One of the biggest improvements with the Galaxy S9 and S9+ is the redesigned camera, with the latter scoring an impressive 99 overall on DxOMark. But with an abundance of features and enhancements, tweaking the camera's settings for optimal performance can be a little confusing.
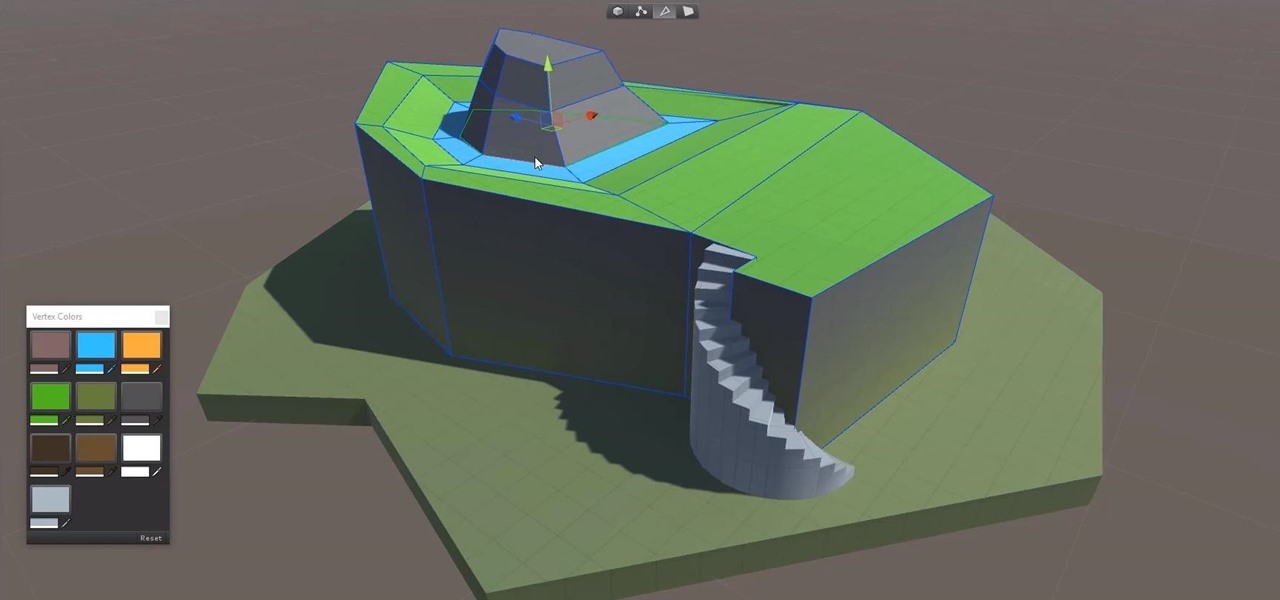
Continuing to take the steps necessary to reign supreme among the top game engines of the world, with a steady stream of major updates, enhancements, and new features, the team at Unity are keeping the user base in a regular state of surprise. At this rate, it's almost like Christmas every few days.

The once blurry and mysterious vision of Magic Leap's future is slowly coming into focus in the present, despite the company's obsessive attempts to keep any and all information under wraps until the next reveal is absolutely necessary. A new tidbit of information hints at an addition to the company's unfolding story that almost no one had accounted for: retail stores.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.

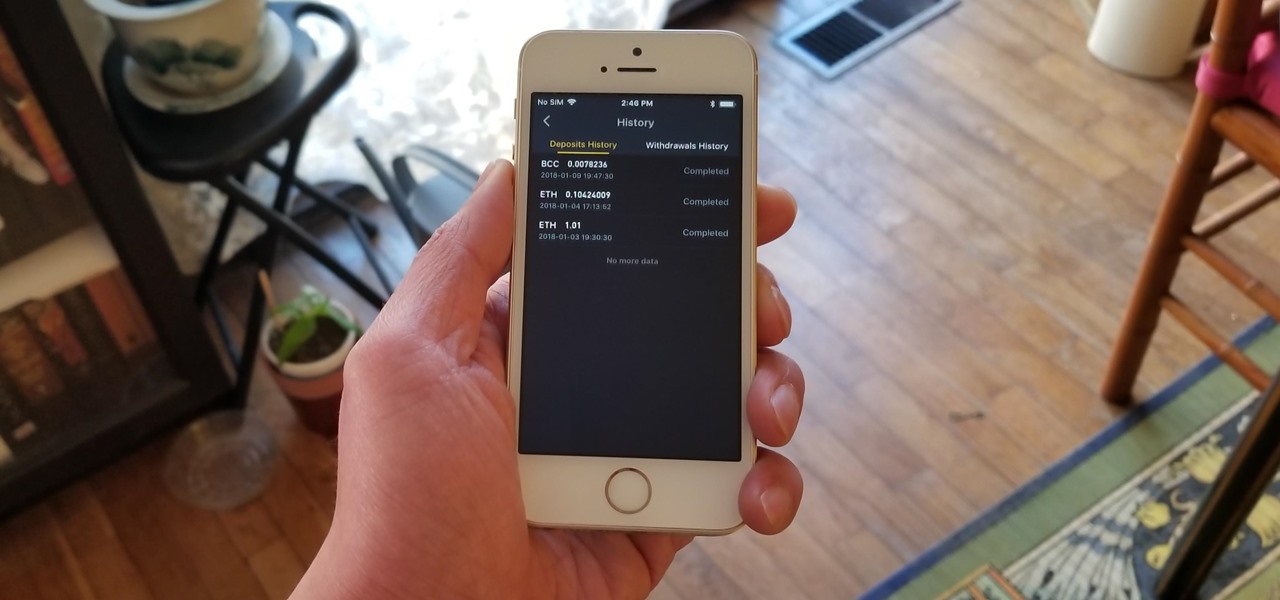
As cryptocurrencies gain mainstream acceptance, it's not far-fetched to think that we'll one day be able to buy alt coins like Ripple (XRP) and Stellar (XLM) using debit cards and bank accounts. Until then, we'll have to rely on using bitcoins and ethereum to buy digital coins. Thankfully, depositing and withdrawing cryptocurrencies with Binance is relatively hassle-free.

Having your home and work addresses set in Apple Maps makes them incredibly easy to navigate to no matter where you're located. If you move to a new house, stay in a hotel or resort while vacationing, report to a different office, or have multiple job sites to visit regularly, updating these addresses isn't only straightforward — there's more than one way to do it.

Whether you just bought an iPhone X or one of your friends or family members did, iPhone X accessories are probably on your shopping list this holiday season. Cases, screen protectors, fast-chargers, wireless charging stations ... whatever they may be, you'll find the best deals on them this Black Friday weekend.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

The iPhone X, iPhone 8, and iPhone 8 Plus may be some of the fastest phones of 2o17. However, the equally new iOS 11 isn't quite as impressive. That being said, Apple is continuing updates to the developer beta for iOS 11.1, as it releases the 5th version of the beta today.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

A virus easily spread among trout and salmon could make it harder to keep your favorite fish on the menu.

When Apple announced their ARKit platform in June, they immediately staked the claim to the largest augmented reality hardware platform, with millions of iPhones and iPads compatible with iOS 11 becoming AR devices this fall.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Urinary tract infections (UTIs) drive over eight million people to seek medical attention every year. Almost all — as many as 90% — of those infections are caused by Escherichia coli. Copper can kill bacteria, but E. coli has found a way to capture the copper, preventing its antibacterial action. Now, researchers have found that, in a cruel irony, the bacteria use the copper it grabs as a nutrient to feed its growth.

The growing list of dangerous antibiotic resistant organisms has just acquired three new members. Researchers have discovered three new species of Klebsiella bacteria, all of which can cause life-threatening infections and have genes that make them resistant to commonly used antibiotics.

After years of telling patients to finish any prescribed course of antibiotics completely, a group of researchers in the UK say it is no longer necessary, and could even be harmful if we want to preserve the antibiotics we can still use.

Cancer cells do a pretty good job of flying under the radar of our immune system. They don't raise the alarm bells signaling they are a foreign invader the way viruses do. That might be something scientists can change, though.

New research explores how the bacteria on the penis can leave men more susceptible to infection with HIV.

Twelve-year old Rory Staunton took a dive for a basketball during gym class and came up with a cut on his arm. The school nurse applied a couple of band-aids, without cleaning the cut, and off he went. In approximately three days, hospital physicians told his parents there was nothing else that they could do for their son; he was dead.

Colorectal cancer — cancer of the colon or rectum — is the third most commonly diagnosed cancer in the US. To reduce the chances of a diagnosis we are all urged to stop smoking, keep our weight down, decrease our intake of alcohol and red meat, keep active, and get screened for colon cancer. But, new research has found something that participates in the development of colorectal cancer that might not be as easy to control: A strep bacteria that promotes tumor growth.

Facing claims of misappropriation of trade secrets and confidential information by Meta Company, DreamWorld, led by Meta's former employee, Zhangyi "Kevin" Zhong, has fired back with a motion to dismiss the lawsuit.

Even though HIV rates declined 18% between 2008 and 2014, 1.1 million people in the US are living with the infection. Part of that is because HIV is treatable, but not curable.

A little-known feature in Apple Maps for your iPhone lets you tour big cities like you're Godzilla, and it's actually quite easy to access — if you know the secret.

Bone loss and belly fat may no longer be certain fates of menopause, thanks to new research from an international team of scientists.

Facebook is testing a new feature in India. One that could help you protect your profile photos from being used on sites without your permission.

HIV infections persist despite treatment that successfully decreases viral blood levels to the point where doctors can't detect the virus. But that doesn't mean the person is cured. The virus hides in the body, not replicating, just waiting for a chance to jump out of the shadows and reemerge.

Alzheimer's disease — an irreversible, progressive brain disorder — is the sixth leading cause of death in the US and more than afflicts 5 million Americans. As if those numbers aren't scary enough, the Centers for Disease Control and Prevention expect that number to nearly triple by 2050.

Citrus greening disease — caused by a bacteria spread by psyllid insects — is threatening to wipe out Florida's citrus crop. Researchers have identified a small protein found in a second bacteria living in the insects that helps bacteria causing citrus greening disease survive and spread. They believe the discovery could result in a spray that could potentially help save the trees from the bacterial invasion.

Dangerous to humans and dogs, Rocky Mountain Fever, along with several other tickborne infections, is on the rise.

Activating the body's own immune system to fight cancer is the goal of immunotherapy. It's less toxic than chemotherapy and works with our body's natural defenses. The trouble is, it doesn't work for most patients — only about 40% of cancer patients get a good response from immunotherapy. But coupling it with another type of cancer therapy just might deliver the punch that's needed to knock out cancer.

Mixed reality display manufacturer Realfiction has developed a 64-inch display capable of delivering 3D holograms without a headset.

As headlines focus on melting glaciers and rising water levels caused by global warming, climate change is quietly taking its toll on the nearly invisible occupants of this planet, the microbes.

The bacteria Klebsiella pneumoniae is a bad actor known for being antibiotic-resistant and causing a variety of serious infections in hospitals, including pneumonia, surgical site wounds, and meningitis. K. pneumoniae is something you do not want to encounter if you have a compromised immune system.

Have you ever had a burning sensation when you urinate? Low fever, back pain, and maybe cloudy urine? Male or female, it could have been a urinary tract infection. If it lasted long enough, the chances are good you went to the doctor for help. For about 20% of women, standard testing for a UTI does not reveal the presence of infection-causing bacteria, even though bacteria may be causing their symptoms. Well, a new test may provide better answers.

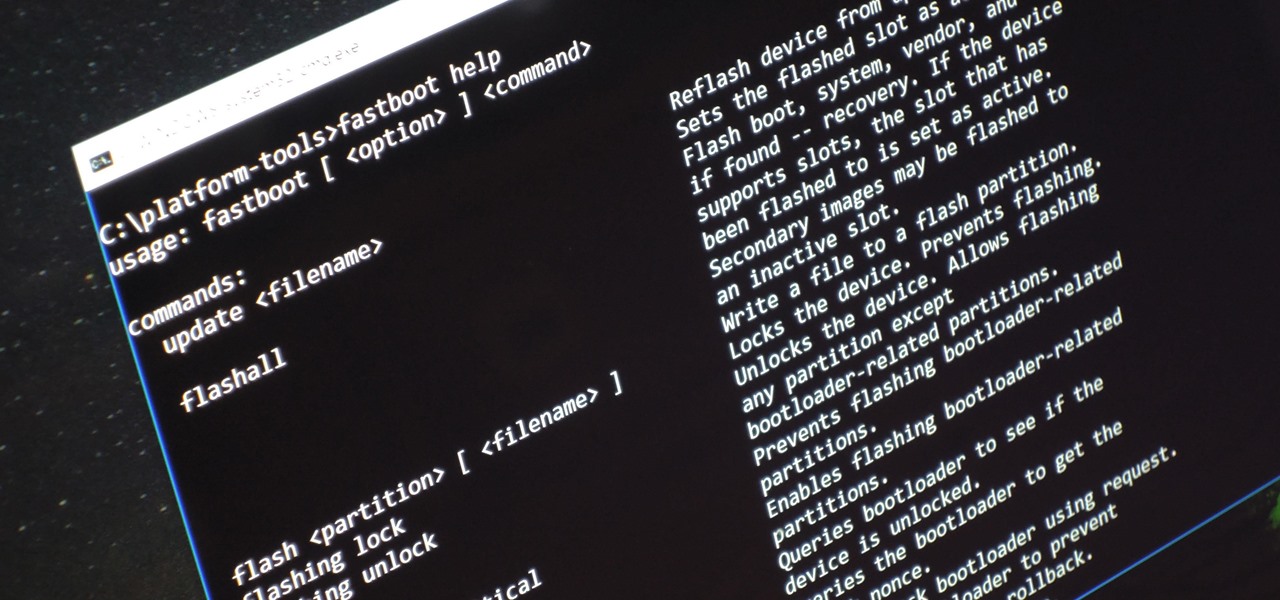
Unless you're experienced using the Linux terminal, running ADB and Fastboot commands can get confusing very fast. The problems often stem from having to hunt for various files — usually IMG or ZIP files that you need to mod your Android phone — and then move them to your platform-tools folder, which, depending on how you installed ADB in the first place, could be anywhere.

When just floating peacefully in the water with their brood mates, the Culex mosquito larvae in the image above does not look very frightening. But in their adult form, they are the prime vector for spreading West Nile virus — a sometimes mild, sometimes fatal disease.

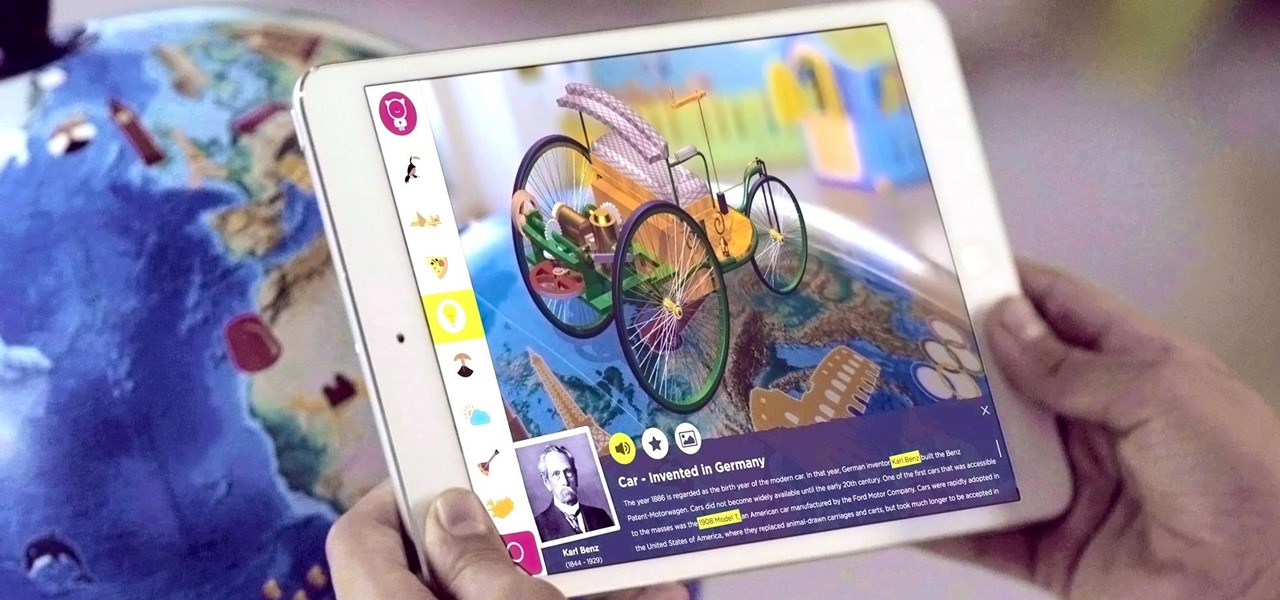
Globes used to be standard in households, usurped in many ways by modern mobile and desktop applications. But one company believes they can upgrade the globe for the 21st century.