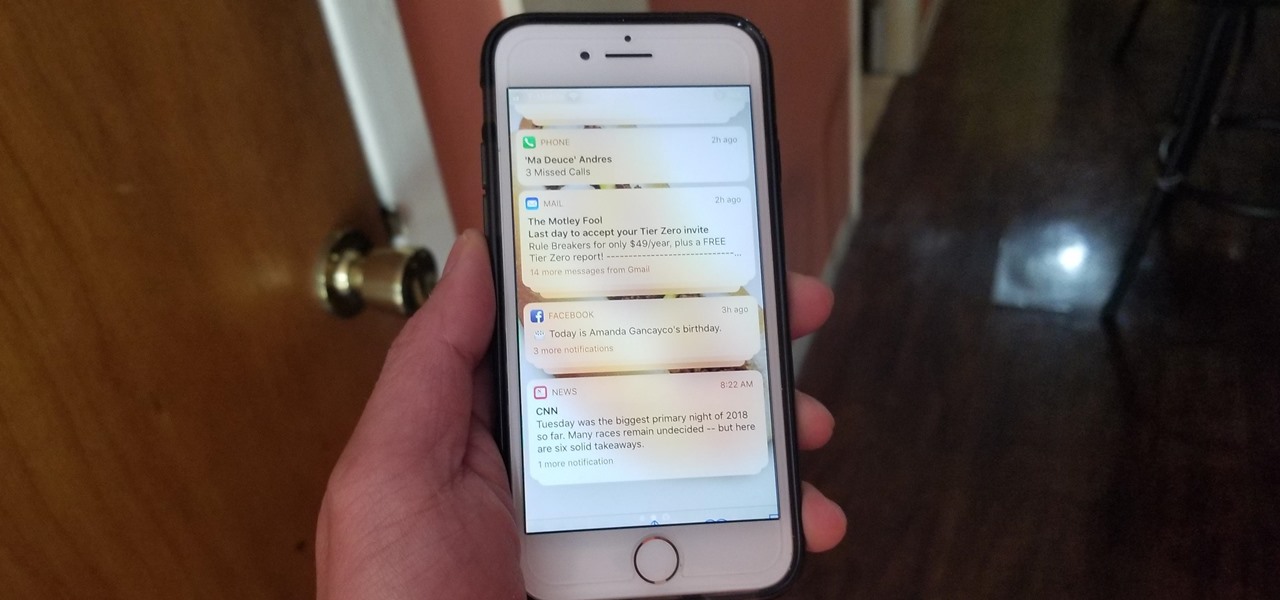
Identifying security software installed on a MacBook or other Apple computer is important to hackers and penetration testers needing to compromise a device on the network. With man-in-the-middle attacks, packets leaving the Mac will tell us a lot about what kind of antivirus and firewall software is installed.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.
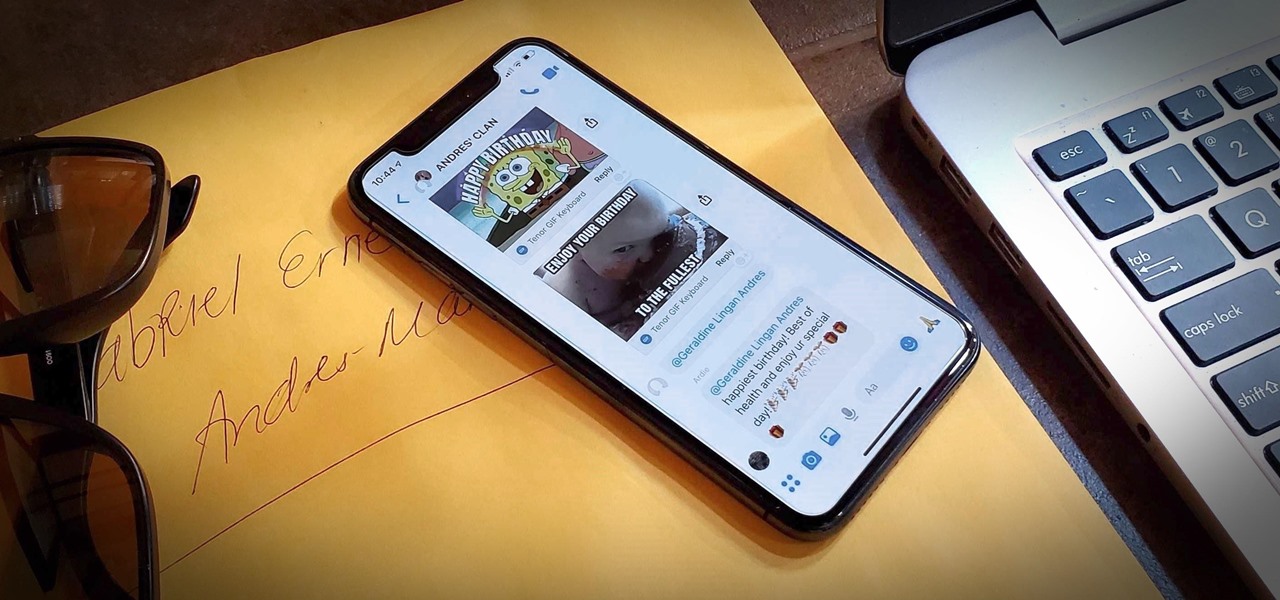
Group chats in Facebook Messenger can devolve into outright noise pollution as people chit chat randomly and bombard you with distracting notifications. Unfortunately, leaving the group outright alerts everyone inside, so if you want to get out of the thread unnoticed, what exactly can you do?
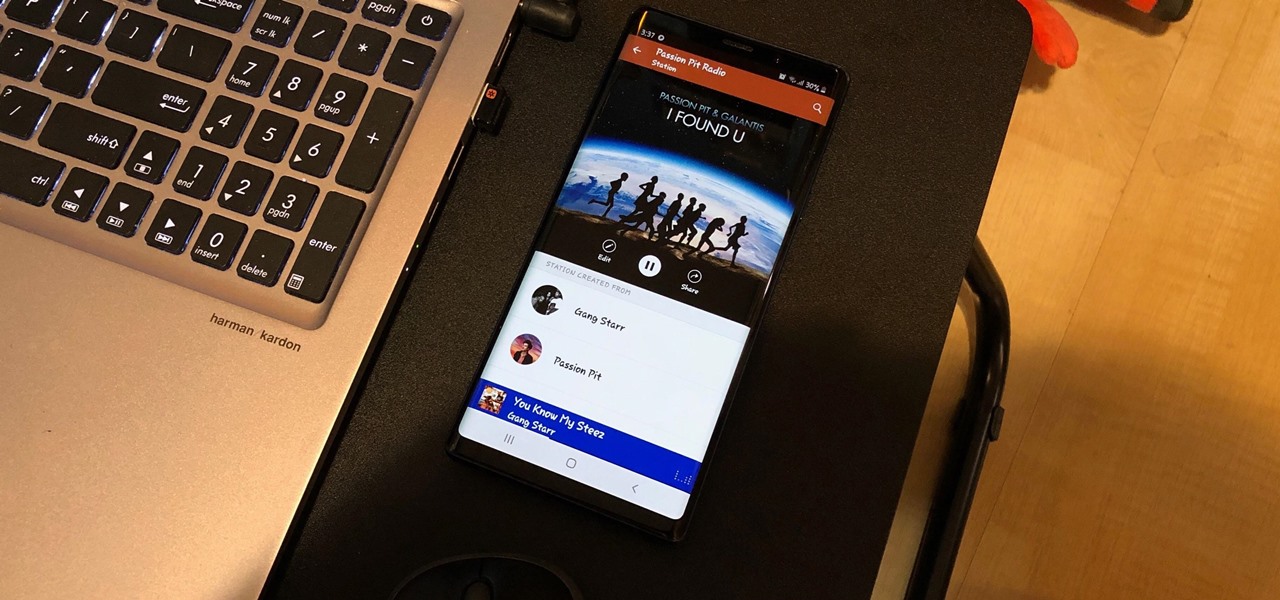
Whether you're out for a drive, commuting to work, or just taking a stroll, listening to your favorite tracks on Pandora takes the legwork out of choosing which songs to play next. After a while, however, you go-to playlist can get repetitive, as the same songs from the same artists seem to play over and over. Luckily, Pandora makes it easy to add variety to your stations in just a few taps.

Cosmetics augmented reality specialist ModiFace appears to be really benefiting from the brand power of L'Oréal, which acquired the company last year.

After getting its start with models of augmented reality planets that serve as targets for augmented reality experiences, AstroReality is diversifying its portfolio by paying tribute to one of the space agencies that made its products possible.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Simulated training can help soldiers and sailors learn how to use their weapons safely, but simulations can sometimes lack the stressful environment of a real firefight.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Apple officially released iOS 12 to everyone on Sept. 17, and while the new iPhone XR, XS, and XS Max will come with the software by default, you have a choice on whether or not to update your current iPhone model from iOS 11. There are a lot of tempting features to want to update right away, but there are also some compelling reasons to wait it out and install at a later time.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

Less than two months after launching its augmented reality platform for casual gaming and shared experiences, Snapchat is ready to make Snappables available to advertisers.

When you first update to iOS 12 on your iPhone, notifications on the lock screen and in the history will be grouped automatically into stacks based on a variety of factors for each app. For example, articles from Apple News will be stacked together based on sites. But you can also change this so that all alerts from a particular app will be grouped in one bundle, not separate ones.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

At its F8 developers conference on Tuesday, Facebook announced new tools and features coming in a new version of AR Studio, including the integration of 3D content aggregator Sketchfab's Download API.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

Moviegoers who arrive at the theater early are no longer a captive audience for the ads, trivia, and miscellaneous content that precede the movie trailers than run before the feature presentation, as the ubiquity of the smartphone has become the preferred distraction for early birds at the theater.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

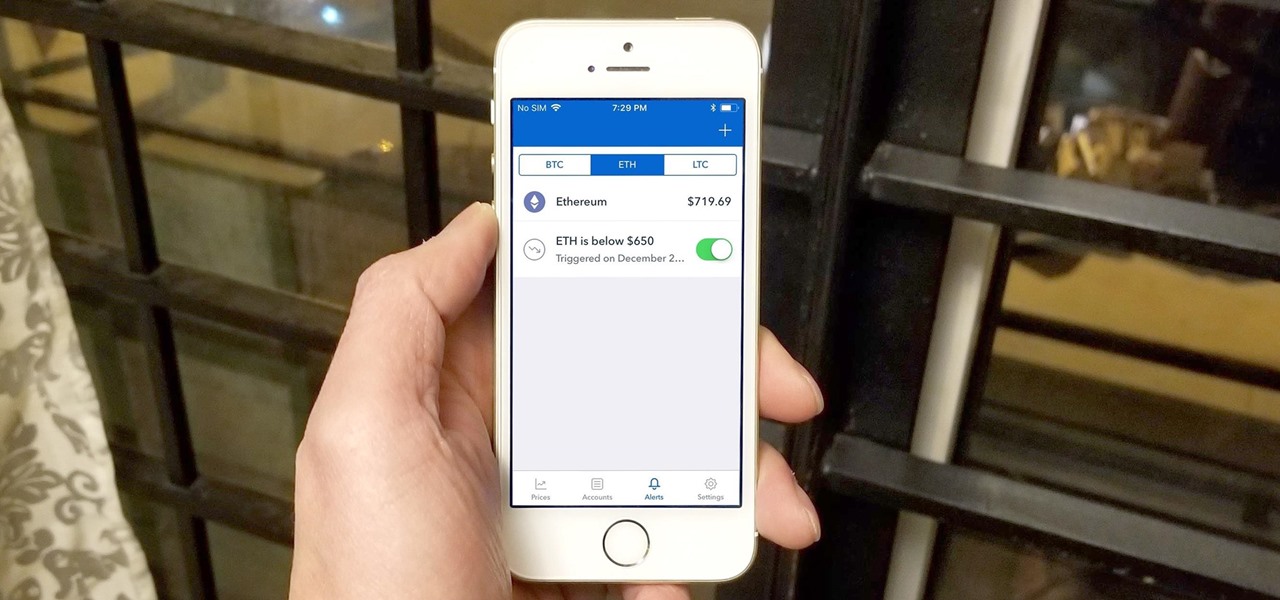
Bitcoin's wild price fluctuations — and by extension, Bitcoin Cash, Litecoin, and Ethereum — can be terrifying if you're new to trading cryptocurrency. Seasoned traders, however, see these price movements as opportunities to maximize their holdings and profits. With Coinbase, you can trade cryptocurrencies more efficiently.

The promise of augmented reality when it comes to gaming is the conversion of the player's real-world environment into a virtual playground.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Though the Microsoft HoloLens' release to the consumer market is still a distant thought at the moment, Ubisoft is preparing for the future with the unveiling of AR video game prototypes.

About a year ago, a certain watershed mobile augmented reality game based on a familiar video game franchise was released into the wild. Today, a number of imitators and emulators have introduced their own location-based games with hopes of similar success.

A new dating advice site, WittyThumbs, launched today that lets users offer advice to others as well as seek it; the site combines that collaboration with advice from designated dating experts.

Another entrant — Aryzon — has joined the competition to be crowned as the "Cardboard of AR." The Netherlands-based startup launched their Kickstarter campaign Monday (May 29) and the campaign has already surpassed its funding goal. The company expects to ship units to backers in September.

4DViews, the volumetric capture company that films actors and performers in augmented and virtual reality for things like movies, TV series, and applications, has just released the app 4DViews: Raise Virtual to Reality, to demonstrate its technology for smartphones.

T-Mobile just unveiled two new services—Scam ID and Scam Block—which specifically target those pestering robo-calls that reach out to 2.4 million Americans every month.

On Wednesday, Microsoft launched a chatbot on social media that learns from conversation, and trolls quickly taught it how to be a shameless, Nazi-loving bigot. Oh Internet, an opportunity for a Hitler joke never slips past you, does it? This Is Why We Can't Have Nice Things

If you're entirely new to smartphones, Android's share menu can seem like a foreign concept at first glance. In reality, it's one of Android's most central and unique features, and with a little experience, it can make your smartphone a lot easier to use.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Welcome to this short and easy tutorial on hacking and DDosing (is that even a word I don't know) anyways lets get started

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.

We share links on an almost daily basis, usually not even thinking twice about it. Whether you're sending a funny cat video to your sister, or letting your coworker know where to go to download relevant files, there are plenty of reasons you might be giving someone a URL.

Link shorteners like TinyURL and Bitly are great for Twitter (or anytime you're limited on space), but they're also great for hackers. It's easy to hide a malicious link in an innocent-looking shortened URL, which increases the chances that people will click on it.

As if you needed another reason to lock down your Facebook profile, the company's sketchy new partnership with data mining firm Datalogix is geared towards giving advertisers more information on what you're doing—even when you're not online. It's just not enough that they can target ads based on your preferences, now they want to know how those ads are influencing your buying habits in the real world.

In 1998, a Beechcraft Baron was following a Boeing 757, with approximately 3 to 5 miles separation. Air Traffic Control warned the Baron pilot three times with the phrase the phrase pilots hear on a regular basis: "Caution. Wake Turbulence".

Catching sight of a hummingbird floating from flower to flower is one of those rare gifts from nature. In this quick and easy guide, use a little bit of science and learn how to make a hummingbird feeder that will attract all the birds in the yard.

Driving around and notice an accident the road keeping you from getting where you need to go? Well, you're in need of a GPS navigation system. Check out this video tutorial on how to Use media functions on a TomTom Go 930 Traffic navigator device. You'll see how to use the GPS system in details and see all of the key features of the Go 930 TomTom, like playing music, listening to audiobooks, and watching videos.

Driving around and notice an accident the road keeping you from getting where you need to go? Well, you're in need of a GPS navigation system. Check out this video tutorial on how to use the TomTom Go 930 Traffic GPS navigator device. You'll see how to use the GPS system in details and see all of the key features of the Go 930 TomTom.