In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.
Hi guys, I'm gonna keep this short because I got assignments and a lot of notes to study and also other how-tos and forums to reads. lol...Since I'm keeping this short...no story time just scenario. And I want to thank n3stor for giving me the idea to post this.

Everyone's favorite Android modding tool is finally available for the Galaxy S6 and S6 Edge. Thanks to some hard work by Wanam and a few other developers, we can now install the Xposed Framework on Samsung's latest mid-sized flagship phones.

Hello you sexy, savage, surreptitiously tech-savvy penetrators (Pun intended)!

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

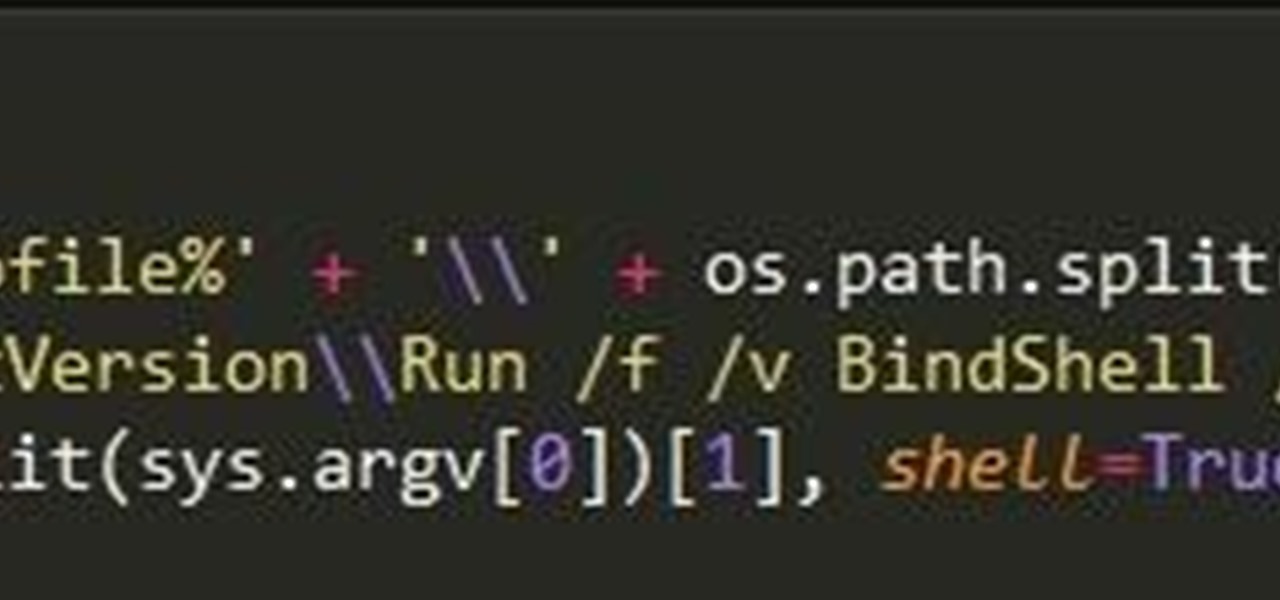
Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

Make no bones about it—Google is an advertisement company first and foremost. Nearly everything they do is geared towards targeting the right people with the right ads.

Let's say that we want to see what someone is doing on their computer? In this tutorial, we'll be hijacking cookie sessions to do just that!

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

Starting April 10th, you'll will be able to book 15-minute appointments online to try on an Apple Watch in person at Apple Stores across the world. With the April 24th release date just around the corner, making an appointment is a great idea for those who are unsure about which color and size to purchase—or if they'll even want one.

Beginning with KitKat, I've been used to customizing every aspect of my Android phone, but with the release of Lollipop, there is quite a bit of catching up that developers need to do. Most customization features, like quick settings rearrangement and theme support have already been ported over, but any type of lock screen customization has been noticeably absent.

If you're an Android fan, you probably made your choice in mobile operating systems based on the insane level of customization options that Google's software offers. Don't like your home screen app? Simply replace it. Not a fan of a particular app's sharing system? No big deal, just share through a third-party app.

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach.

Pushbullet is one of those apps that helps separate Android from its competition. By pushing the boundaries of cross-platform data syncing and file sharing, the service truly demonstrates how flexible and robust the world's leading mobile operating system can be.

The new OnePlus One packs a 3,100 mAh battery that promises to last all day and night. While that will work for most, some of us don't quite know how to put our phone down and save some juice.

The way you use your camera just got a bit more interesting. Phogy, a brand new camera app for Android, allows you to capture pictures with a 3D effect that comes alive when shifting your phone from side to side.

Welcome back, my greenhorn hackers!

Google recently updated their TOS to reflect the email scanning practices they use in Gmail, which are used to display more relevant ads, among other things.

While rooting your Galaxy Note 2 certainly has its advantages—everything from increasing security to relieving the Power button of its duties—it's definitely not for everyone.

By this point, you've definitely come across an app or two that wasn't designed with the HTC One in mind. Either the resolution is too small, the status bar stays active when it shouldn't, or the font isn't the ideal size. There are ways out there to get that changed, but up until now it wouldn't just change one app—it would change all of them.

Besides the obvious, fingernail polish can be pretty useful around the house—for men and women. It can keep your buttons from falling off, sort your keys, prevent your shoelaces and hoodie strings from fraying, and even curb rust rings in the shower. Turns out, nail polish also comes in handy on April Fool's Day.

Photo mosaics have interested me since I was a kid. I could never understand how someone took the time and effort to make one large masterpiece out of hundreds of smaller images. Maybe I'm too daft to grasp the concept, but it seems extremely difficult. I certainly don't have the necessary skills to make my own work of art, but luckily my Nexus 7 does.

The use of smart phones is not limited only as a mode of communication now-a-days. There are many things that can be done with the help of a smart phone.

The Nexus 7 is a huge jump in screen size when coming from a phone, but obviously this tablet is still smaller than some of the major players such as the Nexus 10, Galaxy Tab, etc. One way to squeeze out a little more space is to eliminate the navigation and status bars.

Give me a paintbrush and easel and you'll be sorely disappointed, but give me a Samsung Galaxy S3 and a new app called Let's 8-Bit Art and you might call me the next Picasso.

Navigating through row after row of plants, my tiny fingers would reach into the leaves to pluck all the vile little creatures from their homes and deposit them into a can of gasoline. Potato bug duty, my least favorite gardening chore. Growing up, my family had a small garden every year. And every year, I was recruited to help plant, maintain, and eventually harvest the vegetables from it. There were some tasks I didn't mind, but the ones I hated most usually involved bugs (have you ever see...

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

The art of persuasion is a very crucial characteristic that anyone can learn, and it has countless benefits. Whether it's at work, home, or in social situations, the ability to be veritably persuasive can have an unheralded impact on your daily life.

This guide will explain how to configure a USB Flash Drive / Memory Stick so that you can run a keylogger within just a few seconds of plugging it in any computer.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

As the holidays approach, so does that wonderful Autumn day where loads of people happily camp out in freezing weather in front of their favorite stores to save a few bucks on their favorite electronics. And yes, that day is near... Black Friday brings the biggest markdowns of the year, and that includes slashed prices on many of our favorite touchscreen devices, including the Kindle Fire HD, Samsung Galaxy Tab 2, and Nexus 7. Want to get your hands on an Android tablet for cheap? Below are a...

It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...

RFID chips are everywhere. They're in passports, credit cards, and tons of items you've bought in the last 5 years or so. Big retailers like Walmart started using tracking products with RFID as early as 2004, and today, they're used in everything from mobile payments to hospital record systems. Chances are, unless you're a hermit (in which case you wouldn't be reading this anyway), there's an RFID tag within a few feet of you. Photo by sridgway

Today we're going to draw Spongebob! He's going to be facing forward, so even beginners should find drawing this guy to be a piece of cake! 1) Begin by sketching out a rectangle with a broader top and a narrow bottom, make sure it's not too skinny though. This will be the base of Spongebob's body.

There's a cool little plugin for your WordPress blog that will help you get more traffic from people searching the web on mobile devices. It's called MobilePress. Your visibility will become greater on mobile phones and other mobile devices when activating this plugin on your blog.

This Sports video tutorial shows how to hit the golf ball as a draw. Frank demonstrates in this video how to hit a draw. It is very easy to hit one. What you should aim to achieve is an inside outside swing. He has laid out three clubs on the ground. One club is on target line. The other two clubs are parallel to each other and are on swing path line with the ball placed in their middle. When you swing your club back, go through the two clubs winding up. In the unwind portion, your club shoul...

In the early days of the internet, if something was there and not password protected, you could see it. In the process of becoming the indispensable work and entertainment resource that it is, the internet also grew the same borders that countries have while also getting less safe for the people using it. If you want to watch something, you have to hope it was available in your country. If you want to keep your information safe, you have to take some extra steps to make sure that happens. The...