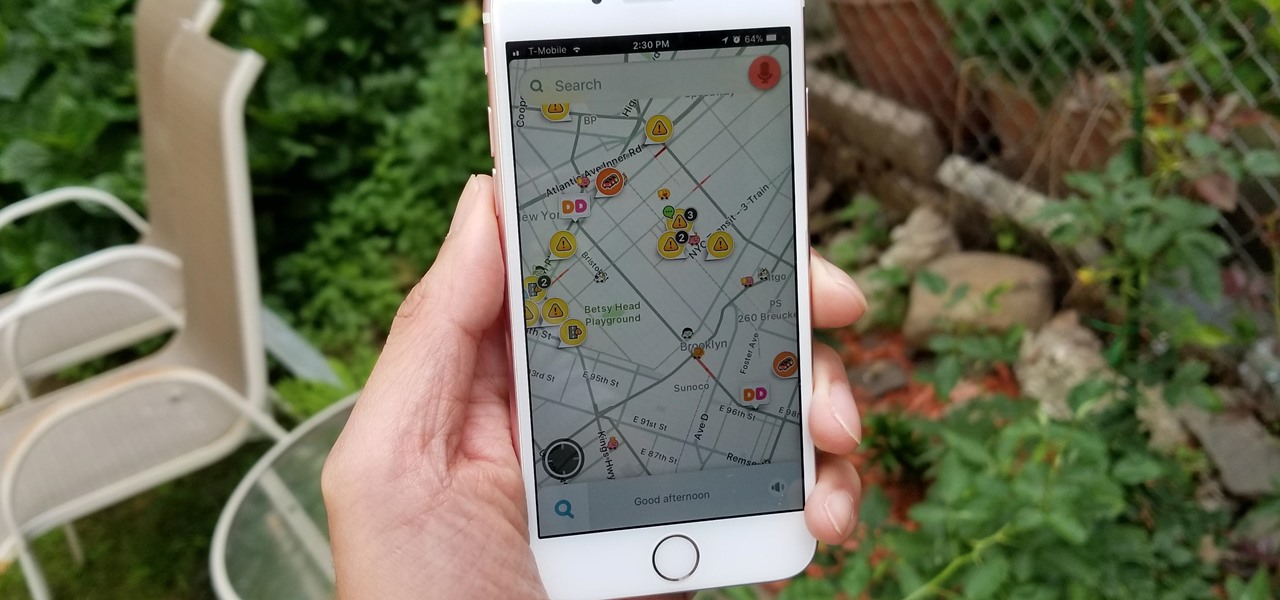
With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

Some of the things that make Waze such a great navigation app are also its biggest downsides. Real-time data shows where individual users are, and the app automatically gathers traffic info that other drivers may encounter. These elements ensure that road conditions are as up-to-date as possible so that everyone gets to their destination safely, but it's certainly not ideal if you're a privacy-minded user.

The launch of the Audi A8 marks the world's first Level 3 car on offer in retail channels, except there is one catch: it can only take full control of driving at speeds of 37.3 mph or less.

Geotagging your location on Instagram is one of the most undervalued ways to generate traffic to your profile. The beauty about adding your location to your IG posts is that it allows you to be seen by other users than the ones that already follow you.

In the driverless race, technological advances can sometimes just add more tension to an already heated competition, if Waymo suing Uber over their allegedly stolen LiDAR technology is any indication. Now, Sony is offering a new camera sensor, one that should help self-driving cars "see" the road with much more accuracy than any other camera sensors available for vehicles currently.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

This is just a heads up that thieves are now using GPS fitness apps to target people. Thieves are using popular GPS fitness apps such as Strava to find out where you live where they will then come and steal your bikes.

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

When it's most important for me to browse the web incognito, I always seem to forget to enable private browsing. If that sounds like you, it's time you stop making that mistake for good. Manually deleting the cache and browser history is a thing of the past, and as it turns out, so is manually switching to incognito mode.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

In this how to video, I discuss three different exercises that have really helped me to tone my waistline. Although you cannot specifically target different fat deposits while dieting, it is still important to perform these exercises to give your core and waist that aesthetic look. These exercises have given me great results, but a solid diet and a good training program is also extremely important to sculpting your body. Enjoy!

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

AdSense. It's a beautiful thing, isn't it? Google AdSense is something every website owner or blogger should use… it's what every blog needs… if you plan on making any money and surviving. So, how much traffic do you need to actually start making money via AdSense? This video will try and answer that question for you. You must have targeted traffic to drive your blog.

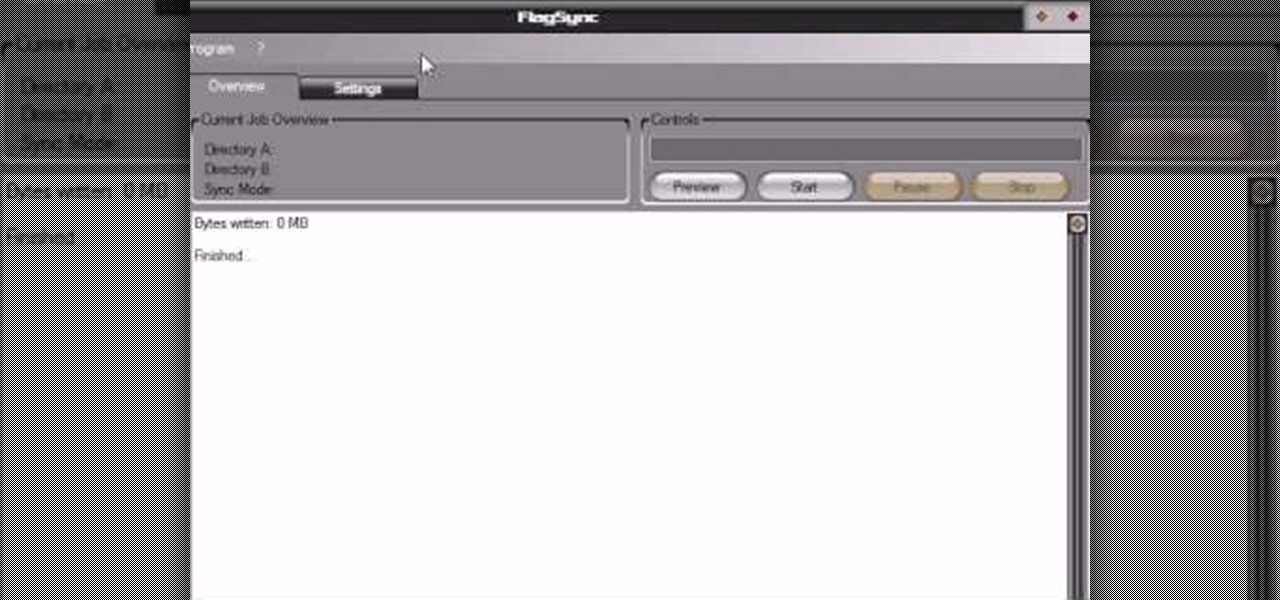
Video demonstrates how to synchronize two folders on windows without doing much of copy pasting and does the job easily. This is a free wear, “FlagSync”.

Get ready for the boss fight of your lifetime in the Xbox 360 game Darksiders. In the boss fight in Twilight Cathedral, spar against Tiamat. When you reach the bat queen Tiamat she will take offf into the air immediately. Quickly dash to the Inert Bomb Growth around the edge of the arena closest to the flying and then throw it at Tiamat. Now you need to use your Crossblade and target a flaming urn then the bomb you stuck onto Tiamat to light the bomb on fire. Once you detonate the bomb on her...

Keep your crossblade near for this level of the Xbox 360 game Darksiders, In the sub-boss fight in Twilight Cathedral - The Jailor, make sure to target the sores. This grotesque monstrosity towers over War. It is almost as wide as it is tall. You'll want to keep your distance from the Jailer as it has a powerful attack in which it slams the cage it carries onto the ground. You'll want to spend most of you time here with the monster targeted while you backpedal away from it. The biggest annoya...

Caged Fighter: Make your way across town and you'll find an injured soldier on the rooftops that gives you some new information on finding Bartolomeo, who should in turn help you with Silvio. You get a large green area added to your map, but note that it's overlapped by a restricted area. Expect trouble.

Knowledge Is Power: But can power be knowledge, too? Pay a visit to Leonardo and he'll cook up a new weapon for you based on a mystery codex. After the cut scene, move out to the yellow map marker and you'll get some directions on how to use your new pistol. Lock onto the three dummies across the river and shoot 'em. Holding down the fire button builds up your accuracy, making it possible to hit the distant targets. When all three targets are shot, return to Leonardo to complete the mission. ...

Infrequent Flier: Fly through this episodic mission and take control. As you take flight, immediately pause the game and check out your map. You can see the locations of all of the fires in the city, as well as the target to the far, far southeast. If you make a simple beeline for the target, the Palazzo Ducale, you won't get the updrafts you need to maintain your height and infiltrate the fortress. Instead, you need follow the trail of fires that lead you east and then north before finally t...

Have you tried working out with a swiss ball? A swiss ball and outer thigh lifts are an essential part of toning your legs and strength training. This fitness how-to video demonstrates how to target the outside of your thighs with outside thigh lifts. Learn about muscle training and exercises in this video workout.

Software needed: Voodoo motion tracker, virtual dub and blender

First of all you have to understand that this exercise is very versatile and you can actually target different areas of your chest just by twisting your wrists. First of all lie down on the bench and hold the dumbbells in your hands. You can do this upper chest exercise to build your upper chest muscles using dumbbells. Now bring your dumbbells down and then again take them up. While bringing your dumbbells you have to twist your wrists towards inside such that your palms are facing away from...

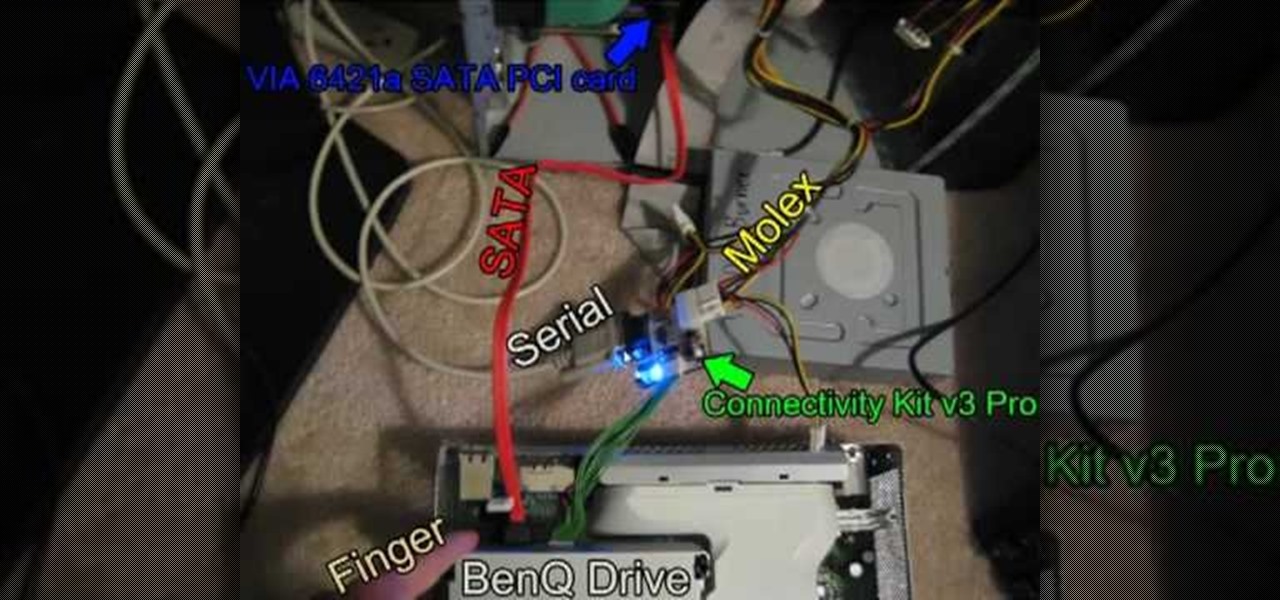
In this Video Games video tutorial you are going to learn how to flash the Benq VAD6038 Xbox 360 DVD drive. This video will show how to do this with the connectivity kit and the jungle flasher. You will need a compatible card for this. VIA 6421a SATA PCI card is probably the best card. Install the VIA card and make the connections as shown in the video. Before you power on the connectivity kit, install the port IO 32 drivers and also the USB drivers for the connectivity kit if you are using U...