If shield kicking is legal in your game, here's how you can safely and effectively kick your opponents shield (and perhaps even knock them down). Know what's a good target, and a good way to deliver the kick without exposing your leg to be hit in turn.

This next video, is a great blend of woodworking and technology. In the tutorial, you'll be finding out how to create a wooden frame for the small digital picture keychains that can be bought from stores like Target and Best Buy. It's a great gift idea for parents, relatives, or just for you. So check it out, take notes, and good luck!

Practice lineout throws for rugby from the Ford Academy in Australia. Throwing the rugby ball with two hands overhead. It is important to focus on targeting, speed and your teammates. A lineout throw is made when the ball goes out of bounds and you need to reenter it into play.

Want to improve your tennis skills? Check out this instructional tennis video that demonstrates how to hit a tennis ball across the court in this video tennis lesson.

Check out this instructional baseball video that demonstrates how to play infield. This video offers a few tips for fielding ground balls. Learn how to make a play on a grounder from a professional in this baseball video.

There is not better way to get in shape and target trouble zones than with the help of some experts in fitness and some simple workout equipment. In this how to video tutorial SELF Magazine shows you how to tone and sculpt your body with a simple beach ball. Tone difficult areas with tilt-a-whirls, dipsy dos, squeeze play, close reaches, reverse lunges, pendulums, hold your own and tummy toner exercises.

Don't have time for a workout? Then watch this how to video to learn how to do a five minute workout that will get you six pack abs. These exercise will target your upper abs, lower abs, and obliques.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

After opening up its Spark AR platform on Instagram for all creators, Facebook is already expanding the platform's capabilities on its Snapchat killer.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

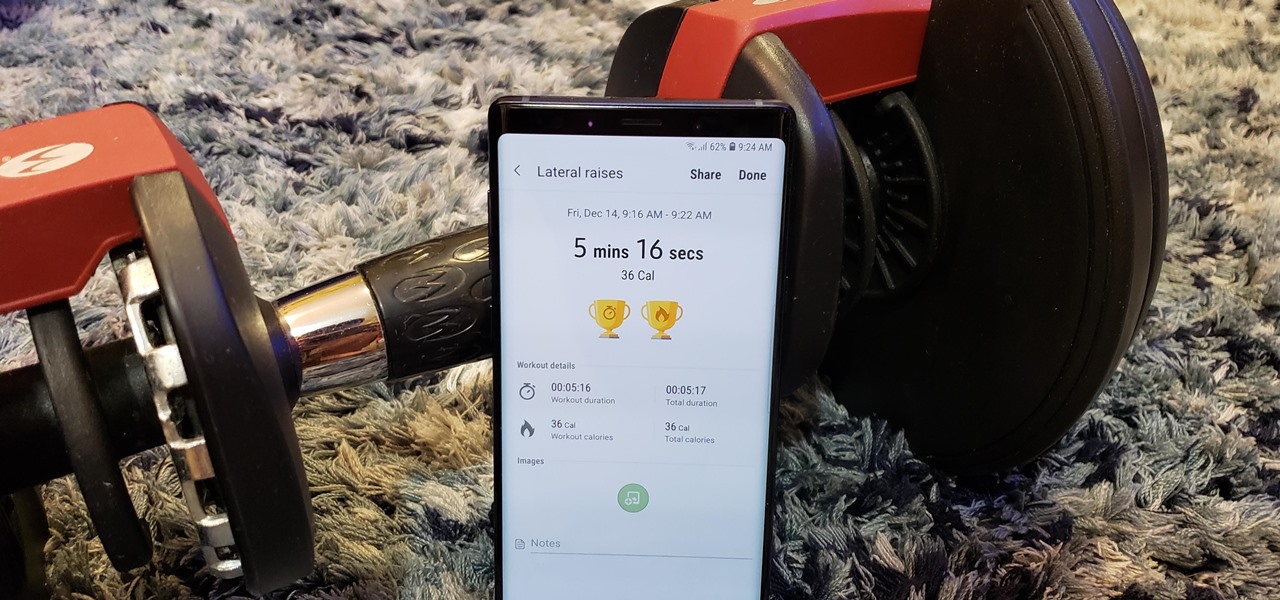
Keeping track of your physical activities can be difficult, especially if you have a hectic lifestyle with responsibilities to constantly stay on top of. Thankfully, Samsung Health is there to help you log your workout routines, leaving you with one less thing to keep track of as you go about your busy day.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Virtual reality headsets aren't new, but they may be something you or someone on your holiday shopping list hasn't experienced yet. If you're going to dive into the world of smartphone-based virtual reality, the best time to do it is during Black Friday when all the good sales are going on.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

You don't need to invest in fake hair - AKA hair extensions - to look like you have a head full of enviable voluminous, thick hair. In fact, all you need to do to create buxom hair looks is a few tricks, and a few hairstyles targeted towards making your hair look fuller.

Baking soda is like a miracle in a box. Whether you need to clean a doggy doo doo stain on your carpet, need to deodorize your refridgerator, or need an all-natural face scrub, baking soda has a cure for it all.

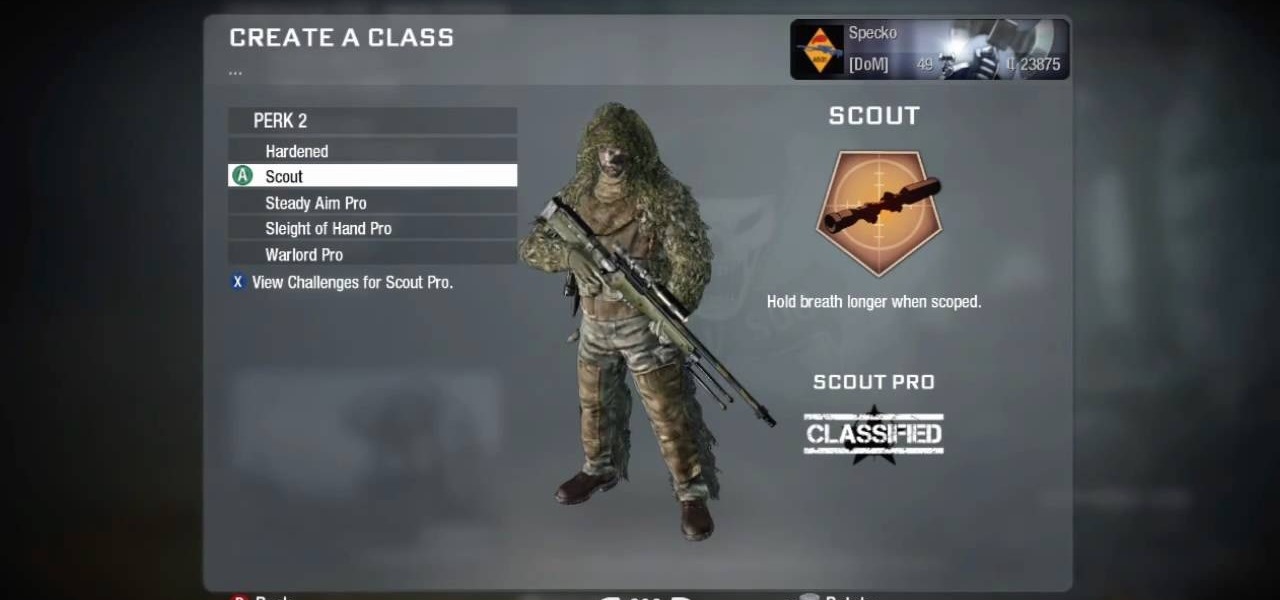
Sniping is a good skill to pick up when playing war games, since it allows you to kill enemies with great accuracy at long range. You'll need to find good spots with decent cover that give you access to enemy targets without revealing your own location.

Love the idea of a superhero MMO, but prefer the feel and controls of a first person shooter? You can actually set up your controls and targeting system in the game to make the interface behave more like your favorite FPS!

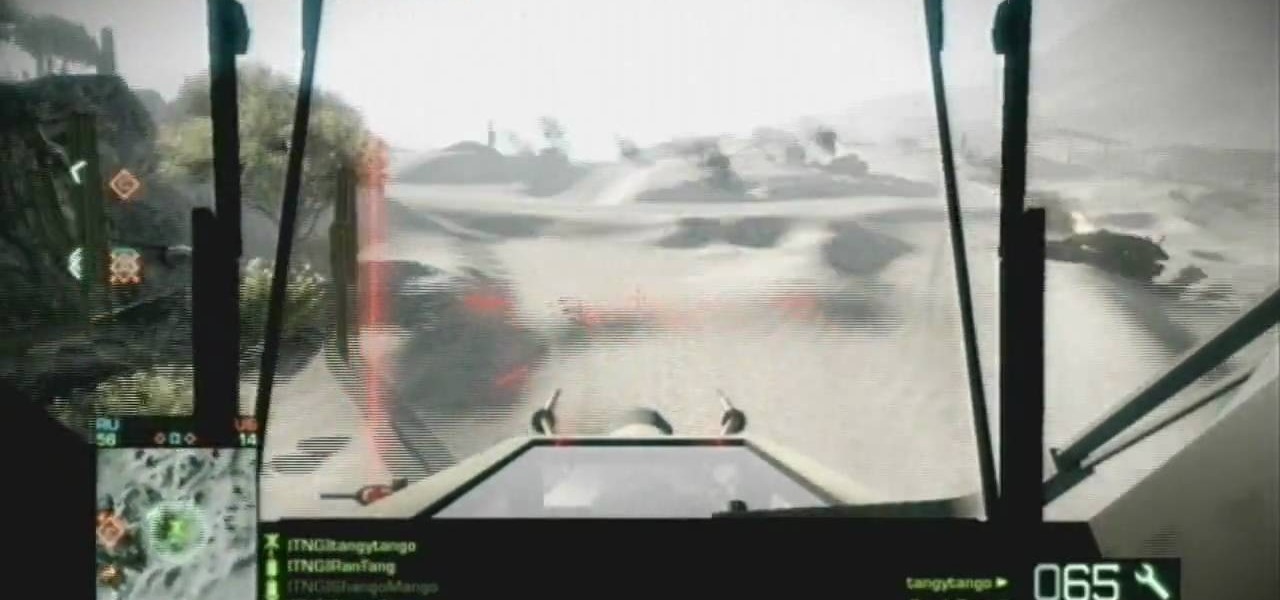
The helicopter in Batttlefield: Bad Company 2 is really powerful, but really pwning people with it requires a lot of technique. This video for advanced BC2 flyers will show you some cool tricks for improving your game, including how to utilize a copilot properly and how to prioritize your targets.

This clip demonstrates a simple Reformer-based Pilates exercise routine to target your legs. With Pilates, as with any physical fitness system, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. Whether you're looking to slim down or merely tighten up your core, you're sure to be well served by this home fitness how-to from the folks at Balanced Body Pilates.

This clip offers a demonstration of a simple Reformer-based Pilates to target your flexor muscles. Whether you're toying with the idea of opening up your own Pilates studio or merely need some help tackling a certain pedagogical or administrative problem, you're certain to be well served by this free video tutorial from the folks at Balanced Body Pilates. For more (and more comprehensive) information, take a look.

Target your shoulder girdle with this effective Pilates arc routine. With Pilates, as with any physical fitness system, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. Whether you're looking to slim down or merely tighten up your core, you're sure to be well served by this home fitness how-to from the folks at Balanced Body Pilates. For complete instructions, give this free exercise video a gander

If you want to make a movie with zombies, or the apocalypse, or the apocalypse and zombies, then you are going to have to learn how to create a really haggard-looking, disease-ridden face out of makeup. This video will show you how to do it using Rice Krispies, among other things. The end result is terrifying, and sure to scare your audiences or trick-or-treating targets into doing what you want (buying theater tickets or giving your candy, respectively).

Score those famously fit football player shoulders by watching this video, which teaches you how to perform a pull up exercise.

Brickbiys518 here, teaches you to make a LEGO cabinet. You need one 2x6 thin, two 1x6 chunkies, six 2x1 thins with the dot in the center and 12 traffic light bricks. To start off, take the 12 traffic light bricks and put them into stacks of two. There are 6 stacks in the end. Lay them out horizontally one below the other. Take the 1x2 with the dot in the center bricks and put them on two stacks at a time thereby joining the two stacks. In the end, you have three stacks. Put them aside and tak...

The experts at Bunning's have come up with a few tips for the consumer to consider when they are next in the market for paving equipment. Find out if the job needs a solid block paver or a thinner grade paver. Preserving the tools once they leave the store is in your hands. Last, but not least, watch the weight!

You see someone doing something illegal and there are no police officers around. Do you have the right to play cop? Here’s the lowdown.