Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

This a simple drawing video targeted for and taught by a young girl. The instructor demonstrates how she sketches out female figures, either little girls or women, on her drawing board. She makes additional remarks about hoe to modify and personalize these renderings. So gather up some pens or pencils and paper, and check out this cute little video. You'll learn how to sketch people in no time!

Aerobics are targeted by total physical fitness: strength, flexibility and cardiovascular fitness. Aerobics can be taken in classes and are usually done with music. To practice aerobics you should follow an instructor, stay in motion, use arms to lower or raise intensity, and strengthen heart rate. With this how to video soon you will be able to practice aerobics.

Learn to play the board game "Plunder" with tips from this how-to video. To play Plunder, you need six players at the most. It is targeted mostly toward adults but even kids as young as eight like to plunder.

The oblique muscles targeted by this bend-and-twist exercise will help you pick up everything from envious stares to spare change on the sidewalk.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

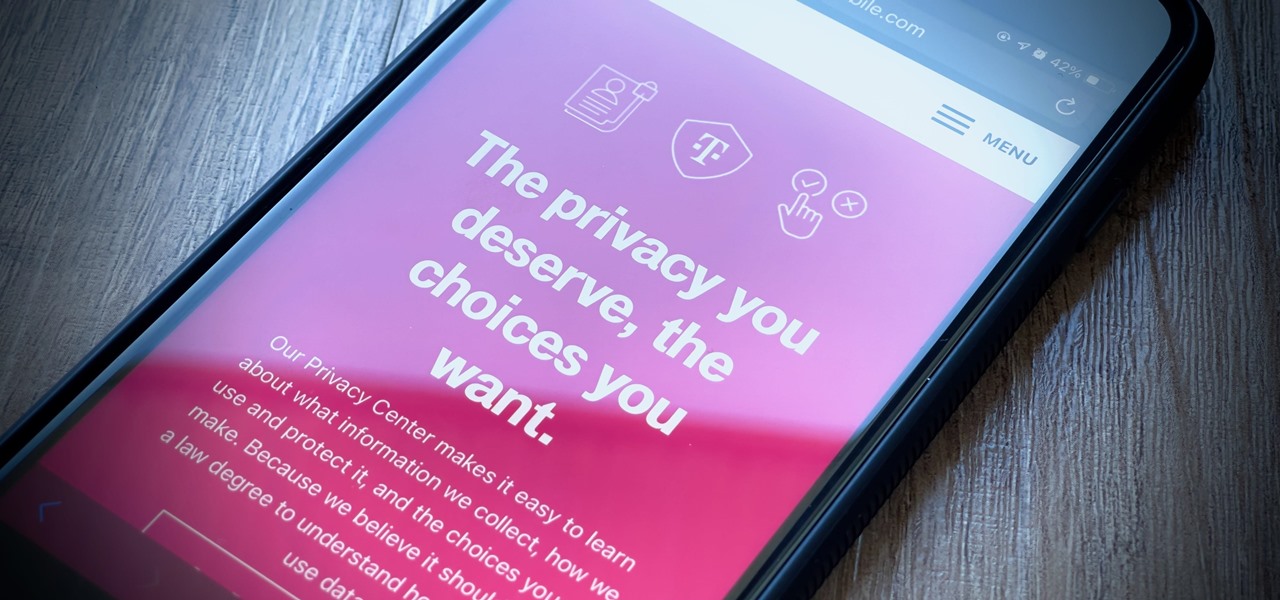
It's getting harder and harder to escape ad tracking by the day. For the latest example, look no further than T-Mobile. The No. 2 carrier updated its privacy policy on Feb. 23, 2021, indicating that it would start sharing customer data with advertisers under the guise of more relevant ads starting April 26. If that's not something you'd like to participate in, there's a way to opt-out.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

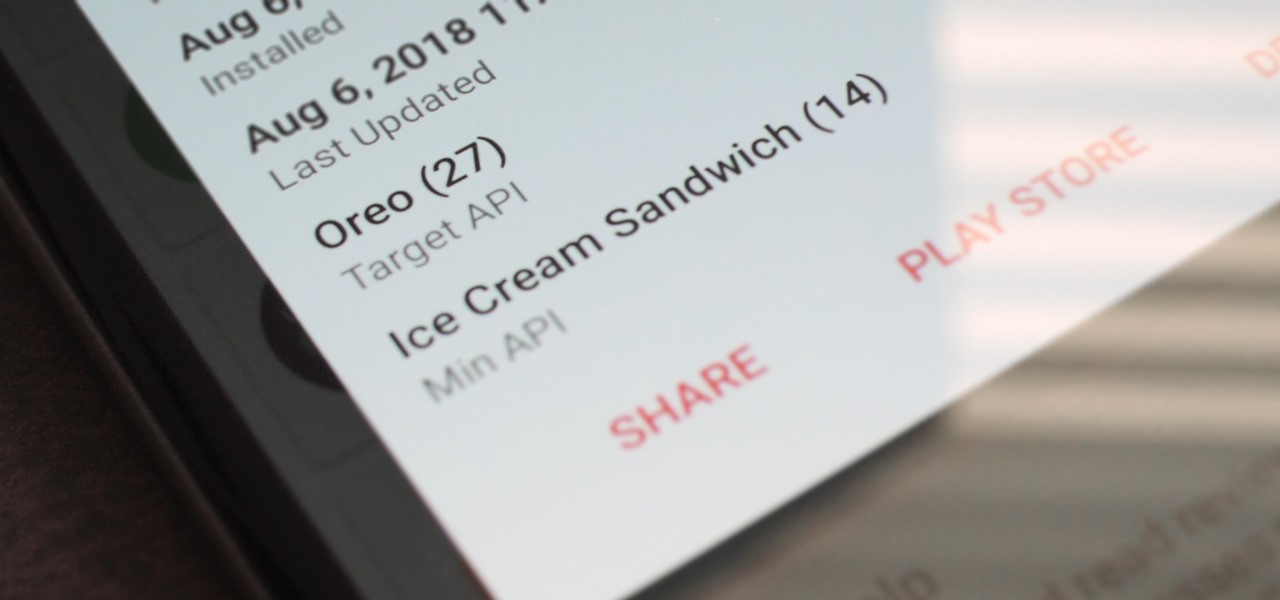
Starting November 1, 2018, Google will require that all new apps and updates to existing apps target Android 8.0 Oreo or higher. This move means the developers behind many of your favorite apps are now scrambling to get their software modernized, while others are considering abandoning outdated apps altogether.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

As you may have heard, Verizon has jumped on the "giving up users' data to whomever will pay" bandwagon with its new AppFlash spyware app that's all set to be pre-installed on at least one of the Android phones they sell.

When Facebook purchased WhatsApp for $19.3 billion back in 2014, we all knew this was coming—it just took longer than we thought. But starting today, the data mining became official, and now, information from your favorite messaging app is no longer out of reach for the world's biggest social media site.

Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

Super Mario Run was released for iOS on December 15, 2016. Even though it debuted as a "free" app, almost all of the playable content was hidden behind a ridiculous $10 unlocking package. Despite coming with such a hefty price tag and receiving a two-star rating on the day of its release for iOS, Android users are still very much interested in giving this game a whirl.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

Cars are expensive to buy, replace or repair. Check out this video and learn how to avoid the most statistically dangerous parking areas. There is no guarantee that no one will touch your vehicle, but by take precautions you are much less likely to be targeted.

Big business is on the web these days and you don't have to build a shopping website or blog to get involved.

Don't sit back and take verbal abuse! This tutorial will teach you how to dish it back out and craft the perfect insult.

The iOS 14.4 developer beta was pushed out a day ago, and now the iOS 14.4 public beta is out and ready for your iPhone. At first glance, there's not much to look at in the new beta release, and it's not yet known if it lays out the groundwork for missing features such as 5G data with dual SIMs, shared third-party app subscriptions, and Xbox Core Controller.

The next big phase of iOS 14 has started with the release of the iOS 14.4 beta. Right now, the developer-only beta features only one known item. Apple introduced the ability to scan App Clip Codes in iOS 14.3 with the Code Scanner control, and now in iOS 14.4, you can launch a local App Clip experience via Camera, NFC, Safari Smart App Banner, or iMessage.

Despite the launch of ARKit a year ago, and ARCore this year, a true killer app has not arrived for either platform, that's according to the head honcho for one of the leading development environments for 3D applications.

Google's new AI-powered camera, Google Clips, seems to be targeted at parents of young children in its current form, but the idea itself has unique potential. Just set it up somewhere, then you'll never miss a moment trying to capture the moment — you'll have a robot photographer taking care of that stuff for you.

Coming into this year's Consumer Electronics Show (CES), the common sentiment among observers was that this was expected to be the big year for augmented reality.

Your iPhone has a lot of personal information contained within it, so of course you want your device to be secure. You don't want that information getting into the wrong hands — or any hands other than your own, for that matter.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!
Welcome back Hackers\Newbies!
How Do You Do A Business Plan? Part 1 of 5 (Series designed to discuss the parts of a business plan, what information is involved in each part, and why a business plan is needed.)

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.