Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

Steam is an online platform that lets you download and play over 2,000 video games, from first-person shooters to RPGs, as well as a pretty long list of indie games. You can play on your PC, Mac, mobile device, or even your television, and it has a community of over 40 million gamers. Prices are different depending on the type of game and how new/popular it is, but they're generally about the same as what you'd pay for an Xbox or PlayStation version. They also have a decent list of free games...

Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmissions that planes use to communicate with airport towers are both unencrypted and unauthenticated.

Starting a business has to involve a desire to benefit someone else other than you. If all your reasons for starting a business are to benefit you, chances are good that you have missed the big picture. At least one reason you have to want to stat a business needs to be to help someone else. Either use proceeds from the business to help a charity of your choice or to solve a problem or provide a solution to a need for the target group that your business serves. Focus on one issue to start wit...

Everyone who owns or runs a website needs to know how they can improve traffic, and search engine optimization is the answer. This 13-part video series on SEO basics and strategies will give you more traffic for your site. It's jam-packed full of tons of great SEO tips! Check out each video in the series:

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

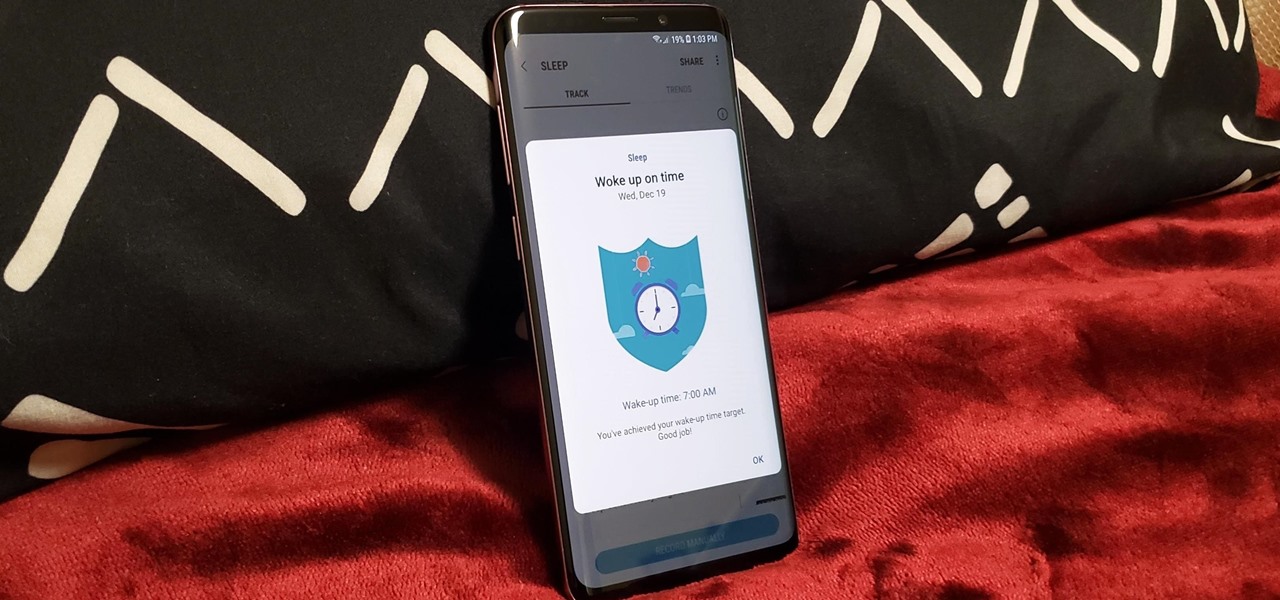
The quality and length of your sleep will almost always dictate how the rest of your day unfolds. Sleeping fewer hours increases your chances of spending the day in a tired and cranky state, while having a restful night's sleep contributes greatly to being alert and productive. Luckily, if you want to track your sleep patterns to figure out how you can improve your circadian rhythm, Samsung Health has you covered.

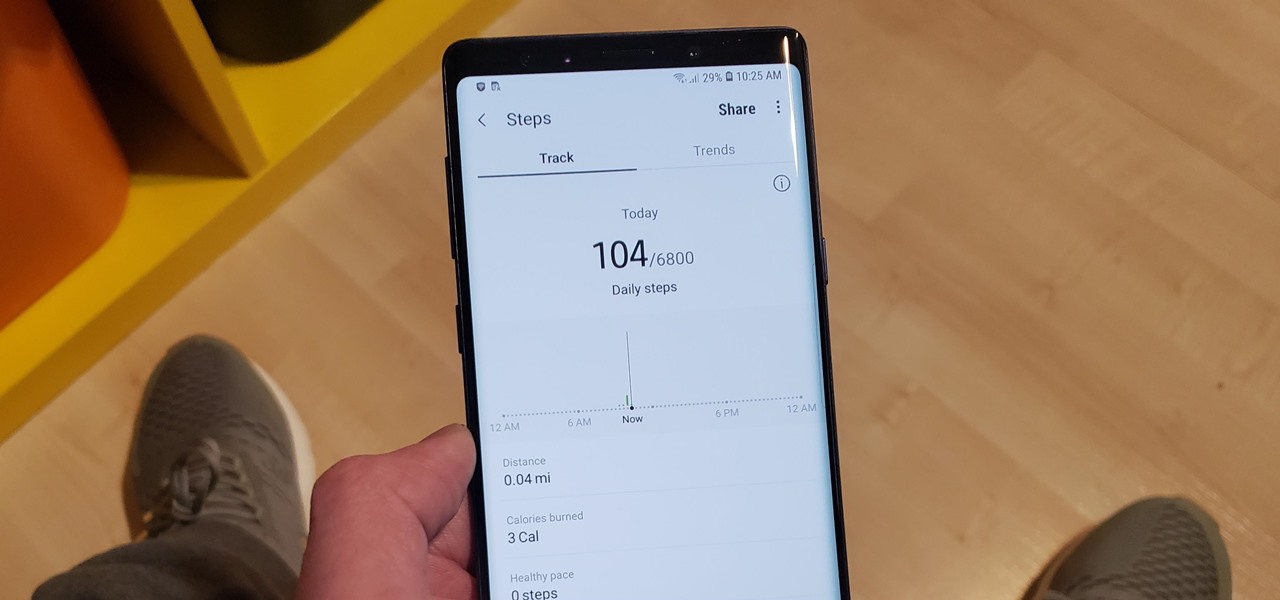
Once known as S Health, Samsung Health has become one of the most comprehensive health apps available for Android. In fact, we all can benefit from the features the app brings to the table — whether you're a marathon runner or a couch potato. If you're in the latter category, the app has a simple feature that can nudge you towards becoming more active.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Epic Games just released update v3.4 for Fortnite Battle Royale on all four platforms. This new version brings a number of UI changes, performance improvements, and bug fixes, but the addition that will get the most players excited is a new weapon: the Guided Missile.

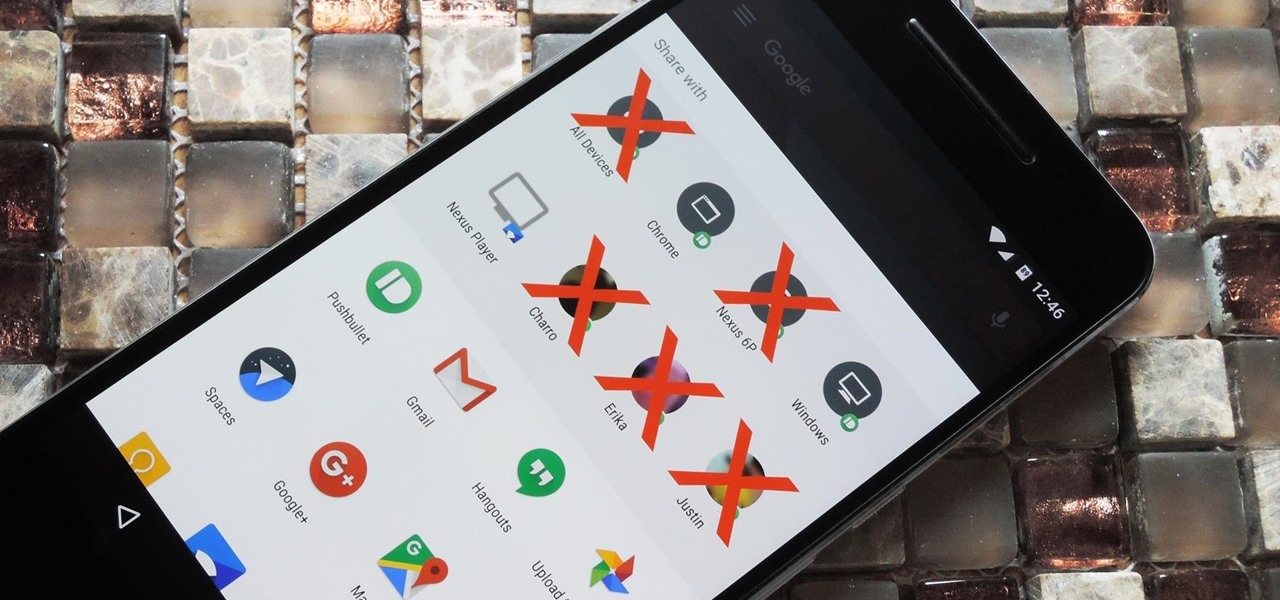
Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

If you've ever wanted to hone your paintball skills, without spending a ton of money and making a huge mess, Show Me Virtual and Apple's ARKit have an app for you.

Android 6.0 introduced a new feature called Direct Share that allows apps to pin a more specific set of targets to Android's share menu. You've probably seen it already—messaging apps will allow you to share a file directly to a specific contact instead of just to the main app, and there are several other implementations like this.

Anyone who paid attention to the Lavabit shutdown had a feeling it was connected to Edward Snowden, the high-profile NSA whistleblower. Ever since the government's case against Lavabit went public in late-2013, people have put two and two together.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Five Phases of Hacking:- The five phases of Hacking are as follow:

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

In this how-to video, you will teach your dog how to target objects with its front paws. You will need a clicker, treats, and a target such as a yogurt lid or ball on a stick. Take a treat and hide it under the object. Click when the dog does any paw movements towards the object. After ten successful tries, pretend to put a treat. Once the dog paws the object, show that there is no treat but still give the dog a treat. Once this is done, wait until the dog paws the object, and give a treat. I...

Watch this video tutorial to learn how to use hand signals on a bicycle. Bicycles don't come with turn signals and brake lights. Fortunately, there's already a universal language for indicating turns and stops on a bike.

A lot goes into making a hunt successful, and most of it happens before you take to the field--like making sure your rifle is properly sighted in. It's not hard to do if you follow a few simple steps: first, and this is the first step when you do anything with a firearm, make sure it's unloaded. Make sure your scope is properly mounted and the mounting screws are tight. Remove the bolt from the rifle and sight through the barrel to make sure you're lined up with a sight-in target placed at 25...

Trying to get more traffic for your Wordpress blog? Looking to connect with the people who visit you online? This video will show you how to facilitate web interactions by adding social media icons to your blog's header. This video uses the 2010 theme to demonstrate. CSS may be intimidating, but this video will show you exactly what to do.

In this clip, you'll learn how to get started using Blue Coat PacketShaper on your Microsoft Windows PC. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just under four minutes. For more information, including detailed, step-by-step instructions, take a look.

Brake fluid is important, we all should know this. If you're in the city, then you know that once that stop and go traffic hits, you're going to want some good response out of your brakes. An in-depth look at checking the brake fluid and how to add more.