If you have trouble deciding on just one cover photo for your Facebook profile, this new app is perfect for you. It's called InstaCover and it lets you create your own cover out of Instagram photos. They can be your own photos or you can choose from all of the public photos by other Instagram users. All you need is a Facebook account.

Uh oh. Somebody screwed up big this time. It has recently been reported that Iraqi insurgents have used $26 software to intercept live video feeds from U.S. drones located in Middle East conflict zones. The drone (a remotely piloted aircraft) is considered one of the U.S. military's most sophisticated weapons. Apparently not sophisticated enough, however.

A target is set up to sit on a reclining chair which is rigged with pressurised air and wont open. When someone says that one problem could be something stuck underneath it to prevent it opening. The target checks and gets blasted with the chair when it is set off.

By Camilla Cicconetti - Visit LifeStyleWebTV for more travel articles, videos, recipe demos and more.

This is the first official announcement for a new weekly activity on Null Byte for the community to participate in. Starting next week, depending on how much traffic we get doing it, we are going to start doing live social engineering calls via Skype. I've made a list below so that you can get a feel for some of things we'll try to accomplish in these calls.

UTILIDOR n pl. -S an insulated system of pipes for use in arctic regions 59 points (9 points without the bingo)

Sharing a laptop's wireless Internet connection with other computers connected to its Ethernet port is a great skill to know. It can be good for a number of reasons; Your computer may not have proper hardware to have a standard setup, or you may have an awkward network topology where sharing your wireless Internet via Ethernet would just be a better option.

Got a knack for speeding? Like running red lights? Believe or not, the police have better things to be doing than pulling you over, like catching real criminals. That's why more and more cameras are popping up at known speeding zones and on street corners—so the cops can clean up the streets, compared to just ticketing them.

Spending five days with the game is enough to know it's not to my liking. Is it a horrible MMO? Yes, yes it is. There are better Free to Play MMOs launched years ago that are better than this. As a fan of the Final Fantasy series (I am currently playing and liking Final Fantasy 13), this MMO is so bad that at some point I couldn't justify the awful environment, game play, and interface.

Imagine this scenario: Late for work, you jump in the car. Going your usual 10 or maybe even 15 miles over the speed limit, suddenly a ball tumbles into the road, closely pursued by a little girl! Scared sh*tless, you slam on your brakes.

WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling.

With gas prices soaring in the US and around the globe, the cost to drive to a vacation destination is becoming a much larger expense item in the overall travel budget. Although it's easy to see that gas prices have risen dramatically in the past several months, it's not nearly as easy to figured out how it will impact that upcoming car trip, so here are the items you need to take into consideration to calculate how much it will cost to drive to a destination.

There are many different types of prepared catfish baits for catching channel and blue catfish. These baits are often referred to as "stink baits", but while they might smell quite foul to some anglers, the smell really attracts catfish.

If you're targeting big bass during the summertime, the best bait to use is a swimbait lure. You may know that they don't give you tons of bites, but in this case, quality is the key. The best bass you'll eve catch will come off this swimbait lure. This is why swimbaits are favorites with anglers who have the confidence to continue casting them in search of lunkers. Wade Bourne of MyOutdoorTV shows you how to fish a swimbait lure.

Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let’s move on to hacking a Linux system and using the Meterpreter to control and own it.

Ladies, be efficient with your time. If you are stuck in a car pool line or in traffic, spend that time to make yourself more beautiful! This video will show you how to do just that. 10 Seconds

I finally got around to trying out another one of Will's mad science experiments and found out that this one was actually more satisfying (and less frustrating) than my slightly uncooperative jar jet. There's something very pleasing about making potassium nitrate at home in the kitchen and then watching the transformation from semitransparent liquid to spiky, frozen crystals. That was the best part for me, second only to igniting it with its sugar companion.

The Xbox 360 is America's video game system. It was designed in America, it has better market share in America than anywhere else, and it has the most overtly macho game catalog of any console. For many Xbox fanboys, gaming heaven is shooting hordes of really well-animated things in the most intuitive way possible. Trouble Witches NEO - Episode 1: Daughters of Amalgam, released last week on Xbox Live Arcade (XBLA) for $10 by Japanese developer Adventure Planning Service, is a typical Xbox 360...

The whole world seems better when you’ve had a full night’s sleep, and if you don’t believe me, you’re JUST FRIGGIN’ WRONG. Studies show that getting enough sleep during nighttime hours can make you less irritable, help you lose weight, and reduce your risk of cancer and other totally bogus-time diseases.

Terry Jenner, also known as the 'Spin Doctor', demonstrates leg-spin bowling, one of the greatest mysteries of cricket. You've got to have the right grip, body alignment, release, and hit the target area. Leg spin bowl in cricket.
Collapse At Hand Ever since the beginning of the financial crisis and quantitative easing, the question has been before us: How can the Federal Reserve maintain zero interest rates for banks and negative real interest rates for savers and bond holders when the US government is adding $1.5 trillion to the national debt every year via its budget deficits? Not long ago the Fed announced that it was going to continue this policy for another 2 or 3 years. Indeed, the Fed is locked into the policy.

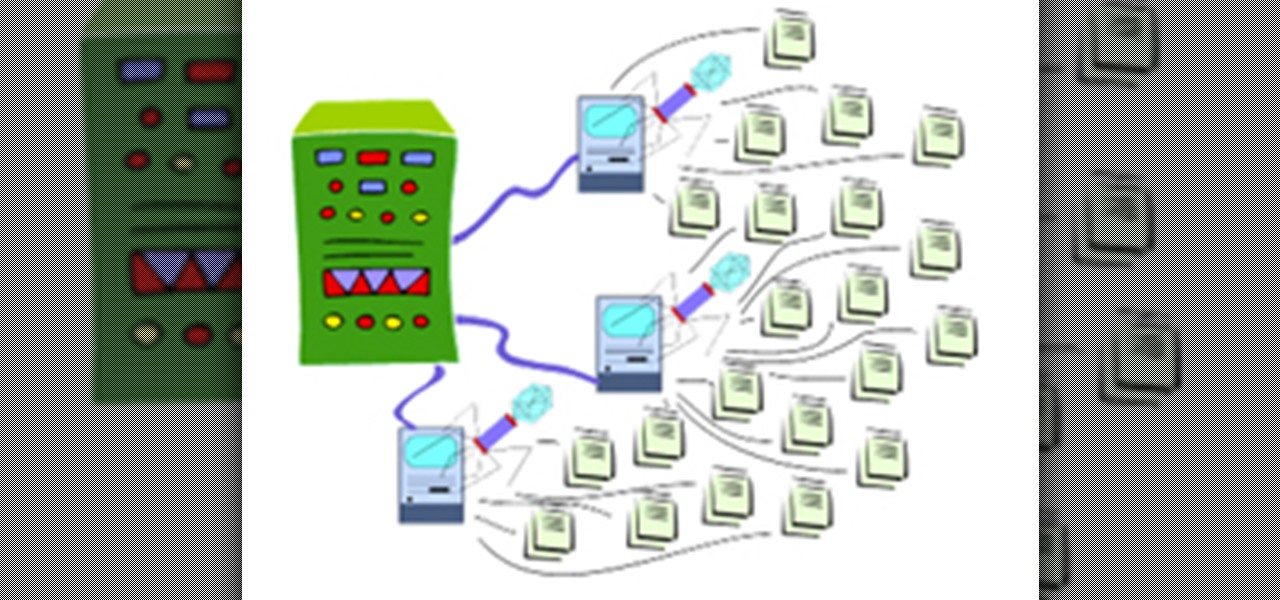
Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

US can legally kill Americans in terror groups You read it right. The US can now target Americans who are supposedly part of terrorist groups. Here's my analysis of Attorney General Eric Holder points (keep in mind though, these are point's brought up by MSNBC, original article here):

Last Friday's mission was to accomplish solving HackThisSite, realistic 2. This second mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend take down a racist hate-group website.

Last Friday's mission was to accomplish solving HackThisSite, realistic 1. This is the first in a series of realistic simulation missions designed to be exactly like situations you may encounter in the real world. This first mission, we are asked to help a friend manipulate the website voting system for a Battle of the Bands vote count in his favor.

How many people use the big search engines here? I'm going to estimate 90% of everyone on WonderHowto uses one of the following on a regular basis: Google, Bing or Yahoo! Search. The question is: are you in that 10%? You should seriously consider dumping Google search for DuckDuckGo. Why? DuckDuckGo does not track you.

Our mission for this week's Community Byte was to create a Python program to crack web-based passwords, like the ones you would see on an email or router login. I wanted it to be universal in the sense that it could be easily modified and adapted to another website just by changing a few variables. That was a success! Even though people weren't on time to the coding session, everything went well.

There is a near-infinite amount of ways a computer can be broken into. But that does not mean that there isn't a reason to secure our computers as best as we possibly can. It's like the principles of a secure house. Which are the most secure houses? The ones with locks and advanced alarms, obviously, but not for the reasons people normally think.

Electronic Arts (EA) and Hasbro have always been a little slow at adapting Scrabble for the cyber culture. They failed to beat Scrabulous to the Facebook market by a whole year, but managed to save face by targeting the mobile market, specifically iPhone and iPod touch, making Scrabble one of the very first mobile apps in the iTunes App Store.

On October 7th, the IndieCade Conference will open its doors to some of the most innovative minds in the independent gaming industry. The three day event located in Culver City, California includes presentations by notable indie designers, workshops, galleries, and mixers. On the following day, however, the IndieCade Festival begins. Unlike the conference, the festival includes events targeted at gamers and the general public. While a $15 wristband will grant you access to keynotes, events, a...

Children under the age of 13 possess insight that can blow the minds of their elders, but not the wherewithal to make important life choices for themselves. This is exactly why there are strict rules against marketing cigarettes to them. In 2000, a law went into effect called the Children's Online Privacy Protection Act that institutes similar consumer protections for our youth's online identities, prohibiting companies from soliciting personal information from children under 13 years of age ...

The whole world is connected to the Internet, which means bank for advertising companies who track your every move online. Most of the content you see on the web is free, and that's because of advertisements. If there were no ads, none of us would be addicted to the Internet because none of us would be able to afford it.

It's been a great year for video games, kind of. Sure, the AAA release lineup has been a trainwreck and hacking has been a bigger problem than ever. But two things have happened involving the federal government that have made video games more legitimate in the United States than ever before. The Supreme Court ruling establishing that video games were the equivalent of movies and books, not porn, was the more significant decision. But in May, the National Endowment for the Arts made another si...

Google started culling Google+ accounts. There are two main targets: businesses and those who are using pseudonyms. For businesses, Google is promising to provide their own version of Facebook Pages, which will be released later this year. For those who use pseudonyms, they aren't so lucky. According to Google+'s community standards, users must "use the name your friends, family, or co-workers usually call you". The purpose of this rule is ostensibly to discourage spammers and people from set...

Team Fortress 2 (TF2) is one of the best multiplayer games of all time. It took nine years to make, and the developers have supported it with more post-release free updates than any other game ever. Four years after its release in 2007, it is still immensely popular, and although its price has gone down, Valve has managed to continue making a massive profit by introducing the first successful microtransaction model in a mainstream American shooter. That model has been so successful that it lo...

This article describes the very basics of compiling a program on Linux. It is targeted at the absolute beginner. Sometimes beginners search for programs on the web for their Linux systems, and is faced with the reality that they have to compile the program themselves, either because there exists no binary for their architecture, or the author of the program just doesn't release any binaries at all, but only sources.

With the globally rampant use of such social networking platforms as Facebook, Twitter, and Foursquare, the issue of privacy has become a prevalent concern for many. And for good reason—there's the violation of Facebook employing user names in ads, the Etsy slip-up, and of course, the everyman act of recklessly sharing too much information via common social media outlets: a night of drinking results in morning after embarrassment, or worst case scenario, sloppy Facebook posts and tweets resul...

Hello readers again! Sorry about the long wait (scary computer problems). Today I am going to talk to you about security problems on Wizard101. I have recently encountered many security flaws on Wizard101, including hacking, frauding and other crazy things. Wizard101 is the target for many online predators, many of who are fully-grown adults aged 60 or 70. Here is the link to an article I found about it: Wizard101 Internet Predators

Flash video. It's what all smartphone users have been waiting for. Why has it taken sooo long? And why is Apple still resistant?

Lifehacker posts an article on the art of cracking weak passwords, courtesy of Internet standards expert, CEO of web company iFusion Labs, and blogger John Pozadzides. Pozadzides certainly knows a thing or two about password logic. (Note: this information is not intended to hack into accounts, but rather to protect you from using weak passwords).