The holiday season is upon us, and that means all the big-box stores are competing against each other to offer the best prices on electronics. What was once a 24-hour period of flash deals the day after Thanksgiving has now become a holiday in and of itself — Black Friday is an event you don't want to miss.

If you or someone you're shopping for has a newer iPhone model or an Android smartphone like the Galaxy Note 9 or Pixel 3, they come with wireless charging capabilities. Problem is, they don't come with wireless chargers. But there's no better time to snag one than on Black Friday, and we've found the best deals out there for 2018's holiday season.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Last week, we told you about one of the first pairs of augmented reality smartglasses to get Amazon Alexa functionality, and now we're finally getting a look at how it works.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

Last week, augmented reality startup Proxy42 released Father.IO, a multiplayer game that turns any indoor or outdoor space into a laser tag arena.

While Apple launched ARKit to enable developers to build augmented into mobile apps, Mozilla, the company behind the Firefox browser, is taking advantage of the platform to advocate for browser-based AR experiences.

There are a lot of Android phones out there, and chances are that someone in your life is looking for one this holiday season. Well, there also happens to be a lot of Black Friday deals on Android phones this year. So we've rounded up the best deals taking place on Black Friday weekend to help you save big.

Trendy restaurants are fun, but waiting in line isn't. Too often, we arrive at a location to find a queue between us and our dinner. If only we could know when wait times were down so we could go out at the optimal time.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

Hak5's products get a lot of attention. Popping up in popular shows like Mr. Robot, their hacking tools are bold proof of concepts with space built into the design for the community to add their own tweaks and modifications. On Friday, Oct. 27, Null Byte attended the Hak5 release event in San Francisco to check out their latest devices, including the new Packet Squirrel.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

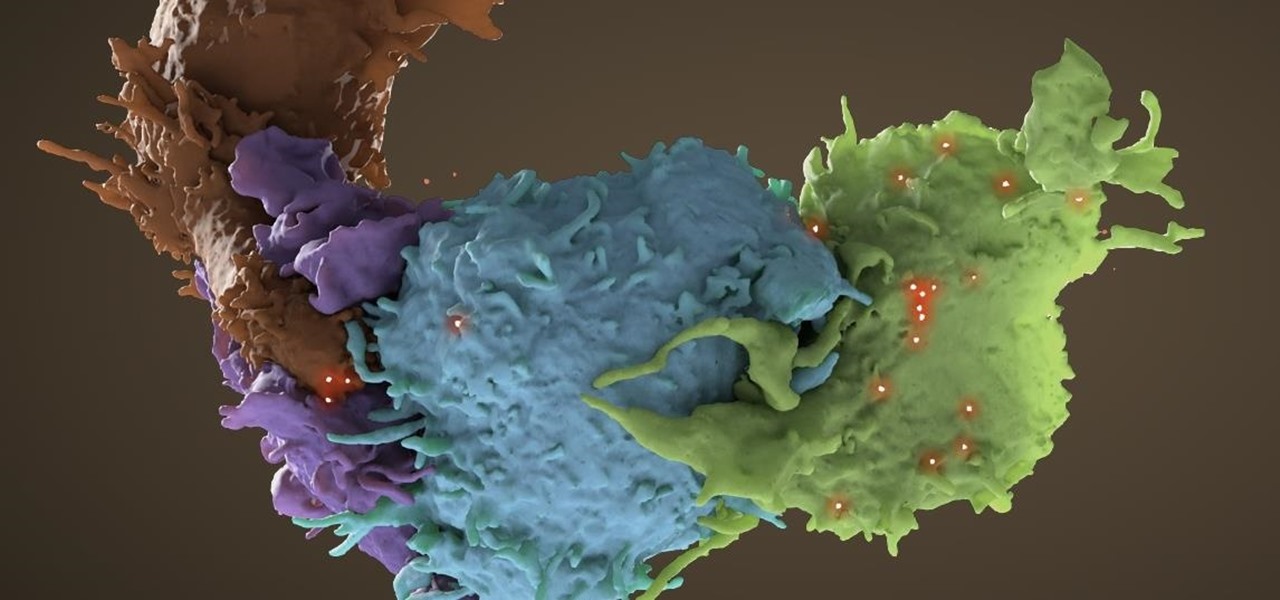
A deadly type of brain tumor and Zika-related brain damage in developing fetuses are devastating brain conditions that, at first glance, may seem unrelated. However, thanks to new research, their paths seem to cross in a way that could benefit patients. A new study has shown that Zika kills brain cancer stem cells, the kind of cells most resistant to treatment in patients with glioblastoma, a deadly brain tumor diagnosed in about 12,000 people in the US each year.

A vaccine against HIV might prevent the disease that we can't seem to cure. Some HIV patients make antibodies that can take down the virus, much the way a vaccine might. But, scientists haven't been able to provoke that type of response in other people. However, in a process that might work in humans, a group of researchers has successfully generated antibodies in cows that neutralize multiple strains of HIV.

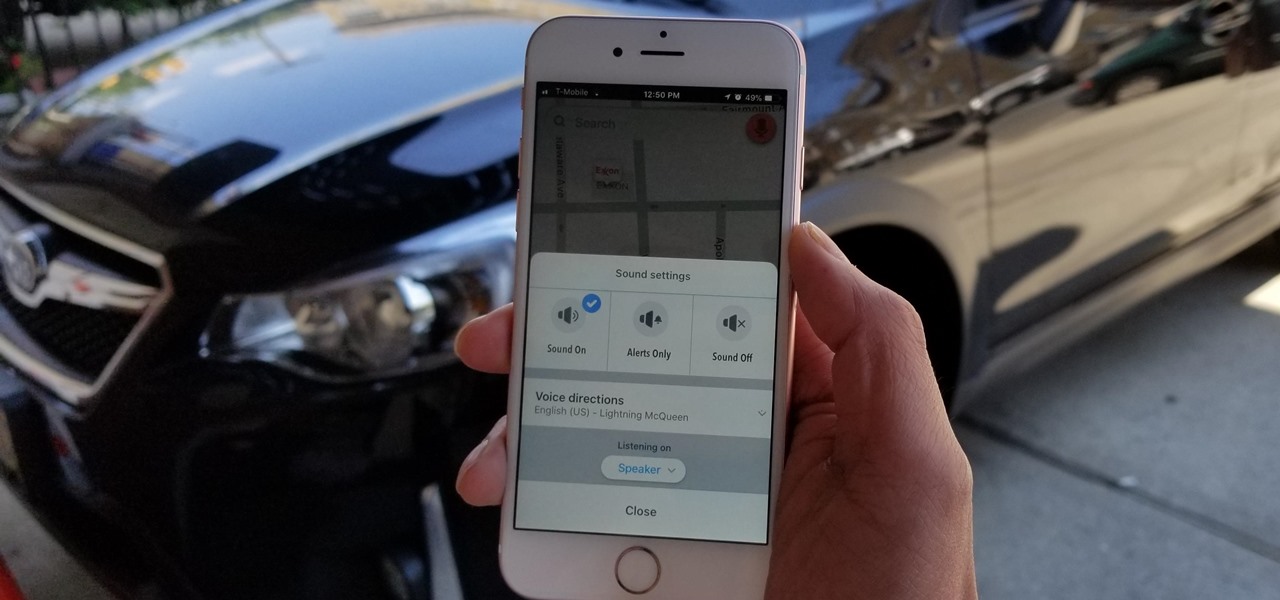
If you've been looking for an alternative to Google Maps, look no further than Waze. In addition to benefits like crowd-sourced traffic data, police trap locations, and road work avoidance, the app even lets you personalize the voices used for navigation and directions.

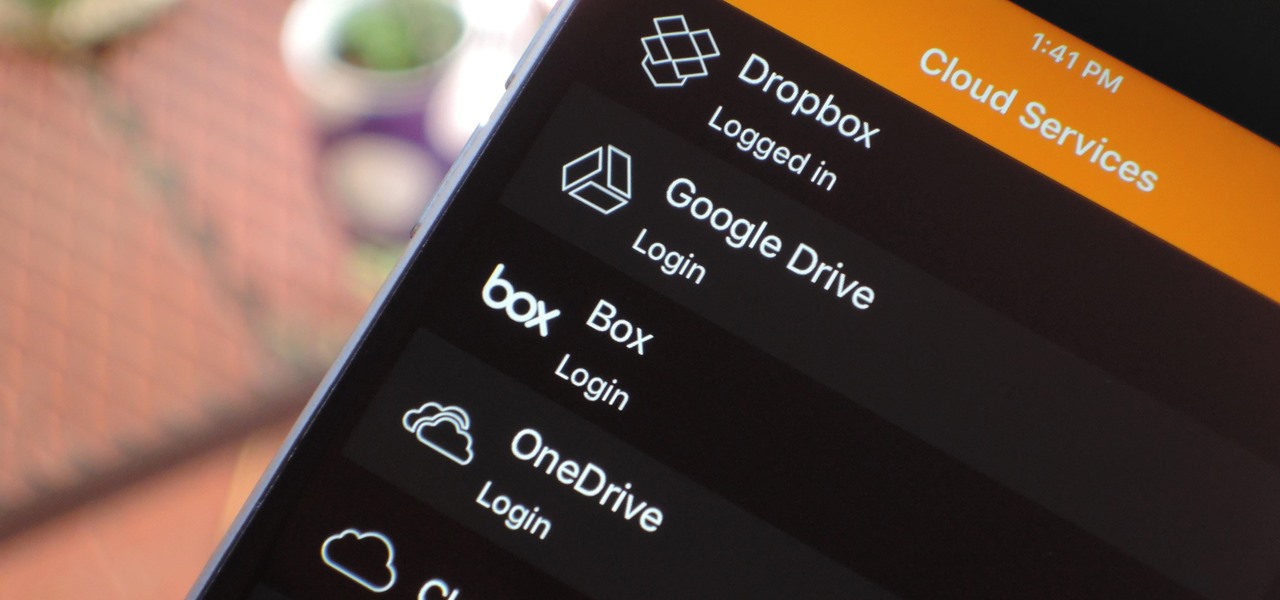
If you have movies and videos stored on Box, Google Drive, Dropbox, or OneDrive, you should definitely be using the VLC app for iPhone. After setting a few things up, VLC will let you stream videos directly from any of these services with a proper video player UI, complete with gesture controls.

Significant strides have been in the race to find antibiotics to treat superbug infections — those caused by bacteria resistant to the antibiotics used to treat them. Now, an international team of scientists has discovered a new antibiotic produced by a microbe found in Italian soil.

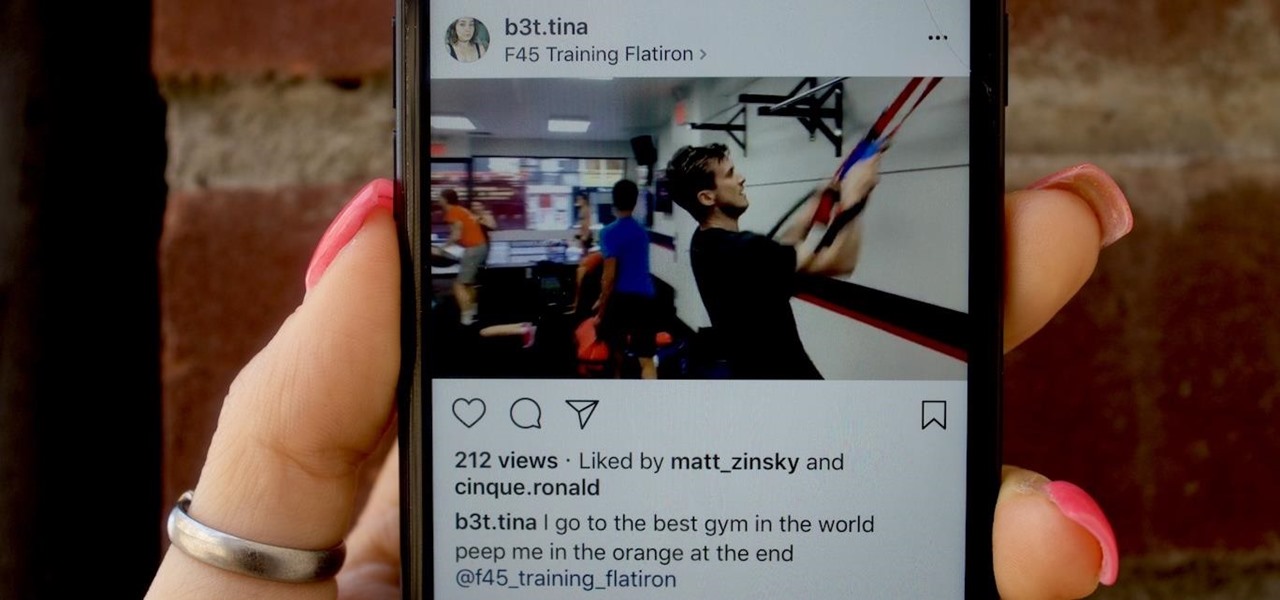
As you all journey along with me on my challenge to become some sort of Instagram expert, let me share with you one hack that is currently helping me out a lot. If you've ever wanted to put a line break in your posts, then keep on reading.

Waymo has done a lot of things over the course of their driverless journey, but their solution to little birdies pooping all over a self-driving car's LiDAR system is definitely our favorite.

You would think most people would agree that you shouldn't use your smartphone while driving. Apparently, most people would be liars, according to recent data from the National Safety Council (NSC) and Zendrive.

While not quite a true self-driving car, Mercedes is gearing to release a vehicle with a plethora of assistive-driving features, some that might have you excited about what autonomous vehicles can do in the future.

As you may have heard, Verizon has jumped on the "giving up users' data to whomever will pay" bandwagon with its new AppFlash spyware app that's all set to be pre-installed on at least one of the Android phones they sell.

At Adobe Summit 2017 this week, Adobe announced they are looking to occupy a new space in the market by combining their analytic capabilities with augmented reality. Teaming up with Microsoft, the company has combined Adobe Sensei software with the HoloLens, reports GeekWire. Together, the tech and software create a new tool for retailers to track their consumers' habits.

Tremendous strides have been made in the treatment and outlook for patients infected with HIV, the human immunodeficiency virus. Treatment with a combination of antiretroviral drugs can keep patients with HIV alive for decades, without symptoms of the infection. The trouble is, if HIV-infected people stop taking their medications, the virus takes over in full force again—because the virus hides out quietly in cells of the immune system, kept in check, but not killed by the treatment.

Both the US and UK seem to be leaning toward requiring level 3 autonomous cars to train their "eyes" not just on the outside world, but even on the driver itself.

A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.

Welcome back to this series on making physical objects come to life on HoloLens with Vuforia. Now that we've set up Vuforia and readied our ImageTarget and camera system, we can see our work come to life. Because in the end, is that not one of the main driving forces when developing—that Frankenstein-like sensation of bringing something to life that was not there before?

The story of Helicobacter pylori is a real testament to the tenacity of medical researchers to prove their hypothesis. It took decades before the scientific world would accept that the bacteria H. pylori caused ulcers.

Findings from a mouse study suggest that the Zika virus infection may have serious reproductive consequences for men.

Earlier today, Alphabet announced that the Self-Driving Car Project has officially graduated from their innovation factory (X) and will now operate as an independent company called Waymo.

HoloMaps, an application by Seattle-based Taqtile, is available for free on the Windows Store. Taqtile, whose Vice President of Product Management was Microsoft's former Director of Business Development, is one of the few partners currently in the Microsoft HoloLens Agency Readiness Program. This interactive 3D map they have created, powered by Bing, offers more than just a top-down view of the world on the HoloLens.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic