Safe motorcycle riding requires knowledge and skill. Testing two-wheel vehicle operators is the best measurement of the skills necessary to operate safely in traffic because people often overestimate their own abilities.
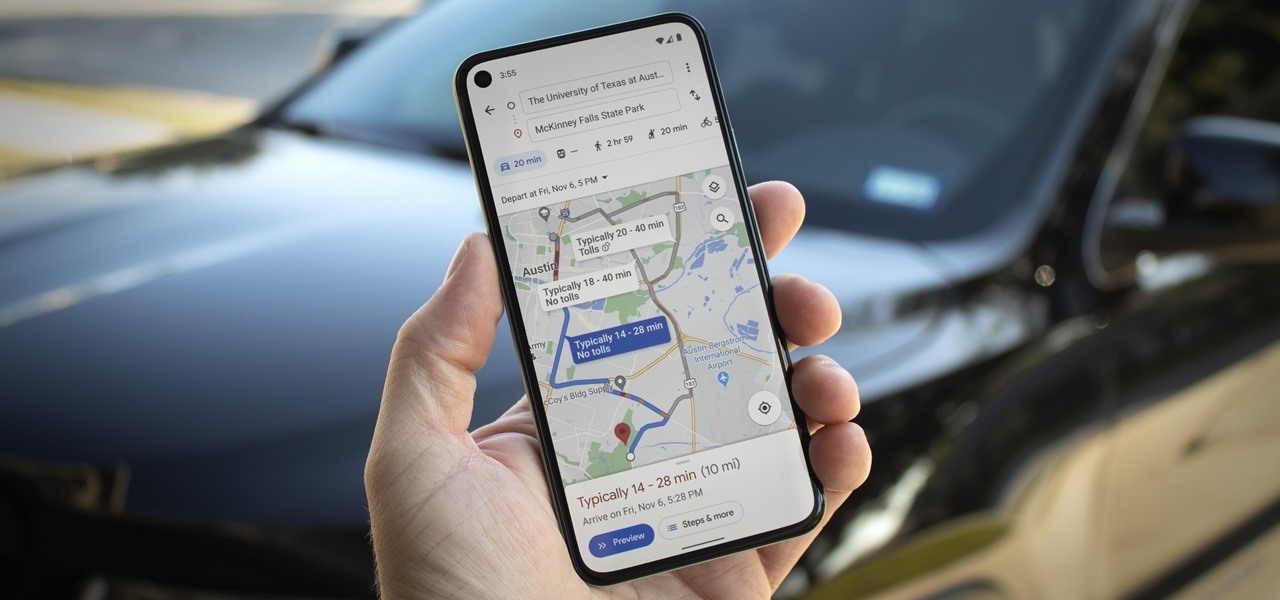
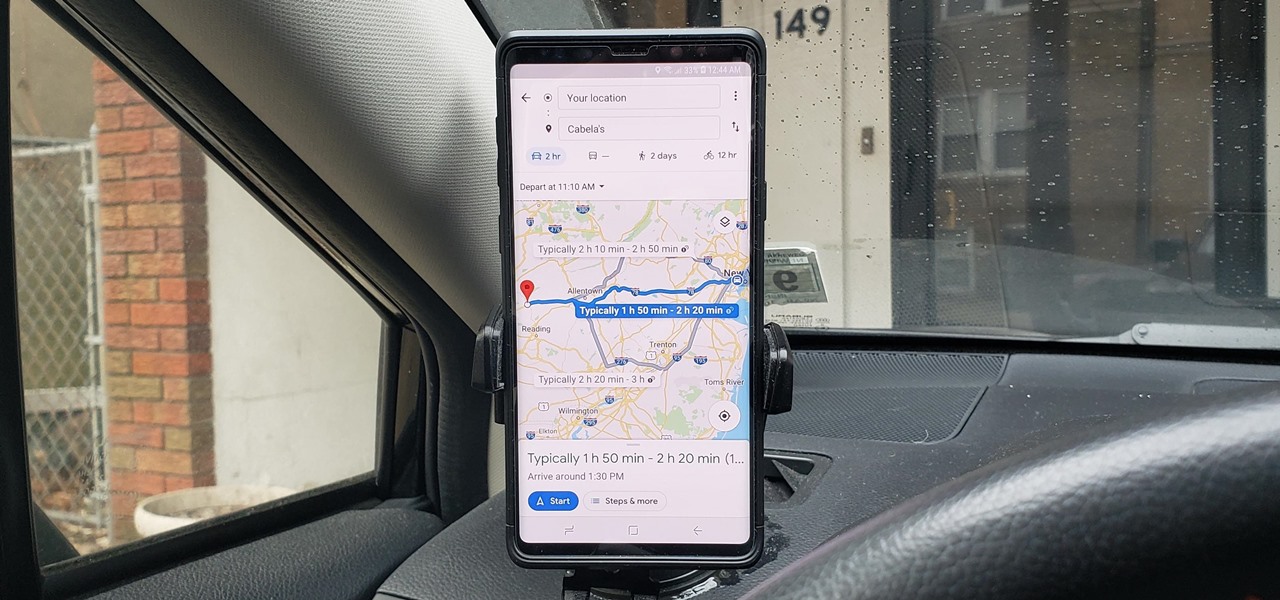
If you're in the market for a new house, how do you know what your commute would be like if current traffic is unseasonably low? Or if you're considering a new job across town and want to weigh the pay raise against the extra time stuck in a gridlock, how do you measure the discrepancy? Google Maps can help.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

As intuitive as Google Maps is for finding the best routes, it never let you choose departure and arrival times in the mobile app. This feature has long been available on the desktop site, allowing you to see what traffic should be like at a certain time and how long your drive would take at a point in the future. Fortunately, Google has finally added this feature to the app for iPhone and Android.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

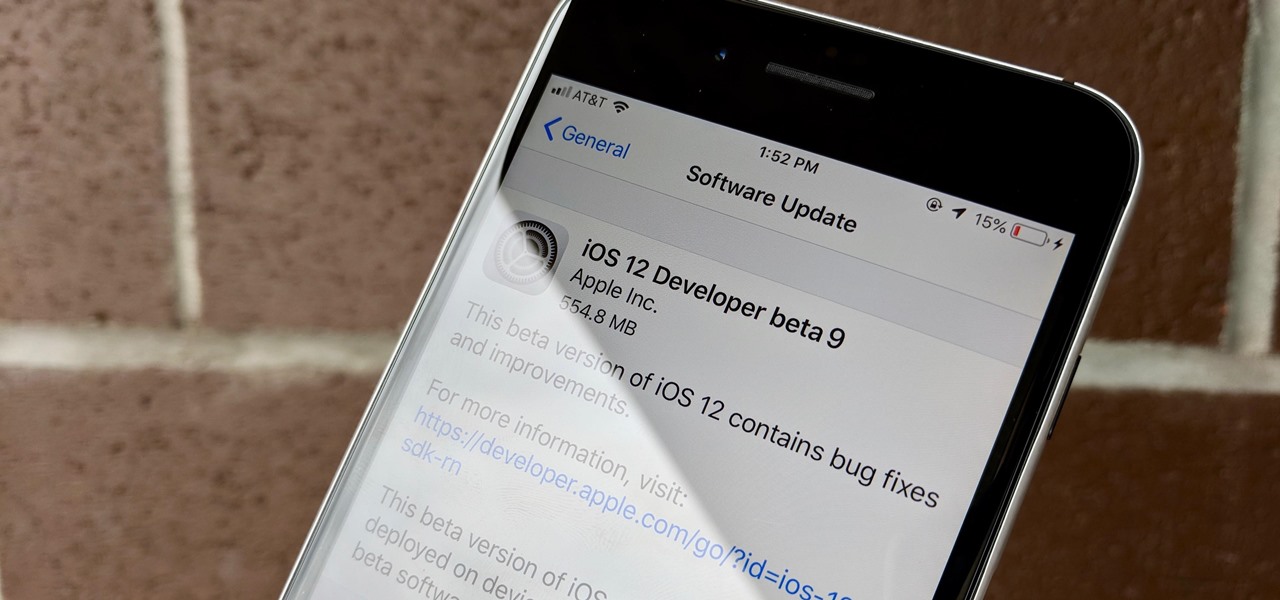
Can't say we didn't see this coming — Apple released iOS 12 public beta 7 on Monday, August 20, the same day it seeded the ninth version of the beta to developers. While the two betas may have different names, public beta 7 and dev beta 9 are virtually identical, so public testers shouldn't feel as though they are missing out.

Apple released iOS 12 beta 9 to developers on Monday, August 20. The company seeded the update just five days after releasing dev beta 8 to testers, itself a quick replacement for the problematic beta 7. This update was followed closely by public beta 7, confirming Apple's new same-day release schedule for both developer and public betas.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Razer just made a big step into the mobile industry by releasing an absolute beast of a smartphone. The gaming-centric Razer Phone tries to provide the best experience for its target audience: Gamers. With that in mind, they created a top-tier device with some of the best specs available on Android. But how does it compare to the current spec champion, the Samsung Galaxy Note 8?

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

Well, well, well. Uber, we knew you were investing a ton of money into creating self-driving taxis and flying cars, but what we didn't know is that you were already testing out your driverless vehicles on the streets of New York City.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Cortana, Microsoft's voice-activated personal assistant, originally launch on Windows Phone, but is now built directly into Windows 10 complete with "Hey Cortana" voice search (take that, Apple). It can help you locate files, set up reminders, control music.

Part 1: What is Popcorn Time? Part 2: What is a torrent?

Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too.

Urgot is a unique champion who can deal out high amounts of damage early in his game, and eventually evolves into a tank/assassin hybrid who can be sent after important enemy targets. Here's a guide for building and leveling Urgot to take advantage of his capabilities to help your whole team.

Lady Gaga is definitely in shape. No one can deny that. But how does she do it? How does pop music's most popular artist stay in perfect shape? How does she get those great looking abs?!?

Is your blog booming or just plain boring? IMaybe it's not boring, but you probably aren't getting much traffic, at least, not the amount you want. If you want to learn how to increase your traffic to your blog or website, this video has information pertaining to quick traffic.

Shane goes into detail on a specific type of boof in which the paddler comes across the drop with angle and boofs into an eddy.

Suspect that your bovine (bull, cow) is pregnant. Well, there's only one way to be sure. Put on a plastic glove and insert your hand into the rectum, with your fingers together. See how to find out if your cattle is pregnant with help of this video tutorial.

Selling stuff at the local flea market sounds easy enough, but it isn't anything like having a yard sale. There's a lot more to it that just getting rid of your junk, and the biggest things are being licensed and having a sales tax number. Flea market vendor may not be your first career choice but, like many, you may find it’s a lucrative full-time job or a profitable and fun sideline.

In some places, it's illegal to ride your bike at night without lights or reflectors, so if you plan on going for a joyride on your street bike, then you need to be prepared to share the road with vehicles and be seen. Appropriate gear and lighting are essential for safety when riding a bike at night.

First of all you have to loose the altitude by taking a circle or two around in the air. On the final turn make a good straight approach to runaway and don't use too much ‘ailerons’ then. Just use the controls ‘rudder’, ‘elevator’ and ‘throttle’. Also watch for the cars or the traffic where you are going to land. Keep constant low ‘throttle’. You have to maintain good ‘idles speed’. You might want to adjust and remember the trim settings. After touch down, don’t pull on elevator. Just cut the...

There's nothing better than being your own boss some say. If you are ready for the risks and the work, take your passion to the next level and start your own business. Learn how to start your own business with help from this video.

Wearing a seat belt while in a car can save your life. Do you know how to adjust and properly use it? Learn how to drive safe and use seat belts properly (Ford DSFL). A professional driver explains how to fasten your seat belt properly.

What do you know about braking in an emergency situation? If you're not even sure what kind of brakes you have on your car or truck, then you need to do some research. Learn how to drive safe and deal with emergency stops (Ford DSFL). A professional driver explains the differences between braking with Antilock Braking Systems (ABS) and standard braking systems.

Driving a vehicle is a big responsibility and road safety is paramount. Improve your driving skills by using your most important tool -- your EYES! Learn how to drive safe and always look ahead (Ford DSFL). A professional driver explains why it's important to look where you want to go, not at an obstacle, when you're driving.

When you're on the road, you want to be in control of your vehicle. The only way to be in control and improve your driving skills is by having good hand positions and correct and comfortable seating position. Learn how to drive safe with a good hand and seat position (Ford DSFL). A professional driver gives this important tip about seating position.

Nobody likes having to stand at the crosswalk waiting for the light to change so you can cross. This seems to happen more times then not these days. A way has been discovered to eliminate this problem with ease. The first thing you are going to want to do is go to the pole that has the button to push for the crosswalk. Once you get there you are going to want to enter a combination of long and short clicks to get the light to change so you can cross. The first combination is going to be three...

Separate restroom hygiene fact from fiction – here's how. You Will Need