Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Looking for a way to speed up the boot time on your favorite programs in Windows? This video will show you a little tweak to make your most-used applications start up in no time. Basically, you just go to the "Shortcut" tab in the program's properties menu. Then add " /prefetch:1" to the end of the target location in the "Target" box. This tweak works on PCs running Windows 7, XP or Vista.
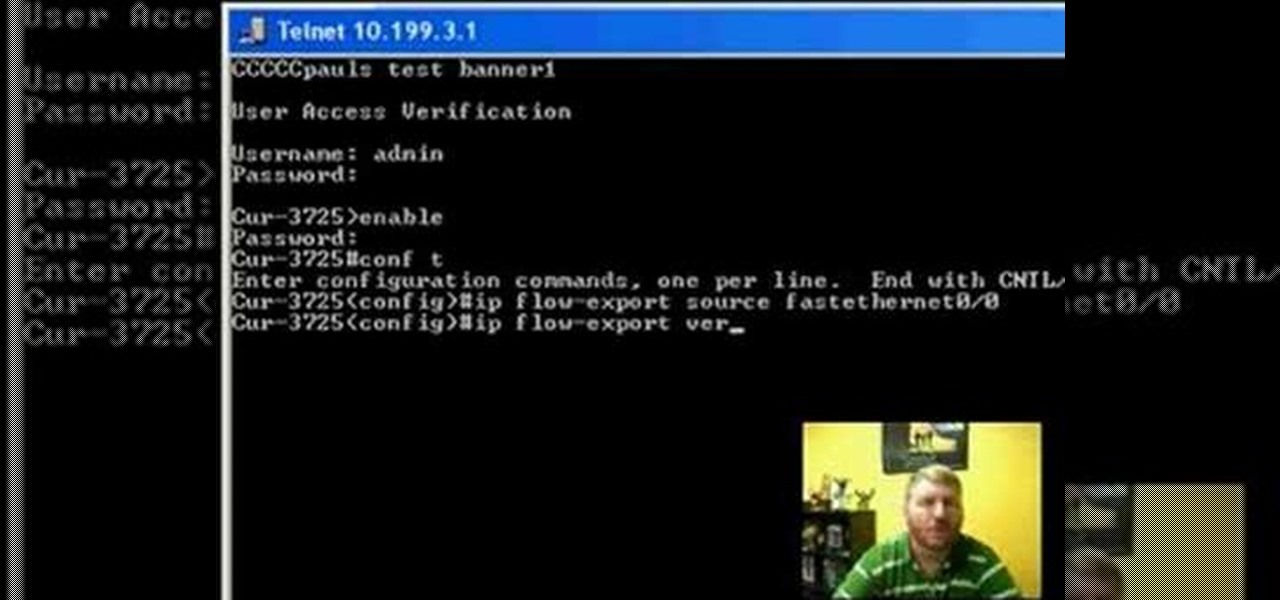
Netflow technology allows you to monitor web traffic to your website - find out who comes to your site, where they're coming from and where they go afterwards. You can configure a Cisco router manually to monitor netflow going through the router.

In this Pets & Animals video tutorial you will learn how to train your dog to perform the "cop-cop" trick. In this trick the dog learns to put its feet on your feet. Step 1 – teach the dog to target a book or a mat with their feet by offering them some treat. You can do this either by appreciating or clicking when both the feet touch the book. The next step is getting the dog to target the book with their feet while they are between your legs. You have to continually reinforce the dog to ma...

Looking to work on your form? Try this free video golfing lesson for size. In short: When putting, to be able to release the putter down the line to your target, the club must travel slightly inside the target line. For a complete overview of how to become a better putter, watch this video guide.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

Consumers are chomping at the bit for augmented reality smartglasses from Cupertino's finest, but one market analyst is saying not so fast, Apple fans. Meanwhile, automotive AR is gaining speed, with the latest milestone coming courtesy of a major investment in waveguides by Continental. And although mobile AR apps have already arrived, retailer Target is taking a different approach. So why is Target tinkering with web-based AR? Answers below...

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

Carriers really suck, don't they? We constantly have to monitor our data usage, even though many of us are on "unlimited" plans, which, in reality, will just be throttled to a slower 2G or 3G connection when we hit a certain download threshold.

This video will show you how to target your audience for Facebook post. You could set country, language, age group, qualification, etc. for watching your post. Watch the video and follow all the steps. Employ the technique in your Facebook account.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

Just because you need to assemble an outfit for work doesn't mean it has to look all boring and aging. As long as you stay mostly covered up and don't pull out your neon-colored cheetah print stockings, you'll do just fine accessorizing and dressing fashionably.

When you are riding with a group or in a trafficked area, communicating with the people around you is essential for keeping all of you safe. This videos will explain the importance of good communication for riders and show some commonly used hand signals that you can use to signal your fellow riders. These will help you avoid obstacles and have the most fun ride you can.

In this video tutorial, viewers learn how to properly shoot and sight in a compound bow. It is recommended that users use a release. Your body should be perpendicular to the target. Hold the bow vertically, and hold it with a relaxed and secure grip. When you are ready to begin shooting, learn a technique that will help you relax and steady the bow. When you draw the bow string back, you should be looking through the peephole on the bow string and where the target and pins come into view. Thi...

In this video, Tom Leese, Director of Instruction at Angel Park Golf Club, gives pointers for your pre-shot routine in golf. Important in the transition from the practice range to real games, your pre-shot routine helps you get situated and ready to play real competitive golf. Tom explains, first, how to set your lines, taking a straight and purposeful line down course where you want your ball to go, and remaining fixed on it, as you approach your tee. Then, when positioned at your ball, he t...

Customize your directions on Google Maps. Drag and drop the default directions to your preferred roads or highways, get walking or public transit directions, route around traffic, or add multiple stops on your way.

Customize your directions on Google Maps. Drag and drop the default directions to your preferred roads or highways, get walking or public transit directions, route around traffic, or add multiple stops on your way. Print directions with Street View, photos included.

Hip flexors are important muscles to target when weight training to build functional strength in the legs. Learn how to do hip flexor exercises in this strength training video. Take action: knees to chest exercise targets core, hold weight between feet, raise knees as high as you can, start in push up position and bring alternate knees to elbows, and work for quick reps and endurance. Tom Clifford, the instructor in this how-to video, has a degree in physical education, fitness and health fro...

Needless to say, we're talking minor traffic violations. If you've just led the cops on a high-speed chase down the freeway, you're on your own.

Big business is on the web these days and you don't have to build a shopping website or blog to get involved.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

L.A. Noire is one of the most realistic video games ever created. To solve the cases in the game, you'll need to think and play like a real detective. This video will show you how to beat the first traffic desk level, called The Driver's Seat.

So, you've finally figured out how to stand up on your skateboard and ride it without having the thing fly out from underneath you. The only problem is, you don't know how to stop. Instead of jumping off when you're headed towards traffic, watch this video and learn how to stop your skateboard three different ways.

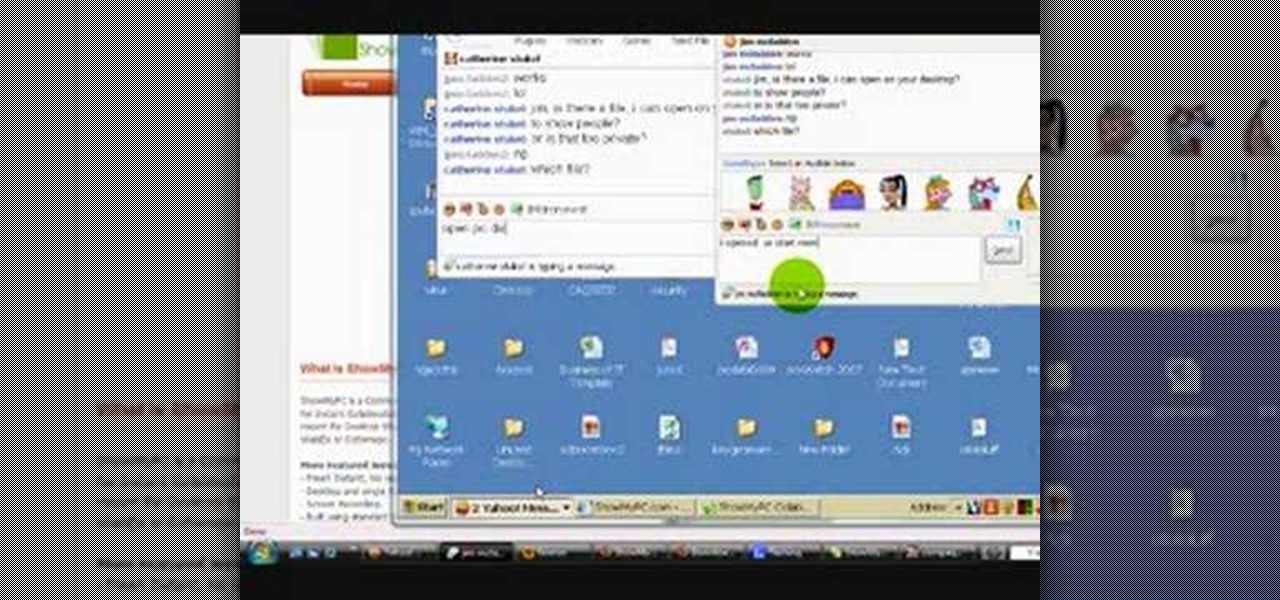
Want to be able to hack into a computer remotely? This method takes a little extra time and cunning to set up, since you will need to first install the ShowMyPc program on your target computer. Once you have installed this program, however, you will be able to go to the website ShowMyPc.com and be able to see what your target has been up to. Even better, you can use that computer and the files on it as if it were your own desktop!

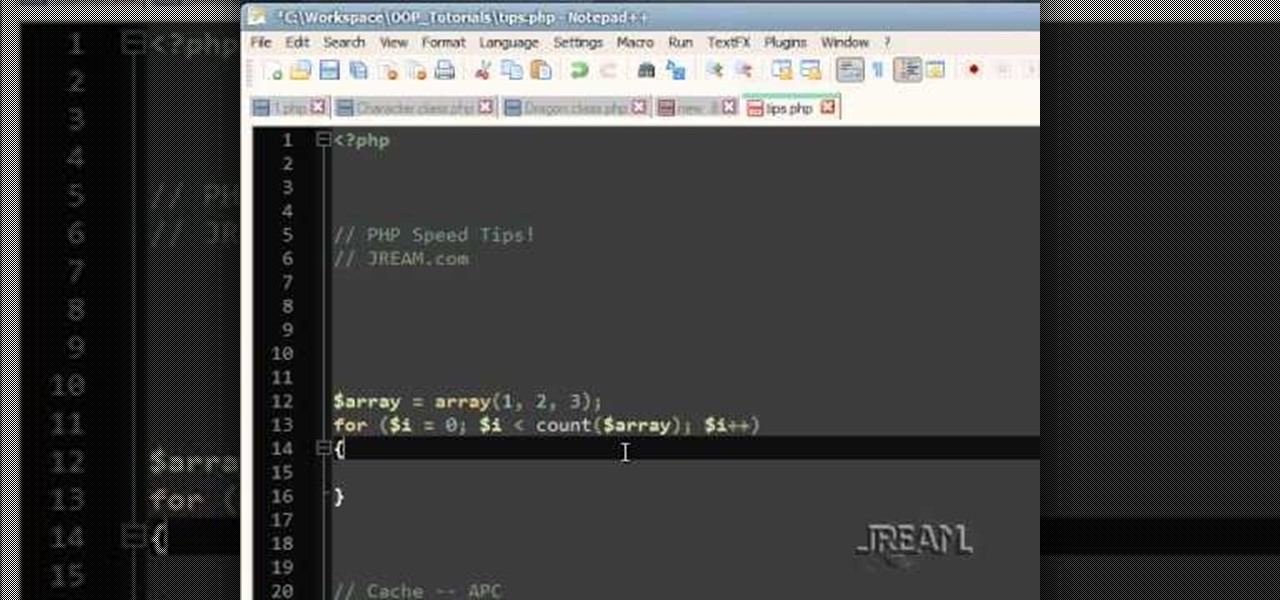
If you're looking to shave a few milliseconds off the Zend Engine's work load, check out this tutorial for some PHP programming speed tips. This efficency will pay off when you have tons of traffic to your site and save you valuable server resources.

If you're looking for a way to get info on your YouTube channel, check out this video and learn how. If you have AT LEAST 20,000 subscribers to your YouTube channel, you'll want to use VidStatsX and, if you have less, you can use ChannelMeter.

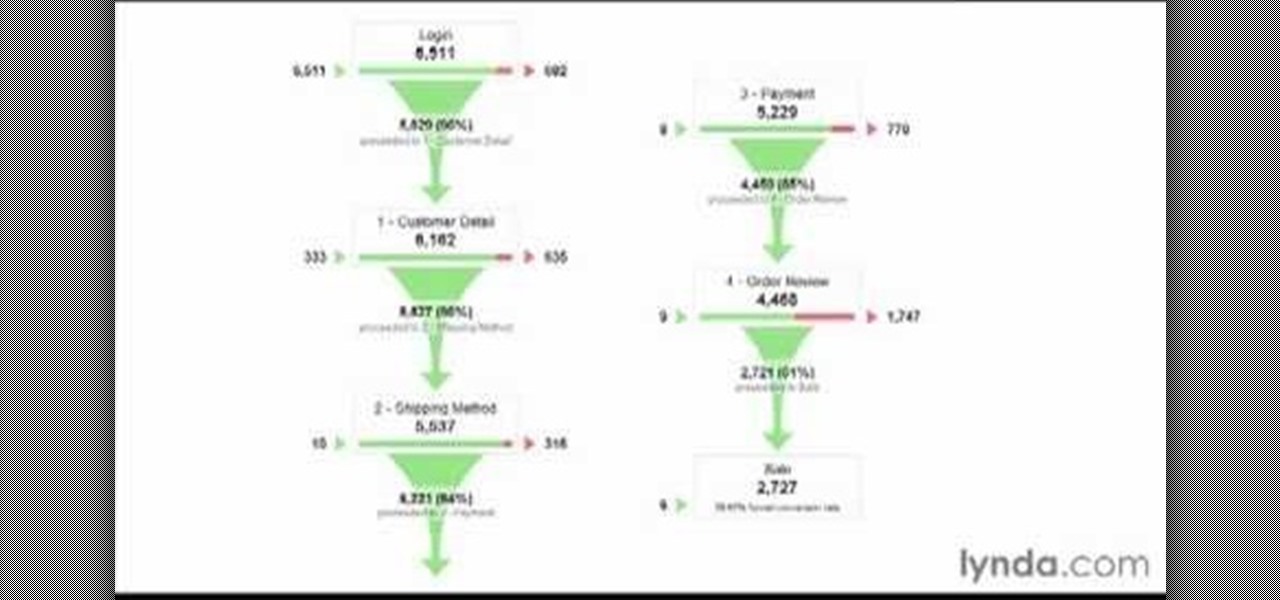
All websites have weak points and problems, and it's important to analyze the overall traffic on your site so you can address these problems and improve your site. This tutorial shows you how to employ Google Analytics and Google Website Optimizer to analyze and maximize your website's potential.

Need some help coming up with keywords to drive traffic to your website or blog? With the Google Keyword tool, it's easy! So easy, in fact, that this home computing how-to from the folks at Easily can present a complete (and somewhat talky) overview of the process in just under five minutes' time. For the specifics, and to get started using Google's Keywords tool yourself, just watch this handy how-to.