Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

Have you always dreamed about quitting your day job to pursue your true passion in writing about tips on how to bake your famous cupcake pops? Stop dreaming and start doing! Thanks to the prevalence of the internet, blog writing is more popular than ever, and successful bloggers actually make quite a hefty chunk of change doing what they love.

Are you using your website or blog for exposure or business? If you would like more people on the web to notice your masterpiece, check out this clip. In it, you will get real, helpful tips on how to get people to your site, so they keep coming back. There are plenty of ways to promote yourself and you will learn all about them here. So, grab a pen and take some notes and get ready to become the next Internet superstar.

Ever wonder how to get out of doing the things you don't want to do? Work, relationships, and simply driving in traffic can make you so tired that you're asleep on your feet. Not any more!

This video gives you the lowdown on making a lag switch for gaming. But why would you want a lag switch? What is a lag switch?

In this tutorial, we learn how to teach your child how to ride a bike. Before you get them on the bike, make sure you pick a place that is fun and safe. Make sure there are no distractions and no traffic. Pavement is the best place to practice to ride a bike. Make sure the bike is ready for them before you teach them as well. When you teach them, place training wheels on and then when they are comfortable, take them off and start off with a slow ride. Let them walk and ride with the bike to s...

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

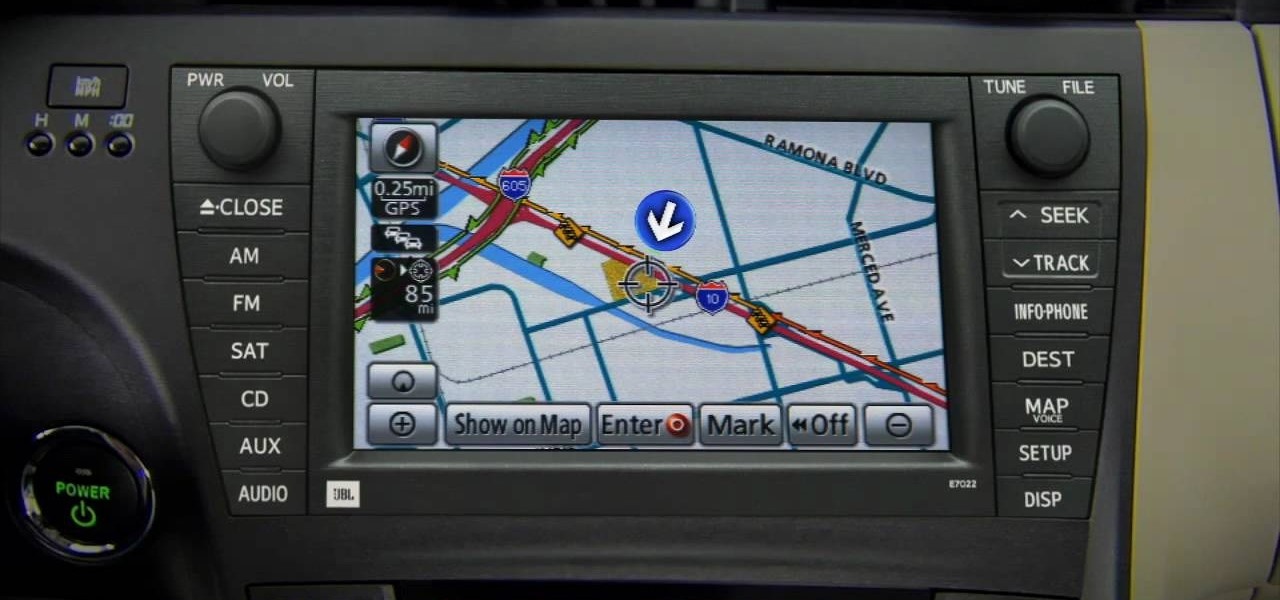
In this video, we learn how to use the XM NavTraffic feature in a 2010 Toyota Prius. First, turn the system on and then use the plus button toe navigate to where you are on the map. Next, you will be able to see what is coming up in the next few miles and what road blocks or delays you can expect. You can also enter in the destination that you are headed to, and the system will give you directions on which way will get you there the fastest. You can mark different areas that you have been at ...

Wouldn't it be nice to know how many people actually visited your site each day, and how long they stayed there? Google Analytics is a great, free utility from Google that will tell you just that and so much more. In this clip, the Web Guru will show you how to use this program, generate and install an HTML code onto your site so that you can keep track of your visitors and demographics. This is a fantastic tool for advertising purposes and so you can see which content is working best for you...

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Magic Leap's legal battle against Nreal has taken an intriguing turn this week, as Magic Leap set a date to discuss the matter with Nreal. But a new partnership struck by Nreal adds another wrinkle to the duel between the two AR wearable makers.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

Filmic Pro harnesses the full native power of your iPhone or Android phone — and then some. If your smartphone shoots in 4K resolution, Filmic Pro will let you choose that resolution. However, it's not all about the pixels — bit rate is an essential factor in determining the overall quality of your 720p, 1080p, or 4K video, something Filmic Pro gives you full control over.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

Until self-driving cars become mainstream, augmented reality might be the next big technology to hit your dashboard.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

The new Leaf with Nissan's ProPilot driverless feature could launch as soon as this year, following a teaser image and video the Japanese carmaker released of its flagship EV yesterday.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

Alright, this will be my first tutorial in C. Note that this guide is written for Linux.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

Over time, a wooden floor can sustain a heavy amount of damage thanks to the weather, heavy foot traffic, and things constanly falling on it. So, it's always a good idea to refinish a floor every few years or so to make sure that it will last longer. This tutorial will show you how to sand and save a wood floor. It's a difficult task, so make sure you have the time and patience to do it. Enjoy!

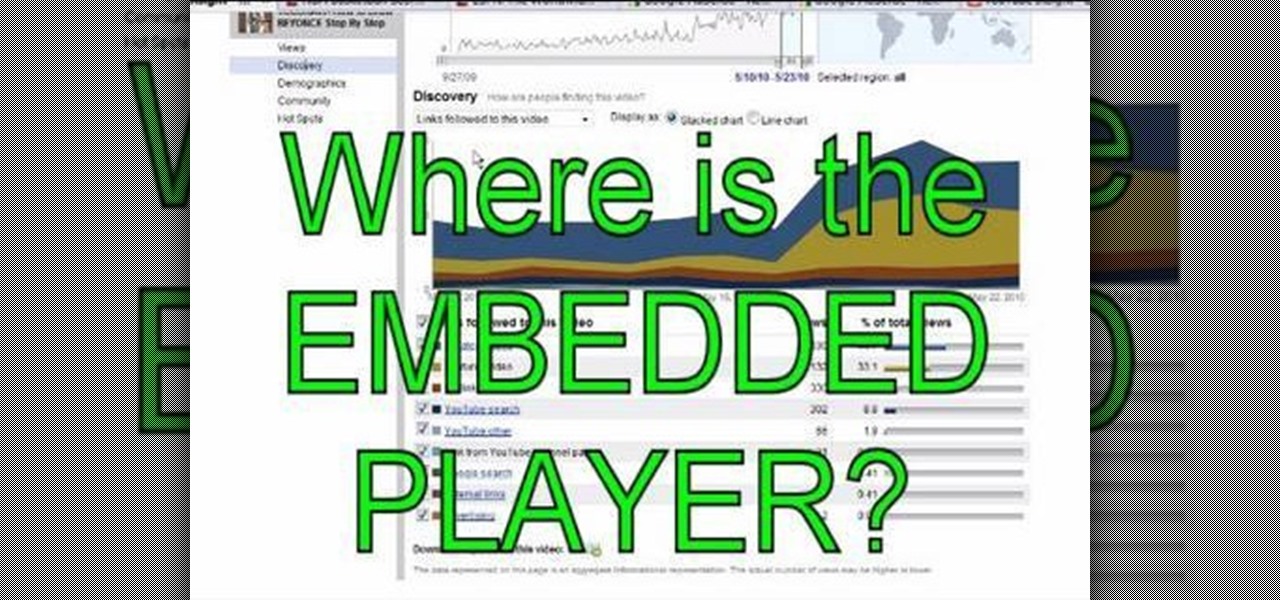
Are you a frequent Youtube poster? Then tracking which blogs and other sites have embedded you videos can be helpful in determining who is interested in your videos and increasing your number of views. When Youtube changed their site recently, they moved the Embedded Player tool that allows you to track that information and used to be under the Insight tab to a new place, causing mass confusion. This video shows you where to locate that tool in the new site layout, allowing you to track where...

In this video tutorial, viewers learn how to rent bikes in Europe. The cost to rent a bike is about $15 and the cost decreases per day the longer you rent it. Bikes can easily be rented in towns in small rental shops. Europe has many bike paths with signs for tourists to travel along without any traffic. To find these paths, users should get information from the tourist information centers or bike rental shops. This video will benefit those viewers who will be visiting Europe and would like t...

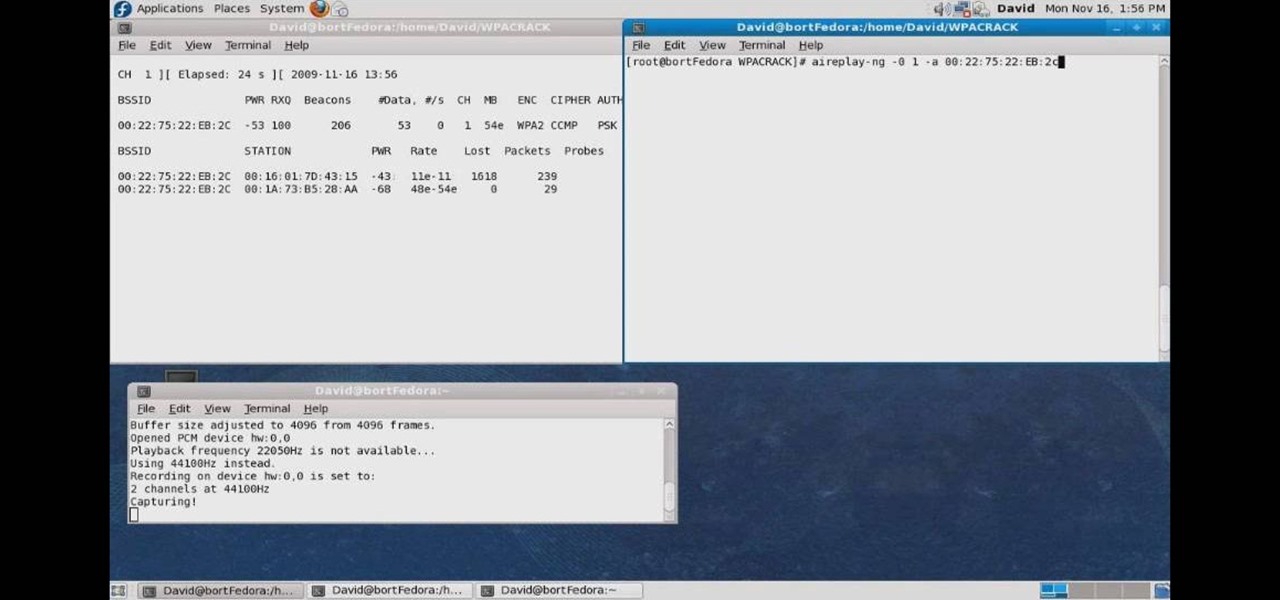
In this how to video, you will learn how to crack a WPA encrypted wireless network. To do this, you will need the Air Crack package for Linux. First, disable the wireless adapter and enable monitor mode. Next, identify the channel in the wireless network and Mac address. Once you have this, you can listen to the traffic coming to and from this point. Wait for the handshake or disconnect something in order to force it to reconnect. From here, you are ready to perform the attack. With any encry...

Brad Garland guides us through the process of sharing our media files so that they can be stored on a single computer in our home, and played on any computer that is connected to this computer with iTunes 9. Using this technique, he and his wife can not only play the music that's stored on the central computer via their laptops, but also copy the desired music and videos over to their laptops much like they would for an iPod. Brad explains that he does not include Podcasts in this process, be...