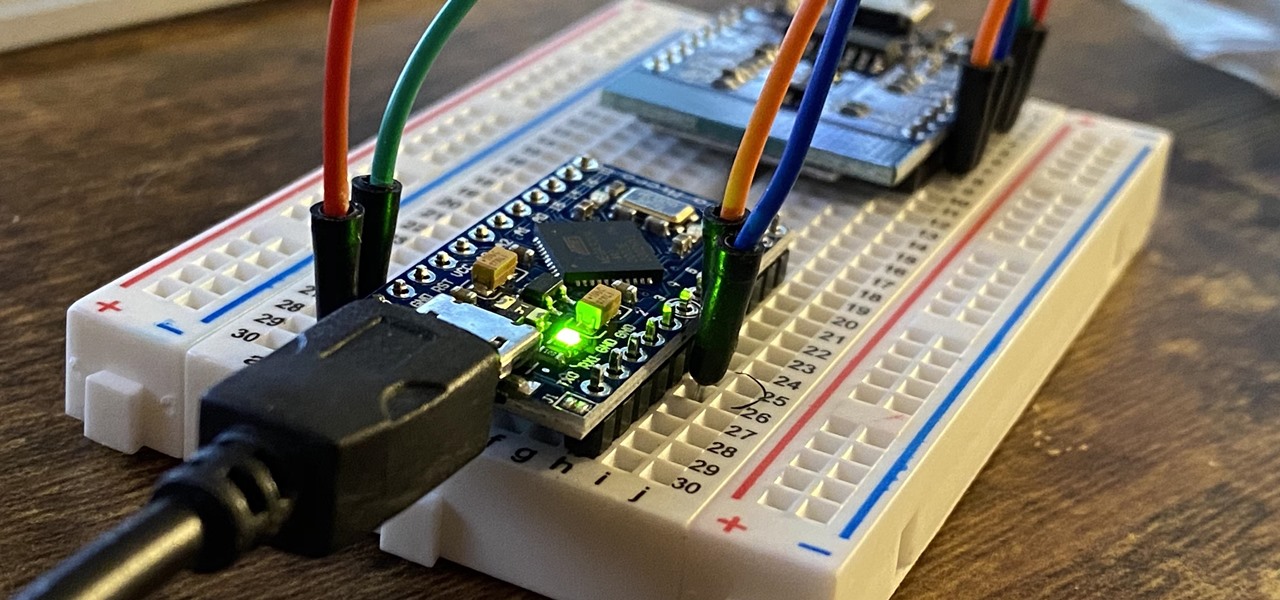
Like theme music, I always feel that I need more fog in my life. Fog can be useful for many reasons—warding off smaller siblings from your bedroom, keeping curious hands out of your cupboard, and tricking your friends into thinking there's something horribly wrong with their vehicle. So, today we'll be making a very simple fog machine for small scale applications.

If you've run out of time for all of our more time-consuming Halloween costume ideas, here are some places on the web for free, downloadable paper masks. There must be at least 100 options among these links to satisfy your last-minute costume needs! Just download, print, and cut 'em out to the appropriate size, then either glue a stick/handle on or tie some elastic string on.

Discover the art of Telescopic Pole Setup in this informative video, where we guide you through the process of preparing your pole for speedfishing. Whether you're targeting Bluegill, Crappie, Trout, or Perch, pole fishing stands out as one of the most effective methods to reel in a catch.

This particular video series covers what is called the natural facelift. It is essentially an intense facial that is more involved and has agents that target those trouble areas where wrinkles tend to occur more often such as around the eyes and mouth. This is a fantastic alternative to the pain and cost of surgery. Instead of weeks of recovery you have no recovery time and see effects almost immediately. It also removes the risks of a surgical procedure and is very relaxing as well. Check ou...

Dive (or more appropriately, soar) into another Tom Clancy video game on the Xbox 360— This walkthrough series for Tom Clancy's H.A.W.X. 2 covers the whole entire gameplay for the newly released sequel. Gun down countless MiGs, bomb enemy tanks and shoot down nuclear missiles before they destroy their targets! This video game is all about speed, battle and adrenaline. Try out this air combative flight simulator yourself, and see if you're not on the edge of your seat. Watch the full walkthrou...

Wireless emergency alerts help warn mobile phone users of imminent threats to life or property, such as extreme weather and natural disasters. These alerts target affected geographic areas and come with a loud sound scary enough to make you want to turn off emergency alerts altogether on your iPhone, but there's a way to keep emergency alerts without the ear-splitting, intrusive sound.

A low-key iPhone feature that's been around since iOS 10 can make the iMessages you send to family and friends more exciting overall. One particular element is, if you'll forgive my decades-old slang, "da bomb" for emoji.

Wireless charging is pretty much ubiquitous among modern iPhones and Android smartphones, but the technology has brought a lot of clutter with it.

The big day for Snap that resulted in the debut of brand new augmented reality Spectacles smartglasses is turning into a big week.

As a hacker, the final stage of exploitation is covering their tracks, which involves wiping all activity and logs so that they can avoid being detected. It's especially crucial for persistence if the target will be accessed again in the future by the attacker.

After years of testing and modifications, the US Army is moving forward with its customized version of HoloLens 2 from Microsoft.

With non-fungible tokens (NFTs), particularly those that are 3D in nature, holographic displays are becoming more indispensable for those looking to show off their valuable works of art.

Samsung and Google have done some amazing work together in the past, particularly with Android related projects. But after years of an inexplicable lack of interoperability, the primary smart home hardware divisions from both companies are finally on the same page — starting right now.

There are at least 24,000 different Android devices, and they all have varying hardware components. This is why many developers publish several unique variants of their apps, which, among other things, helps accommodate all of the different display sizes and resolutions on Android phones and tablets.

The USB Rubber Ducky is a well-known hacking device in the cybersecurity industry, but it needs to be preprogrammed before it can be used. That means it's not easy to issue commands to a target computer since you can't interact with it from afar after plugging it in. And if you don't know what the target computer is, you might come up empty. That's where the WiFi Duck comes in handy.

As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ways. Today, we will be covering various methods to perform banner grabbing to learn more about the target system.

While the stock market can be unpredictable, it's not a complete enigma. There are patterns to watch for that can make you a successful trader. Fortunately, there is an expert guide to becoming an analyst that's now available to everyone.

You don't need to work as an executive at Google to understand and appreciate the importance of large-scale data analytics in today's world. Whether you're interested in joining the ranks of a major tech firm or want to improve your company's marketing campaigns through consumer analysis, knowing how to work with large sets of complex data is paramount.

An attacker can create three, five, or even ten new Netcat connections to a compromised MacBook with one command. Performing complex post-exploitation attacks might otherwise be difficult from a single shell without this essential trick.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

It's finally here. After years of rumors and speculation, Apple unveiled the new iPhone SE on April 15. While it doesn't have a 4-inch display like the original SE, it's the smallest new iPhone you can buy today, with the chipset of the iPhone 11, 11 Pro, and 11 Pro Max. So, when can you get your hands on it?

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

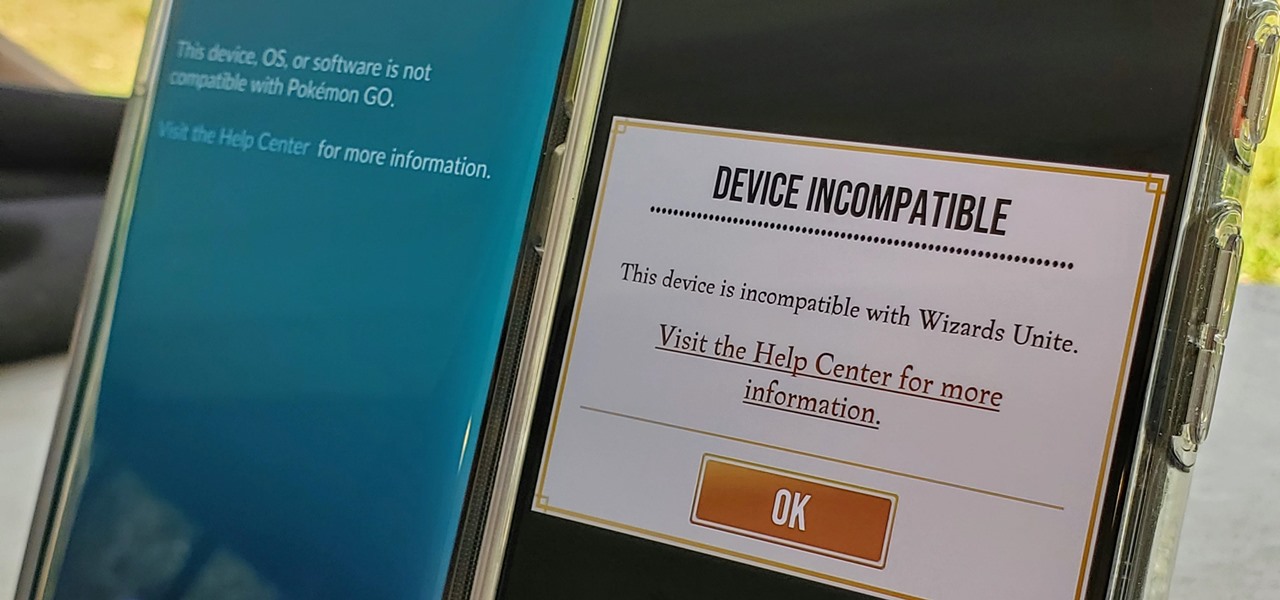
Both Pokémon GO & Harry Potter Wizards Unite are augmented reality games developed by Niantic, and neither needs much introduction. Pokémon GO, all by itself, created a worldwide phenomenon that still carries a strong fan base years later — Wizards Unite is working on doing the same. However, things are not all fun and games, as you might think in the world of monsters and magical creatures.

With every new Galaxy flagship release comes the age-old dilemma: do I choose great hardware or great software? For years, Samsung has given users the best components available on any smartphone. The problem is the software is an acquired taste. But there is something you can do about it.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

After facing reports of financial troubles over the past month, Magic Leap came out swinging this week with a big push for the enterprise segment of AR, including a repackaged Magic Leap 1, a suite of enterprise apps, and updates to Lumin OS and its supporting development ecosystem. Oh, and its AR headset managed to win a starring role in the marketing juggernaut for the forthcoming Star Wars movie.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

While some people might like Thanksgiving because of the food, seeing family, or another wholesome reason, many of us also enjoy saving big on the items we've been eyeing all year. Take iPhone cases, for example. Speck, Insignia, even Apple all make cases that can put a dent in your wallet. A good Black Friday deal can mean a shiny new case for your iPhone and some extra dollars in your pocket.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

Indian startup Dimension NXG is launching augmented reality headsets into India's consumer market with a bold idea: focusing on immersive computing in education on the high-end. The plan is to give a new kind of AR headset to schoolchildren in remote Indian villages, starting from class 5 (age 10) until graduation.

In our comparison of the best gaming phones in 2019, the winner actually surprised us. A phone that most people don't know about from a brand you probably haven't heard of ended up as the clear winner. But how? Well, it ticked so many flagship boxes despite its midrange price tag.

The Reader mode in Safari is a great way to view a webpage on your iPhone in a stripped-down manner, removing unnecessary images, videos, and advertisements for a streamlined experience free of distractions. Apple's iOS 13 improves upon Safari Reader when it comes to choosing which sites you want it to run automatically on, so everything is more accessible with more controls to work with.

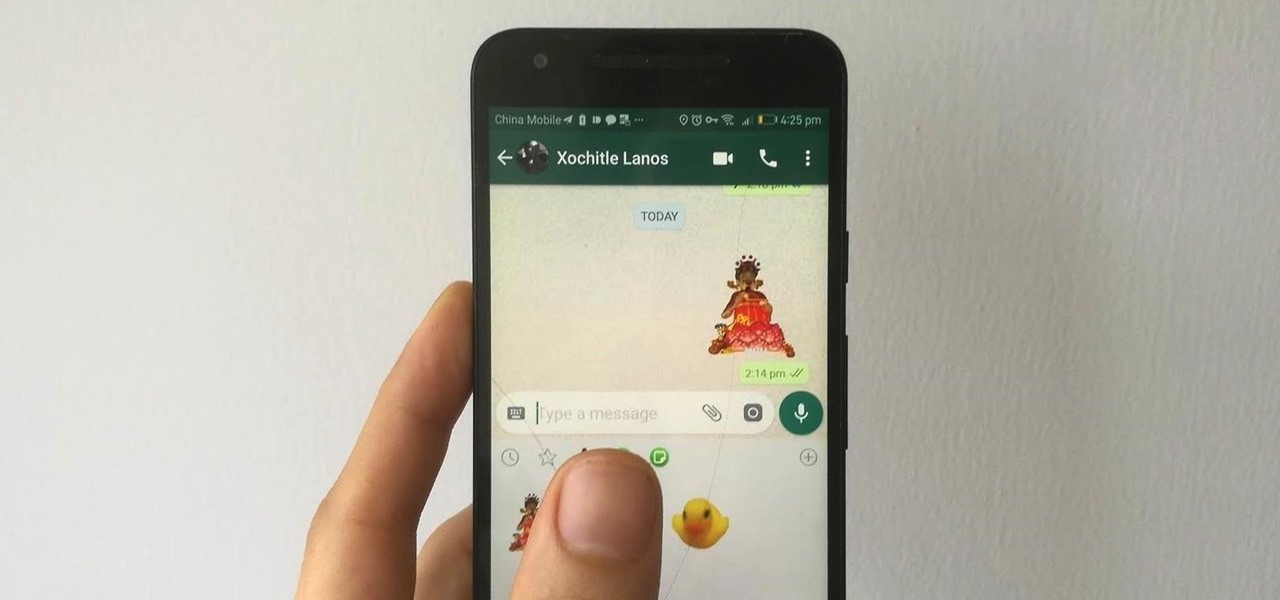
WhatsApp stickers can make your chat more fun. The stickers that come with WhatsApp are fine, but they're standard and accessible to everyone. What if you wanted to show off unique stickers that your friends haven't seen? To take things to the next level, you can create your own WhatsApp Stickers.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

In the first guide, we laid the groundwork for our ultimate goal of uploading and running the unix-privesc-check script on our target. We identified an input field vulnerable to SQL injection and utilized Sqlmap to set up a file stager on the server. Now, we're ready to upload files and execute the script, so we can identify any misconfigurations that could lead to privilege escalation.