Apple's lead marketing tool for the iPhone X, 3D Animoji that you control with your facial and head movements, are once again in the spotlight in a new commercial the company posted on its Korean YouTube account this week.

Location services company Mapbox has added new capabilities to its location-based gaming tool to fend off Google's challenge for the same mobile app category.

It doesn't matter how cool or groundbreaking a particular technology is, if it doesn't offer the promise of big returns on investments, you'll have trouble drawing interest from both Silicon Valley and Wall Street. That's why we're increasingly seeing existing augmented reality players doing everything they can to focus in on revenue generation, which was the message coming from Snap Inc. this week.

The Tesla-riding Starman that was launched into space via Elon Musk's SpaceX last week will miss its Mars target and is instead headed toward a lonely asteroid belt in the void of space. But if you missed the initial launch and would like to get a taste of what Starman is seeing, you can now take a short ride along thanks to a new Snapchat Lens.
In another move that pushes Meta 2 toward becoming a legitimate workplace tool, Meta Company has partnered with Dassault Systèmes to bring augmented reality support to the latter's Solidworks 3D CAD software.

Although expected to be only a modest upgrade over the S8, we can't help but be excited about the Galaxy S9's unveiling late next month. Among the many rumors and questions we're looking to see addressed, one of the biggest queries we have is, of course, with the price tag. We might not have to wait a month for the goods, however, thanks to a new pricing announcement out of South Korea.

Samsung has kept us busy with their Android 8.0 Oreo beta testing program for the Galaxy S8, and most recently, the Galaxy Note 8. As the beta continues to receive new updates, stability has improved continuously, and new features keep on creeping in for both devices.

Razer took to the stage this month to unveil their new flagship phone, fittingly called the Razer Phone. The device is targeted at gamers, but has a list of specs that make it an intriguing daily driver for any user. Its headlining feature is an 120 Hz IGZO display, the first of its kind in a flagship smartphone released in the US. Tonight, Razer officially opened up orders for the new phone on their website.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

San Francisco-based startup AstroReality is putting the AR in lunar with a high-detailed model of the moon that comes to life through an accompanying augmented reality mobile app.

Measuring a room has never been so easy thanks to Apple's ARKit. SmartPicture 3D is known for its quick measurements based on pictures from your smartphone. Recently, they released a video of the company measuring a room using the ARKit.

Screen mirroring app iDisplay has arrived for Vuzix M300 Smart Glasses. With the app installed on the M300 and the companion software running on a Mac or Windows computer, users can mirror or extend the computer's desktop to the headset's display, which is connected to the computer via Wi-Fi or USB cable. The app does not yet appear on Vuzix's app store.

Making a custom location on Instagram is one of the best ways to generate traffic to your account. It gives you that extra uniqueness when it comes to standing out amongst other companies. It also allows people to check in at the same location, further promoting your account across other platforms.

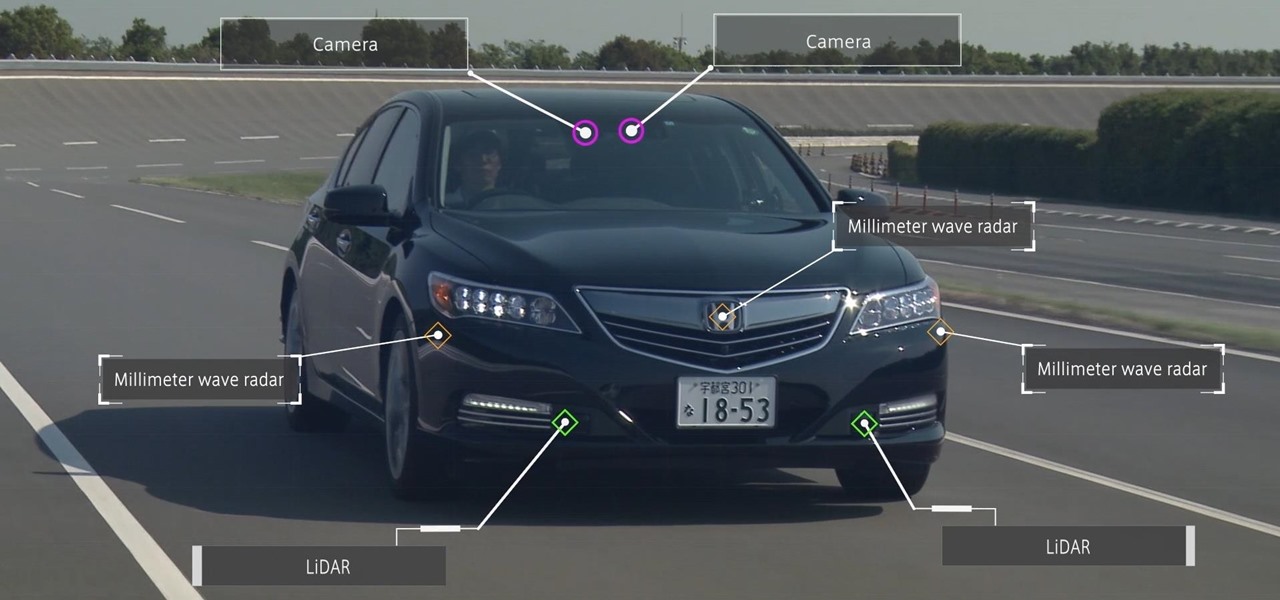
Honda president Takahiro Hachigo has just announced that Honda will complete development of fully self-driving cars by 2025. While the company aims to have level 3 — or conditionally autonomous cars requiring human intervention only in emergencies — on the road in time for the 2020 Tokyo Olympics, these level 4 cars would require no intervention in most environments and thus bring Honda one step closer to producing fully driverless cars.

In an effort to make its services more accessible to users who live in developing countries, Facebook has released a streamlined version of its messenger app. Messenger Lite, at less than 5 MB, is much smaller than its regular 25 MB counterpart and was developed for use on older and lower-end phones. Finally, the app is now available for download in the US.

Who likes security? I like security. I lock my doors at night, and so should you! That's why it's exciting to me that Samsung has just announced its May security update. It's like getting a brand new, top-of-the-line lock for free, but for your phone.

Experts from the World Health Organization just expressed concern for the rising number of measles outbreaks across Europe. Despite a perfectly capable existing vaccine, "immunization coverage has dropped below the necessary threshold of 95%," causing the measles to spread throughout the European region.

Last week it was announced that Waymo, the former Google Self-Driving Car project, had graduated from Alphabet's X innovation center. This graduation had been in the cards for many months with senior members of the project team and X hinting that it would be soon.

In response to the flurry of doubtful headlines about Magic Leap today, set off by an unflattering article from The Information, Magic Leap CEO Rony Abovitz released a short blog post quickly detailing what to expect from the company over the next year. The gist comes down to this: big things are happening in 2017.

In mid-November, Vuforia officially released Vuforia 6.1, which has full support for the Microsoft HoloLens. They also released their AR Starter Kit to the Unity Asset Store, which contains scenes that show you how to use Vuforia features. While I have yet to find any confirmation, I believe it is safe to assume that the AR Starter Kit will work with the HoloLens. I already had a Vuforia tutorial planned for this week, so as soon as I know for sure, I will begin working on it.

In the past, some of Google's Nexus devices have had root methods even before the phones hit shelves. The Google Pixel and Pixel XL are basically Nexus devices from a software standpoint, so why have we gone more than a week since release without a working root method or custom recovery?

It just got a whole lot easier to decide whether or not saving $50 on Amazon's new ad- and bloatware-subsidized smartphones is worth the headache of having to see an advertisement on the lock screen every time you wake the device.

When casting a flyrod, in most cases, tight loops will allow the fly to travel farther, more accurately, and with less effort. To cast these tight loops, the tip of the rod must travel in a straight line path, slack must be eliminated, and there must be a constant acceleration to a sudden stop. The most common mistake is using the wrist to move the rod which causes the tip to travel in a half circle or windshield wiper type motion.

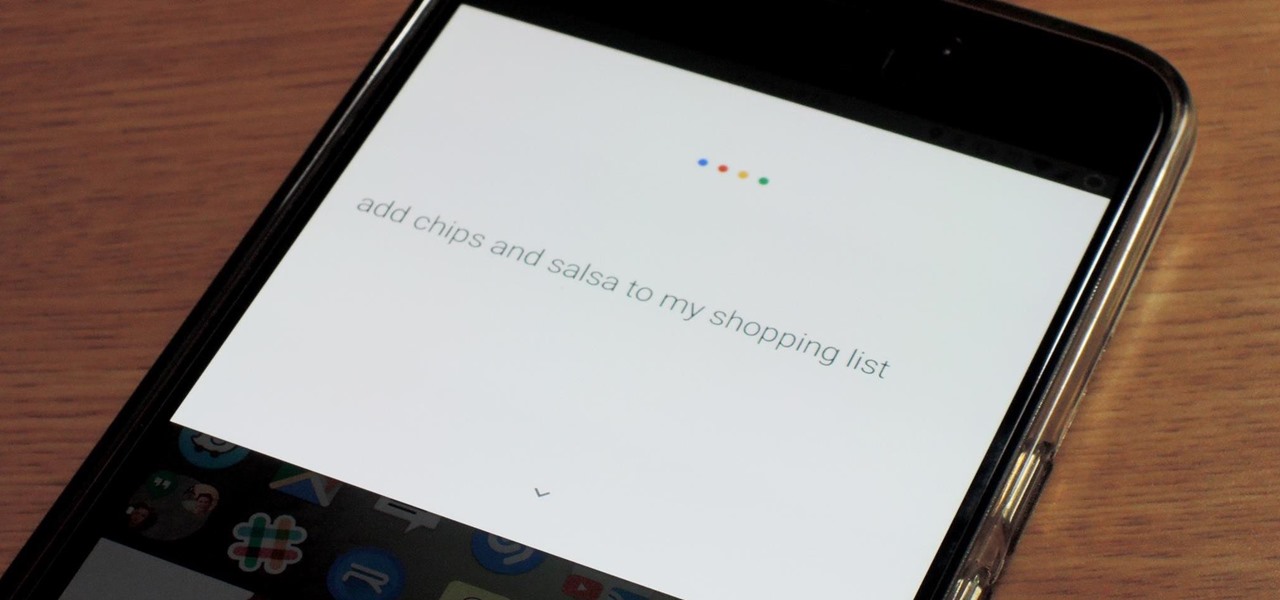
If you use Google Keep, you'll be happy to know that you can add items to lists and even start new ones with "OK Google" voice commands on Android, and it works fairly well. (Hat tip to Reddit user rambantu for finding this trick.)

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

There are a lot of great tutorials on Null Byte using Python to create backdoors, reverse shells etc, so I thought it might be worthwhile making a tutorial on how to convert these python scripts to exe files for Windows victim machines.

Google's Chromecast has been out for almost two years, and I can safely say it has changed the way I use my TV. At first it was a hassle to even get local media to play on it, but now casting has branched out to torrent streaming, which was a real game changer. Unfortunately, most apps only let you stream one video or song at a time, or you can't add magnet links or torrents to a playlist of local content.

It's no secret that Google stores your search history in order to provide you with targeted ads when surfing the web. What's even more interesting (or freaky) is that your Google Now voice searches are also being stored, and you can actually listen to them right now.

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

Well Welcome Back My Fellow Hackers. What is Slowhttptest? You may be asking. Slowhttptest is a Application Layer Denial of Service attack aka an attack on HTTP. You can read more about it here and also download it if you don't have Kali Linux. slowhttptest - Application Layer DoS attack simulator - Google Project Hosting.

If you took a big step back and really looked at the world, you'd see how downright silly our nations look when they put up fences to separate themselves from one another. Creatures big and small roam free while respecting each other's space, but humans create borders and physical barriers to delineate their cultures.

I may not be a well-traveled man, but one thing I've learned from my few excursions across the world is that currency exchange rates are a serious pain to keep up with. With global markets seemingly in a continuous flux, I started looking for anything to make staying on top of them easier, and thats when I found Price Helper.

As much as it pains me to say it, without my phone, I would pretty much be useless. I can barely remember what I had for lunch yesterday, let alone all of the hundreds of numbers in my contact list. That's why whenever I forget my phone at home, I am pretty much stuck having to choose whether I want to be late to wherever I'm going, or feeling completely lost and disconnected for the rest of the day.

Have you ever been a little overzealous in dismissing notifications on your Nexus 5? Perhaps you missed your target and swiped away the notification you meant to read later. Or maybe you simply hit the "Clear All" button when you really meant to tap the button that switches to the Quick Settings tiles.

A good prank requires decent effort, creativity, and impeccable timing. If you're in the office, there are plenty of hilarious pranks to play on coworkers, and for your family and friends, there's everything from toothpaste-filled Oreos, to solid milk, to impossible-to-solve Rubik's Cubes and smartphone-friendly pranks.

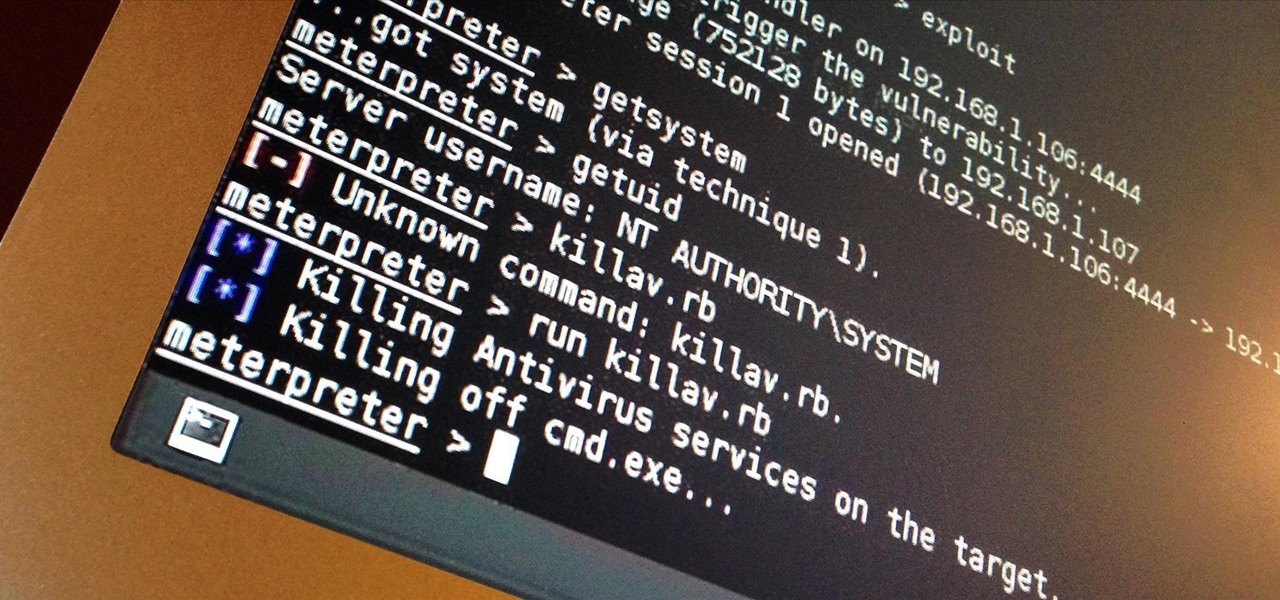
I've done numerous tutorials in Null Byte demonstrating the power of Metasploit's meterpreter. With the meterpreter on the target system, you have nearly total command of the victim.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.