Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road
Many marketers are NOT using this powerful strategy to get free traffic and increase their brand exposure. It's as simple as signing up for a free Gravatar account and commenting on blogs in a similar niche. See some good examples and some bad examples...

In this clip, learn how to tie up your bait like a pro. You will get step by step advice on tying a traffic jam trico cluster for flyfishing. If you would like to catch the big guys, you will need to use this tutorial to get started.

To do a hippie jump on a skateboard, first find a good hippie jump target. A good target is something that your board can easily fit under. Approach the target rolling at a comfortable speed. When you are near the target, jump straight up so your skateboard continues rolling under the target. You will then land on your skateboard on the other side of the target and roll away. Make sure that you don't jump forward because it will cause your skateboard to roll backwards and you will not be able...

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).
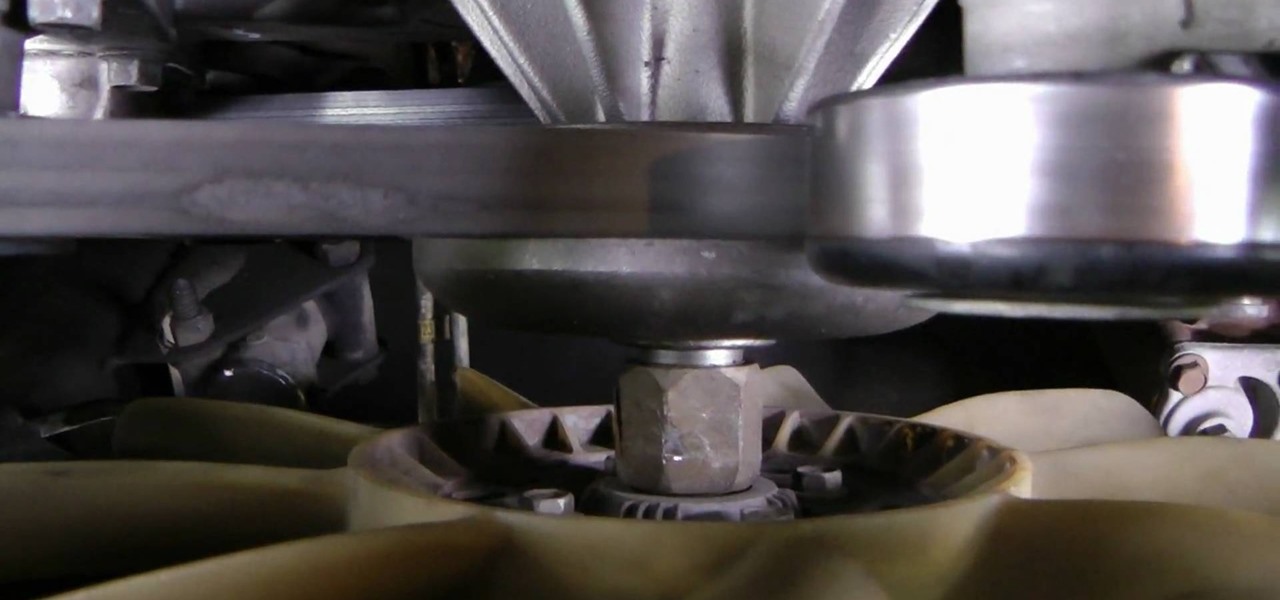
If your car overheats in traffic but not on the highway, you may have a broken radiator fan clutch. In this video you'll learn how to find and fix this problem on a truck, with special consideration for the massive size of such vehicles.

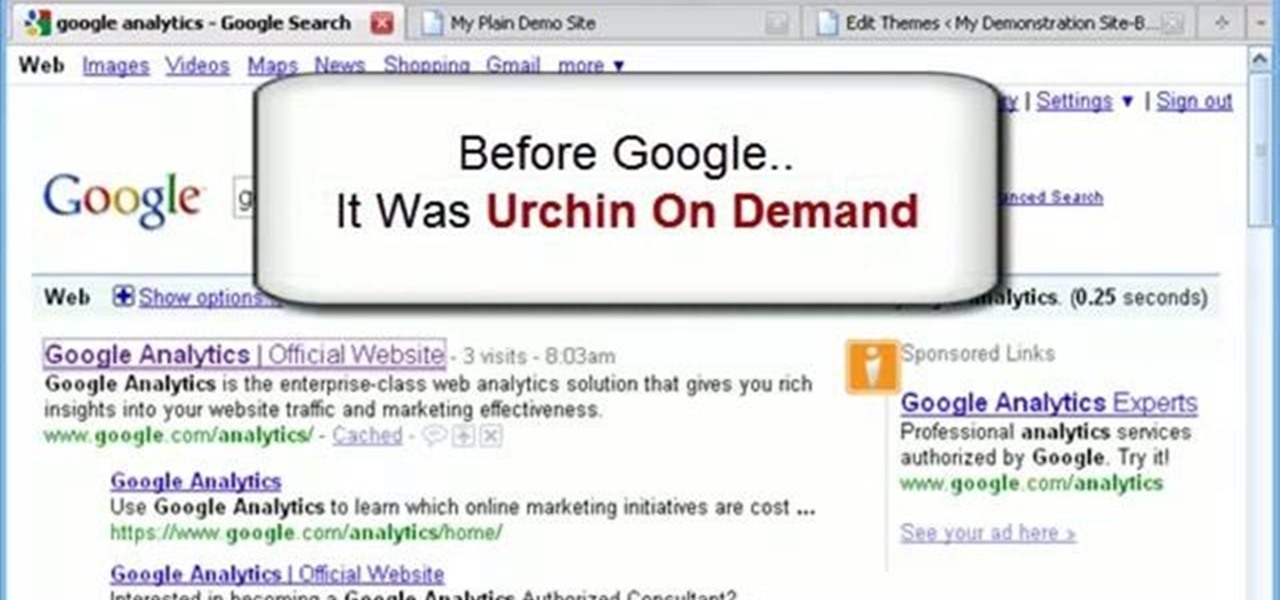
Google Analytics is a state of the art barometer of how a website is doing. With this program you can measure traffic, get statistics and anything else you would like to know about your page. This free service is especially useful to business owners and others who depend on site traffic to stay afloat. So, whether you need it for business reasons or are just curious, check out this clip and get started with Analytics.

This instructional video shows how change traffic lights from red to green, using science, and without actually having to know anything about magnetic fields or properties! Save gas, time, and frustration in your car and during your commute! Works great! See the test results! Yay for Kipkay! The trick in this video hacking tutorial will teach you how to get green lights on your bike or motorcycle that is too small or light to trigger the traffic light.

The Recon character class in Battlefield Bad Company 2: Vietnam is a thinly veiled sniper, and utilizing their target-spotting functionality is key to effective sniping in this game. This video is a complete guide to effective Recon play, teaching you about all your abilities, guns, and how you can spot targets to make yourself much more effective from much further away.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

If you exceed your monthly mobile data limit, your cell phone bill can skyrocket pretty quickly. This is why a lot of people vigilantly monitor internet usage and even uninstall apps that use too much background data.

One of the best ways to increase traffic to your web site is to participate in social media. This video will show you how to optimize your social media posts so that they generate the most interest in your site and attract the most visitors.

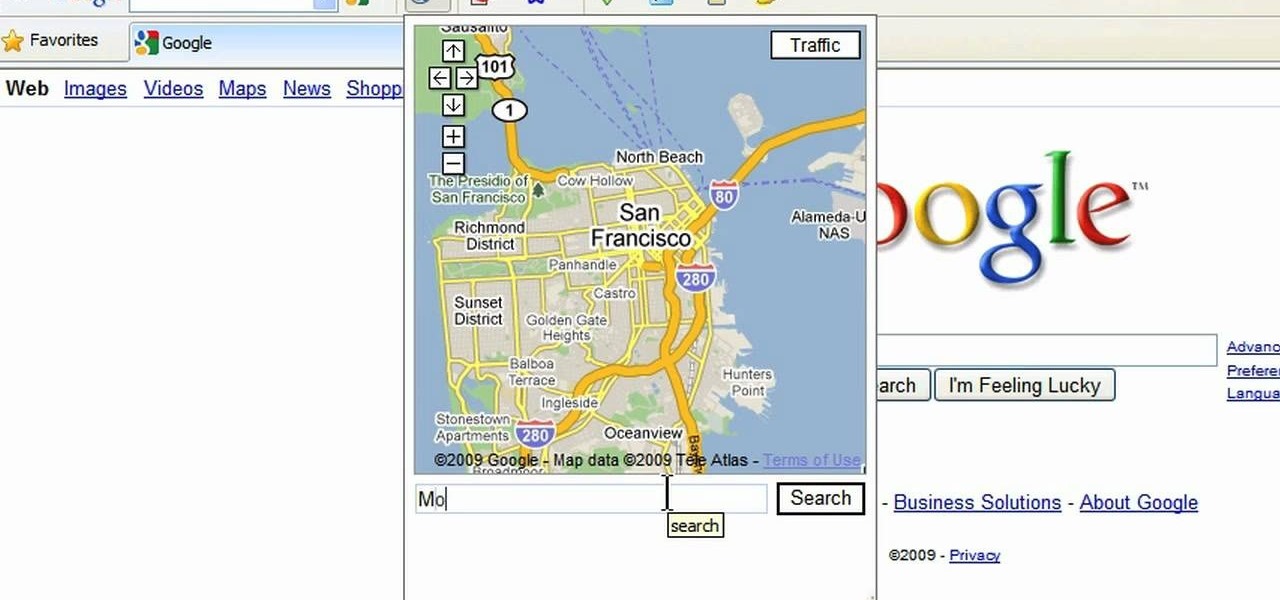
This is a video tutorial in the Computers & Programming category where you are going to learn how to avoid traffic jams using the Google Maps button on the Toolbar. Click on the Google Maps button on the toolbar. This will bring up the maps window. Here you type in the area in the search box, for example, "mountain view, ca" and click 'search'. On the next window click on the 'traffic' button and the map will then show you the roads that are clear of traffic jams in green color. There you go!

This video is a tutorial on how to ride a bike in traffic. The first rule is to obey the law. You would need to follow the laws of traffic as though you were driving a car. If there is a bike lane, use it. It is not a good idea to use the sidewalk as that is reserved for walkers and runners. Ride predictably by signaling your turns. The video tells the viewer which side of the road to ride on, and also provides tips. He also discusses how to ride with another cyclist. This is a very informati...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to set up SSH tunneling to securely transmit HTTP traffic.

If you're looking to increase the ranking of your website in Google, and so increase your traffic, you'd do well to at least a rudimentary understanding of what Google looks at when considering the relevance of a web page to a given query. This SEO tutorial offers a cursory explanation of how the Google search robot sees, or spiders, your website. Drive more traffic your website with this SEO how-to.

The silent film era ended long before anyone had conceived of something like machinima, so your machinima movie had better have some talking! This movie will teach you how to use morph target in 3DS MAX to give your imported World of Warcraft characters facial expressions and animate their mouths to make them appear to be talking. You'll also learn how to make your model sneer, smile, and perform other facial actions.

In this Cinema 4D tutorial, you'll see how to create a Target Effector MoGraph which is amazing. With only 4 simple steps, you can create a very special scene. Primitive Object, Cloner Object and Target Effector will be used in this tutorial. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, and to get sta...

Cars are expensive to buy, replace or repair. Check out this video and learn how to avoid the most statistically dangerous parking areas. There is no guarantee that no one will touch your vehicle, but by take precautions you are much less likely to be targeted.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Greetings my fellow hackers.

A shady practice in place by AT&T and Verizon Wireless—and possibly more wireless carriers—was recently uncovered. Outgoing data requests sent from devices on these service providers are being injected with a Unique Identifier Header (UIDH) that allows websites, the carriers, and potentially even government agencies to track your online activity.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

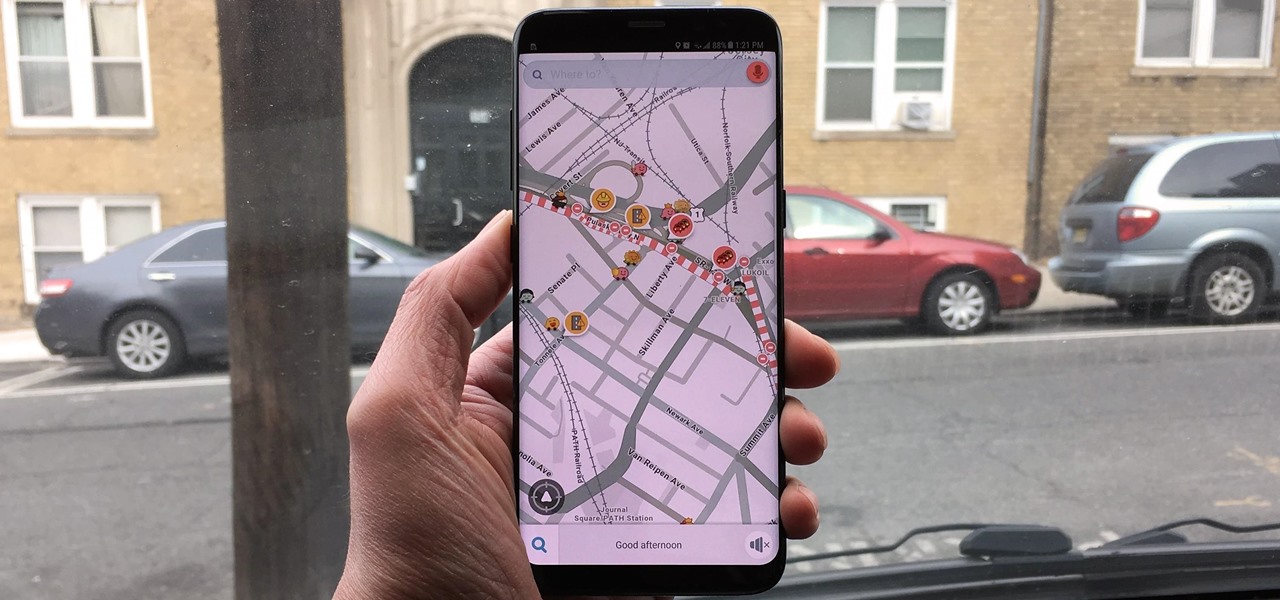
Because it sources a majority of its vital data from actual drivers on the road, Waze is easily one of the best navigation apps to use if you prioritize safety. Benefits such as crowd-sourced traffic data, police trap locations, and road work avoidance, when combined, help you anticipate traffic conditions with unprecedented accuracy and make adjustments accordingly.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to use GPS maps and the compass on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

In this video tutorial, Chris Pels shows how to create a Cross Page PostBack in ASP.NET, where a control on a source page raises a PostBack event to a different target page. First, learn how to configure a Button control to PostBack to a different target page. Then, learn how to get information from controls on the source page with the PreviousPage property and the FindControl method. Then, learn how to use public properties on the source page to expose data to the target page, and learn how ...

Want to perform an unplugged version of Blink 182's "Easy Target"? See how it's done with this free video guitar lesson, which presents a complete breakdown of the song and its chords. While this tutorial is geared toward those who already have some knowledge of the guitar, players of all skill level should be able to follow along given adequate time and effort. For more information, and to get started playing "Easy Target" on your own acoustic guitar, take a look!

Traveling often is super fun, but sitting through 13 hours on the flight from California to Bangkok is killer on your skin, especially since the airplane recycles air and therefore dries out your skin.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

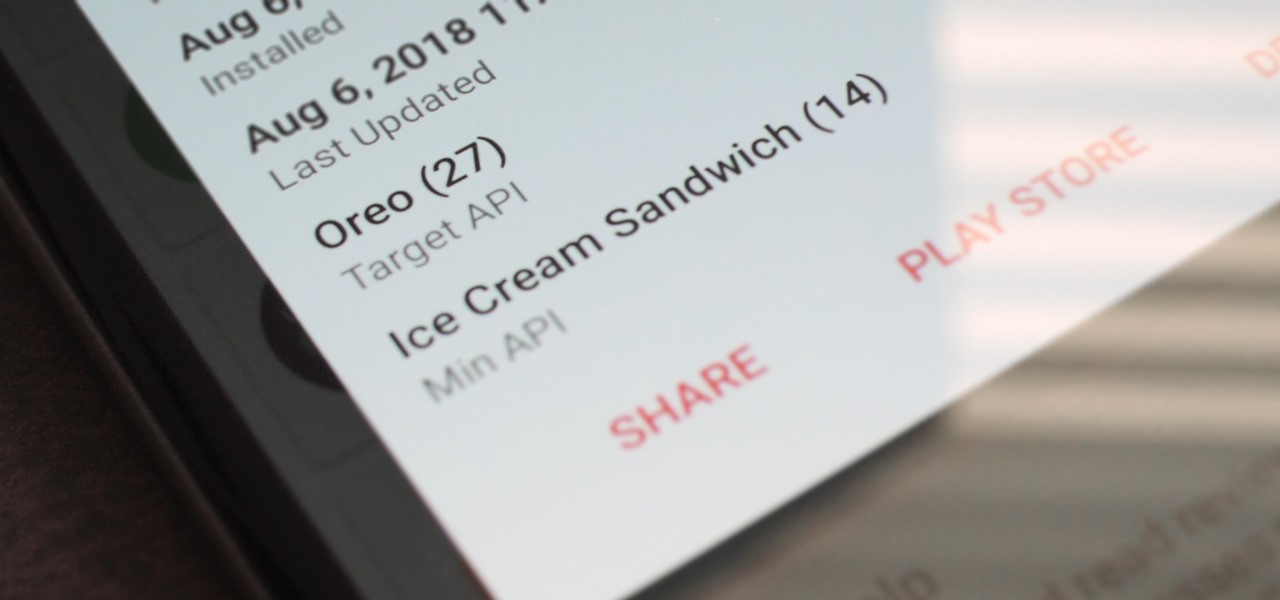
Starting November 1, 2018, Google will require that all new apps and updates to existing apps target Android 8.0 Oreo or higher. This move means the developers behind many of your favorite apps are now scrambling to get their software modernized, while others are considering abandoning outdated apps altogether.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

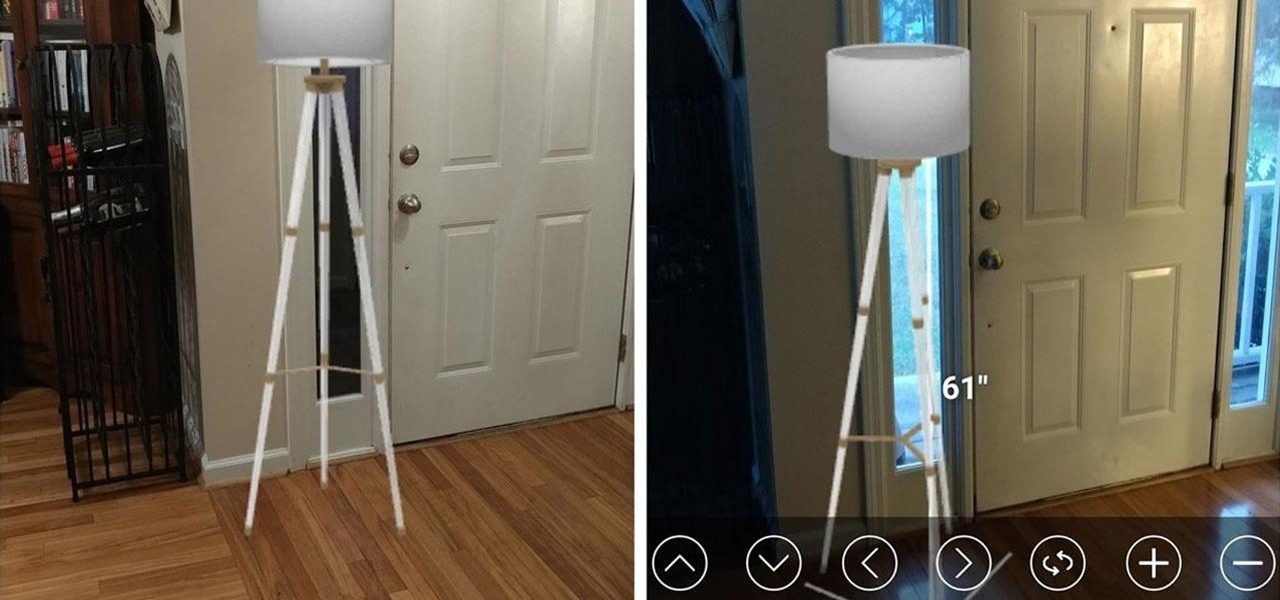
While some companies like IKEA and Lowe's zig towards ARKit to entice shoppers, Target has opted to zag to broader appeal with an augmented reality see-before-you-buy tool for its mobile website.