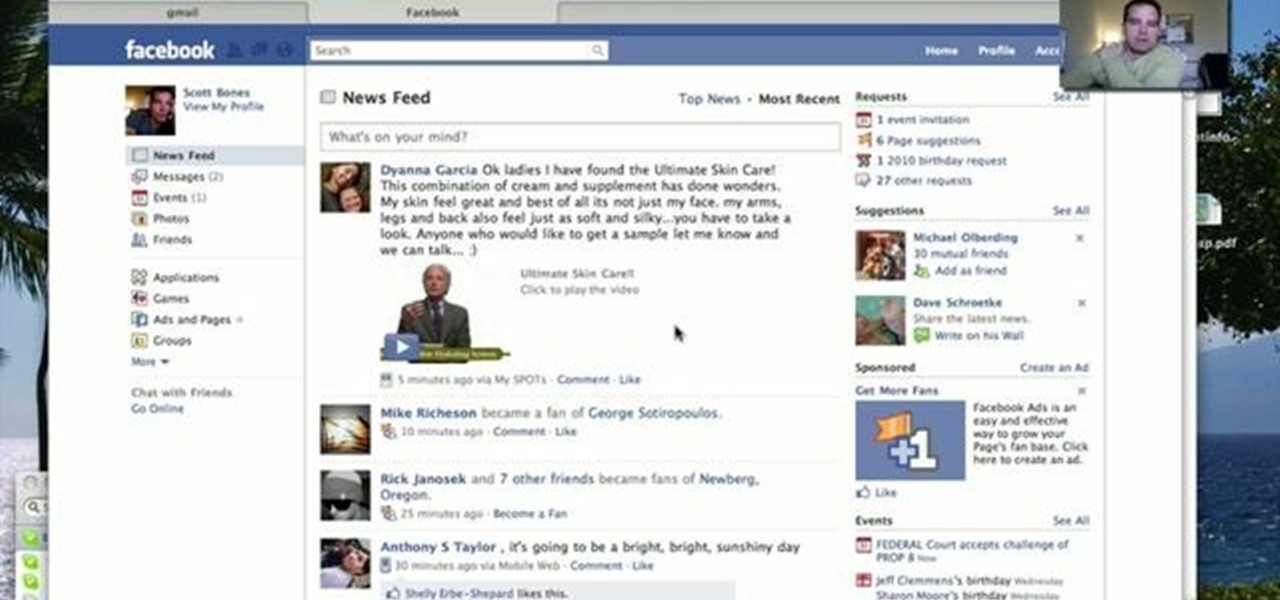
How To: Send a private wall post on Facebook
Privacy is important on Facebook, a lot of users don't even realize that their posts are being broadcast to the masses.


Privacy is important on Facebook, a lot of users don't even realize that their posts are being broadcast to the masses.

If you're planning to become a veteran yogini, you'd better start practicing and loving the up dog pose now, because you'll be spending the greater part of your yoga flow doing up dogs and down dogs.
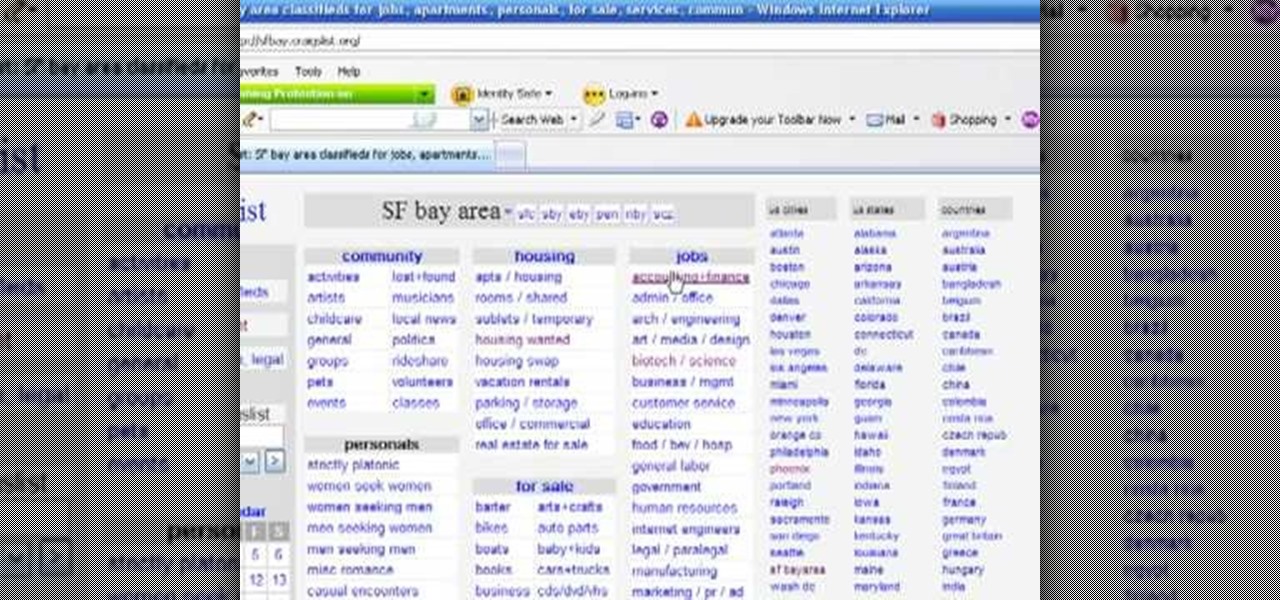
Sometimes searching Craigslist can be a real hassle if you're looking for something specific. You really have to sort your way through all the clutter in order to find whta you're looking for. If you are looking for email addresses of people who might fit your target market, you can scrape Criaglist for emails. This video will show you how.

Beef brisket is a delightful tradition that all families will love. But, brisket can be one of the hardest things to BBQ. Check out this tutorial if you are having trouble. This recipe works very well.

There are many so-called methods for beating the dealer at BlackJack, but not many of them actually work. In this tutorial, get tips from a professional gambler on how to outsmart the system and win every time. You will be raking in the cash after a few practice sessions with this video as your guide. All of the methods in this video are totally legal ways to win..so why not try it? I mean, in these rough economic times, couldn't you use some extra cash? And it's fun too!
Knowing what traffic lies ahead is detriment to getting home on time. If you get stuck in a traffic jam or road construction, then the only thing you gain is frustration. But with Ford's new SYNC system, you can get up-to-date real-time traffic reports for your local area or specific drive home. Real-time traffic reports help keep you posted on construction, accidents, and other accidents in your commute. You just need to set up some simple preferences on your online owner's account.

If it's an emergency, sometime you just don't have enough time or energy to pick up your mobile phone and call 9-1-1. Sometime you just can't move and the only thing still working is your mouth. Ford's new SYNC system provides an option for hands free 911 Assist. In a crash involving airbag deployment, 911 Assist places a call directly to a 911 operator. Your bluetooth phone must be on and stored somewhere inside the vehicle.

Sometimes pairing your mobile phone with your car is a difficult and unwritten chore to accomplish. But now with Ford's new SYNC system, you can easily pair your cell phone. It's as easy as pressing the Phone button. Let it search for already stored bluetooth devices, and if none are stored, simply press the Arrow buttons until you see the Add Bluetooth Device option. It's that easy!

To make sure your car is healthy and up to par with required maintenance, you can use Ford's new SYNC system to get vehicle health reports for you car. It gives you vehicle diagnostics, scheduled maintenance, recall information, and more. You just need to go online to your owner's account and set up your reports.

What if you're in the middle of a call before you enter your car? Ford's new SYNC system has a solution. As long as your cell phone is paired with SYNC, you can continue the conversation uninterrupted. See how to use hands free calling with Ford SYNC.
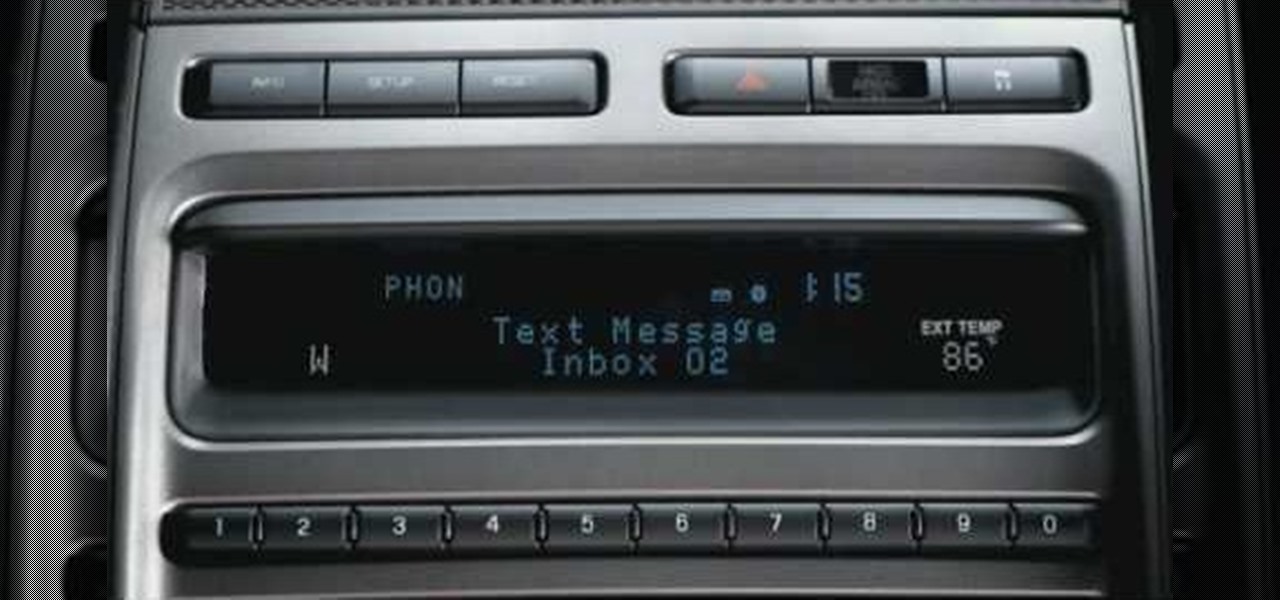
Texting is one of the biggest problems in automobiles today. It's very dangerous and distracting. Ford's new SYNC system makes texting safe for everyone, with audible texting. If you receive a text message on your mobile phone, SYNC can read the message to you out loud with the touch of a button. It can even translate LOL and smiley faces. See how!
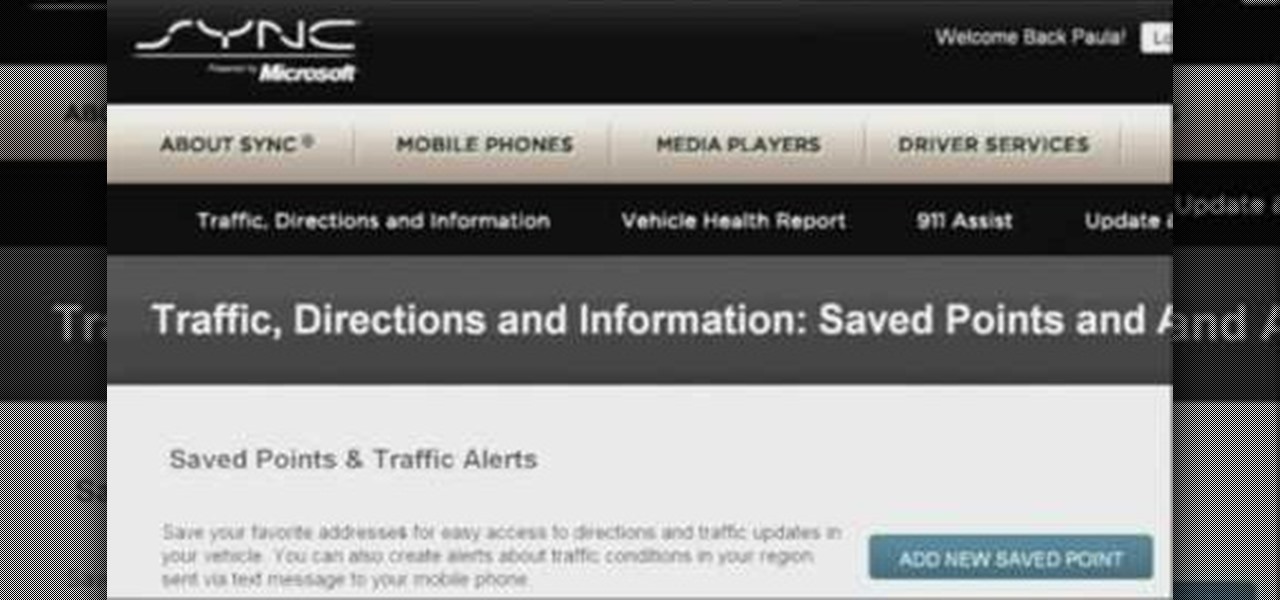
Customizing your user account online for Ford's new SYNC system is a cinch. Simply go to the website and customize news and sports, vehicle health reports, and your personal favorites. You can even start out by adding your favorite destinations for turn-by-turn directions later. Learn how to customize your Ford SYNC online user account.

Ford's new SYNC system makes it easy to receive personalized alerts, including weather, news, and sports alerts… hands free! You only have to go to your owner's account online and set your favorite alerts for your SYNC system. Then just press the Voice button and select your service.

Turn-by-turn navigation is easy with Ford's new SYNC system. Cities, businesses, your favorite places - name your destination and SYNC returns with your turn-by-turn directions. To add your favorite locations, you simply need to visit your owner account online, then you're ready to find your favorite directions, or any other directions needed.

Thanksgiving is all about the turkey. So much can go wrong with a turkey, though. The turkey could come out tough and dry, and totally unappetizing. Learn how to combat gross turkey, and turn out a moist, flavorful turkey for an awesome Thanksgiving.
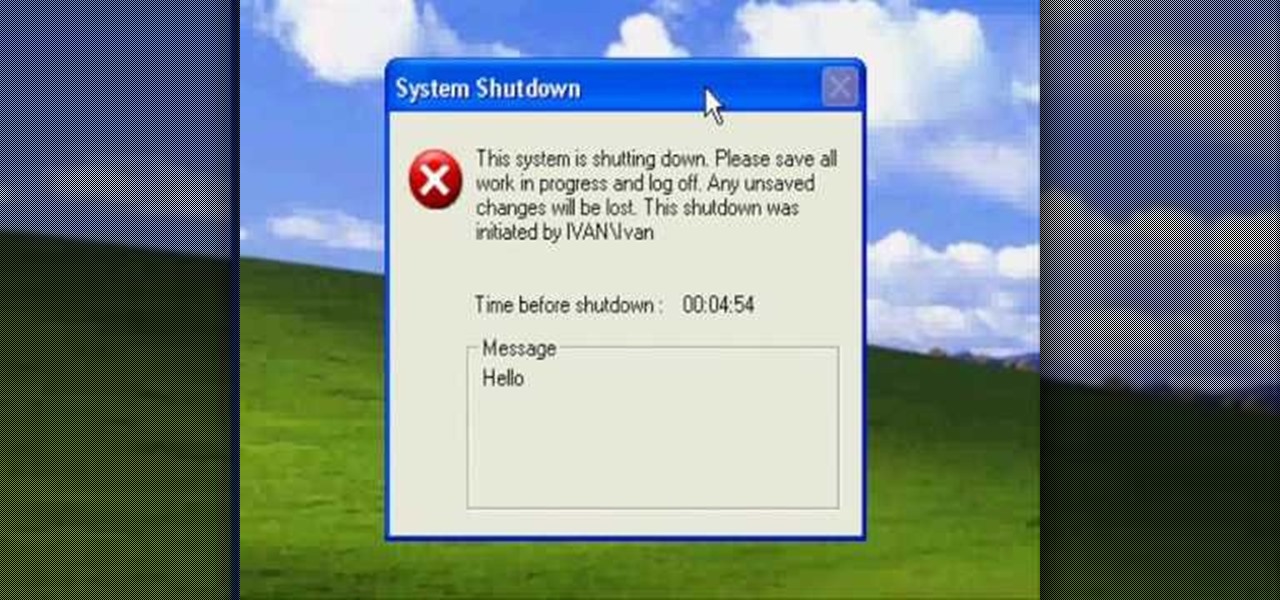
Okay, what's the greatest prank you can play on a friend in this day of technology? Mess with his computer!

When it comes to Photoshop, if you can imagine it then you can make it. Of course, more complex objects (and more realistic objects) take longer to complete, but the results are totally worth it. Just check out this lifelike coin, for instance. This Photoshop tutorial will teach you how to produce realistic coins via applying textures to a 3D cylindrical object.

Bethany, oh Bethany. What would we do without you? Bethany's makeup tutorials are completely inspired. She covers everything from cartoon characters to action figures to tv show characters and manages to make totally cute eye makeup based on al of them! All of her pretty eye makeup looks are nostalgic of childhood memories and favorite bands. Be sure to check out the rest of Bethany's tutorials on WonderHowTo.

In this episode of Hak5, Darren shows us a USB key, dubbed the USB Hacksaw, that instantly and silently installs on target Windows 2000 or higher computers with guest or higher privileges which will monitor USB ports for flash drives and automatically download their contents for silent archival and email. For detailed instructions on replicating this hack yourself, watch this video hacking tutorial.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.
Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Epic Games just released update v3.4 for Fortnite Battle Royale on all four platforms. This new version brings a number of UI changes, performance improvements, and bug fixes, but the addition that will get the most players excited is a new weapon: the Guided Missile.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.
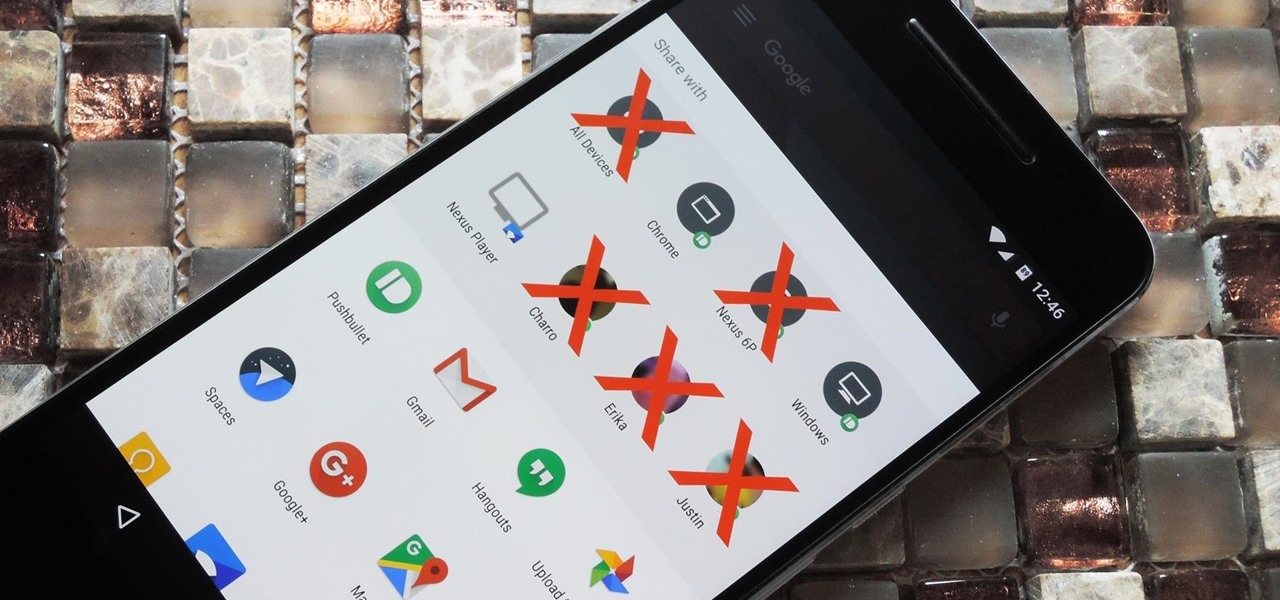
Android 6.0 introduced a new feature called Direct Share that allows apps to pin a more specific set of targets to Android's share menu. You've probably seen it already—messaging apps will allow you to share a file directly to a specific contact instead of just to the main app, and there are several other implementations like this.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

Five Phases of Hacking:- The five phases of Hacking are as follow:

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?