BitTorrent—corporations hate it with a passion, but the people love it. The notorious file-sharing protocol was responsible for 36.8% of all upstream Internet traffic last year, as well as 10.3% of all traffic.

We've all had that awful, sinking feeling when something you've been typing away at is suddenly gone. Maybe you accidentally hit the Back button, lost your internet connection, or your computer crashed, but whatever the reason, losing your work totally sucks. A lot of word processing programs have a built-in auto-save feature to prevent you from losing everything, but most websites and blogs haven't gotten there yet. An extension for Chrome and Firefox called Lazarus: Form Recovery can help y...

While graffiti may never be fully accepted by the masses, it has already become a very large medium for creative artists across the globe, who make mundane and austere cityscapes a little more interesting for the rest of us. Walking past this Banksy stencil on my way to class (at UCLA) made my day. Art like this can cause people to stop and appreciate the otherwise boring and blank walls that surround the city. It can stir up artistic feelings, pensive thoughts, and other emotions stored insi...

It's tough out there on the battlefield, especially when your stuck in the trenches and your comrades are dropping like flies. There's no hope. At least, until the next airsoft battle.

You can do a lot with water guns. Have trouble waking up? Make a water gun alarm clock that (almost) no one could sleep through. Prefer real ammo? Turn your water gun into an airsoft BB gun. And if you don't have one, you can even make your own.

Yesterday, Bryan Clark pointed out a new option on Verizon's privacy settings that gives new customers 30 days to opt out of a data sharing program that gives advertisers information on basically everything you're doing on your new iPhone (or any other smartphone).

The streets of Tokyo are about to get a lot scarier (or more awesome), after Suidobashi Heavy Industries unveiled their latest project: a 13-foot tall, customizable, piloted robot. It's armed to the teeth with a water bottle rocket launcher and a BB Gatling gun capable of firing 6,000 rounds a minute; all for the very reasonable price tag of around 1.35 million dollars.

Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

It takes talent and training to drive a semitrailer. See if you have what it takes to operate one of these rigs on the open road.

Ever a hacker can have their own business that goes beyond cashing in on profitable bug bounties. With the right skill set and certifications, an ethical hacker could build a cybersecurity firm, become a penetration testing for hire, or even just consult on preventive measures to defend against black hats. But learning how to start and grow a business is rarely easy.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

This Black Friday, there are a lot of smartphone deals. Whether you're picking up a new phone or already have one, one of the first purchases you'll want to make is a protective case. And just like nearly every other item, there's plenty of money to be saved on some great phone covers.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

An augmented reality system developed by Lyft might make it less awkward for drivers to figure out who they are supposed to pick up.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Apple may pride itself on its commitment to user privacy and security, but it isn't invulnerable. We now know there is a bug in the latest version of iOS 12 and iOS 12.1 beta that allows those in the know to bypass your passcode and access contacts and photos. This applies to both Face ID and Touch ID-enabled iPhones. Not only do we know about the bug itself, we know exactly how to exploit it.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

The HoloLens team is finally beginning to realize that to truly engage the mainstream, augmented reality needs to make its way out of the lab or factory floor and onto the streets.

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

Accused of violating whistleblower and age discrimination laws by its security director, Magic Leap has taken an internal situation to the US District Court to clear its name of the allegations.

On Thursday, Snapchat opened up its walled garden of World Lenses to the masses of creators with the launch of Lens Studio.

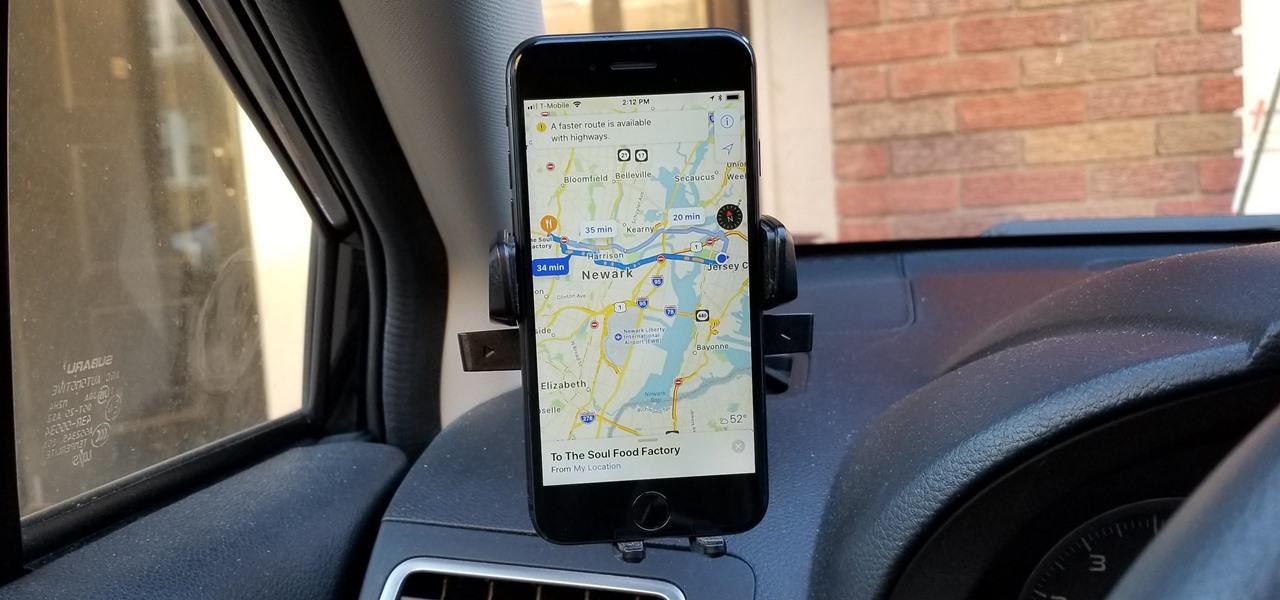
Highways are among the most efficient routes of driving from one place to another. Unfortunately, however, they're also the most used route taken by everyone else resulting in migraine-inducing congestion, especially during rush hour. Thankfully, Apple Maps has a feature that will direct you along lesser known routes that could be faster and/or safer.

With the raw, visceral feeling of zooming around on the open road, it's easy to get carried away when you're out for a ride on your chopper, super bike, or scooter. This increases your chances of getting lost, plus routes can differ slightly for motorcyclists and cagers, unbeknownst to most drivers. Luckily, Waze has rolled out a feature that caters specifically to bikers.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

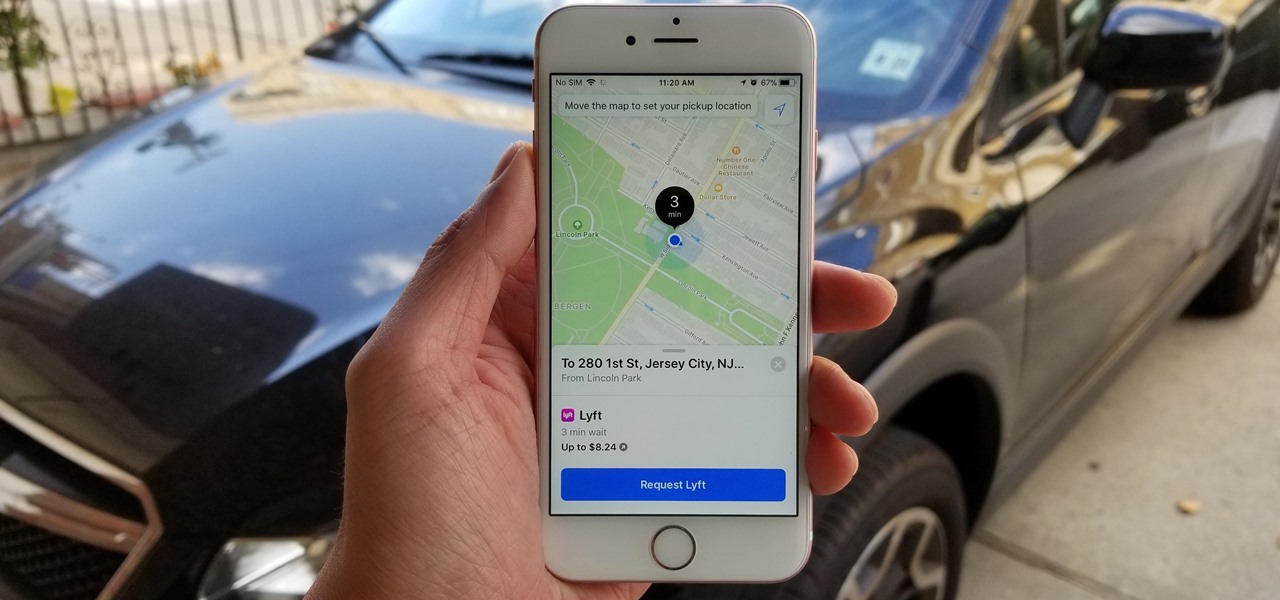
There's no denying the impact ride sharing apps like Uber and Lyft have made on our lives. With fares that undercut traditional yellow cabs, combined with the fact that your ride is just a tap away, these services have become the primary mode of transportation for many folks in urban areas. Thanks to iOS 11, booking an Uber or Lyft has just become a lot more convenient.

If you have a taste for sweets, you have at least one thing in common with mosquitoes. While too much sugar is unhealthy for humans, a new product makes sweets deadly to mosquitoes.

Recently released accident reports by the state of California's Department of Motor Vehicles show humans did a lot of dumb things to cause accidents with General Motors' (GM) Cruise Automation driverless vehicles in San Francisco this year.

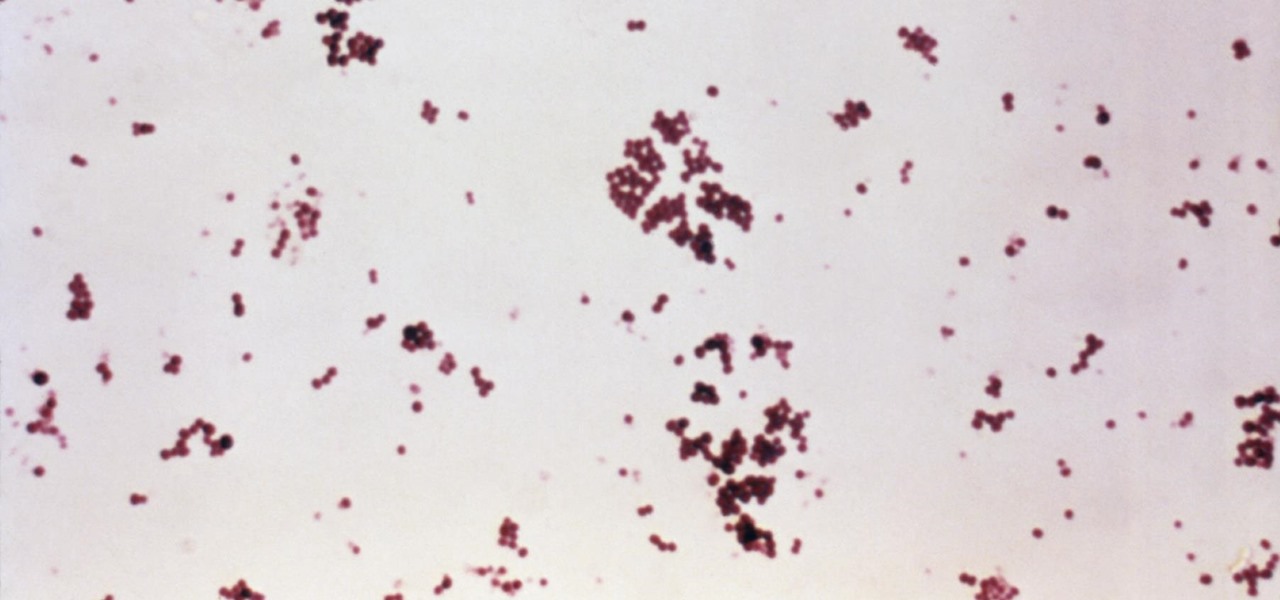
Infections with group A streptococcus, like Streptococcus pyogenes, claim over a half million lives a year globally, with about 163,000 due to invasive strep infections, like flesh-eating necrotizing fasciitis and streptococcal toxic shock syndrome.

Nintendo's Super NES Classic system, a pint-sized version of the iconic Super NES from the '90s, is highly anticipated in the gaming world. The retro system has already met its fair share of controversies and it's been a long journey to preorder. Finally, the Super NES Classic is officially available for preorder, but it's selling out fast.

The Chinese government's tight restrictions on gathering data by foreign firms for 3D mapping, the lifeblood of machine-taught driverless systems, could at least slow down access to the market by Waymo, Tesla, General Motors (GM), Ford, and other players hoping to make inroads there.

France's Groupe PSA (formerly known as PSA Peugeot Citroën) — one of the world's top-10 carmakers — aggressively seeks to take a lead in the rollout of the industry 's first driverless cars, as it becomes the first mainstream carmaker to announce it will launch a Level 3 self-drive vehicle launch by 2020.

Instagram Stories is one of the most flexible ways to share creative and original content with your followers. It allows you to alter text, markup images, and add cool graphics and stickers, along with other fun ways of expressing yourself.

Virgin Wireless, perhaps best known for Sir Richard Branson and all of his antics, is an affordable cellular option here in the US. Virgin customers can enjoy — if that's the right word for it — Sprint's cellular service, at a discounted rate, however, there are usually some compromises for that. Now, there will be yet another compromise for Virgin customers who don't like iPhones — Virgin will now only carry Apple's phone on their network.

Uber drivers do a lot for us. They sit through traffic, make conversation, put on our favorite tunes, drive us however far we need to go, and they work long hours. Some even have to deal with people who may have had too much to drink, which we all know can be obnoxious. So yeah, we'd say that it's about time for Uber to include a tipping feature in their app.

Instagram can be pretty exact when it comes to where you are located. That's why, sometimes, it's best never to geotag your precise location, but a broader area where you are less likely to get, well, um ... stalked?