Ok, this prank is an idea I have for part of a comedy film I am writing a treatment for, and it is dedicated to pranks and pranksters!This idea is based on women always, ALWAYS, going nuts over their butts and how big they are! Women are always so self-conscious about their weight and their butts, and always putting guys on the spot asking how they look in clothes and if something makes their butts look big, so this is dedicated to all those women out there!We would need a guy, maybe a cast o...

Hey guys! Just made a tutorial on one of the best TNT cannons I've ever made. It was in a video, but I've improved it to shoot soooooo much farther. Hope you guys like it!
The Intercontinental Ballistic Missile (ICBM) was successfully launched from the Plesetsk facility in northwestern Russia and its dummy warhead landed on target on the Kamchatka peninsula on the Pacific coast, the Defense Ministry said.
DARPA is at it again. This time, the Defense Advanced Research Projects Agency has announced plans to create nanochips for monitoring troops health on the battlefield.

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

As you may or may not know, the US and France have deployed four nuclear warships on either side of the Strait of Hormuz, which, along with helicopters, scour the area for underwater mines.
The department of Homeland Security released a list of 'words and phrases' it uses to search social media for terrorism, and whatever else they decide they are looking for that day. Read some of these. A few are obvious "bomb, nuke" and some "target, event" are just down right vague. More reasons to watch what you do on the Internet. You are not the only one watching!

In a recent address, Obama supports drone attacks against people 'on the list'. He talks about the people on the list being known of 'going to attack Americans', and who have a 'track record of terrorism'. Let me tell you, targeted strikes will, 90% of the time, have civilian casualties. There is no such thing as a clean strike. But I'll let you decide.

In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...

Formerly ipchains, iptables is a script-based firewall that's included with both Mac and Linux operating systems. In my opinion, it's the best firewall in existence. The only downfall is that it's complicated for some people to use due to its script-based nature. But this should be disregarded, as firewalls are nearly the entire security of your computer.

When you're out and about in the dangerous world of Wi-Fi, it's hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Private Network) server and client.

This Null Byte is the first part in a mini-series on the art of Social Engineering. I will be teaching you how to effectively defend yourself against it.

Step 1. Be there at the right place at the right time. Step 2. Target the scene with your camera phone.

We love all things Jackass at WonderHowTo, but before Johnny Knoxville and his pals were sticking fireworks up their butts, snorting wasabi, and taking a shock to the gonads (à la the childhood game, Operation), in the far off land of Ontario, Canada reigned another daredevil—a man named Ralph Zavadil, a.k.a. Cap’n Video. Just as we all winced when Knoxville tore his uretha, community access viewers of the '90s cringed as Cap'n Video bounced off concrete and broke his neck... until Zavadil wa...

The tragedy of the Triangle Shirtwaist Fire repeated itself. Over 25 Bangladeshi workers died in a sweatshop who sewed clothes for JC Penney, Target, Abercrombie and Fitch, and many more. Check out the link.
As You Sow, an organization fighting for a just workplace in garment factories just published a report on the top brands (Wal-Mart, JC Penney, Target) and scored them on their labor practices. Check out the report for yourself.

White: the first thing comes to my mind when I see light white is an angel, I think that this color represent the good side of everyone, the angel form of a person, sometimes you can see someone and look at him like he is a real angel, what a wonderful feeling, and even someone who is very gentle with you, you can display him in your mind with a white circle on his head.

China's latest futuristic project is a massive "3D Express Coach", a clever project proposed by Shenzhen Hashi Future Parking Equipment Co. as a solution to traffic in the extremely overpopulated country.

IP Hider masks the real IP of a user, allowing him to browse all kind of pages without ever worrying that the ISPs or any other marketing tool is monitoring your surfing habits or spammers are attacking your computer. The simplest way to do this is to have traffic redirected through anonymous proxies.

This quick 3D modeling software tutorial explains how to bake a normal map in modo 301. Learn how to bake a normal map mesh to mesh using high-res meshes targeted to a low res mesh in modo 301. Bake a normal map.

Steve Davis and John Parrott show how to hit the screw shot, in which the cue ball rolls back after contact with the target. The video contains slow motion footage of what's happening to the cue ball in response to contact with the cue. Hit a screw shot in snooker.

I made a Origami Valentine's day present for my Little Sister and Neice using heart and rose origami patterns I found on-line and put them in a backet with heart shaped lollipop I bought from Target.

A former decorated undercover FBI agent, Mike German, explains how the national security state, in league with local law enforcement, is secretly targeting Americans for political views and activities perceived as a threat to the political establishment. » Former FBI Agent: Surveillance State Trashing Constitutional Protections Alex Jones' Infowars: There's a war on for your mind!.

Behavioral ad targeting companies are diving deeper into the realms of your subconscious with a new approach to serving adverts to you online—and they're using your television.

Blogs are a gold mine Some of the best sentences you will ever get when building your vocabulary can definitely come from blogs. The language and vocabulary usage in blogs is always changing to reflect how people talk in this day and age, and therefore are the perfect research tool for vocabulary sentence building.

A Way Out of the Overload How do we simplify? There's a welter of information, advice, techniques, schools and every imaginable video tape available on the market to answer that question for you. In making a selection from this movable feast you'd want to take into account the background and credentials of the person offering you a way out of the overload. That's assuming you didn't just throw up your hands in exasperation and walk away from the task entirely.

This clip introduces the Constraint Tag and specifically looks at the use of the Aim parameters. If you make use of the Target Tag in Cinema4D, then watch this tutorial to see how the Constraint Tag could open up a lot of extra possibilities. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, and to get sta...
With more and more vehicle owners simply deciding refuse to pay red light camera and speed camera tickets, private, for-profit companies and municipalities are growing increasingly desperate. America’s second-largest city shut down its photo ticketing program last year largely because residents who could not afford the $500 citations did not pay them. On Monday, Las Cruces, New Mexico announced it would shut off the utilities of city residents who refused to pay Redflex Traffic Systems, the A...

As you may have seen in your city or town, red light cameras are on the rise in the United States. In many instances in my area, these cameras have sprung up seemingly out of no-where, and mostly without any reason. Over use of these systems can make privacy (even on the road) a fleeting possibility.
Multiple airport screeners have been arrested for allegedly taking handsome bribes to look the other way while loads of illegal drugs slipped through security at Los Angeles International Airport, federal officials announced today.

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

This article is all about creating content. This is a very important concept to grasp because the content that you create for a website is going to be the basis for how you will advertise and promote that website. Content, meaning articles, videos, and even podcasts is now really the new advertising. Instead of traditional types of advertising and instead of the traditional separation between editorial content and advertising, that has gone the way of the dinosaur.
Make money promoting yourself, build links and drive traffic. Yes thats is right you can get paid to promote yourself by using free to join sites that let you share revenue, I have included a list of sites that will allow you to build links to your online content or sites. this will aid in building your site authority as well as let you make some revenue to help you pay for your hosting fees ect.

A prolific travel writer can always consider starting his own travel site. If you know a country or a city inside out then you really can start your own site, work on drawing traffic and make money from ads. Not much money, maybe but something. And you get read.

Cyclists and unknowing vehicle participants "collaborated" on a public guerilla graffiti art piece in Berlin this last week.

This clip shows a large double roundabout with traffic lights and how to negotiate the lights as you turn right and then straight.

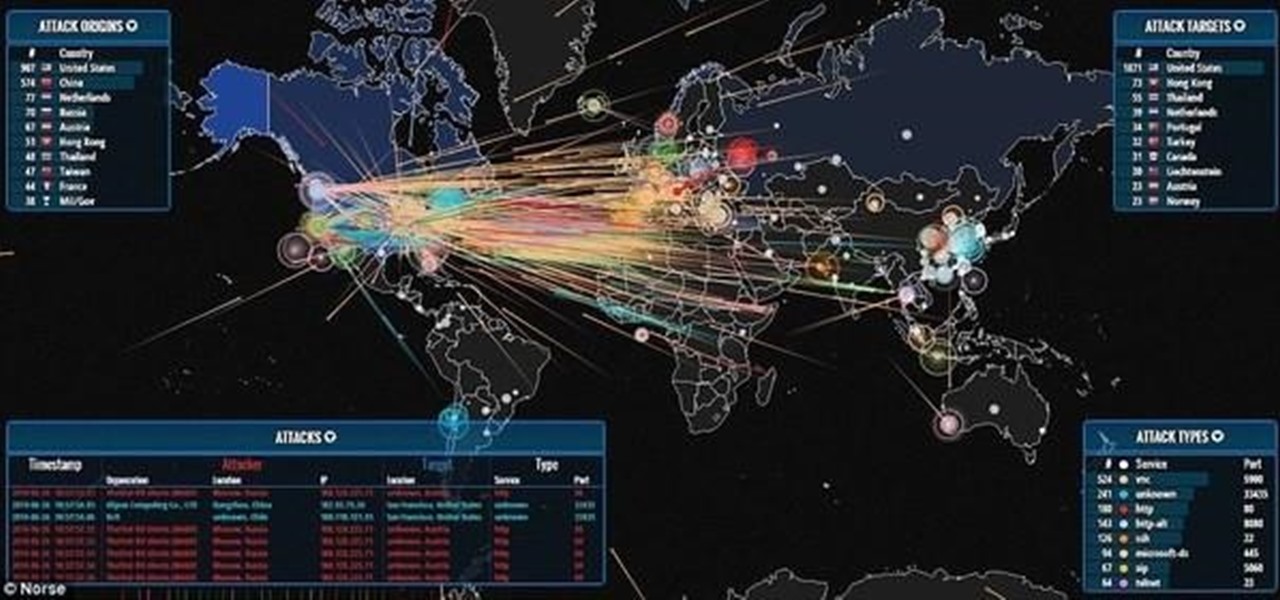
This is a live map feed to current DDoS Attacks globally. Live DDoS MAP Thought I would post this to give you an idea of the size and scope of DDoS Attacks at any given moment. Plus it looks k00l.
Welcome back my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on us all, all the time.

Remember Dan White's "Twinkie defense" in 1979? Well it turns out that the the ability to convert food into glucose is correlated with the ability to control oneself.

Whoa. Someone just got caught this weekend cheating at the 2012 National Scrabble Championship in Florida. He was holding on to some blank tiles, which dropped on the floor mid-game. How did this kid even think he'd get away with hiding blank tiles? Wouldn't it be a little suspicious once his opponent got a third blank tile from the bag? It was the first time anyone has been caught cheating in the National Scrabble Championship, though that can't be said for club, regional, or world tournamen...