scripps Research Institute (TSRI) in La Jolla, California, offers a distinct HIV-killing advantage.

Fighting fire with fire, scientists are harnessing the adaptability of helpful microbes to challenge the adaptability of deadly microbes. What are we talking about? Hunting with phages — viruses that attack and kill bacteria.

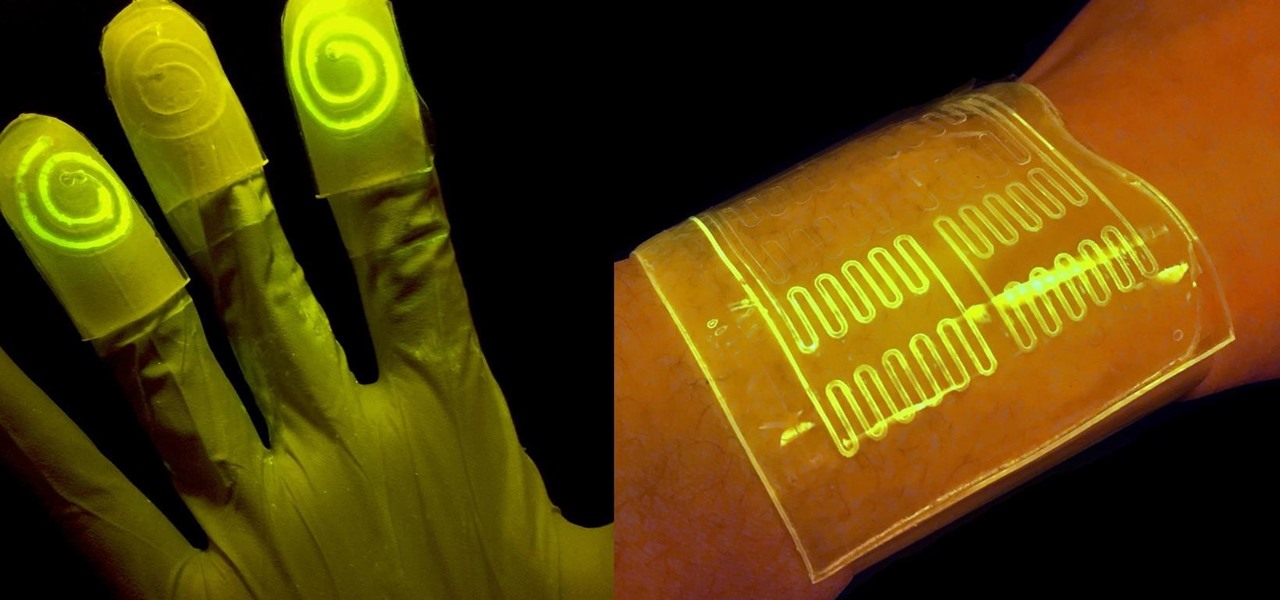
While at work, you notice your gloves changing color, and you know immediately that you've come in contact with dangerous chemicals. Bandages on a patient signal the presence of unseen, drug-resistant microbes. These are ideas that might have once seemed futuristic but are becoming a reality as researchers move forward with technology to use living bacteria in cloth to detect pathogens, pollutants, and particulates that endanger our lives.

Being infected with HIV means a lifetime of antiviral therapy. We can control the infection with those drugs, but we haven't been able to cure people by ridding the body completely of the virus. But thanks to a new study published in Molecular Therapy by scientists at the Lewis Katz School of Medicine (LKSOM) at Temple University and the University of Pittsburgh, all that may change.

The squiggly guys in this article's cover image are Propionibacterium acnes. These bacteria live in low-oxygen conditions at the base of hair follicles all over your body. They mind their own business, eating cellular debris and sebum, the oily stuff secreted by sebaceous glands that help keep things moisturized. Everybody has P. acnes bacteria—which are commonly blamed for causing acne—but researchers took a bigger view and discovered P. acnes may also play a part in keeping your skin clear.

Japan is in the process of curbing its aging population and mature workforce. According to The Diplomat, the country's population has been declining at a steady rate. To meet future productivity demands in commercial and industrial sectors, local officials are turning to self-driving technology, including truck platooning, where three or five vehicles travel autonomously in a string formation. This practice, according to a study by MIT, can reduce fuel consumption by up to 20% (more about thi...

A tiny louse is responsible for decimating the citrus industry. Diaphorina citri, the louse in question, better known as the Asian citrus psyllid, harbors and spreads the "Candidatus Liberibacter asiaticus" bacteria that causes citrus greening disease.

Transmitted by a sandfly one-third the size of a mosquito, parasitic Leishmania protozoa are responsible for a flesh-destroying disease that kills an estimated 20,000 people per year. Two new studies offer understanding of how the parasite provides immunity through persistence and why some people suffer more virulent forms of the disease.

Seriously, what's with all of the candy corn hate? I don't care what anyone says, candy corn is and always has been the perfect Halloween snack for me. Only recently did I realize that not everyone gets as hype as I do about small, sugary vegetables.

Looking past the obvious visual similarities between the iPhone 7 and Google's new Pixel phones, there are several indications that the search giant had Apple in its sights as they released their latest flagships. For once, this isn't an Android phone we're talking about, it's a Google phone—and it showcases Google's latest strategy.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.
If your company has already released some popular and addictive game and you're thinking about creation a sequel, this article is just what you need. We gathered the main tips and advices that will be useful for the building a strategy and a sequel itself. Check out the following instructions and recommendations that can lend you a hand in making a sequel for your game.

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

There are many, many home remedies out there for relieving itchy mosquito bites. Everything from mud to banana peels and basil leaves to Alka-Seltzer tablets can help curb the itch. But before you even have to resort to any of those methods, you should be thinking about prevention. Wearing white clothing can help to keep mosquitoes aways from your skin, and there are many plants that will help mask your mosquito-attracting smell. But there's even more ways to keep those bloodsucking bugs away.

Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?