
News: 'Pilotless' Commercial Ship to Set Sail by 2020
A Norwegian shipping company says it will launch an unmanned container ship within four years, as the shipping industry begins to apply driverless technology to commercial sea transportation.


A Norwegian shipping company says it will launch an unmanned container ship within four years, as the shipping industry begins to apply driverless technology to commercial sea transportation.

In this article, I am most likely going to humiliate myself by showing you all the horrible hashtagging I am wont to do. When it comes to hashtags, well, everybody knows if you desire any chance at all of getting noticed on Instagram, you got to hashtag.
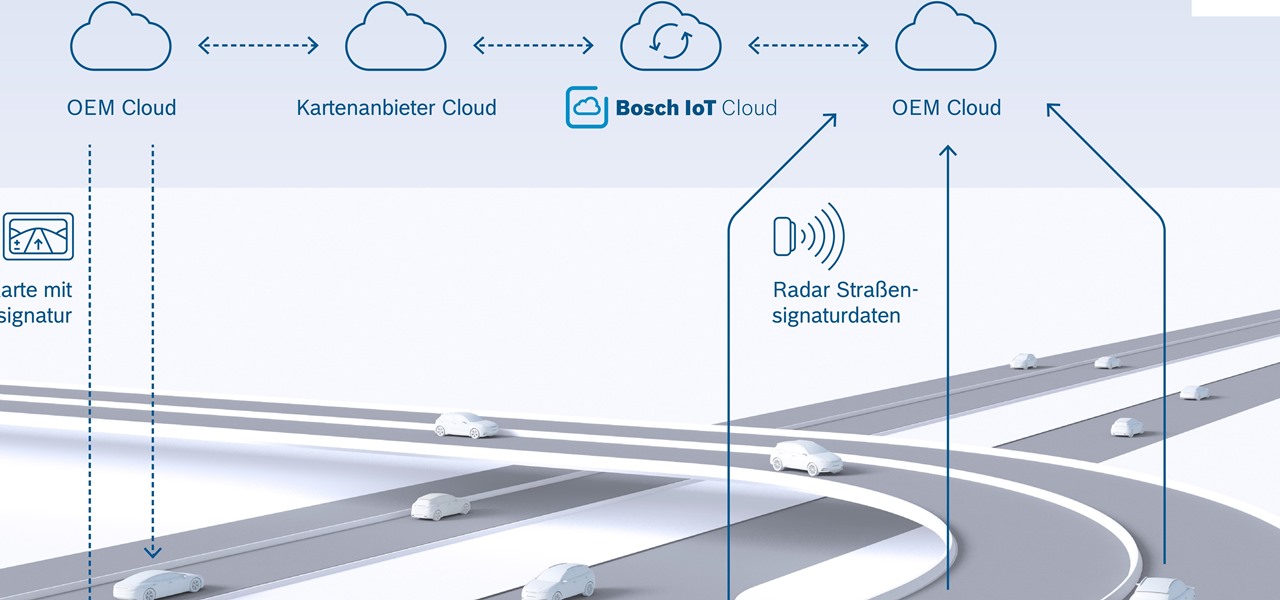
New "radar road signature" technology from Bosch will be used to create maps for high-accuracy self driving. The new map is the first to use radar signals for a localization layer.
New York City may not be the friendliest city, but with the apps Via and Curb now letting users ride-share in the city's yellow taxis, New Yorkers can expect to snuggle up close in the back of a cab next to complete strangers. That's right, get ready to feel the love.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

It seems like everyone wants to be flying without wings these days, and some big players in the autonomous car industry want a piece of that airborne action. Google co-founder Larry Page just invested in flying car startup Kitty Hawk, while Uber is adamant that its own-brand of flying vehicles will be zooming around the US come 2020.

Apple staff will be put through their paces now that the company's "Automated System" for driverless cars is in motion.

It seems nowadays there's no limit to what type of companies are looking to invest in augmented reality. Given both the positive outlook on the future of AR, and its reported benefits for efficiency in employees, this makes sense. Safran, an international corporation with three main sectors—aerospace, defense, and security—is one such company taking the plunge into incorporating AR in their business.

In a race to make self-driven cars mainstream, Intel announced today that they've bought Israeli microchip technology company Mobileye for $15.3 billion, setting the stage for Intel to dominate a large portion of the driverless market.

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.
The Pixel and Pixel XL come with an awesome data-saving feature called Wi-Fi Assistant that automatically connects to open internet hotspots, then creates a secure VPN on your device to keep your data safe.

The desktop browser market has some stiff competition going on, but Opera has always been able to maintain its market share by offering innovative features such as a data saver option. With over 350 million users, it's safe to say folks are appreciative of the efforts being made by the web browser's development team.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Starting in Android 4.3, Google added some code to AOSP that tagged your internet traffic when you were running a mobile hotspot, which made it incredibly easy for carriers to block tethering if you didn't have it included in your plan. But as of Android 6.0, this "tether_dun_required" tag has been removed, which means you no longer have to edit a database file to get tethering up and running.
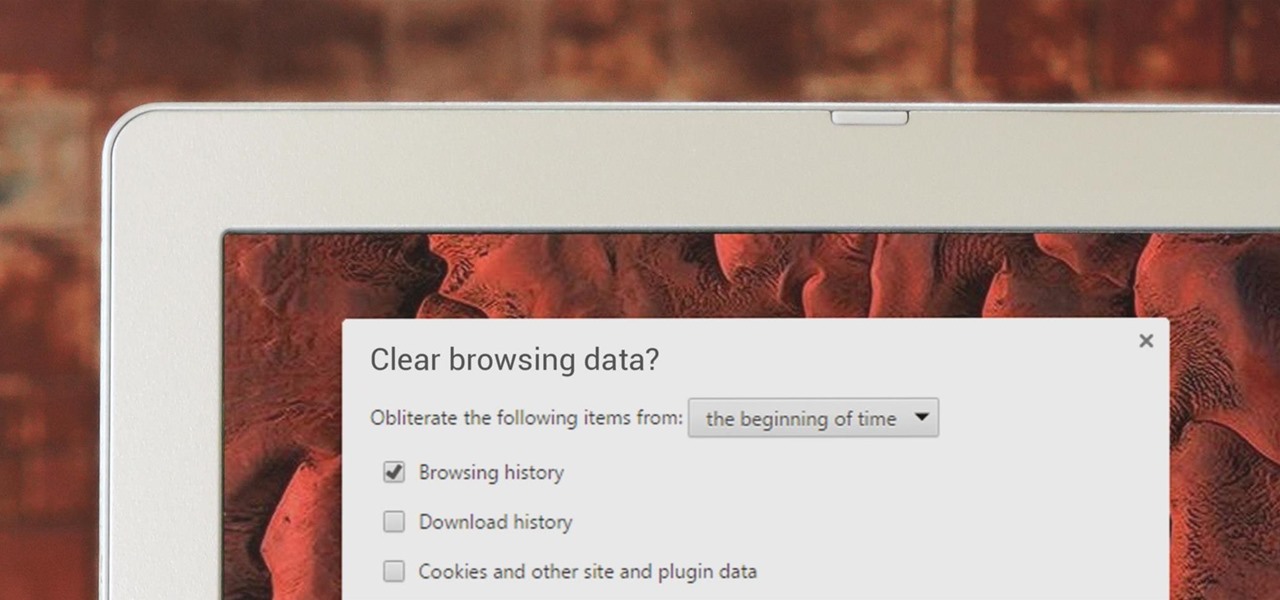
If you've been visiting websites of ill repute, or if you've been Christmas shopping and don't want to spoil the surprise, it would be a disastrous situation if anyone were to come across your browsing history. Visited sites, cookies, and cache can paint a very clear picture of your recent internet activity, and depending on the situation, you may only have a few seconds to delete your history before someone else barges in.

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

If you're just starting out with Android—or smartphones in general, for that matter—there are a lot of little things to learn. One of the first terms you'll likely encounter is "Wi-Fi," which is a wireless internet connection served up by a router in your home, office, or local coffee shop. This differs from your smartphone's regular "Mobile Data" connection, which is provided by your cellular carrier and included as part of your monthly bill.

Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.

Hello, multicolored-hat hackers!

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

The shooting of Walter Scott (who was unarmed) has been dominating the news these past few weeks. Scott, who ran away from police officer Michael Slager after a routine traffic stop, was shot in the back and pronounced dead shortly thereafter. Unlike similar cases where a cop shoots an unarmed person, the police officer involved in this particular shooting is currently in jail, facing a potential murder charge.

With all of the productivity tweaks and usability enhancements that we cover here at Gadget Hacks, it's nice when we come across a unique and noteworthy app that's simply about having fun.

Ever wanted to communicate with another driver on the road, but just didn't know how? Sure, you could flag them down by waving or honking at them, but that assumes that they're in close proximity, that you have a unobscured path, and that they're paying attention. And if you're in a fit of road rage, flagging them down probably isn't the best idea for either of you.
In late 2012, Instagram CEO Kevin Systrom made a sudden and controversial change to his social media service when he removed Twitter Card support.

Yellow buses are beginning to trickle into traffic. Retailers are pushing pens, pencils, and notebooks. Grumbling Facebook statuses run rampant through your feed. Surely you recognize the signs—school is starting. For some, it already has.
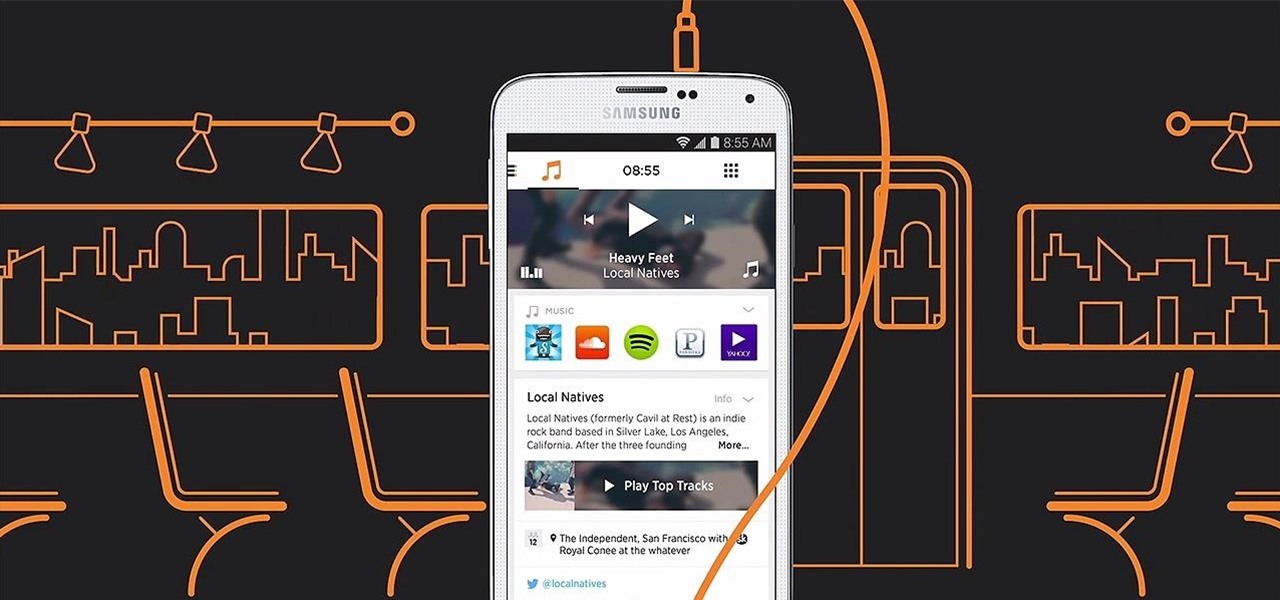
When Yahoo! purchased the home screen replacement app Aviate back in January, many were wondering if the internet giant intended to continue development of the launcher or if the transaction was just another acqui-hire.

T-Mobile continues to make waves in the U.S. wireless market behind CEO John Legere's UnCarrier program. At the latest installment in a series of industry-challenging announcements, Uncarrier 5.0 unveiled Test Drive. The new program is set to allow would-be customers to try out the "latest generation" iPhone for seven days on T-Mobile's network without any financial commitments.

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.
I'll be the first to admit how horrible my memory is, whether it's remembering to take out the garbage or paying a bill on time. That's why I regularly utilize the stock Reminders app on my iPhone; it's definitely compensated for my memory deficiencies.

Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.

Google Glass is all about transforming the world around us with little to zero interaction from the wearer. Much of this is done using augmented reality—a live view of physical, real-world environments that are augmented by computer-generated input in the form of graphics, sights, and sounds.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

Update 1: Evad3ers have released a statement to the jailbreak community, claiming that the safety and security of their users is the most important thing to them and that all speculations about malware being encoded into the jailbreak is simply not true. You can read the full letter over at Evasi0n's site.
Written news was first delivered by an elaborate courier service used by the Pharaohs nearly 4,500 years ago. About 2,300 years later, Romans would post public announcements via bulletins carved in metal or stone. Fast forward 1,600 years to the first monthly handwritten gazette published in Venice, the forefather of modern newspapers, which didn't become commonplace until the early 17th century.

Last month, Alexander Heit drifted into oncoming traffic after being distracted from the road. His sudden correction forced his vehicle to roll and flip over. He was pronounced dead at a local hospital shortly thereafter. All because of a freaking text message. He was only 22 years old.

If you've ever listened to your loved ones sing in the shower or watched a few minutes of American Idol, you would think that the majority of the population is tone deaf. In reality, only about 4 percent of the world's population suffers from tone deafness, or the inability to distinguish between different pitches. Che Guerava, Charles Darwin, and Ulysses S. Grant were all tone deaf.

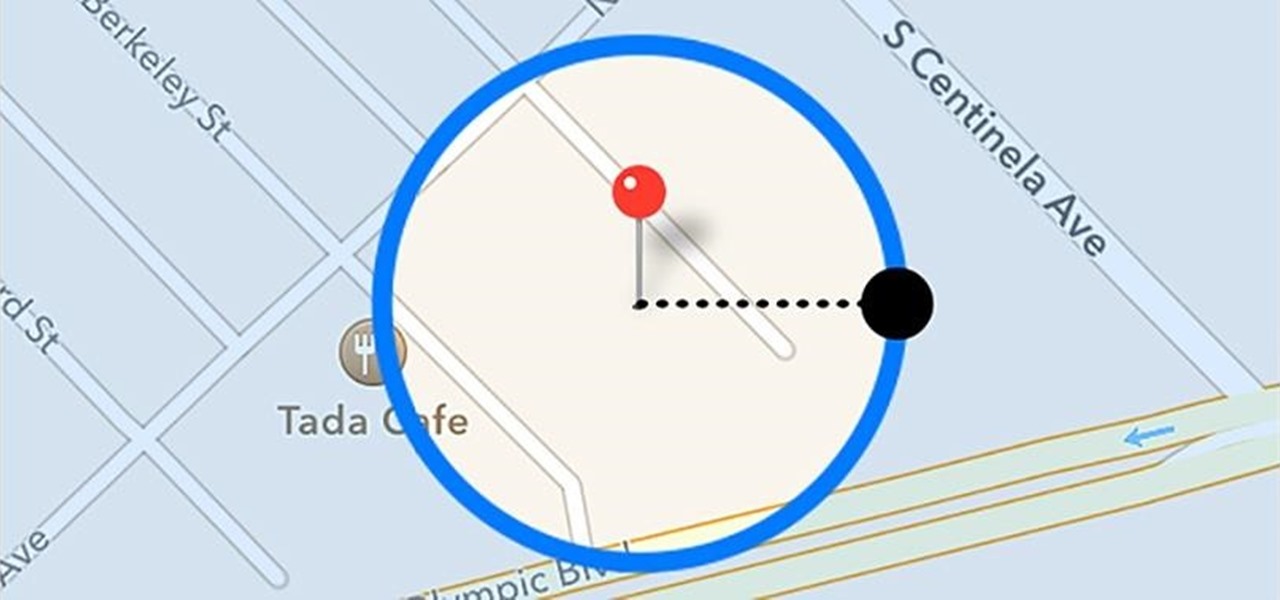
With Google Maps, we can fly from Los Angeles to Tokyo to Paris and New York—all in a matter of seconds. We can zoom in with relative ease and flock around the city of our choice, checking out restaurants, historical landmarks, traffic and scuba divers. Easily the most recognizable and iconic part of Google Maps are the markers that signify all of these locations and point of interests. The iconic markers have already spurred artists to create Google Map inspired art pieces—with one such arti...

As Hurricane Sandy barrels towards the East Coast, 50 million people are expected to be affected in the nation's most populated corridor. The behemoth super storm is a cause for concern, evident by the massive evacuations. The picture above is an eerie snap of the mostly crowded Times Square subway station in New York. Government officials have warned over half a million people to evacuate their homes and head to higher grounds. To help prepare for this storm, the internet has provided severa...