Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

I wonder if Best Buy has any Note 3's for sale?? When trying to figure out when something is in stock, we usually either check online or call the store to talk to someone. If certain products are out of stock the process might be tedious, with having to find phone numbers and calling several stores.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

Running multiple applications at the same time is one of the Samsung Galaxy S3's and S4's biggest advantages over Apple devices, and it's a fact that Samsung certainly harps on constantly in their well-targeted commercials.

Thanks to its dedicated ImageChip, the HTC One has one of the best cameras out of all the smartphones currently on the market. Their branded UltraPixel Camera can take full resolution photos while shooting video, has superior auto-focusing, and provides great overall quality for everything from low-light to action shots.

Welcome back my social engineers/hackarians! Today we'll be looking into a fantastic piece of software, The Social-Engineer Toolkit or just SET for short. SET is designed, Developed and used by several Social-engineers. So... Let's get started!

There are some really talented graffiti artists out there. Some of them are good enough that businesses hire them to paint advertisements, rather than hiring someone to scrub their work off the side of the building.

Search Engine Optimization is important for every successful SEO or blogging campaign. Therefore it is required to be implemented in the correct manner. Google consider many factors while ranking a webpage and it keeps on changing. Some of the common SEO mistakes which you must avoid are as follows:

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

In college, I enjoyed eating, sleeping and making my roommate's life a living hell. My most satisfying prank involved 500 red cups stapled together, filled with water, and strewn across his bedroom floor. He was not happy. To clean up, he had to unstaple each cup, carry it to the bathroom, and dump the water. He was furious, but I was okay with sacrificing our friendship in exchange for a fantastic story that I'll probably tell my grandkids one day. If you're not as cruel as me, there are oth...

UPDATE: A patch to fix the exploit has been released. Download it here.

If you've read anything in the news about Skype recently, it probably hasn't been good. First, there was the controversy over the company listening to and recording users' conversations. Now, there's a new spam tool for Skype that can harvest usernames, see whether or not you're online, and even parse your log files. Image by Lloyd Dewolf

Do you own an HP printer? If so, it may be vulnerable to malware attacks. Researchers at Columbia University discovered that 25% of Hewlett-Packard printers have significant vulnerabilities that put your printer in danger from hackers—even your home. With a budget of just $2,000, researchers Salvatore Stolfo and Ang Cui were able to hack into the printers using remote firmware to install malware, and in some cases even cause the printer to catch on fire. The main issue is with the printer's c...

In today's world of social media, there's really only two powerhouses—Facebook and Twitter. And those of you with Twitter accounts know the power of a Tweet. Getting more followers means reaching more people, but the vast majority of Tweeters are following only a handful of Twitterers themselves. Do you ever wonder why them? What's so special about these selected followed users? Is it worth it to follow them, too? That's up to you, but if you're searching for more people to follow, then it's ...

This video clip shows you how to hit a straight tee shot in golf. There are two parts to this shot. There is the swing path and the face direction. Using a line of golf balls as illustration the demonstrator shows you the path that the head of the club should take as it approaches the ball. Just before impact the head will square up and look in the direction of the target impact. This is called the face direction. There are thus two aspects to a straight shot. The path must be in the correct ...

Need a new iPhone app? Check out Comets and Craters, a new iPhone tower defense strategy game. These ten video tutorials cover all of the gameplay troubles you may have. Steve explains the features and gameplay to help you get the most out of playing Comets and Craters on your Apple iPhone. For those more seasoned Tower Defense players, the video's also provide some insight regarding scoring, upgrades, plus Tower and Enemy capabilities.

At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit.

In this Diet & Health video tutorial you will learn how to check your own blood pressure. Checking blood pressure is a very important part of your personal health routine. Using machines that are widely available, you can easily and quickly check your blood pressure. The target figure will be 140 over 90. The other parameter is the pulse rate. If you are higher than these figures, you need to take a second opinion and consult your GP. Wrap the arm band around the upper arm above the elbow. Pl...

In this video tutorial, viewers learn how to hit a golf ball with a backspin. All golf balls are hit with a backspin, especially with irons. Begin by properly bringing the club backwards. Then return by rotating the hip and release the club with a swing at the target. Finish by raising the club high with a curved shape. The higher that the iron is, the better the backspin will be. Driver clubs do not produce as good of a backspin as an iron club. This video will benefit those viewers who enjo...

Kevin Craft takes us through the steps of throwing a football so that you don't have to be a professional to know how to throw the ball. The UCLA quarterback shows how to hold the ball with one's fingertips. He also goes over how to square one's feet toward the target before actually throwing the ball. A short step movement is followed by a hand motion in the shape of a letter J. Craft makes throwing a football look simple and with some consistent practice, anyone can look like a pro doing it.

This is a video in the Adobe Flash family advances the Flash Action script from 2.0 to 3.0. This video teaches you how to make a flash action script 3.0 button using frames and adding the flash action script coding. Starting with a box and adding text and adding flash coding events, specifically a mouse event and an indication that the button was clicked. Then the programmer adds a variable to the button. She also gives us a hint for the next tutorial which includes a target.

This workout video gives an exercise for you butt or gluteus muscles to tone and strengthen them. Most weight-bearing leg exercises will work out your gluteus muscles to a degree. The same is true with various gym classes, running, rollerblading and ice skating. You can decide to omit targeted exercises for your gluteus muscles from your regular workouts entirely, but it’s good to stretch (particularly if you have a day job which requires sitting on a chair), to strengthen and to tone this mu...

The concept of Metaverse, otherwise referred to as AR cloud, where a digital twin of the real world filled with virtual content anchored persistently for all to see, has been a sci-fi dream of futurists for years and an aim for most tech companies who are serious about AR.

Disney Plus shows WandaVision and Falcon and the Winter Soldier are both streaming hits, but the two series could not be more different in terms of giving fans a taste of the Marvel Cinematic Universe.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

As government officials scramble to contain the new coronavirus outbreak with bans on large gatherings, travel restrictions, and school closures, the rest of us have to worry about how we're going to safely purchase water, toilet paper, groceries, and other household goods during the global COVID-19 pandemic.

One of the main goals of Google Wifi (and Nest Wifi after it) is to make managing your internet connections as simple as possible. A great example of this is how easy it is to prioritize one device and allot it more bandwidth when your network is bogged down with other traffic.

If you thought the news coming from China about the coronavirus might not affect your daily life in Europe and in the Americas, think again.

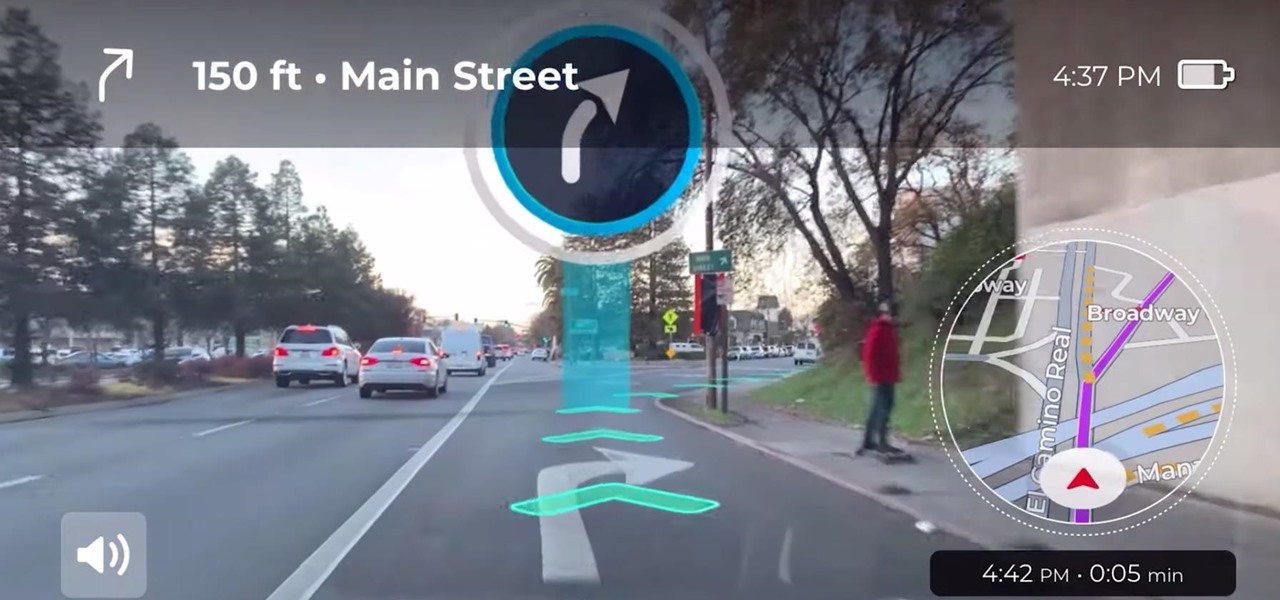
Google pushed a new kind of augmented reality walking navigation to the mainstream last year, and now startup Phiar is hoping users will use its AR app in the same way for driving navigation.

Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

The USB Rubber Ducky is a famous attack tool that looks like a USB flash drive but acts like a keyboard when plugged into any unlocked device. The Ducky Script language used to control it is simple and powerful, and it works with Arduino and can run on boards like the ultra-cheap Digispark board.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

While Magic Leap World gets its share of fun apps for playing with Porgs, watching TV, and exploring the ocean's depths, developers are making a strong business case for the Magic Leap One as well.

They're finally here. Apple revealed the brand new iPhone 11, 11 Pro, and 11 Pro Max on Sept. 10, and despite the questionable names, these are the best iPhone models money can buy. If you're looking to get your hands on one of these devices as soon as possible, there are few important dates you need to know.

The venture arms of Samsung and Verizon Ventures, along with Comcast, are among the strategic investors backing startup Light Field Lab and its glasses-free holographic displays in a $28 million Series A funding round

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

While the technology companies continue to drive forward with autonomous vehicles, Nissan's vision of the future of self-driving automobiles lies in a cooperative experience between human and machine, facilitated by augmented reality.

This week, Next Reality released the fifth and final set of profiles on the NR30 leaders in augmented reality, with this chapter focusing on the influencers in the industry.